Introduction
Although there are multiple definitions widely for ‘Internet of Things(IoT)’, but for purposes of this blog series we will be going with ..IoT refers to any physical device with computing power and capability to transfer data over networks without human to machine interaction.
- Hacking Apps For Android
- Shellphish Install in Termux
- Use of FTK Imager Forensic Tool
- Whatsapp Hacking App 2021
- Penetration Testing Categories
IoT Security Importance
Anyone who knows about The Mirai Botnet and Stuxnet know that how important and serious IoT security is. There are people out there whose daily lives depend on these devices, one good example would be patients with a pacemaker implant; A pacemaker is a medical device for heart patients whose heartbeat is slow or irregular and is implanted in the heart itself.

What is a Threat?
A threat could be a statement to a person, thing, or device that could impose dangerous or unlikely situations on them. A threat poses no danger on its own, for a threat to matter it must have some sort of impact.
What is IoT Threat modelling?
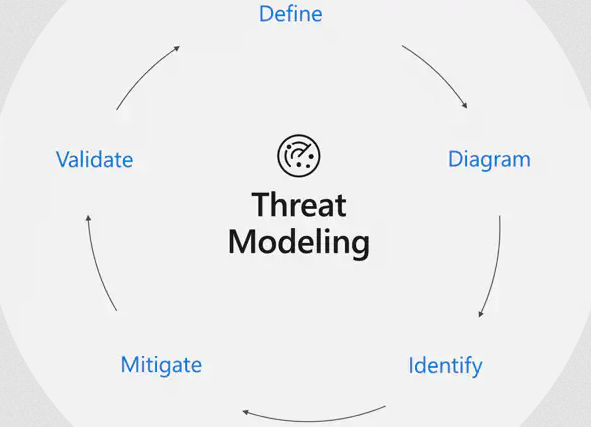
Threat Modelling is a process using which one can systematically identify any possible attacks against any device and then prioritize certain issues against their severity.
IoT Threat modelling is important to understand threats, their impacts, and appropriate mitigations to eliminate them.
Why Threat Modelling for IoT is required?
The IoT world is made up of systems with low computing power, low power consumption, low memory, and disk space and is deployed in insecure networking environments.
Nowadays hardware manufacturers have realized they can easily convert any inexpensive platform, such as an Android phone or tablet, a Raspberry Pi, or an Arduino board, into a sophisticated IoT device and this just opens up a plethora of vulnerabilities in these devices.
In addition to this these IoT devices often don’t have the capacity to run antimalware or antivirus
protection. They have very minimalistic designs which are developed for ease of use, they don’t
support common security controls, such as software whitelisting, in which devices allow
only specific software to be installed, or network access control (NAC) solutions, which
enforce network policies that control user and device access. Here Threat modelling for the Internet of Things comes into the picture.
How it’s done?
The most common way to use threat modelling in your security assessments is to follow a FRAMEWORK.
There are multiple frameworks out there among which most common and effective are STRIDE and DREAD.
STRIDE is a threat classification model and only focuses on identifying weaknesses in the technology and not on vulnerable assets or possible attackers. The STRIDE acronym represents the following threats:
Spoofing: When an actor pretends to play the role of a system component.
Tampering: When an actor violates the integrity of data or a system.
Repudiation: When users can deny they took certain actions on the system.
Information Disclosure: When an actor violates the confidentiality of the system’s data.
Denial of Service: When an actor disrupts the availability of a system’s component or the system as a whole.
Elevation of Privilege: When users or system components can elevate themselves to a privilege level they shouldn’t have access to.
The DREAD classification scheme
DREAD is a risk rating system and it helps evaluate the risk posed by each threat discovered.
The DREAD acronym represents the following criteria:
Damage: How damaging the exploitation of this threat would be.
Reproducibility: How easy the exploit is to reproduce.
Exploitability: How easy the threat is to exploit.
Affected Users: How many users would be affected.
Discoverability: How easy it is to identify the threat.
IoT Threat Modelling Conclusion
In this blog post we provided you with an introduction to threat modelling and frameworks we can use for various approaches. We encourage you to explore other frameworks and processes as well.